Threat Hunting – Zyklon Trojan
This is a lab that is conducted in a test bed. The resources were downloaded from malware.trafficanalysis.net. The samples provided came from a case study of a specially crafted pcap file from possibly an Office workstation that was a victim of a Malware attack.
Scenario
We have been provided a pcap, which is uniquely crafted for this exercise. Remodeling has been made to have more details covered by not only one but many endpoints. Previously, we have covered pcap where only one host was involved as a source. The aim to uncover remains the same. However, there are a few simple techniques which will help reduce the time in figuring out the suspicious host when working with multiple endpoints. There are certain assumptions we can make from other hosts, as they might be virtual machines sharing the same host.

FREE role-guided training plans
Below are links where you can download "pcap" for this exercise:
http://www.malware-traffic-analysis.net/2017/07/22/index.html
SHA-256 - 43f87c33d074b95d4b7b1dec96eea07172e39771790200e76e2a97b5d1e8c45f
Investigation
Before we begin the investigation to simplify the process, we map out the endpoints we will be working on. To do this go to Statistics à Endpoints.

This will list down all the IP addresses we know we are working with. This could narrow down our research for the internal and external ones. This can also help in primarily analyzing the data transfers and then roll out the possible suspicious traffic based on the packets transmitted or received. You can also use different types of endpoint types, e.g., Bluetooth, NCP, IEEE 802.11, USB, etc. with given drop-down menu at the bottom right corner.

We will use it in this case and observe few clues about the internal IP address scheme. We need to apply the filter based on highest bytes of data transferred. There are also many large packet external communication involved, the possibility of command and control center communication and multiple internal host communications.

The internal addresses scheme is "172.16.0.0" series. Below are the internal IP addresses involved. We will shortlist them for further investigation and move ahead.

However, if we consider the IP addresses observed, we see large transmissions and reception from only a few of them. Investigating the internal IP scheme, we will start with the ".pcap" file.

We find a couple of DHCP handshake requests from the DHCP server to the victim. The client-server communication happens in 4 phases which are "Discover, Offer, Request, and Acknowledge." They are pretty much self-explanatory. For further details you can refer below reference link:
To ease out the investigation based on the endpoint, we flag down some malicious internal IPs.
Critical Internal IPs we observed:
172.16.45.52
172.16.45.98
172.16.45.172
The IP addressed flagged based on the number of "http requests" made from them. This will help us on our job to hunt down the malicious host. Let's start by identifying what these hosts are.



We move ahead with identifying what these hosts are:
172.16.45.52 à Windows 7 Operating System based on the Windows NT 6.1

172.16.45.98 à Windows XP Operating System based on the Windows NT 5.1

172.16.45.172 à Samsung SM-G53P Android Lollipop.

Device identification has been completed, and now we are aware of their nature, and we can start by looking at the traffic now. A quick upload on Packet Total shows no sign of any suspicious activity on any of the flagged host.

However, virus total shows some alerts with its signatures for Snort and Suricata. What does Snort alert say:

What do Suricata alerts say for our pcap makes certain about the Zyklon malware? This must be manually analyzed and makes our job easier if we know what kind of behavior a Zyklon CnC demonstrates. :
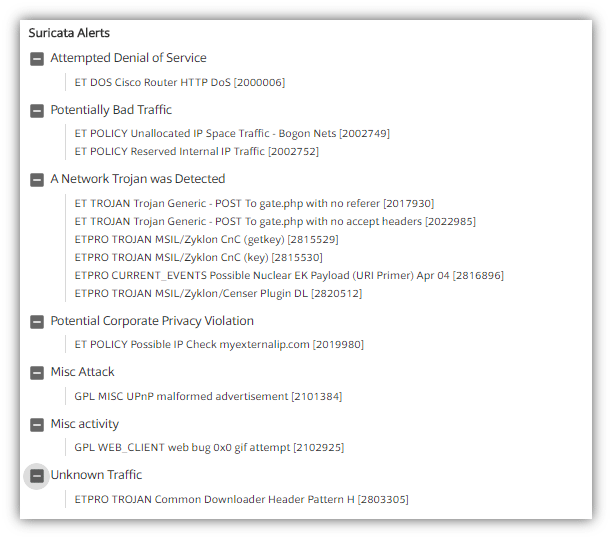
Comparing both the outputs we can say Suricata has made an excellent attempt to pinpoint us in the right direction with critical threat detector which is "ETPRO TROJAN MSIL/Zyklon CnC (key)."Yes, we have a clue now, and we can proceed with the IP "172.16.45.98".The specific reason behind choosing this IP is that there is a noticeable number of requests from this host to multiple external entities.

The first request is to Microsoft controlled domain for fetching the "ncsi.txt" file. This is a windows machine to verify connectivity of the machine. It then performs a DNS lookup for www.msftncsi.com. Then it requests a file named "ncsi.txt" which has contents "Microsoft NCSI."If the response is 200 OK with proper text then the process is completed and operating system analyses status as online.

The next request is to a domain "myexternalip.com" where a couple of scan engines have flagged it as a malicious. Community tab section also reveals some of the important information that the website is also identified in ransomware and phishing website listings.


