Vulnerability Scanners
Security of a website is very crucial thing for any organization or for personal websites. It's always advised to check the security of the website because it's better and safer to know the loopholes of our website before any attackers finds and exploits it. The commonly seen web application vulnerabilities are
- SQL Injection
- Cross Site Scripting (XSS)
- Cross Site Request Forgery (CSRF)
- Insecure Session Handling
- Session Fixation
- Information Disclosure
- Header Injection
- Insecure Configuration
- Weak randomness
Over the times, there are many tools which are being developed for providing better security and for uncovering various vulnerabilities. A vulnerability scanner is developed in order to detect the loopholes and some of these tools also suggest the prevention methods which can be implemented. The main reason why we prefer automated tools is because the process of manual exploitation could produce improper results or can crash the applications. A large number of web application scanning tools are available, both commercial and open source. We will see about few top web–application scanners and some of them are as follows

What should you learn next?

What should you learn next?
- Websecurify
- Net Sparker Community Edition.
- WSSA
- NStalker
- W3af
- Acunetix
-
Websecurify:
URL: http://www.websecurify.com/
Websecurify is a tool that can be run on Windows, Linux and MAC. It is the best tool to find the common web vulnerabilities.
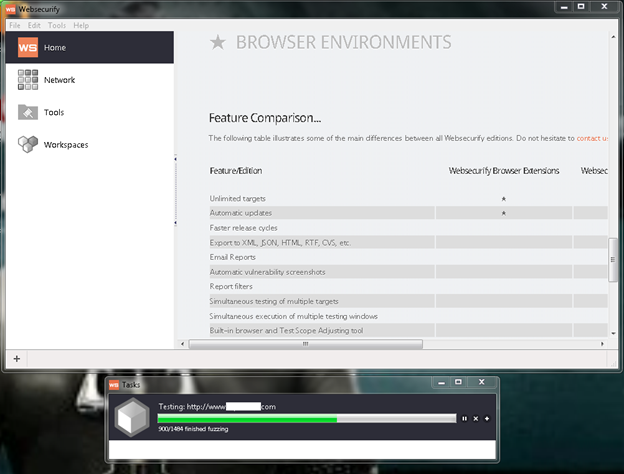
Once the target has been scanned, the tool starts fuzzing and gives the results once it is done. The scan results will contains the description about the vulnerability, solution and the URL which is vulnerable which helps us to understand and fix the vulnerability as soon as possible. A sample scan results are shown below
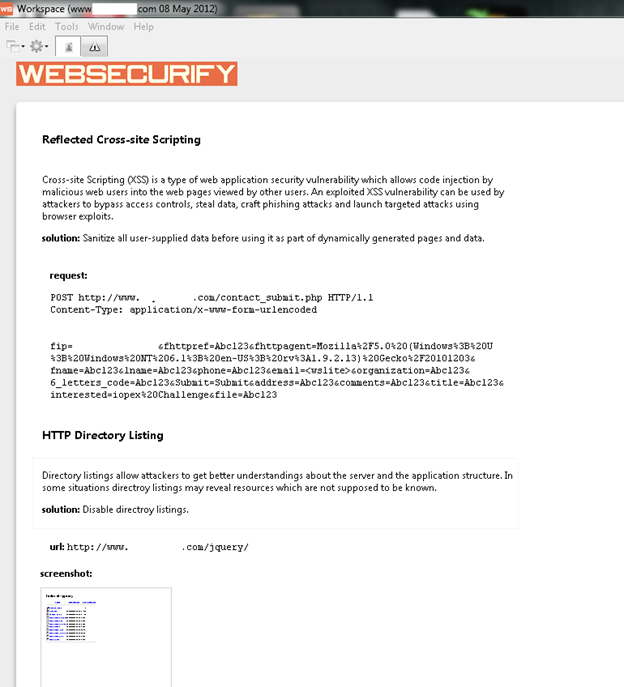
It can detect the vulnerabilities like sqli, LFI/RFI, XSS, CSRF and other categories which come under the OWASP top 10. This tool also has an online version of scanner. The url is http://scanner.websecurify.com and the user has to sign up for further scanning. For further reading, go to http://scanner.websecurify.com/tutorial
Note: The online scanner is beta version.
