Enumerating Disk Artifacts in Memory
In my earlier article, I have listed out ways how to enumerate different structures like page tables, processes, VAD, PEB, etc. (For more information on these check out these articles). In this article let's take a look at the how to enumerate various disk artifacts like MFT in memory using Volatility's plugin. Before starting I would like to make it clear that we might not see complete information in memory for particular disk artifacts since there is a greater chance that some information is paged out.
Master File Table
Windows has a special file known as Master File Table (MFT) which is an index to all the files located on the system. All the entries in the MFT file are 1024 bytes long and contain metadata and other attributes about a file like $STANDARD_INFOMRATION, $DATA, etc. Most of this data is usually found in the single line of record and is called resident data but mostly since data in files are long enough to be not able to fit in memory, so they have to reside outside the record and are called non-resident. Note that if data is small enough to be accompanied in the 1024 bytes long record, then the data will also be resident. We can use Volatility's MFT parser plugin to extract MFT entries from memory. This plugin will extract important attributes such as $FILE_NAME, $STANDARD_INFORMATION, $DATA.

FREE role-guided training plans
Below is a screenshot for MFT parser in action

As you can see, it parses $FILE_NAME, $STANDARD_INFORMATION, $DATA. Also, it can also find the Alternative Data Streams (ADS). If we have to dump the $DATA into a raw file, we can do it with this plugin itself by using the –D switch.
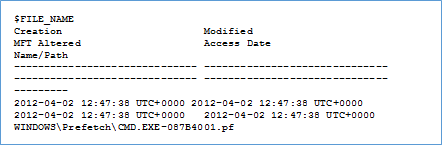
This output of MFT parser can also be done in body format which can be further parsed using mactime utility. We can use the MFT parser plugin output to look out for other things using simple grep like looking for prefetch files(.pf). Below we can see that cmd.exe prefetch file got created on the system.
Sometimes it happens that when the data is small, it gets stored in the MFT itself. In that case, make sure to run the MFT parser plugin in the verbose mode. That will help to extract the data stored within MFT itself. Another great use of MFT parser is to find the ADS (Alternate data Stream) content. ADS is often used by attackers to hide malicious files in the system because these hidden cannot normally be enumerated by the scan. Volatility plugin MFT parser can be used to extract these hidden files. Also, MFT parser output can be used to determine the user execution of several documents. It can be detected with the presence of various LNK files which will not only show that the file existed on the system but also user interacted with by double clicking it.
Volatility's dump file and file scan
So far we have seen that the MFT parser plugin is good in enumerating the metadata about the file like MFT record number, the path of the file and even contents in $DATA attribute (if the data is less than 700 bytes). But what about larger files, how to view their contents (even partially) from memory? We can use Volatility's dump files plugin. Dump files will extract exe's, DLLs, registry hives, PDF and even office document.
Volatility's dump file plugin works by enumerating handle table and VAD for FILE_Objects. Each FILE_Object contain following section pointers:
- DataSectionObject: Pointes to memory mapped files
- SharedCacheMap: Points to file cached by Windows Cache Manager. Windows cache manager works with Windows memory manager. Memory manager controls which part of the file will be in memory and cache manager uses that information to cache data within virtual address control blocks.
- ImageSectionObject: Points to memory mapped binaries.
Below is an example of dump files plugin in action:

Here I have used dump file plugin following switches:
-r: It is a regular expression. Looking for *.exe in this example
-n: It says to reference the original file name in the output.
As stated earlier, since dump files work by querying handles or BAD tree, there are still some important areas that this plugin misses like $MFT which is not in VAD. We can use file scan to enumerate FILE objects within memory.
Below is an example of file scan in action.

If we have some file of interest that we want to investigate, then we can use the offset provided by file scan as a parameter wit –Q to dump that file/executable.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Therefore, we have seen that how various disk artifacts can be recovered from memory which can be used to set the context on the investigation.







