What Is Vishing?
What Is Vishing?
If you pay any attention to the world of cyber-crime—and you should—you’ve probably heard all about phishing. It’s a method of cyber-crime by which the attacker pretends to be an authority figure in an email, or other form of communication, to trick the target into giving up sensitive data. There’s actually a very good chance you’ve been on the receiving end of such an email, too.
However, there’s an even simpler form of criminal behavior that works much the same way and is equally important to know about. Voice phishing—or vishing—is when someone tries to pull the same kind of scam over the phone. Sometimes, a criminal will use both techniques in combination.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
Either way, it’s important that you understand how this type of scam works so you don’t end up becoming a victim.
Let’s begin with the step-by-step anatomy of a vishing attack.
Step One: Finding the Target
Just because this doesn’t seem like the most sophisticated attack in the world doesn’t mean that the scam artists aren’t using all kinds of crazy techniques to reach their goal. Today’s scam artists and cyber-criminals are as innovative as they are ruthless and there’s no lack of technology out there to leverage. This is why it’s vital that you don't underestimate something as seemingly harmless as a phone call.
If you are contacted by a vishing perpetrator, rest assured you were probably not the only one. Vishing is largely a numbers game, so the criminals need to call as many people as possible. To do this, they use special software that allows them to cast the widest net they can. Should you be the unlucky individual who actually answers, you’re also one step closer to becoming a victim.
In this way, these attacks mimic many email versions where the criminal is sending out as many messages as possible. They generally don’t waste their time trying to go through, say, an entire company one-by-one.
Still, many vishers are putting in a bit of extra work. They may have gotten your number from another successful attack—perhaps using phishing—and therefore know what bank you belong to or the health insurance company that provides you with coverage. This helps them put on the identity of an authority and trick their victims into simply accepting what they say and direct them to do.
The Importance of Social Engineering
We’re going to stop here for a moment to highlight the bedrock of vishing: social engineering. It was originally a psychological term that referred to manipulation that relied on widespread habits or social norms.
If a researcher put on a lab coat when they conducted a study, for example, a room full of subjects would immediately grant them more authority and give them greater respect. People simply associate that uniform with authority and respect, so they automatically react accordingly.
These days, though, social engineering has taken on a much darker connotation. It refers to con artists and cyber-criminals who use these triggers to trick victims into handing over personal information, security credentials and, of course, cash.
Kevin Mitnick, a reformed cyber-criminal, actually popularized the more modern use of the term. He is famous in the world of cyber-security for pointing out that it is far easier to trick someone into handing over, say, their password than to go to the trouble of hacking them. In fact, he went as far as to say that it was his single most effective tactic.
When you look at those prophetic words as a prediction, you can see that Mitnick was actually ahead of his time. While hackers still use lines and lines of code and highly-evolved software to launch attacks, phishing is exploding on a global level. Much of this is no doubt because social engineering is so much simpler that just about anyone can do it (provided they have no conscience).
Step Two: Tricking the Target
The next step for the visher is to actually trick their victim into handing over sensitive information. You might think you’d be too smart to fall for such a ploy. Perhaps you’d ask certain questions to trip the criminal up. Because a lot of these attacks come from overseas, you may also feel confident their poor grasp of English would give them away.
Well, these criminals are thinking the same thing. That's why they usually use a prerecorded message. Such a message has the added benefit of being able to essentially leave a voicemail too. That means their “dialing for dollars” mass-attack approach can have an even higher rate of return.
However, the other big benefit of this method is that it further pushes their social engineering advantage. You naturally believe this recorded voice because it does sound like something your bank, credit card company, or some other large corporation would do. While it may begin changing soon, most of us don’t associate this sort of thing with criminals.
Obtaining Your Information
There are a couple of ways in which these criminals will proceed to get your information. Let’s say, for example, that you listened to the recording and you’ve been told that your phone service provider is going to cut you off because you haven’t paid your bill in three months. To address this, you need to “press two.”
Naturally, you do, which might lead to an actual person answering. Remember, at this point, the criminal may not speak the best English, but their goal is to already have you on the hook. The voice recording, which used the name of your provider and sounded very official, already has you on the hook. Plus, plenty of companies outsource their call centers to foreign countries.
The operator proceeds to describe the problem to you. When you insist that you have definitely paid your bill, they will, ironically, suggest that you may be the victim of cyber-crime. They’ll then reassure you that you won’t be charged for this issue and that they’ll actually resolve the entire thing. Of course, first they just need some information from you.
There are a number of other variations to this sort of scheme. As we mentioned earlier, it could be someone masquerading as the bank or the credit card company that noticed an issue they need to bring to your attention ASAP.
Other times, instead of talking to an actual person, you’ll be directed to call a number and provide your information. Some have even been brazen enough to impersonate the police, a special prosecutor, federal employee, or some other government employee.
In any case, you’re literally handing over access to your bank account to these criminals.
