Building Serialized Phishing Simulation and Security Awareness Campaigns
The Science of Forming Habits
As we discussed earlier, the main goal of an organizational security awareness education program is to modify the participants’ behavior. In other words, we want the employees to develop the right information security habits, such as examining links before clicking them, not sharing sensitive information via e-mail, or reporting suspicious e-mail messages. Therefore, we may want to take a closer look at how habits are actually formed. In psychology, habits are defined as actions that are triggered automatically in response to associated contextual cues [1]. For safe drivers, getting into the car (contextual cue) would trigger the action of putting on a seatbelt. For a safe IT user, seeing a link in an e-mail would trigger the action of hovering the mouse pointer over it and examining the URL. Best part about habits? Once formed, they are here to stay: after conscious motivation (such as completing a Phishing awareness module after getting phished in a simulated campaign) is no longer there, habits are likely to persist. More good news: due to their automatic nature, habits are cognitively efficient, which means your employees won’t even need to think before examining that link. What’s the bad news? It’s not that easy to develop a new habit. The common myth of forming a new habit in 21 days has been debunked by scientific studies that show that it may take up to 254 days to intentionally develop a new habit, depending on the difficulty of the action [2]. They key to success? Repetition and a ‘small changes’ approach.

Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization.
Need for Repeated Phishing Simulations and Awareness Training
“As behaviors are repeated in a consistent context, there is an incremental increase in the link between the context and the action. This increases the automaticity of the behavior in that context.” - Wood & Neal, 2007 [3]
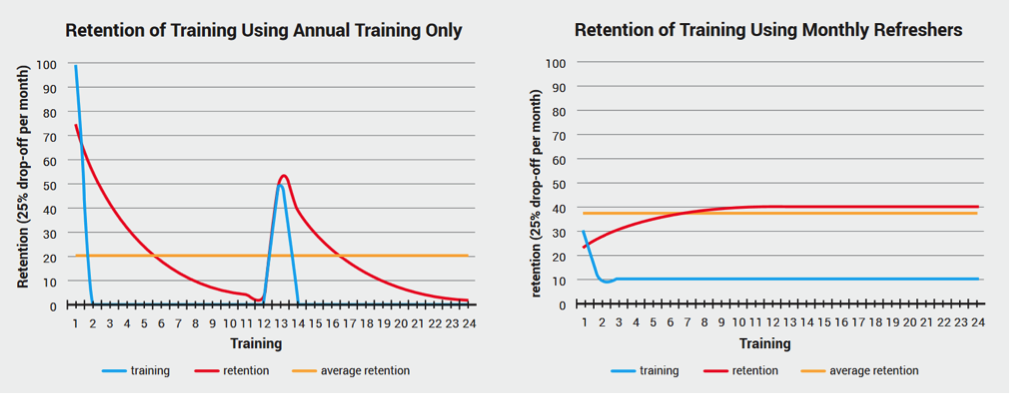
Notice the words ‘repeated’ and ‘incremental increase.’ Research shows that learners lose up to 25% of the previously remembered material. When applied to the traditional annual awareness training versus staggered training module that features monthly refreshers, the average retention rate can be nearly doubled! In the illustration below, the graph on the left represents the traditional annual training model, with the 25% loss of retention applied. Even though the retention rates are sky-high immediately after the training, they drop to nearly zero by the end of the year, with the average retention rate being only 20%.
The figure on the right shows a different model, where the initial training session features only 30% of the total material, with 10% more added every month. Result? Almost 40% retention rate throughout the year. So, to make your security awareness program more efficient, choose a training solution that will allow you to easily repeat training sessions and add small portions of new material. Later we will see how this can be easily achieved with AwareEd, part of the InfoSec Institute’s SecurityIQ platform.
Repeatability is even more important for simulated phishing campaigns, because here we are actually talking about changing behavior rather than retaining knowledge. And also because the most successful real phishing campaigns a) include multiple e-mails and b) are repeated multiple times. Verizon 2013 Data Breach Investigation Report states that using just three e-mails in a campaign “gives the attacker a better than 50% chance of getting at least one click. Run that campaign twice and that probability goes up to 80%, and sending 10 phishing e-mails approaches the point where most attackers would be able to slap a “guaranteed” sticker on getting a click”[4]. If you want to think like an attacker, this is what you should look for in a phishing simulator for your campaigns: an ability to send out repeated phishing campaigns, each including multiple templates.
