Setting Up a VPN-Based Penetration Testing Lab
Introduction:
In today's information security training, time and location is one of the crucial elements for the attendees. Many tend to choose a flexible training program that can be attended right from their home. Some organizations have already taken some advancements by providing online training and labs that are accessible from anywhere in the world using Virtual Private Network(VPN). If you have ever wondered how they could set up such lab which is flexible and accessible from anywhere in the world if you are connected to the Internet, you are at the right place. This short e-book is an attempt to explain the step-by-step process to set up a VPN based penetration testing lab using Virtualbox and pfSense. By the end of this book, you will have the following VPN based lab set up for practicing penetration testing.


What should you learn next?
Virtualbox is chosen to simulate the whole setup within one system. When you do it in the real world, you may also choose other options such as VMWare ESXi.
What is VirtualBox?
"Oracle VM VirtualBox (formerly Sun VirtualBox, Sun xVM VirtualBox and Innotek VirtualBox) is a free and open-source hypervisor for x86 computers from Oracle Corporation. Developed initially by Innotek GmbH, it was acquired by Sun Microsystems in 2008 which was in turn acquired by Oracle in 2010.
VirtualBox may be installed on some host operating systems, including Linux, OS X, Windows, Solaris, and OpenSolaris.
It supports the creation and management of guest virtual machines running versions and derivations of Windows, Linux, BSD, OS/2, Solaris, Haiku, OSx86, and others, and limited virtualization of OS X guests on Apple hardware."
Source: https://en.wikipedia.org/wiki/VirtualBox
VirtualBox can be downloaded from the following link.
https://www.virtualbox.org/wiki/Downloads
Download an appropriate version of VirtualBox software for your host machine and install it. This is required to be done before we proceed to the later sections.
What is pfSense?
"pfSense is an open source firewall/router computer software distribution based on FreeBSD. It is installed on a physical computer or a virtual machine to make a dedicated firewall/router for a network and is noted for its reliability and offering features often only found in expensive commercial firewalls. It can be configured and upgraded through a web-based interface and requires no knowledge of the underlying FreeBSD system to manage. pfSense is commonly deployed as a perimeter firewall, router, wireless access point, DHCP server, DNS server, and as a VPN endpoint. pfSense supports the installation of third-party packages like Snort or Squid through its Package Manager."
Source: https://en.wikipedia.org/wiki/PfSense
pfSense firewall can be downloaded from the link below.
https://www.pfsense.org/download/
Installing pfSense in Virtualbox:
Launch virtual box and click "New" to create a new virtual instance.

pfSense is based on BSD. So, when creating the new virtual machine, select type as "BSD" and version as "FreeBSD (64 bit)". This is shown in the following figure.
Allocate 512 MB RAM for pfSense.

You can specify 6 GB hard disk space for pfSense. Then Choose "Hard drive file type" as "VDI." Check "Dynamically Allocated" for storage on the physical hard drive. All the settings mentioned above are as shown below in the following screenshot.

Finally, click "Create."
Now, we should have a new virtual machine instance. Select the VM instance and click "Start."

It will ask for the source image. Choose the live CD you downloaded in the beginning.
Once after choosing the Live CD, click "Start" as shown in the figure below.

We should now see the following screen.

When the above screen pops up, hit enter. It will automatically take you to the next screen as shown below.

Now, we are greeted with various options.
If you want to install the pfSense instance rather than booting it as live CD, we can simply type "I" and hit enter before the timeout.
So, it will invoke the pfSense installer as shown below.

Choose "Accept these Settings" and hit enter.

Then choose "Quick/Easy Install" and hit enter.

After reading the above warning, if you are OK with the installation, choose "OK" and press enter.

The installation will take time to process as shown in the figure above.

When you see the above screen, just choose "Standard kernel" and hit enter.

Once you are done with the installation, you should see the above screen. Choose "Reboot" and hit enter.
Congratulations! You just completed pfSense installation.
Once you are done with the installation, remove the image file so that vdi file will be used from the next reboot.
Following are the steps to do it.
Navigate to the pfSense VM and then click on Storage. You should see the following screen.

Now, choose the image file and give a right click as shown in the figure below.

Once after removing the attachment, you should see the following window.

If you boot pfSense now, the vdi file will be loaded, and any changes that are made to this disk will now persist.
Configuring the network interfaces for pfSense:
This section covers the network configuration for the pfSense virtual machine. This configuration is important to simulate the public users and internal machines.
Select pfSense VM and navigate to settings->Network->Adapter 1 and then choose Bridged Adapter as shown below.