Step Three: Using the Stolen Information
Obviously, these criminals aren’t just going to leave your finances as they found them if they have your bank account number. As the majority of vishing schemes originate in China, they’ll transfer your balance to an account in their home country, immediately zero it out, and vanish.
If you gave them your credit card information, it’s even easier. They’ll just keep making purchases with it until you finally stop them.
Taking you for all your money may not even be the worst damage they do, though. They may also steal your identity once they have the necessary information and sign up for credit cards. This gives them almost unlimited spending, but can leave you with a credit score that has been completely ruined. You can easily spend thousands and thousands of dollars repairing your credit score, to say nothing of how much you’ll suffer in terms of lost opportunities.
Step Four: Disappear
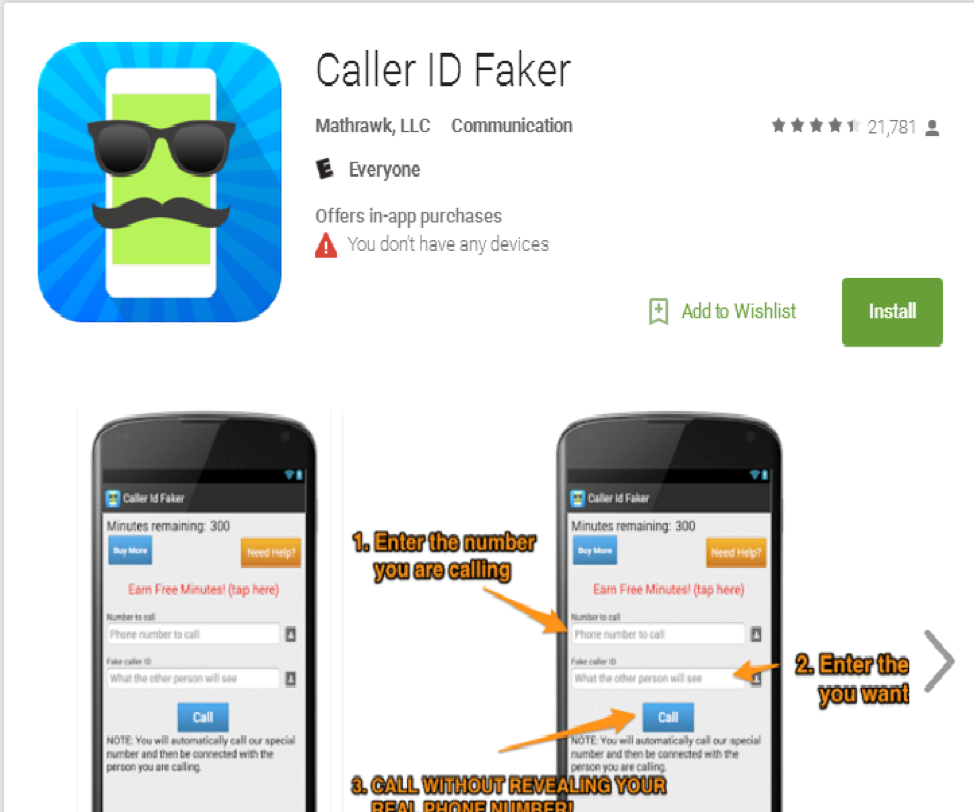
Calling people using a fake number has never been easier thanks to apps like these that make it possible
This is by far the easiest part of the vishing scheme. Whether they’re in China or calling you from next door, it’s nearly impossible to capture these thieves. In today’s day and age, it’s no great challenge to place a phone call through the Internet. So it’s not as if you can simply trace the number back to its owner.
In fact, part of their social engineering tactic is often to pick a number that will look familiar to you. They may robo-dial hundreds of people in your area code using the same one, making it easier for you to believe that it is, indeed, your local bank that’s having trouble with your account.
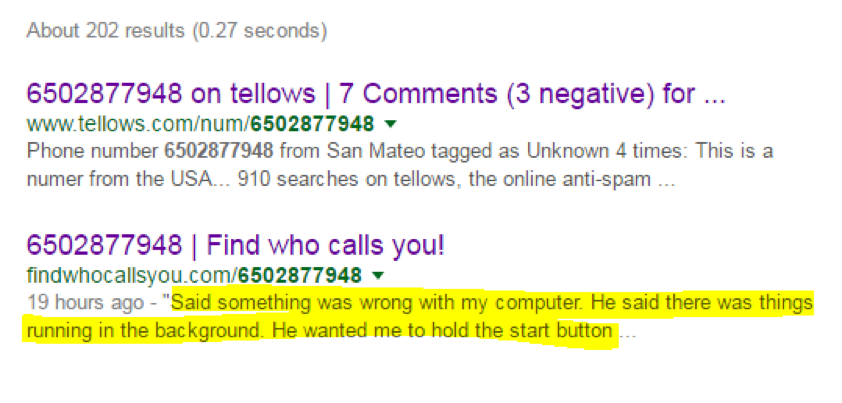
These are examples of “bad numbers”—those used by vishers to call people anonymously
Given how scary a threat this simple kind of attack is, let’s now look at two ways of keeping yourself from becoming a victim.
