Security Awareness & Training Resource Center
Featured content

Deconstructing Human-Element Breaches | Infosec HRM
Human risk management isn’t just rebranded SA&T — it’s a profound change of mindset, strategy, process and technology that approaches human-related breaches in a new way.
![Inside an Infosec Boot Camp: All your questions, answered! [replay]](/globalassets/is-wb-24-05-inside-an-infosec-boot-camp_thumbnail2.webp?width=338&height=304&rmode=Max&bgcolor=transparent)
Inside an Infosec Boot Camp: All your questions, answered!
You need to get certified, but is an Infosec Boot Camp the right choice for you — or your team? Find out in this live Q&A with two Infosec instructors.

Emerging trend checklist: Which certifications cover which new skills?
Boost your team's cybersecurity skills with the right certifications. Discover the most in-demand skills and the certifications that cover them in our free guide.

Security Awareness Outcomes with Infosec IQ
See security awareness and training outcomes from more than five million Infosec IQ learners.
Our resources

Role of Threat Intelligence in Business World
Judy Malware: Millions of Android Devices Potentially Exposed

Malware-as-a-service

How Hackers Use Fear and Urgency to Get Your Information
/dev/random:Sleepy CTF Walkthrough

Learning Pentesting with Metasploitable3

The Virtual Personal Assistant and Its Security Issues

How to Recognize Phishing Emails

Top 7 Ways to Use Wi-Fi Hotspots Safely
How is AI Addressing Cyber Security Challenges?

Impact of Cyber Security on Start-ups

Risks and Benefits of Security Policy Templates
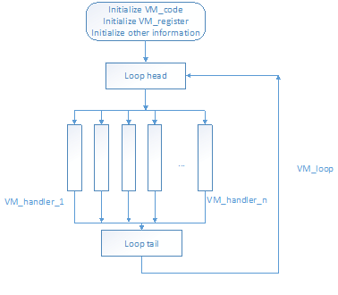
Tutorial for Building and Reverse Engineering Simple Virtual Machine Protection

Super Mario CTF Walkthrough

Jailbreaking Your Smartphone

5 Key Steps to Survive as a Cyber Security Startup
Metasploitable: 2 - walkthrough
NullByte - Walkthrough
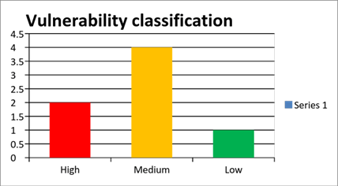
Application Security for Beginners: A Step-by-Step Approach
BilluBox CTF Walkthrough 2

Top 50 database administrator interview questions [updated in 2018]
User Privacy: The Price Paid
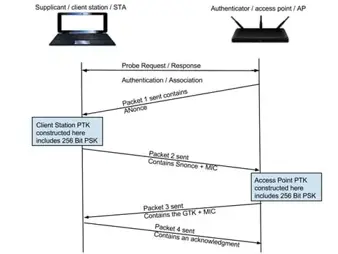
Cracking a WPA2 encryption password file
Metasploitable: 1 - walkthrough