Features of this tool:
- Easy to use
- Simultaneous testing
- Advanced Reporting
URL:
http://www.mavitunasecurity.com/netsparker/
NetSparker is again an effective website vulnerability scanner and also very simple to use. It comes in both community edition and paid version.
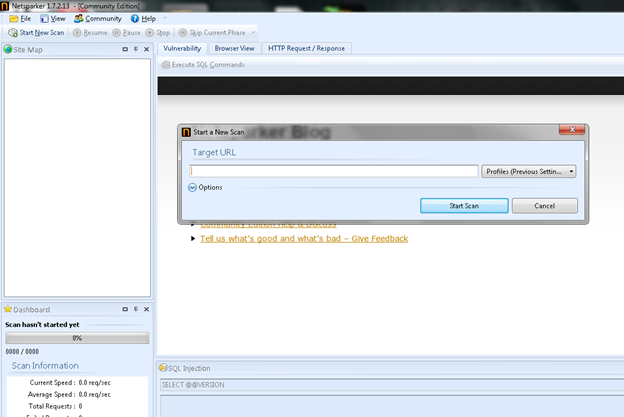
To perform the scan, press the "Start New Scan" option and enter the target URL and press start scan to scan the website. You can find three tabs namely vulnerability, browser view and Http request/response.
In the vulnerability tab, you can get the information about the vulnerable URL, description, impact and how it can be fixed.
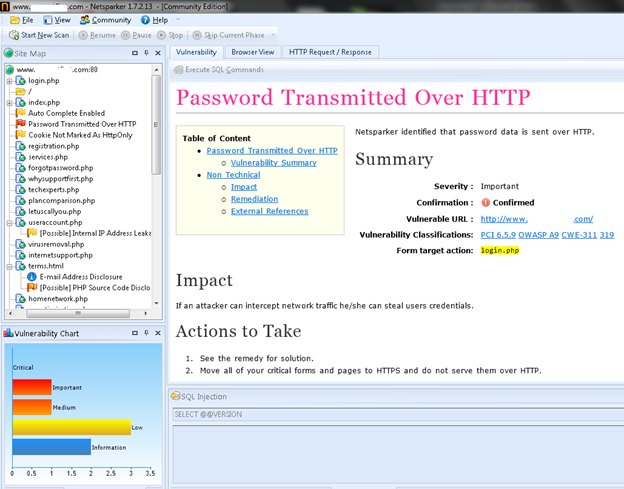
You can view the vulnerability chart also to understand the various loopholes along with the seriousness level.
Features:
Some of the features are
1. Post Exploitation feature takes automated exploitation to the next level.
2. We have in built encoder in this scanner.
3. We have an option for controlled scan.
Web Site Security Audit - WSSA
URL:
http://www.beyondsecurity.com/vulnerability-scanner.html
Beyond Security have a very good web application vulnerability scanner and also integrates with network scanning. The WSSA also comes with Automated Vulnerability Detection System (AVDS) focus is accuracy. A problem in web application scanning is the 'false positive. There are many scanners that give a long list of possible vulnerabilities but on further investigation it can be found that some of these are not actually present. The technology used does the testing based on the behavior instead of version checking. Testing behavior of a host is like penetration testing. Checking the version number and using that to assume vulnerability is present is inaccurate. For more information on these two testing methods
At the same time, some scanners have a false positive rate of 10%. Most of them have 3%. AVDS is at .1%. This low rate means reduced time spent looking for problems that are reported but do not actually exist. It also increases confidence that the vulnerability report is accurate and that repair and remediation action is truly required.
This scanner is a paid version but comes with a 15 days trial.