Prevent Vishing
Block Automated Calls
The first method is actually fairly simple. Get your number on the National Do Not Call Registry. Even if you’re never targeted for a vishing attack, you’ll most likely appreciate receiving far fewer automated calls than you’re used to.
However, this doesn’t mean you’ll never get them. You still need to practice basic common sense.
That being said, if a robo-caller does get through, you should know something is wrong because you’re on the national registry. If you’re not sure if it’s a robo-call, it’s probably a safe bet if they used absolutely no personally identifying information. Someone calling from your phone company should have no problem using your name, for example.
It doesn’t actually hurt you to listen to their message. If it’s a robo-call, just don’t comply with their demands. Instead, after you hang up, look up the number online. Simply Googling it may bring up complaints from others who got the same call. There are a number of websites that collect these responses.
Obviously, if you don’t find any such responses, that doesn’t mean you should follow their instructions. Always go to the alleged company if you have any reason to believe the call might be real. Don’t call the number back, for example. Call the credit card company and ask them about the message.
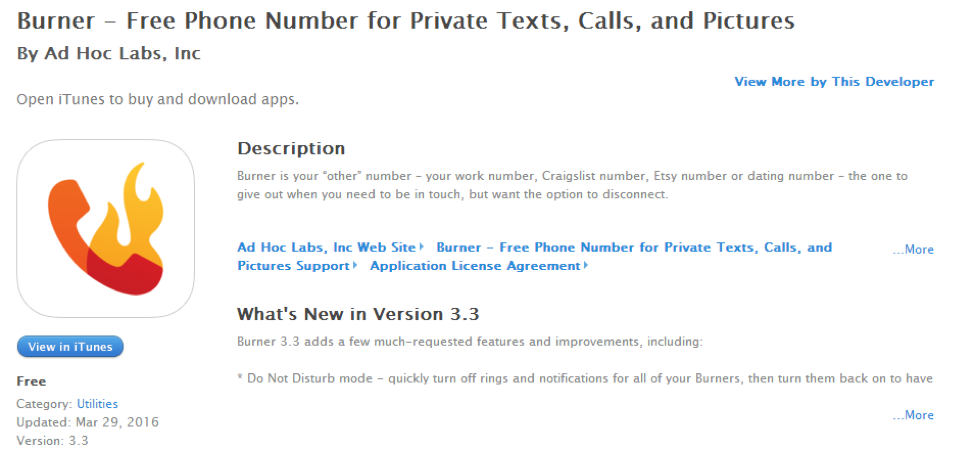
As you can see, there is no shortage of apps for hiding an attacker’s number—this one is even free!
Dealing with Personalized Attacks
Earlier we talked about how vishing attacks rely heavily on software that allows the criminal to dial numerous people at once. A lot of times, when you answer, you’ll get a machine. That’s not always how it works, though. Sometimes, there will be an actual human on the other end of the line.
While this is a lot harder for the scammer to pull off, it can also be far more rewarding. Most of us simply aren’t cynical enough to suspect someone who is calling us, personally, is personable, and has personal information about us, to be anything but genuine. The criminal will further their chances by giving you some type of information so you don’t have much time to think.
Maybe it’s someone from Visa and they’ve found suspicious activity on your card. You need to act right away to shut it down.
You don’t have to be rude to these people, but being a decent human being also doesn’t need to backfire either. Ask them for information that someone in their alleged position should have.
They’re calling from Visa? Fine. What are the last four digits of my number?
It’s your bank? What’s my account number?
The phone company? What’s my email address?
Again, someone actually working for the company they say they are should have that information on a screen right in front of them. Just tell the person that you know about vishing and are simply practicing basic common sense. If you’re wrong about them, they’ll have no reason to be offended.
Even then, though, we can’t guarantee you’re safe. If a visher is going to the trouble of personally calling you, they must have a reason to think that you’re going to make a good victim. This could mean they’ve gone out of their way to collect information on you.
The smartest move is to tell them you’ll call the company back in just a moment. Then hang up, call the credit card company, bank, phone service, etc., and ask about the previous call you received.
Conclusion
Vishing may not get as much press as phishing, which definitely accounts for far greater losses, but that’s no reason to let your guard down. If you have a phone number, someone out there will most likely call you at some point and see if you’re going to make a good target.
Interested in reading more about phishing? Check out these articles:
Phishing: Technical Details & Reasons For Attack
Spam vs. Phishing: Definitions, Overview & Examples
Phishing: Who Is Being Targeted By Phishers?
References
http://www.elitepersonalfinance.com/vishing/
http://www.koreatimes.co.kr/www/news/opinon/2012/02/167_104914.html
http://searchsecurity.techtarget.com/definition/social-engineering
http://studall.org/all3-27238.html
http://www.elitepersonalfinance.com/vishing/
https://www.donotcall.gov/register/reg.aspx
Phishing simulations & training