Snort Session Sniping with FlexResp
Exercise 1: Packet Sniping
FlexResp is a keyword used within Snort to snipe or tear down existing connections. The resp keyword is used to close sessions when an alert is triggered. In Snort, this is called flexible response.
Flexible Response supports the following mechanisms for attempting to close sessions:

What should you learn next?
rst_snd Send TCP-RST packets to the sending socket
rst_rcv Send TCP-RST packets to the receiving socket
rst_all Send TCP_RST packets in both directions
icmp_net Send a ICMP_NET_UNREACH to the sender
icmp_host Send a ICMP_HOST_UNREACH to the sender
icmp_port Send a ICMP_PORT_UNREACH to the sender
icmp_all Send all above ICMP packets to the sender
These options can be combined to send multiple responses to the target host.
Let's build a Snort rule to alert on the cmd.exe banner.

It is highly unlikely that a legitimate host would send this connection out over any port other than FTP or Telnet. Let's use the string "Microsoft Windows [Version 6.3.9600]" as the content to watch for. We will want the rule to be of type alert so that a FlexResp option can be added to the rule. Open the local.rules file in a text editor as root.
sudo gedit /etc/snort/rules/local.rules
Add the following rule as a new line on the bottom:
alert tcp $HOME_NET !21:23 -> any any (msg:"CMD.EXE Banner"; content:"Microsoft Windows [Version 6.3.9600]"; sid:1000015; rev:1;)
Let's test this rule and make sure that it triggers before enabling any intrusion prevention action. Save the file and start Snort in IDS mode:
sudo snort -A console -q -c /etc/snort/snort.conf -i eht0
Remember where we have seen this banner before? Correct, when we were using ncat to connect to the Windows Server 2012 R2. And, we had it listening on port 999, so this should be perfect for testing our rule. You may still have the ncat listener open from the previous lab. If you closed it, open a command shell on your Windows Server 2012 R2 VM, change to the ncat directory, and start the listener again on port 999:
cd
ncat –l –p 999 –k –e cmd.exe
Now go to Kali Linux and connect to the listener from a terminal shell:
ncat 192.168.x.x 999
Check your Snort output. You should see an alert.
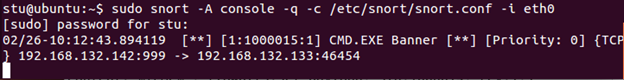
Stop Snort (Ctrl+C). Now we can enable the FlexResp option to our alert. It is quite easy: simply add a resp keyword to our alert to send out the TCP RSTs:
alert tcp $HOME_NET !21:23 -> any any (msg:"CMD.EXE Banner"; content:"Microsoft Windows [Version 6.3.9600]"; resp:rst_all; sid:1000015; rev:1;)
Save the file. Time to test it out. Start Snort again, then go to your Kali Linux ncat prompt, hit Ctrl+C to break the connection, then re-issue the command. The session will be immediately terminated.
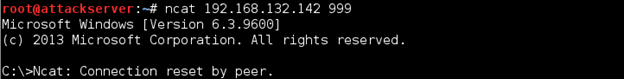
Exercise 2: Protocol Sniping
In Exercise 1 we terminated any suspicious command shells for Windows 8.1/Server 2012 R2. But what if the attacker compromised a computer running Windows 7? Or what if we want to respond to an activity that involves the legitimate use of cmd.exe? In some cases, we will want to block protocols from being used on the network rather than look for a system-specific content.
Remember our rule for detecting unauthorized file transfers from FTP server? In this exercise, we will use FlexResp to not only detect, but respond to such activity. For this, we will need to look deeper into client/server communications.
On your Ubuntu Server VM, launch Wireshark as root from a terminal shell (sudo wireshark). Start capturing traffic on eth0. Now go to your Kali Linux and connect to the FTP server running on the Windows Server 2012 R2. Remember, login credentials are infosec/password$$$. Once logged on, download the testfile.txt with get, then try uploading it with put (you will get a permission error, but that doesn't matter for our purposes). Enter exit to close the connection. See below for the complete sequence of commands.
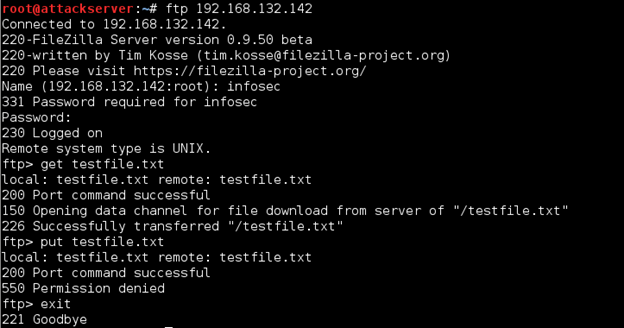
Go to your Ubuntu Server VM and stop the Wireshark capture. Apply the following filter to the results, to only show communications between our FTP server and client (x.x is the Kali Linux IP, and y.y is the Windows Server 2012 R2 IP):
ip.addr==192.168.xx && ip.addr==192.168.y.y
Look through the list of packets. You will see the RETR request and the STOR request further down.
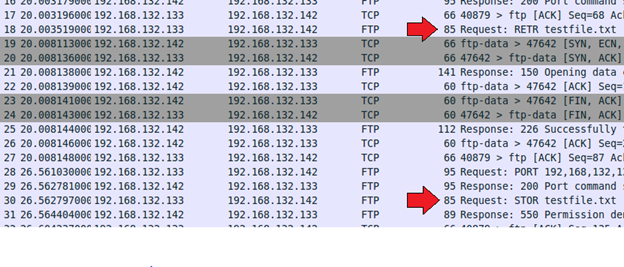
These are raw FTP commands for retrieving a file (RETR) and uploading (storing, STOR) a file to an FTP server. They are standardized, meaning that they will be the same regardless of the system/application used. Which makes them perfect for our rule. In our local.rules file, find the "Unauthorized File Download" rule (sid:1000013) and edit it as follows (x.x is your Ubuntu Server IP, y.y is your Windows Server 2012 R2 IP address):
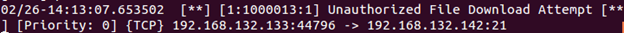
alert tcp !192.168.x.x any -> 192.168.y.y 21 (msg:"Unauthorized File Download; content:"RETR"; resp:rst_all; flowbits:isset,logged_in; sid:1000013; rev:1;)
Save the file and start Snort in IDS mode. From your Kali Linux VM connect to the FTP server again as we did earlier and enter get testflie.txt to download it. Now try downloading a different file: get hashes.txt. The connection is closed now.

Our rule detected file download and terminated the session.

FREE role-guided training plans
Maybe you can find a way to make this rule better?