Serialized Phishing Campaigns: Increased Difficulty
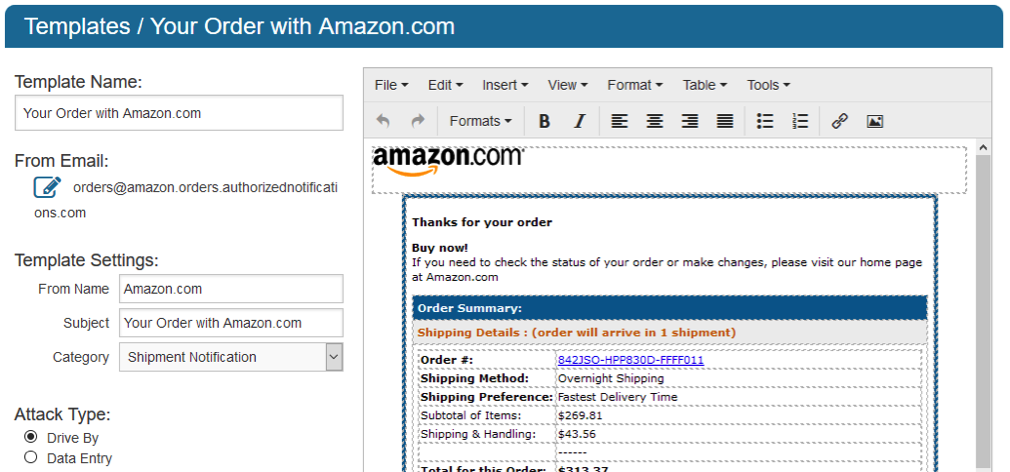
Repeated phishing campaigns, especially if they include an education component (such as an interactive Phishing awareness module presented to phished learners in SecurityIQ PhishSim), can help you in calculating effectiveness and ROI of your phishing simulation solution. The concept of ‘small changes’ can be effectively applied by increasing the sophistication level of your simulated campaigns, as well as by varying attack types. You may start with a simple attack: a Free Pizza coupon, a generic shipment notification, a banking notification without any personalization.
You may then repeat the same campaign with the same templates on just the learners who fell for this type of bait, and increase the difficulty slightly for the rest of the employees: insert actual names and addresses in the message body and the Subject line, select more common yet less obvious bait, such as file sharing notifications or social networking invitations. After that, you can get as sophisticated as imitating internal communication message format and content, and adding another step to your attack, such as data entry or malicious attachments. All of the above is easy to do with SecurityIQ PhishSim.
Serialized Awareness Training: Varying Content
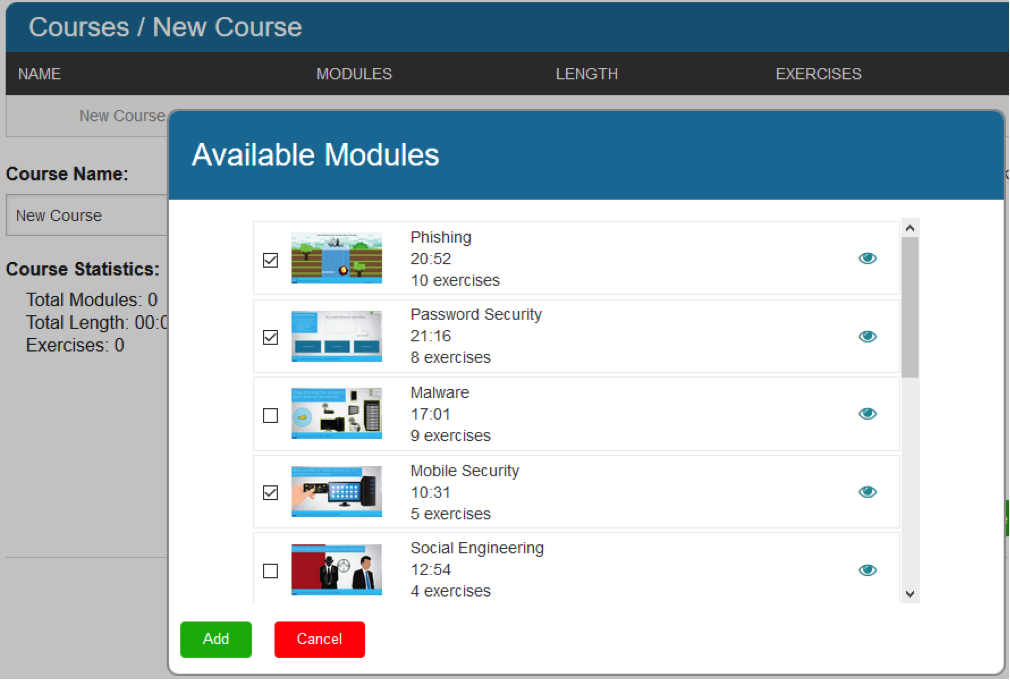
Even the most engaging security awareness content may not have a lasting effect if dumped at learners all at once and only once. As we discussed earlier, the most effective approach to ensuring a high retention rate is by introducing awareness material throughout the year, in small increments. Start with the most important topics, most relevant to your organization (phishing will most likely end up in this category) and applicable to most learners. Then, in subsequent sessions, cover the topics that are more technology specific or address less imminent threats, while re-introducing some of the material as a refresher. “Who has time for all this?” you may ask. Learners, going through all these small sessions, or administrators, scheduling them and ensuring and tracking attendance and completion? Welcome to the 21st century! All you need is a solution that allows you to quickly create courses of various length with various content, and then easily schedule the training sessions, while providing detailed progress reports. In other words, you need SecurityIQ AwareEd.
How SecurityIQ Can Help
Ready? Log on to your SecurityIQ account and start checking boxes.
Phishing Simulation (PhishSim):