This will ensure that any device that is connected to the Wi-Fi network will act as a public user. When you do it in the real world, this interface has to be replaced with a public IP address.
Now, navigate to settings->Network->Adapter 2 and then choose Internal Network as shown below.

This will ensure that any machine that is connected to the Internal Network adapter will be directly connected to the LAN side of the pfSense instance. The machines in the network are treated as internal machines that are going to be accessible to the public via the VPN tunnel.
With this, we have completed all the required settings before booting the pfSense virtual machine.
Assigning IP addresses to pfSense:
After finishing the installation and network settings in the previous steps, it is time to boot your pfSense for the first time and assign IP addresses to the network interfaces we have configured earlier.
Boot your pfSense instance, and you should see the following screen.

Press F1 and you should see the following screen showing the IP addresses for both the interfaces.
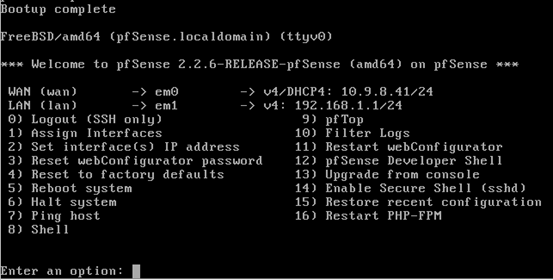
As you can see in the above figure, the IP addresses for both the interfaces have been automatically assigned. The IP address on WAN interface is assigned from the router's DHCP server. Let us change the IP address of the LAN interface to a different series.
When you are on the above screen, just enter 2 to select "Assign Interfaces." Then, we should see the available interfaces as shown below.
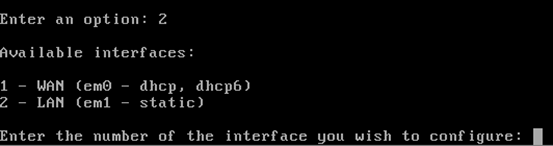
Since we are going to configure the second interface, we will choose "2" again. This should allow us to configure the private interface, which is em1 (LAN).
We will then be prompted for the LAN IP address. In our case, let's provide 10.1.1.1 as the new IP address.
Now, let us hit enter. We will be prompted for the subnet mask bit count.
Enter 24.
All these steps explained so far are shown in the screenshot below.
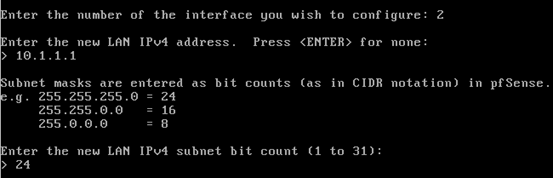
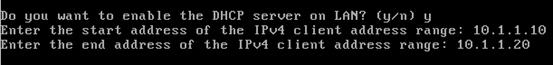
Hit enter 3 times to get the screen to configure DHCP service for private LAN.
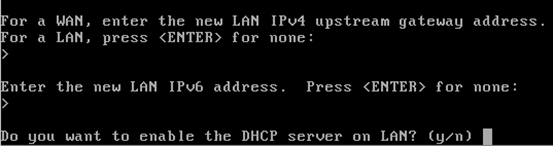
When you see the above screen, enter "y" and hit enter. Then, we need to enter the range of IP addresses. Depending on the number of internal systems in your network you may give a specific range of IP addresses. In our case, we are giving from 10.1.1.10 to 10.1.1.20
This is shown in the figure below.
Once done, hit enter and type "Y" again to have webconfigurator for pfSense configuration from a GUI and then hit enter.
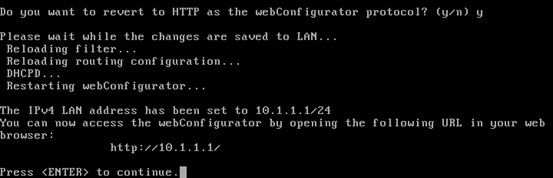
We should see the above screen with the URL where we can access the Graphical User Interface for pfSense configuration.
Finally, hit enter to go back to the command line configuration interface, which appears upon starting pfSense.
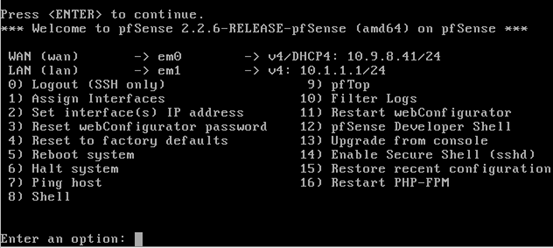
If we now observe, we should see everything set for both the interfaces.
Accessing pfSense from webConfigurator:
Till now, we have configured everything from the pfSense's command line interface. pfSense provides a nice GUI, where you can configure everything with ease. From here onwards, we will use GUI to do the remaining configuration. Let us start a new virtual machine and connect it to the internal network adapter as shown below.

