Port scanners
Port scanning is a popular reconnaissance technique which is used to discover the open ports and services available on a particular host. It can be used by the network administrator to check the open ports; it can be used by penetration tester during the security audit to check for vulnerabilities or it can be used by an attacker or a hacker to discover vulnerable service that they can exploit to break into the system. Every host connected to the LAN or internet run many services that listen on some port. By running the port scan, we can get the information like what all ports are open, what service is running on each port, what is the OS and MAC address of the target host, etc. We can configure the port scanner according to our requirement to get the maximum information from the target system.
Port scanners send a request to connect to each port sequentially and based on the response it decides whether the port is open, closed or filtered.

What should you learn next?
- Open port: The remote host sends a response to accept the connection.
- Closed port: The remote host sends a response indicating the connection is denied.
- Filtered port: There is no reply from the remote host.
There are total 65536 ports each for TCP and UDP protocol which are divided into three ranges:
- Well known ports: These ports are in the range of 0-1023.
- Registered ports: These ports are associated with certain protocols or application. These ports lie in the range of 1024-49151.
- Dynamic /private ports: Ports>49151
Types of port scanning
There are multiple port scanning techniques available. Let's look into each scan type in detail.
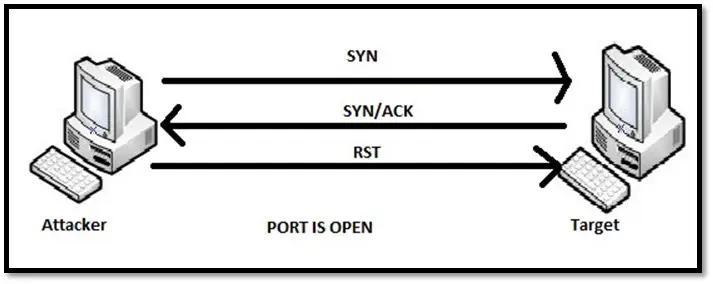
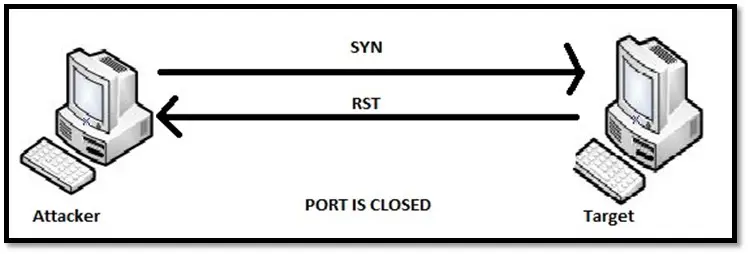
TCP SYN scan: SYN scan is also known as half-open scanning as it doesn't connect completely to the port. In this scan, the scanner sends a SYN packet to initiate a communication and wait for a response. The SYN-ACK packet from the target port indicates the port is listening i.e. open while an RST (reset) indicates the port is not listening i.e. closed.
If no response is received after multiple tries, the scanner marks the port as filtered.
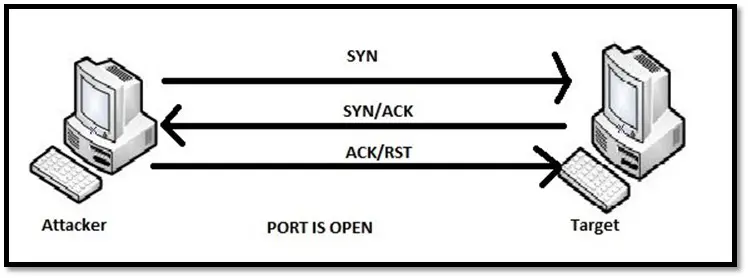
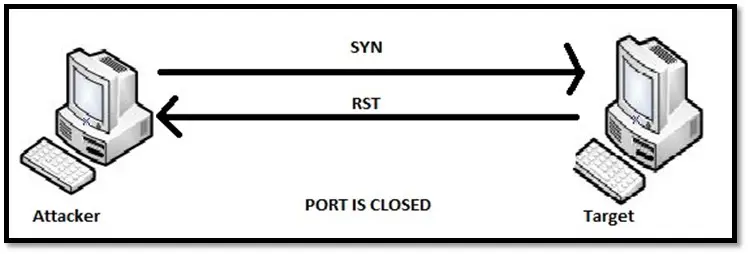
TCP Connect or Vanilla scan: In the connect scan, the OS sends the connect() system call to remote host. If the port is listening, connect() will succeed. In this scan, the attacker sends a SYN packet to the remote port. If the remote port responds with a SYN-ACK packet, that means the port is open. The scanner complete the connection by sending the ACK packet. If the port is closed the response from the remote host will be RST packet. This method is faster than other methods mentioned in this article. The disadvantage of this scan is it can be detected easily as it connects to each port.
