Pentesting mobile applications with Burpsuite
Securing mobile applications is one of the most important issues today, especially with the continuing evolution of sophisticated cyber threats which are becoming very covert today.
Thus, the pentesting of mobile applications has become a necessity to provide an adequate level of security to not only customers but to businesses and corporations whose respective sales teams are constantly on the road.

What should you learn next?
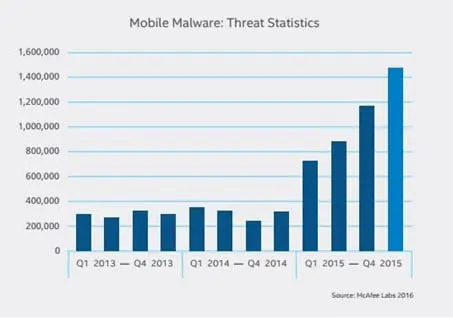
Figure 1: Mobile Malware: Threat Statistics – McAfee Labs 2016
In this article, we will discover how to pentest mobile applications using Burp Suite, one of the more powerful tools used today by pentesting teams.
Burp Suite is one of the most widely used software packages for not only pentesting web applications but, for pentesting mobile applications as well. It is designed for the hands-on penetration tester and has a host of functionalities that help perform various Security related tasks depending on the environment in which it is being used.
The tools available on Burp suite are as follows:
- Proxy: Burp Suite comes with a proxy running by default on port 8080. It is this proxy that makes it able to intercept and manipulate (Forward, Drop, etc.) the traffic between the client and the web application.
- Spider: This feature is used to crawl web applications looking for new links, content, etc. which is located in the target environment.
- Scanner: This feature is used to scan web applications searching for vulnerabilities and hidden weaknesses.
- Repeater: The repeater is used to modify and send the same request several times to analyze the differing responses which arise from it.
- Sequencer: a sequencer is a dedicated tool for the analyzing the degree of randomness of the session tokens which are emitted by the application in question.
- Decoder: This tool is used to encode and encrypt data, or to decrypt data.
- Comparer: This tool is used to perform a comparison between two requests, responses or any other type or kind of data.
- Intruder: This is used for various pentesting objectives such as exploiting vulnerabilities, launching dictionary attacks, etc.
For more information about Burp Suite you can find an informative article here:
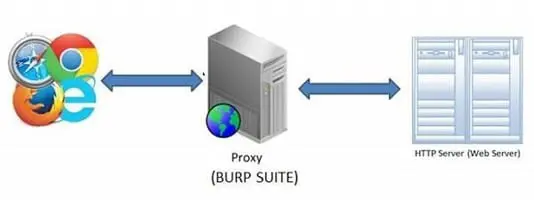
Figure 2: Architecture of Burp Suite
How to install Burp Suite
Burp Suite is by default installed in Kali Linux, but it can be used on any platform. More information can be found here: https://portswigger.net/burp/
After running Burp Suite, the following screen will appear:
Next, click on "Start," as seen on the screen below:
From here, go to the Proxy tab then select the "Options" button:
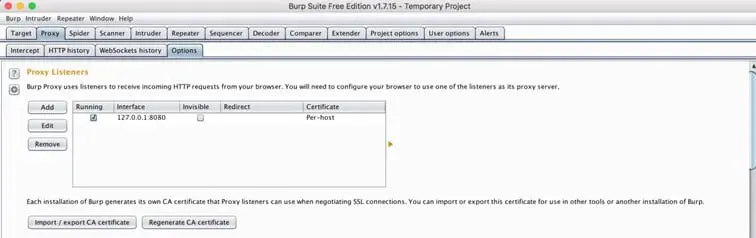
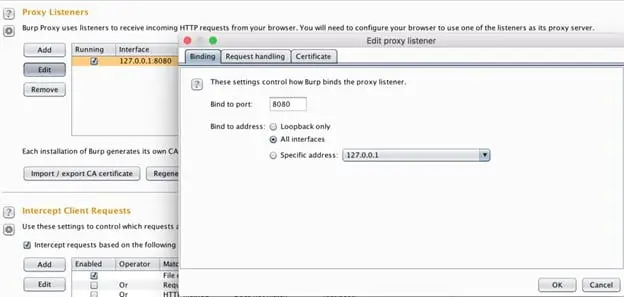
Click on the interface (by default it is 127.0.0.1), and then:
- Click on edit.
- Choose "all interfaces."
- Click on ok.
These steps are illustrated below:
After this, you have to your mobile phone ready and then choose "Settings."
IMPORTANT: You must be on the same wireless network.
To do this, on the settings menu go to the Wi-Fi selection:

