Learning Pentesting with Metasploitable3
Metasploitable is back with version 3, which includes lot more interesting vulnerabilities. Metasploitable3 is special because it is not a pre-configured downloadable VM. The user himself can configure it, and the user can also decide target version of Windows.

FREE role-guided training plans
By its name, Metasploitable is a designed to practice attacks with Metasploit Framework. Nevertheless, it is lot more fun to exploit those vulnerabilities without Metasploit Framework.
In this series of articles, we will discuss most of the challenges that come with Metasploitable3. Instead of just cracking the challenges with the hints provided at Metasploitable3's Github page, we will use the VM to learn the penetration testing concepts similar to how we do them in the real-world penetration testing engagements. We will achieve this by following the steps shown below.
- Information Gathering
- Exploitation
- Post Exploitation
Just to make things clear, it is possible to gain access to the target box using any of the remotely exploitable vulnerabilities. However, we will try to gain access to the machine in multiple ways.
In this article, we will discuss how to setup the lab to follow the rest of the articles in the series. Though, lab setup is straightforward with the PowerShell scripts provided; I would like to cover it here for those who need it with the screenshots and clearer steps.
The setup:
Following are the things needed for setting up Metasploitable3 on your Windows Machine.
VirtualBox – I faced problems with various versions of VirtualBox and VirtualBox 5.0.40 worked without problems.
Packer – Packer is required to convert the Windows ISO image to a box file. It can be downloaded from here.

After downloading packer.exe, make sure that you add its path to the environment variables,

Vagrant - Vagrant, can be downloaded from here.
Download the Windows version of the Vagrant and install it by double clicking the msi file.
Once the installation is complete (a reboot may be required), open up a command prompt and type vagrant. You should see the vagrant help as shown in the figure.

Git – Git is optional, but better to have. You can download it from here.
Once downloaded, run the exe and Git will be installed. You should see the following when you successfully installed Git.
Now, clone Metasploitable3 using the following command
git clone https://github.com/rapid7/metasploitable3.git

Once done, you should see the following.

With this, we are done with the prerequisites. We can begin running the commands to download and build a vulnerable VM.
Open up PowerShell.exe and navigate to the folder where you have downloaded metasploitable3 and run the following command.
packer build .windows_2008_r2.json
The above command will download the Windows server 2008 ISO image from Microsoft's website and convert it to a .box file. After completing this step, you should see a file with the extension ".box".
Next, run the following command
vagrant box add .windows_2008_r2_virtulbox.box –name=metasploitable3
Once the above step is done, run the following command.
vagrant up
The above two commands will set up the Windows server 2008 Virtual machine inside the VirtualBox with all the required vulnerable software for us to exploit. This process may take up to one hour.
After completing the setup, you should see your Windows server 2008, virtual machine up and running.

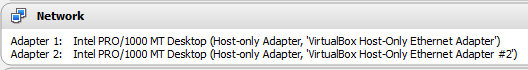
Following are my Network settings for metasploitable3 VM.
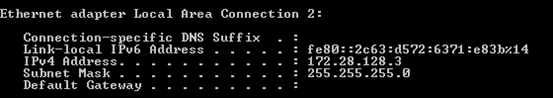
Open up a command prompt and check the IP address.
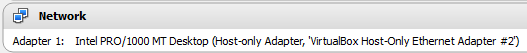
Next, launch Kali Linux. Following are the network settings for my Kali Linux.
Open up a terminal and check the IP address. As you can notice, both Metasploitable3 and Kali Linux are on the same network.

With this, you are good to go to follow the upcoming articles in the series. Just to test if everything is set up correctly, do a simple nmap scan on your Metasploitable3 VM, and you should see the following output from Nmap.


What should you learn next?
Final note
This article has explained the process of setting up Metasploitable3 Virtual Machine on a Windows server 2008 machine. You can set it up on other versions of Windows if you wish. In the next article, we will discuss information gathering concepts using Metasploitable3.