Beyond Security also provide an online website scanner which provides the vulnerability report in a very detailed and can be understood easily even by a normal person. The scan reports are pretty fast and accurate and all this service comes free and if interested, you can also upgrade your account by paying some. The first step would be, entering your website
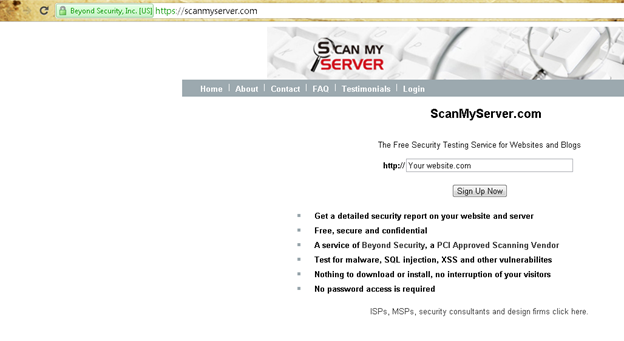
Step 2: Enter the email id which is related to the domain name.
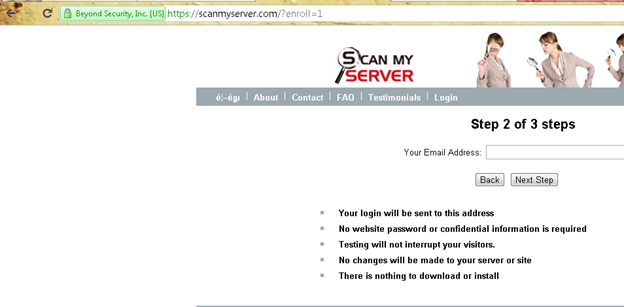
Once done, you will be getting the detailed report about the domain to the email address which you have specified. This online service can detect almost all the vulnerabilities like poorly coded web pages, database connections that have issues, Examples are: SQL injection, XSS (cross site scripting), Remote File Inclusion, PHP/ASP Code Injection, Directory Traversal and File Disclosure.
With this service, we can also identify the results of an attack by a virus, trojan or worm. Example: malicious code may open a TCP port for unauthorized access from the internet.
System mis-configuration. Example: a service using a known default user name or password; or omitted security updates/patches.
URL:
N-Stalker
URL:
http://www.nstalker.com/products/editions/free/
N-Stalker Web Application Security Scanner is a Web security assessment tool. It incorporates with a well-known N-Stealth HTTP Security Scanner and 35,000 Web attack signature database. This tool also comes in both free and paid version.
Before scanning the target, go to "License Manager" tab, perform the update. Once update, you will note the status as up to date.
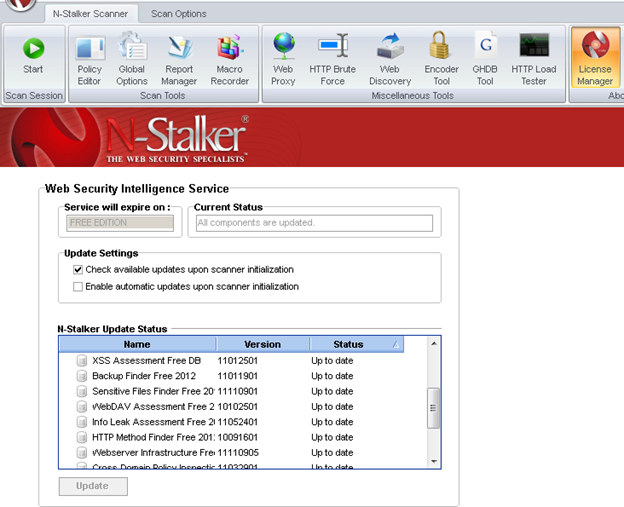
Now goto "Scan Session", enter the target URL.