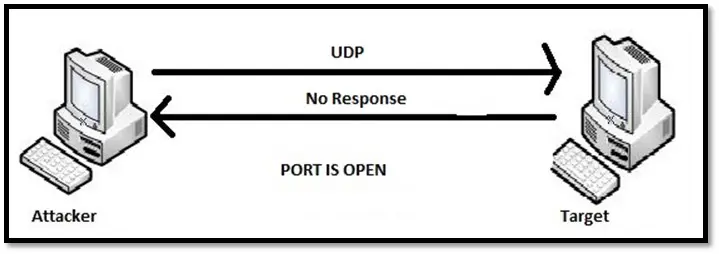
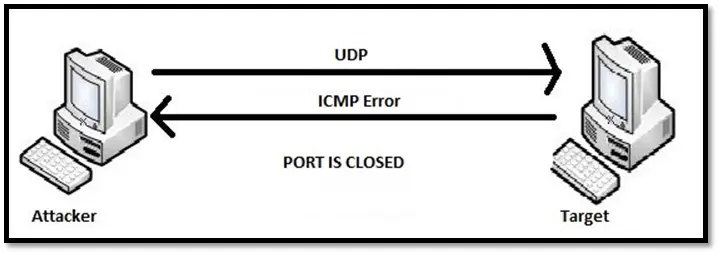
UDP scan: UDP scan sends the UDP packet to every port in the scope of the scan. The port is considered as closed if the scanner receives the ICMP port unreachable error. If the port is open, the packet is accepted, and no response packet is sent.
The major drawback of UDP scan is the scan is slow. Since there is no response from the open port, the scanner has to resent the packet multiple times leading to the delay.
ICMP scan: This is not a port scan, but it is used to ping the remote host to check if the host is up. This scan is useful when we have to check a number of live host in a network.
FIN scan: Unlike other scanning techniques, FIN scan sends a FIN packet to close a connection that is already open. The closed port will respond to FIN packet with RST while open port will drop the packet. No response from the target port can lead to the confusion whether the port is open or probe is blocked by a firewall. Hence, this scan isn't very effective.
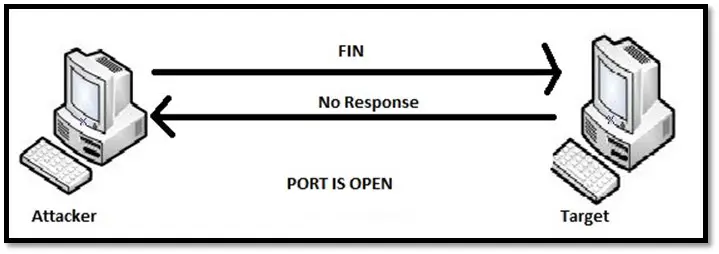
FIN scan for open port
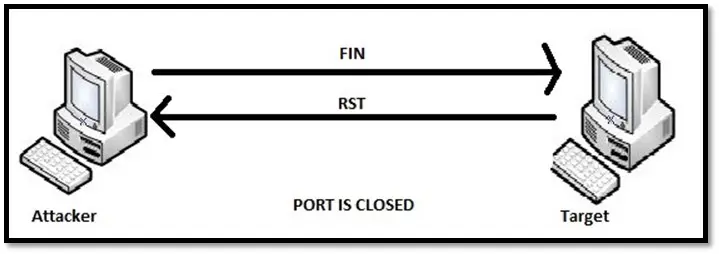
FIN scan for closed port
Other scans which are similar to FIN scan are XMAS scan and NULL scan.
XMAS scan sends the packet with FIN, URG and PUSH flag set whereas NULL SCAN send the packet without any TCP flag. If the port is closed on the target machine, it responds with RST. If the port is open, it will ignore the packet.