Now, launch this virtual machine and access pfSense GUI web configurator using a web browser. This can be done by opening a browser and browse to the Internal adapter of the pfSense instance as shown in the figure below.

Following are the default credentials for pfSense administration console.
Username: admin
Password: pfsense
When you enter these credentials in the above screen, pfSense will run through the initial configuration as shown below.

Click "Next" when you see the above screen. You will be greeted with the following message, where you can click "Next" if you are not looking for advanced pfSense's features.

On the next screen, you will be prompted to enter DNS Server addresses. Enter the Primary DNS Server and Secondary DNS Server addresses as shown in the figure below. These are Google DNS Server addresses.

In the next screen, you can change the time zone if you want. We can leave them
to the defaults if you do not have a specific choice.

Just click "Next" till you see the following screen. You should see the pfSense's LAN IP address and subnet mask we configured earlier.

Click "Next, " and you should see the following screen. It is important to change the Admin Password here for the obvious reasons. Make sure that it is strong enough to prevent brute forcing.

Click "Next," and then you should see the following window.

This brings us to the end of initial pfSense configuration. Click "Reload" button, and you should see the following screen.

Navigate to the pfSense homepage, and you should see the Dashboard as shown in the following screenshot.

Congratulations! You have finished your initial pfSense configuration in virtual box. pfSense firewall is now ready, and we can configure it for various purposes.
Creating a Certificate Authority:
Let us see the steps to create Certificate Authority in PfSense. This is required later for signing user and server certificates. To create a certificate authority, launch Certificate Authority Manager by navigating to System | Cert Manager. This should look as follows.

In the above screen, click the + button under the CAs tab to create a new Certificate Authority. This will create a new Certificate Authority. Fill in the details as shown in the figure below.

Descriptive name can be anything the user wants (In our case, it is VPNLAB_CA) and Method should be Create an internal Certificate Authority.
Key length is 2048 bits, and Digest Algorithm is SHA256. This CA is valid for 3650 days. Finally, we have filled in the other personal details.
After filling everything, click Save, and that is all. CA will be created as shown in the figure below.

The Certificate Authority we have created can now be used to sign internal certificates we create in the next couple of sections.
Creating Server Certificate
To create a server certificate, once again we can launch Certificate Authority Manager by navigating to System | Cert Manager and then clicking Certificates tab. This should look as follows.

Similar to creating Certificate Authority, lets click + button and fill in the details of the certificate as shown in the figure below.

You may notice that we are creating an internal certificate of type Server Certificate this time and naming it ServerCert. You should also notice that we are using the previously create VPNLAB_CA as our certificate authority for this server certificate.
Next, fill in the personal details as shown below and click Save.

The above step will create a server certificate signed by VPNLAB_CA. This looks as follows.

You may notice the second entry in the above figure. Congrats! We just created a server certificate signed by our Certificate Authority.
Creating VPN users
We are done with creating the Certificate Authority and Server Certificate. We now need to create users who can use our VPN Service. Let us navigate to System | User Manager to start creating a new VPN user. This looks as shown in the figure below.

As shown in the preceding figure, click + button under Users tab. This will open up the following form, where we need to fill up the new user's details.

As we can see in the above figure, we are creating a new user vpnuserone with a password. These credentials are important and the user needs them while connecting to our VPN Server.
Here, we have a check box to create a user certificate, which will create later in this section. You can just leave all the remaining fields empty as shown below and click Save.

This will create a new user account vpnuserone as shown in the figure below.

Similarly, we can create multiple user accounts if you have more than one user connecting to your VPN Server.
Creating a VPN User Certificate
We are going to create a certificate for the user in this section. We are going to have bidirectional authentication based on certificates, meaning that the client must authenticate the server certificate and the server must authenticate the client certificate before mutual trust is established.
Both server and client will authenticate the other by first verifying that the presented certificate was signed by the master certificate authority (CA), and then by testing information in the now-authenticated certificate header, such as the certificate common name or certificate type (client or server).
Source:
https://openvpn.net/index.php/open-source/documentation/howto.html
So, let us create a user certificate by navigating to System | Certificate Manager. This looks as shown in the figure below.