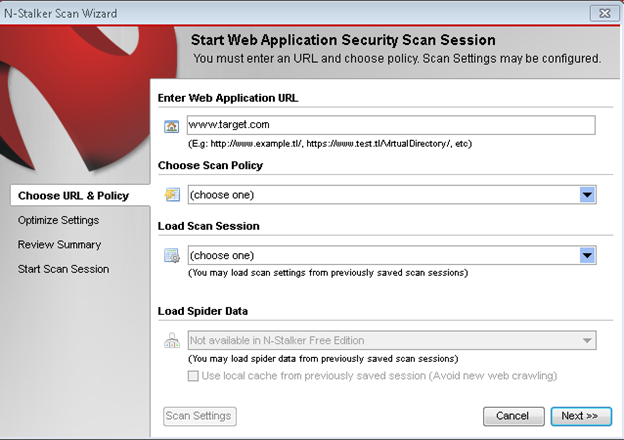
In scan policy, you can select from the four options,
- Manual test which will crawl the website and will be waiting for manual attacks.
- full xss assessment
- owasp policy
- Web server infrastructure analysis.
Once, the option has been selected, next step is "Optimize settings" which will crawl the whole website for further analysis. In review option, you can get all the information like host information, technologies used, policy name, etc.
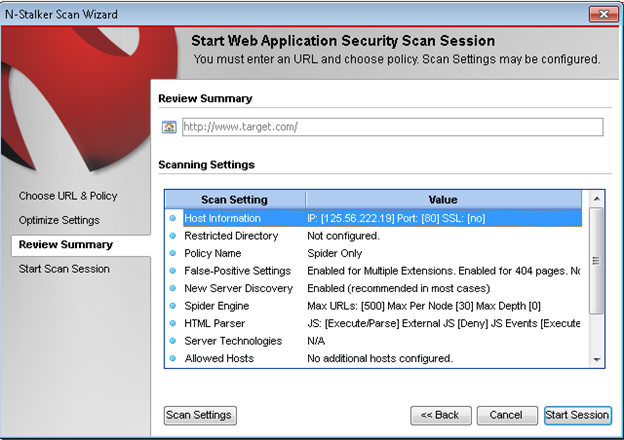
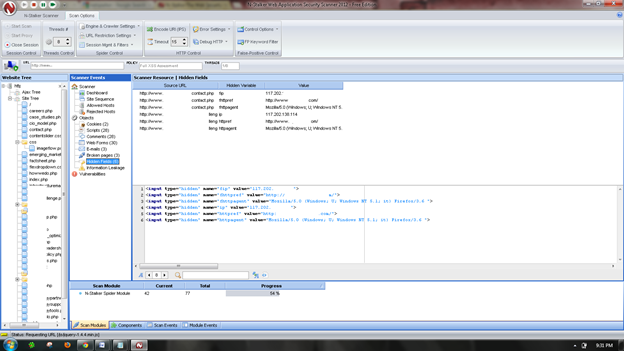
Once done, start the session and start the scan. The scanner will crawl the whole website and will show the scripts, broken pages, hidden fields, information leakage, web forms related information which helps to analyze further.
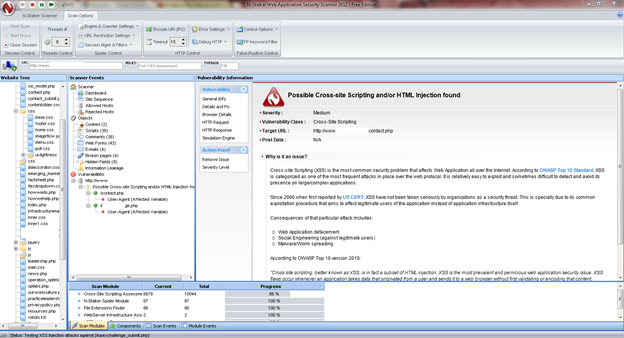
Once the scan is completed, the NStalker scanner will show details like severity level, vulnerability class, why is it an issue, the fix for the issue and the URL which is vulnerable to the particular vulnerability?