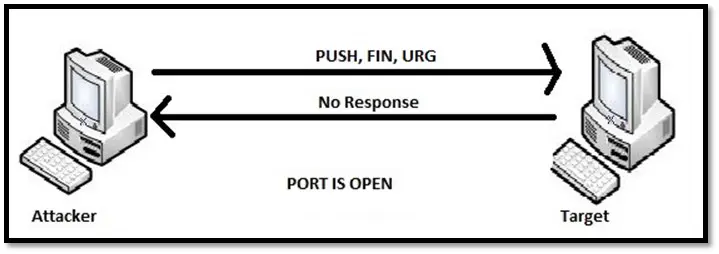
XMAS scan for open port
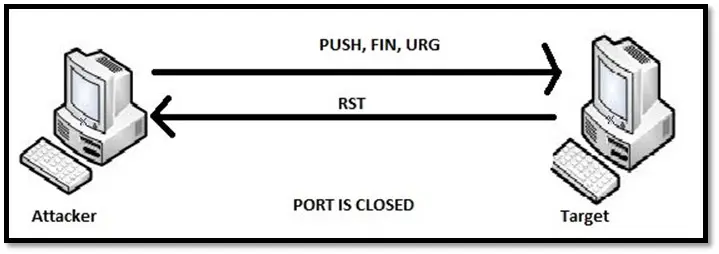
XMAS scan for closed port
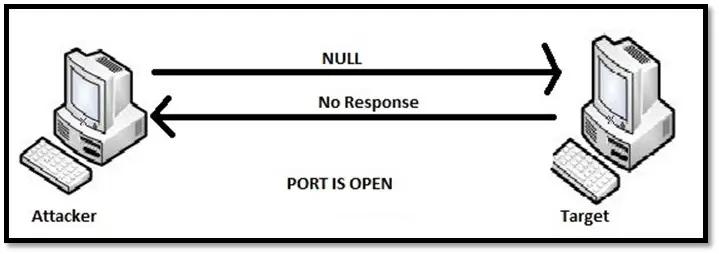
Null scan for open port
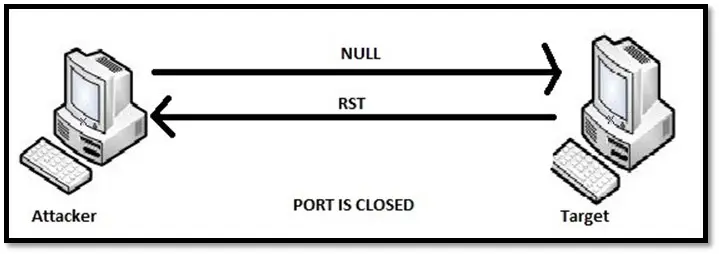
Null scan for closed port
TCP ACK scan: ACK scan is different from other scans because this scan doesn't give the list of open or closed port instead it checks if the port is filtered or unfiltered. It sends the packet with ACK flag set. If in response it receives RST that means the port is unfiltered and might be open or closed. Ports that don't respond or send ICMP error marked as filtered. This type of scan is useful to detect the presence of a firewall.
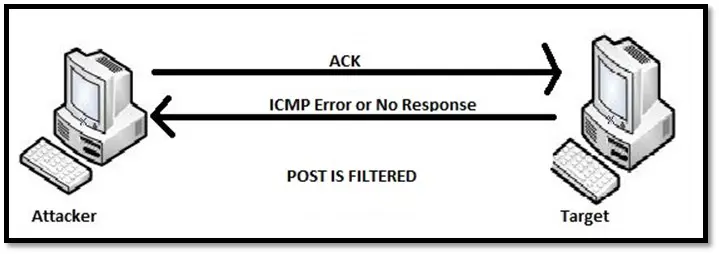
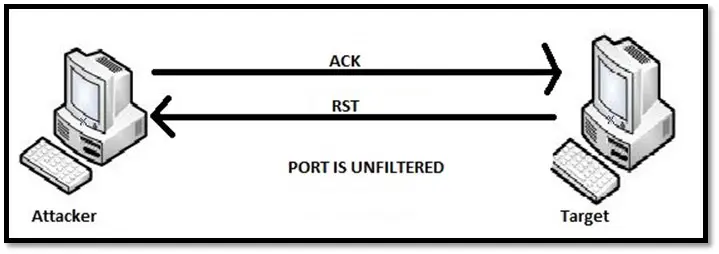
Idle scan: An idle scan is a good option when you want to keep yourself anonymous while scanning. The scan involves sending forged packet to the target host which looks like it is coming from some other host. This scan uses another host's IP address as the source IP address instead of sending attacker's machine IP address.