- Multiple templates in the same campaign? Check! Select templates that you like and include them in batteries to use in campaigns.
- Repeatable campaigns? Check! Run a campaign several times, with the same templates or use different templates for each run. Schedule campaigns once and collect the phish throughout the year.
- Education component? Check! An interactive (and trackable!) training module is included in the default landing page.
- Various attack types? Check! Choose between Drive By, Data Entry, or File Attachment attacks.
- Lots of phishing templates? Check-mate! There are almost 200 categorized customizable templates to choose from, or you can easily create new ones with a straightforward WYSIWYG editor. You can also quickly personalize your e-mails by using variables.
Awareness Education (AwareEd):
- Engaging content? Check! A library of highly interactive modules, each with several exercises, filled with latest threat information and gamification elements.
- Delivering material in portions? Check! Make your courses as short or as long as you want them to be, by adding and removing individual modules.
- Easy scheduling? Double-check! Schedule multiple campaigns or the year, and don’t worry about a thing: SecurityIQ will run them as scheduled and send out notification and reminders automatically.
- Pleasant learner experience? Check! The content is engaging and the process is simple. Give your learners sufficient amount of time to complete your course, and they will go through modules with ease at their own pace, from any compatible device (which means any device with a modern web browser), stopping the training if needed and picking up where they left off.
Forming good security habits is a serious task. So get ‘series’ about it with SecurityIQ!

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
References
- Making health habitual: the psychology of ‘habit-formation’ and general practice. http://www.ncbi.nlm.nih.gov/pmc/articles/PMC3505409/
- How Long It Takes to Form a New Habit. https://www.brainpickings.org/2014/01/02/how-long-it-takes-to-form-a-new-habit/
- Wood, W., & Neal, D. T. (2007). A new look at habits and the habit-goal interface. Psychological Review, 114(4), 843–863. http://dornsife.usc.edu/assets/sites/545/docs/Wendy_Wood_Research_Articles/Habits/wood.neal.2007psychrev_a_new_look_at_habits_and_the_interface_between_habits_and_goals.pdf
- Verizon 2013 Data Breach Investigation Report. http://www.verizonenterprise.com/resources/reports/rp_data-breach-investigations-report-2013_en_xg.pdf