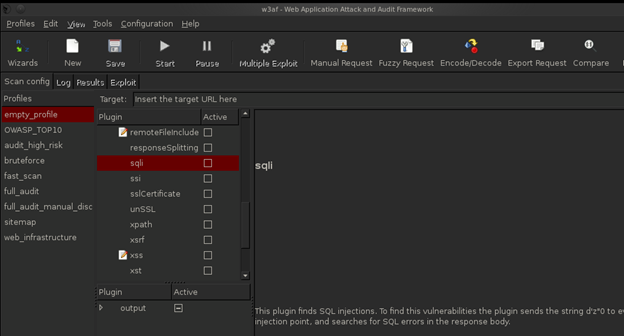
W3af:
W3af is another famous open source web application auditing and attack tool. It's basically divided into various modules like attack, audit, exploit, discovery, evasion, brute force, and mangle which can be used accordingly. These modules in w3af comes with various sub modules like for example, we can select sqli option in Audit module if we need to perform a particular type of auditing.
The below diagram shows a brief flowchart of the target website and makes it's more easy to understand.
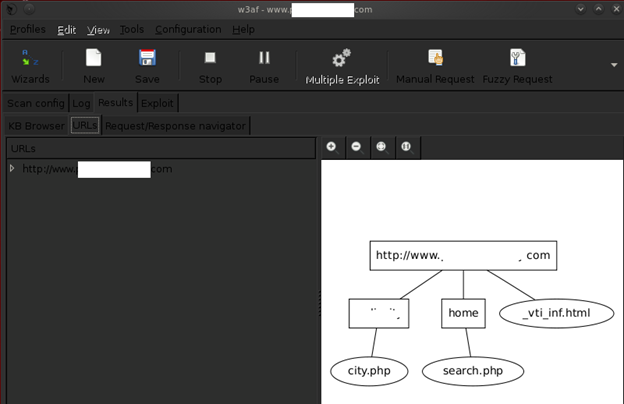
Once the scan is completed, the W3af framework shows a details information about the vulnerabilities found in the target website which can be compromised accordingly for further exploitation.
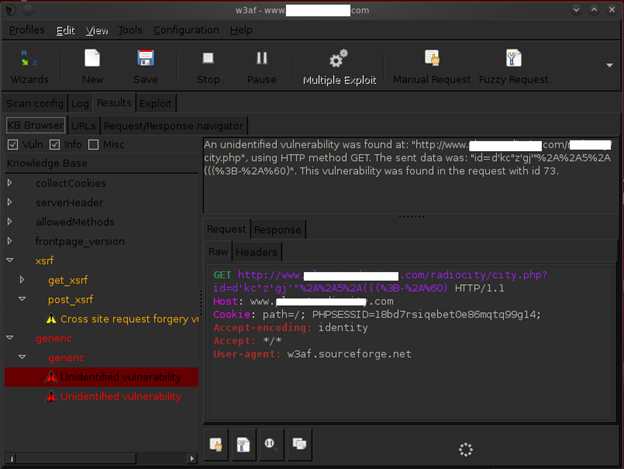
Once the vulnerability is found, we can configure the plugins in the "Exploit" tab and perform further attack which can help us to get a webshell in the target site. Another major advantage is W3af also comes with MSF for taking the attack to next level.
Acunetix:
Acunetix is another famous website vulnerability scanner. It comes in both free and commercial version. To download the scanner, signup in their website and you will be getting the download link. The drawback in the free edition, we cannot perform a full web vulnerability scan.
To perform the scan, click the "New Scan" option and enter the target website.