The idle host involved in this scan is called zombie and hence this scan is sometimes referred as zombie scan.
Let us look into the below diagram to understand how this works.
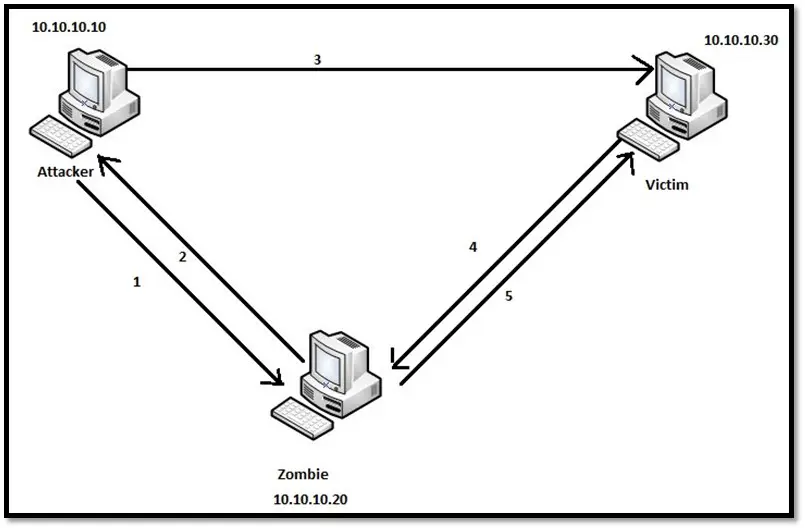
1. The attacker sends the TCP SYN packet to the Zombie, which is up and idle.
2. The Zombie responds with SYN/ACK packet with IPID 10.
3. The attacker sends the spoofed SYN packet to the victim at 10.10.10.30, with the source IP of the Zombie (10.10.10.20)
4. In the case of open port, the victim responds with SYN/ACK to the Zombie because source IP in step 3 was set to Zombie.
5. Zombie on receiving the SYN/ACK packet from the victim sends the RST packet back to the victim with IPID 11.
6. After some time, the attacker again sends the SYN packet to the Zombie host, but Zombie host was waiting for the ACK packet from the attacker as Zombie had already sent a SYN/ACK packet in step number 2.
7. The Zombie host responds with RST packet to the attacker with IPID set to 12.
8. The attacker on receiving the RST packet with IPID set to 12 knows that the remote port on the victim machine is open (Notice the increment in IPID from 10 to 12).
9. In the case of the closed port on the victim machine, the victim responds with RST packet to the Zombie.
10. Zombie won't reply back to RST packet (IPID remains 10).
11. After some time, the attacker again sends the SYN packet to the Zombie host, but Zombie host was waiting for the ACK packet from the attacker as Zombie had already sent a SYN/ACK packet in step number 2.
12. The Zombie host responds with RST packet to the attacker with IPID set to 11.
13. The attacker on receiving the RST packet with IPID set to 11 knows that the remote port on the victim machine is closed (Notice the increment in IPID from 10 to 11).
FTP bounce scan: This scan uses FTP server to port scan other hosts. FTP protocol has a feature of proxy FTP connections which allows a user to connect to one FTP server and send a file to each port of a target host. The error message from the port describes whether the port is open or closed. The advantage of this scan is being able to be anonymous as bouncing through FTP server hides the source address of the attacker. The disadvantages are that it is slow, and many FTP servers have disabled the proxy feature.