Under Certificates tab, click the + button, and you should see the following screen.

Fill in the details properly as shown in the above figure. You may notice Certificate Authority field, where we are using our previously created Certificate Authority named VPNLAB_CA. This will be the CA for the user certificate too. Additionally, you may notice the Certificate Type, which is User Certificate.
Next, fill in the following details and click Save button.

This will create the user certificate as shown in the figure below.

The above figure shows that we have a Server Certificate and User Certificate both issued by the Certificate Authority VPNLAB_CA.
If you remember, we chose to leave Click to create a user certificate check box unchecked while creating the user vpnuserone. So, we are going to add this user certificate to this user now.
We can add the certificate to the corresponding user by navigating to User
Manager section once again. This looks as shown in the figure below.

Select the user vpnuserone and click e button on the right side. You should see the following.

Now, click the + button and make sure that you are under Certificates Tab. Select the method as Choose an existing certificate and choose vpnuserone certificate under Existing Certificates drop-down. Click Save and the user certificate will be added.

This will assign the certificate vpnuserone to the user vpnuserone. You can see the newly added certificate under User Certificates tab as shown in the figure below.

The same process has to be followed whenever a new user is created.
Configuring OpenVPN:
Till now, we have worked on the prerequisites needed to start working with the actual VPN Server. Now, we will configure the VPN server that will allow users to connect to our private lab virtually. To achieve this, we are going to leverage the capabilities of OpenVPN, which comes pre-installed with pfSense.
Click VPN | OpenVPN. This looks as follows.

Open Wizards tab in the above screen, and you should see the following.

Select Local User Access as Type of Server and click Next.
Next, you should see the following window. Make sure that you select the CA we created earlier under Certificate Authority dropdown and click Next.

Next, choose ServerCert, which is the Server Certificate we created earlier and click Next.

Now, we are at the most interesting part of OpenVPN configuration. Carefully follow the steps and choose your options.

We chose WAN as the interface as we are going to get our incoming VPN connections on to the WAN interface.
OpenVPN uses UDP port 1194 by default. So, we choose UDP as the protocol and 1194 as the local port.
Scroll down to see the options further.

Choose the Cryptographic
Settings as shown in the above figure.
Next, we will setup Tunnel
Settings.

Tunnel Network is the virtual network we are going to get to communicate with the physical servers in the internal network. This means when any user connects to the VPN Server, a virtual IP in the range provided under Tunnel Network field will be assigned to the user. Let us fill this as 10.1.2.0/24, so the users will get 10.1.2.x as their IP addresses.
The actual network we have set up earlier with the target machines having the IP addresses in the range 10.1.1.0/24.
Next, fill Concurrent Connections as 10. You may change it according to your needs.
Scroll down further will show us the Client
Settings as shown in the figure below.

Let us fill in the Google's DNS Server IP addresses in DNS Server1 and DNS Server2 sections as shown in the above figure.
8.8.8.8 becomes DNS Server 1.
8.8.4.4 becomes DNS Server 2.
Finally, click Next when you see the following screen.

We will now be on the following screen. Here we will add firewall and open VPN rules. Check the check boxes associated with Firewall Rule and OpenVPN rule and click Next.

Now navigate to Firewall | Rules to check if the firewall rules we have just added in the previous step are successful or not.

As we can see in the above figure, there is firewall rule added on WAN address and UDP port 1194. This means, any connection coming to the UDP port 1194 on WAN address will be accepted irrespective of source IP and port.
Finally, click Finish to complete the OpenVPN set up.

If you navigate to VPN | OpenVPN once again, you will see the following entry which shows the VPN Server configuration.

Installing additional packages
It is important to note that pfSense by default does not have some of the packages installed. However, depending on your needs, you can install the packages. For example: if you need Snort IDS, you need to install it from the Package Manager of pfSense.
Now in our case, we need to install a utility called OpenVPN Client Export Utility. This is required to export the VPN user client certificates. We need to provide these certificates to the users as users need these certificates to be able to connect to the VPN Server.
Let us do it by navigating to System | Packages. This will show us the Package Manager as shown in the following figure.