Follow tcp stream did not indicate a clear indication of a threat or any JavaScript request for any other domain. We will flag this domain since the subsequent requests were all made to a vulnerable domain and "myexternalip.com" might be the landing page for that malware.

More than a few requests are made to "service.tellepizza.com." The domain has been shut down, and the post request is only made top gate.php this makes it more doubtful. A quick look at VirusTotal indicates it been vulnerable with malware infections.

Flagging this URL, we move ahead with following the TCP request. There is pattern observed where the "gate.php" request from a malicious domain with "Expect" header. This header is used when a server behavior is required by the client. In our case, it expects a "100-continue," and then there is a data transfer, which looks to be base 64. However, everything seems to be gibberish.


The data exchanges took place for a long time indicating a command and control center communication established successfully and performed an exfiltration activity.

We have determined an infection and Command and control center, but we are still unsure what these alerts are for and what type of malware is it. The Networktotal website came to rescue here where uploading the pcap made our alerts translate to a Zyklon CnC malware infection. The alert indicated a parameter key and getkey which is visible in our tcp request and packets.
`
What is Zyklon?
Zyklon malware was observed in 2016 and targeted mainly financial services and telecommunication's organizations. The malware comes in a ".zip" file with a ".doc" attachment which makes antivirus system fail against the zip files. The files can be sent through many of the phishing mail campaigns or remote hosting. The code is inside ".doc" with DDE-Auto which will execute the macro code as soon as the document is opened. The code might come in 2 levels with the result of executing a power shell script on the remote server. They leverage 2 vulnerabilities CVE-2017-8759 and CVE-2017-11882.
Once the installation is progressed and completed the malware retrieves the external IP address of the system by visiting below URLs:
- api.ipify[.]org
- ip.anysrc[.]net
- myexternalip[.]com
- whatsmyip[.]com
The communication now proceeds with the POST requests to the server; they might sometimes be proxied using TOR. The C2 server is appended to the "gate.php" and saved in file memory. There is also a base-64 encoded RSA public key.
Everything is as per the flow we observed, and we can now confirm the infection and prepare a summary report for the higher management.
Conclusion:
Infected Machine Details:
Hostname: MEAN-GENE-PC
IP Address: 172.16.45.98
Infection Time and Date: August 22, 2017 (08 Hrs: 13 Mins: 34 Sec)
Operating System: Possibly Windows XP.
Malicious Files Downloaded: "Zip" containing "doc" where the name may include (doc.doc, doc.txt, pause.ps1 accounts.doc Courrier.doc, words.exe)
Malicious Domain Observed:
- myexternalip.com
- service.tellepizza.com
Domain Registered Countries:
- Germany – Sachsen - Falkenstein
- USA– New York - New York City
Malware Variants Downloaded: Zyklon Malware
Malware Impact:
It does the following:
- Detects and decrypts the license/serial keys of more than 200 popular pieces
- Recover PC Gaming software keys from various games
- FTP password recovery from the FTP applications
- Passwords from popular web browsers
Md5 Signatures:
- 76011037410d031aa41e5d381909f9ce
- 4bae7fb819761a7ac8326baf8d8eb6ab
- eb5fa454ab42c8aec443ba8b8c97339b
- 886a4da306e019aa0ad3a03524b02a1c
- 04077ecbdc412d6d87fc21e4b3a4d088
Possible Exploited Software:
- Microsoft Office Documents
- PowerShell
- Microsoft .NET framework.
Signatures Triggered:
- ET POLICY Possible IP Check myexternalip.com
- ETPRO TROJAN MSIL/Zyklon CnC (key)
- ET POLICY Unallocated IP Space Traffic - Bogon Nets
- ETPRO TROJAN MSIL/Zyklon CnC (getkey)
- ET TROJAN Trojan Generic - POST To gate.php with no referrer
Recommendations:

FREE role-guided training plans
There are various techniques by which an organization can defend itself. This Includes all the following:
- Making use of both IDS and IPS technologies for data packet level analysis;
- Deploying firewalls and routers;
- Running up-to-date security features of any software package that is used;
- Getting the latest software updates and installing on them;
- Understanding how malware works via security awareness training programs;
- Limiting user privileges;
- Using caution with attachments and file transfers;
- Being vigilant when clicking on links to web pages;
- Avoiding downloading pirated software;
- Creating and implementing strong passwords.
References:
- https://packettotal.com/
- https://www.w3.org/Protocols/rfc2616/rfc2616-sec14.html
- https://virustotal.com
- https://pastebin.com/d4EpJQgR
- https://networktotal.com
- https://www.fireeye.com/blog/threat-research/2018/01/microsoft-office-vulnerabilities-used-to-distribute-zyklon-malware.html
- https://sensepost.com/blog/2017/macro-less-code-exec-in-msword/
- https://www.cyber.nj.gov/alerts-and-advisories/20180118/zyklon-campaign-targets-telecommunications-insurance-and-financial-services
- https://www.netmanias.com/en/post/techdocs/5998/dhcp-network-protocol/understanding-the-basic-operations-of-dhcphttps://www.webopedia.com/TERM/Z/zyklon-malware.html
- http://whois.domaintools.com