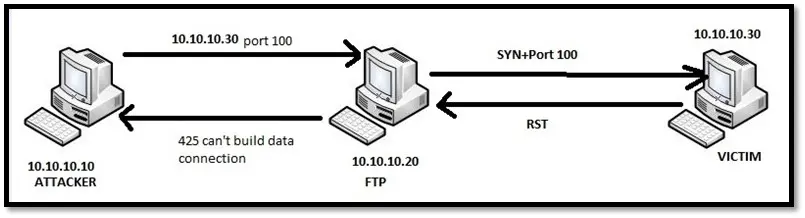
FTP bounce scan for closed port
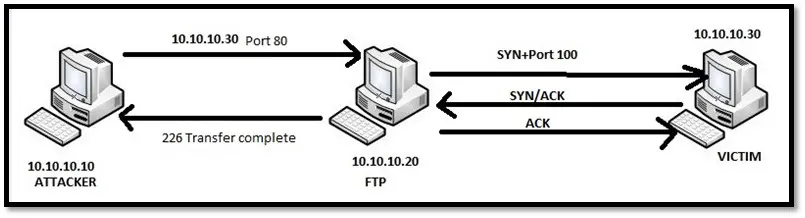
FTP bounce scan for open port
Fragmented scan: In fragmented scan the attacker sends the probe packet in small IP fragment. The idea is to split the TCP header over several packet to make it harder to detect by firewalls. The advantage of this scan is the ability to bypass the packet filters. The disadvantage is it is slow.
Strobe scan: Strobe scan is more focused scan where an attacker scans for the known port to exploit.
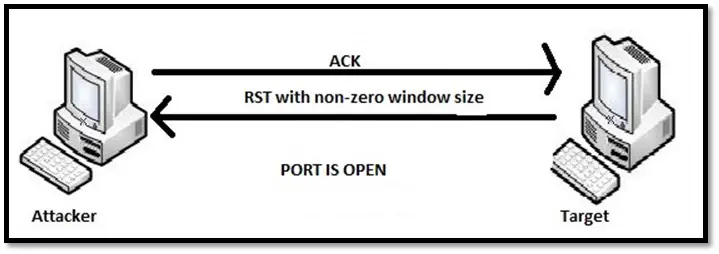
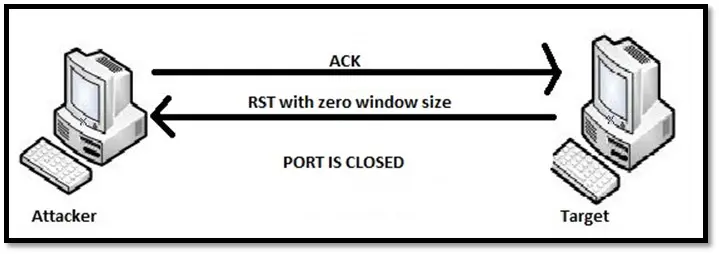
Windows scan: Window scan is similar to TCP ACK scan, but this scan can identify the open ports as well. It is called the window scan because some TCP stack provides specific window size when responding to an RST frame. When ACK packet is sent to the remote port, the open port will respond with RST packet along with non-zero window size whereas the closed port will respond with RST packet along with window size of zero.
The advantage of this scan is it generates minimum traffic and does not open a session, which makes it harder to detect. The disadvantage is that it doesn't work on all the devices.
Service fingerprint scan: Fingerprinting is a method to interpret the response to know what it is. The service fingerprint scan sends a combination of data to the remote host and based on the response it decides the service running on the remote port.
Ethical/Legal Implications
Port scanning is similar to "ringing a doorbell to see whether someone's is at home". Whether or not port scanning is ethical is a trick question. Port scanning is used by the security professional to detect the vulnerabilities, but it is also used by the hacker/attacker or malicious person for the same purpose. It is the first step in a successful attack. Normal port scanning to detect the open port and services cannot be considered as offensive but doing the same thing again and again on similar host or set of hosts belonging to the same company can be considered as illegal. If a computer system is affected by the port scan, it can be considered as an act of Denial of Service (DoS) attack, which is illegal.
Port Scanning Tools
-
Nmap: Nmap is a free tool for network discovery and security auditing. It can be used for host discovery, open ports, running services, OS details, etc. Nmap sends specially crafted packet and analyzes the response. It allows scripting and comes with a huge collection of nmap script to check for well-known vulnerabilities. Scanning results can be saved to an XML file.