Next:
- Choose your wireless network.
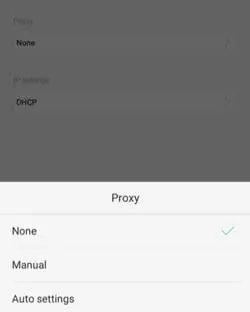
- Select Advanced Settings.
- Set the proxy option to manual:
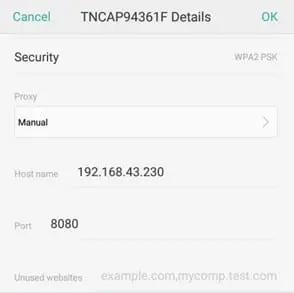
Once the above step has been accomplished, enter the IP Address of your machine and the listening port of Burp Suite (by default this is 8080). This is illustrated in the screen below:
Once the above has been accomplished:
- Navigate to http://burp suite to download burp suite certificate to be able to intercept SSL traffic.
- Click on CA certificate and rename the file to "cacert.cer":
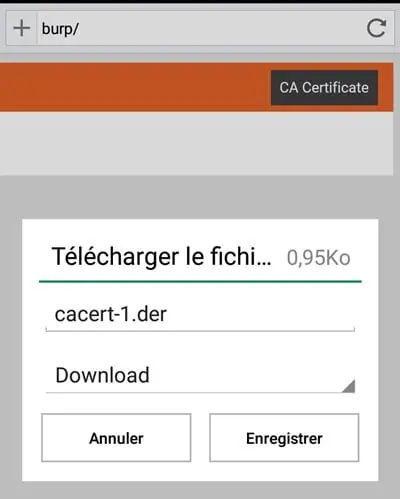
Once the above has been done, go to the location of the file and open it, and from there, the installation will automatically run.
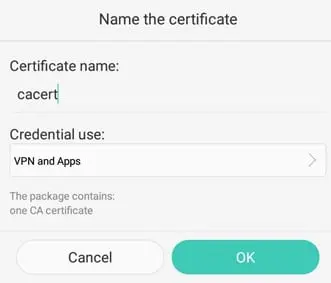
IMPORTANT: Make sure to choose VPN and applications:
Once you open a mobile app on your Smartphone, you can then intercept all the traffic between your Smartphone and the web server of which you are currently accessing. This is illustrated in the screen below:

What to look for in the intercepted traffic log
Here is what to look for in these kinds of log files:
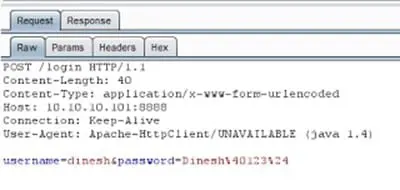
- Un-encrypted traffic:
The following example clearly demonstrates that there is no encrypted traffic (SSL), This means that a Cyber attacker who is covertly on the network can intercept the username/password very easily. This is demonstrated on the screen below:
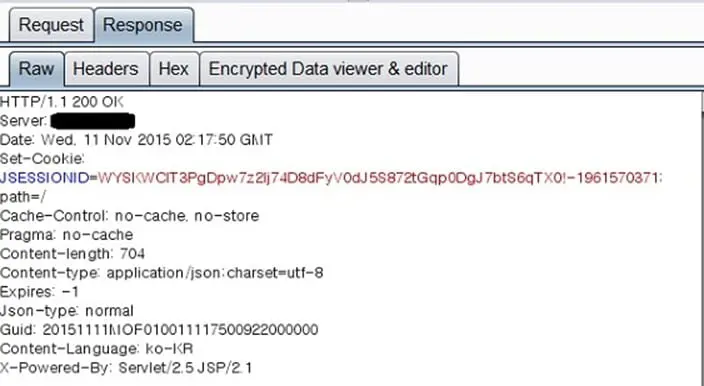
- Session Cookies:
The interception of Session Cookies allows the Cyber attacker to hijack the victim's sessions without the need for any passwords or any other types and kinds of credentials. This is illustrated in the screen below:
- Information leakage:
The screen below displays the "SARAHA" Mobile Application, which can covertly send all your phone contacts to the Cyber attacker without your knowledge:
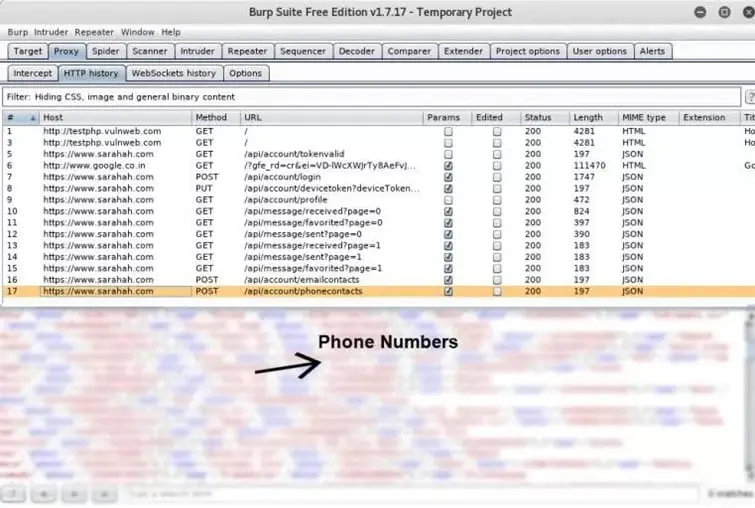
Other extraneous items one can search for by using the Burp Suite software package include the following:

What should you learn next?
- Insufficient Authorization/Authentication o Improper Certificate Validation
- Web Services
- How the mobile app works in a pentesting environment
- Any APIs which are used
Conclusion
In this article, we discovered how to pentest mobile applications using Burp Suite, how to install it, and what kinds of information and data it can show to the pentesting team. In the next series of articles, we will learn to pentest other vectors of mobile applications such as Web Services.