Under Installed Packages, we will have nothing by default since we did not install
Click on Available
Packages tab and search for the following utility.

Click the + button and open up Package
Installer tab.

Click Confirm in the above window and it will be installed as shown in the figure below.

Once complete, you should see the package installed as shown in the figure below.

Now, this package should be visible under Installed
Packages tab as shown in the figure below.

Nice! We are done with all the configurations and ready to connect to the VPN Server as a user. However, the user does not have the required files to connect to the server. So, let us use client export utility and export the certificate as an archive file and provide it to the user.
Navigate to VPN | OpenVPN, and you should see the following.

Click Client
Export tab.

Find the certificate you want to export (in our case vpnuserone) and click Archive link to export the certificate files.

Save the file to your machine and pass it to the user.

Connecting to the server as user
Now the user has the files that can be used to connect to the VPN server. Kali Linux is installed in Virtualbox, and it is connected via bridge network. This means Kali can reach pfSense only through pfSense's WAN interface.
Run unzip command and extract the files into your current directory.
I have renamed the file as VPN.zip to shorten the file name.

Now, navigate to the extracted folder, and you should see the following files.

Check your IP address by typing ifconfig command.

Currently, Kali Linux has two interfaces. The first one is bridged network interface and the second one is loopback address.
If we try to ping one of the machines behind pfSense, we cannot reach them. The following figure confirms it.

Now, let us try connecting to the VPN Server using the following command.
openvpn [filename].ovpn
The credentials are the same as what we setup while creating vpnuserone. So, enter the username and password when prompted.

As you can see in the preceding figure, the client is not able to connect to the server.
This is due to the firewall blocking traffic from IP addresses reserved for private networks. Since we are using a simulated network, we have a private address assigned to Kali Linux. To overcome this problem, navigate to Interfaces -> WAN in pfSense web configurator and uncheck Block private networks.

Click Save, and you should see the following confirmation prompt.
Click Apply Changes, and you should be good to go.

Additionally, you may see the following errors while connecting to the VPN Server.

When you see the above error, open up the .ovpn file that you got after extracting the ZIP file and comment out the line that starts with verify-x509-name. This is shown in the figure below.

Believe me; we have fixed all the problems. Now, let us try to connect to the VPN Server once again using the same process we have seen earlier.

If you see the message Initialization Sequence

This time, we have a new interface tun0 with the virtual IP address 10.1.2.6 as shown in the above figure. If you remember, this is IP Address from the series we have assigned to the tunnel network while configuring OpenVPN.
Now, we are virtually connected to the target private network. Pinging one of the internal machines will confirm this.

We can now start testing the target IP addresses.
Let us scan the IP address 10.1.1.10 using nmap and observe the results.

As we can see in the preceding figure, we can scan the internal machines using the VPN connection.
We can also verify who is connected to the VPN server by navigating to Status -> OpenVPN. This looks as shown in the following figure.

As you can see in the preceding figure, a machine with virtual IP address 10.1.2.6 is currently connected to the VPN Server. We can also see the Real Address of the client.
Similarly, we can add any number of target machines to improve your VPN based pentesting lab. To add a new machine, simply install it in Virtual box and add it to your Internal
Network adapter. This is shown in the figure below.

Now, boot the machine and check the IP address.
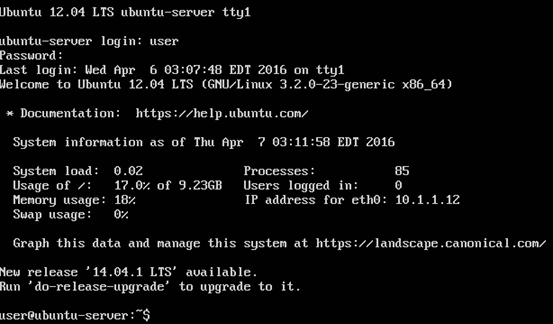
As we can see in the above figure, we have got 10.1.1.12 as our IP address to the new machine.
Once again, we can use nmap to scan this machine. This looks as shown in the figure below.

When internal penetration tests are remotely done, we use the same concepts where the client should provide us the VPN details to be able to connect and test the internal network.

FREE role-guided training plans
Conclusion:
This little e-book has made an attempt to show you how a VPN based penetration testing lab can be set up to be able to set up your network at one place and practice penetration testing from anywhere in the world. This is the trend with many training programs these days as it removes much hassle setting up the labs every time there is a training session. We can simply set up a lab once and use it forever.