Nmap can be downloaded from http://nmap.org/
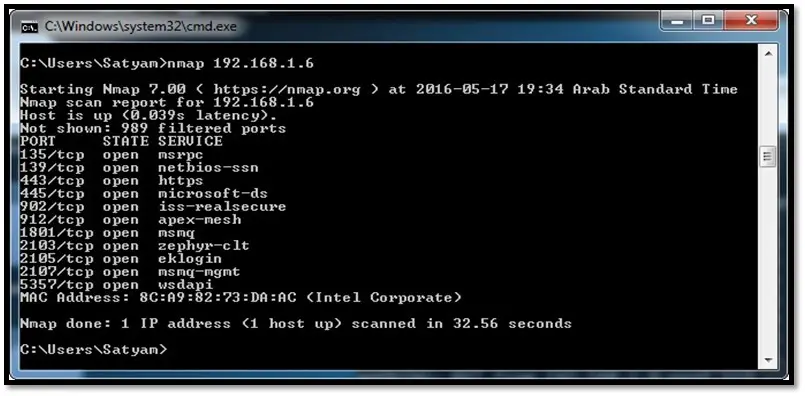
Nmap CLI
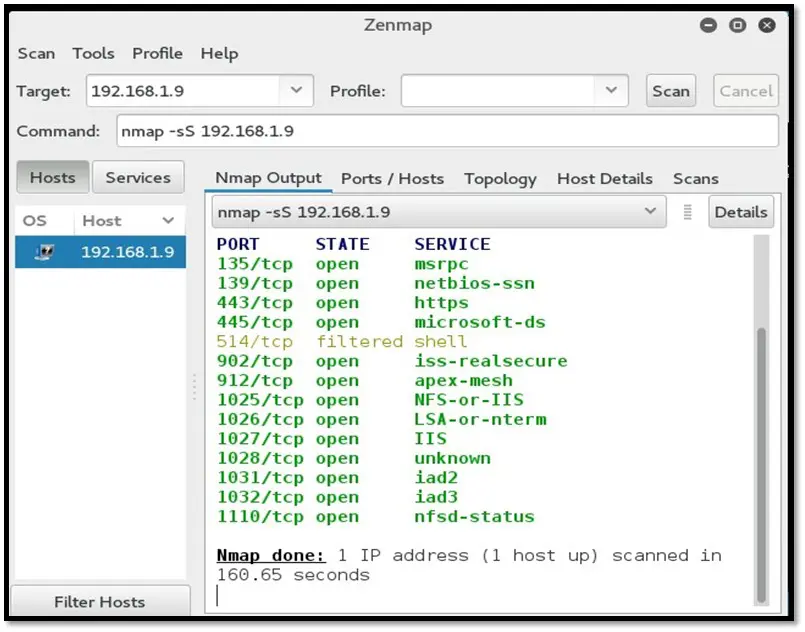
Nmap GUI
-
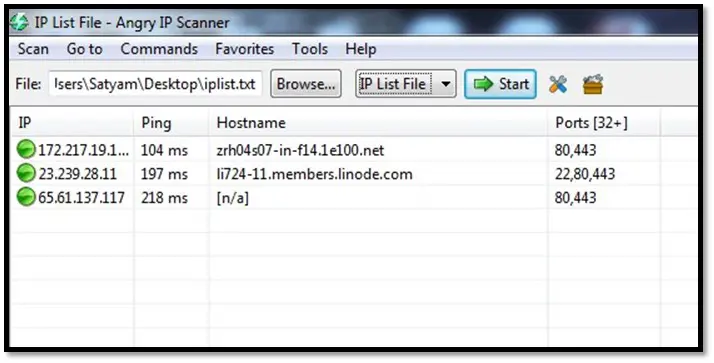
Angry IP Scanner: Angry IP Scanner is an open-source and cross-platform port scan tool. Angry IP scanner simply pings each IP address to check if it's alive, then optionally it is resolving its hostname, determines the MAC address, scans ports, etc. The amount of gathered data about each host can be extended with plugins. Scanning results can be saved to CSV, TXT, XML or IP-Port list files.