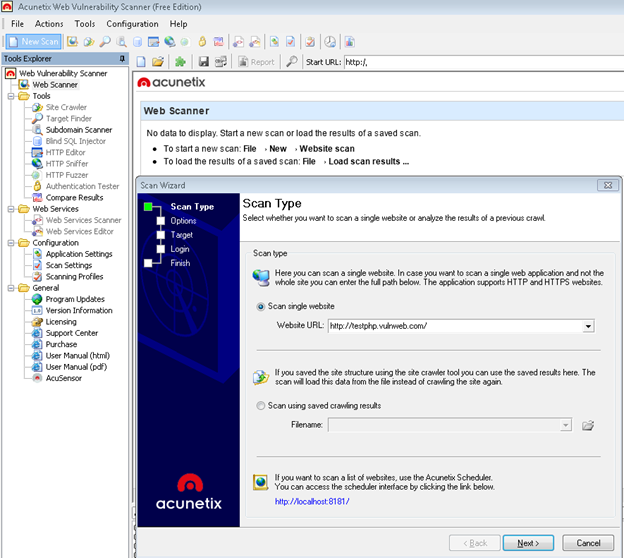
Once the target site is selected, the next step is where you can select the scan profile. This option really saves the time while performing a vulnerability scan. If you want to perform a specific scan like for example Blind sql injection, the scanner would test only for Bsqli rather than performing other scan tests.
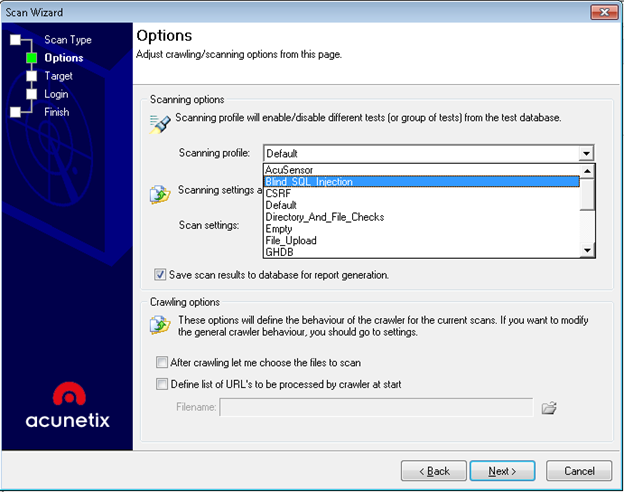
Once the profile is selected, next option is where are you will get options like the details of the website and the technologies used by the target website.
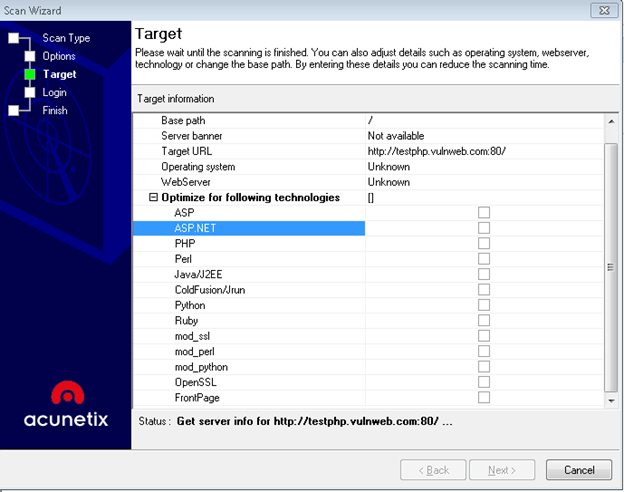
Once the details are done, click the next button and perform the scan. The scan time will depend on the size of the website. For example, if the website is small, then the scan would complete in less time period.
.
Conclusion:
There are many other scanners too in the market which is good and open source and the only thing which makes them stand out is the efficiency and changes of less false positives. Also the difference between the free edition and commercial version of scanners have many limitations and commercial version of scanners have a better sensors, exploit package but all these come in a high price which is one of the negative point.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
While getting a scanner, always do some research on the market in order to understand which is better, efficient, less damage causing to the website as well as network, etc. My all time favorite is scanmyserver.com which gives a simple and easy to understand as well the recommendations for the vulnerabilities are easy to follow.