Angry IP Scanner can be downloaded from http://angryip.org/download/
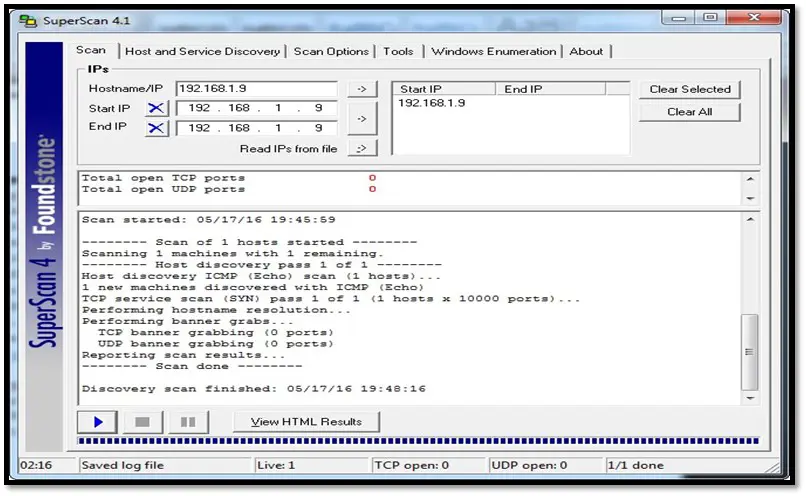
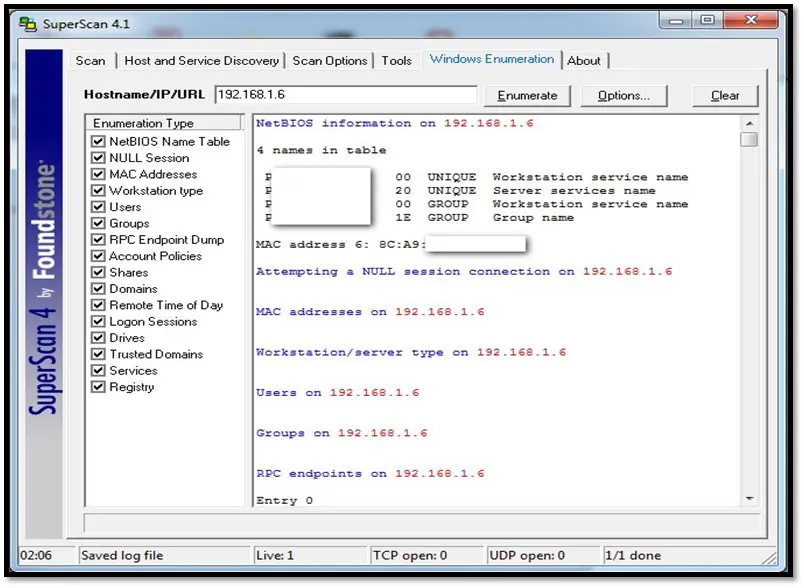
- SuperScan: SuperScan is a popular Windows based port scan tool by Foundstone. It includes a variety of additional networking tools such as ping, traceroute, HTTP HEAD, and whois. It features windows enumeration, which can list a variety of important information dealing with Microsoft Windows such as:
SuperScan can be downloaded from http://www.mcafee.com/us/downloads/free-tools/superscan.aspx
-
AutoScan: Autoscan-Network is a free network scanner. No configuration is required to scan the network. The main goal is to provide the list of connected hosts in the network. It includes a port scanner, TCP/IP scanner, Telnet client, SNMP scanner, VNC client, etc.AutoScan can be downloaded from http://autoscan-network.com/
-
Unicornscan: Unicornscan can be used for gathering network and OS information. Some of its features include asynchronous stateless TCP scanning with all variations of TCP flags, asynchronous stateless TCP banner grabbing, and active/passive remote OS, application, and component identification by analyzing responses.Unicornscan can be downloaded from http://www.unicornscan.org
Conclusion
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Port scanners are generally freeware tools and are easily available on the internet. If your aim is to check the open port, services and OS running on the remote host, any port scanner mentioned in the above section can be used. Nmap scripting can be used to check for well-known vulnerabilities. While doing a security audit, simple port scanner can't be used to detect all the vulnerabilities in the network or host. There are many premium tools which integrate a port scanner in them. Tools like Nessus professional, Qualys Guard, etc. are the professional version of vulnerability scanners where the port scanner is a small integrated module. Apart from giving a list of open ports, these scanner gives the detailed list of latest/old vulnerabilities along with mitigation.







