Penetration Testing: Covering Tracks
"Covering Tracks" is the final stage of a penetration test as a process – all the rest is paperwork. In a nutshell, its goal is to erase the digital signs left out by the pen tester during the earlier stages of the test. These digital signs, in essence, prove the pen tester's presence in the targeted computer system.
Whereas in the phases previous to this one the pen tester successfully managed to avoid detection by firewalls and intrusion detection systems, the purpose of this phase is to cover up all the little clues that would give away the nature of his deeds. "Covering Tracks" consists of 1) measures for the prevention of real-time detection (Anti-Incident Response), and 2) measures for the prevention of digital evidence collection during a possible post factum inquiry (Anti-Forensics).

FREE role-guided training plans
Diagram: "The Last 3 Phases of Penetration Testing with Focus on Covering Tracks."
Anti-Incident Response
Its purpose is to confuse, out-maneuver and disrupt the incident response team at the targeted company. Moreover, anti-incident response activities ensure a pen tester would have the opportunity to gain a long-term foothold on the attacked network even if he has already been detected.
Some important components of a workable anti-incident response are:
- Secretly deploy backdoors
- Set up an agile lateral movement infrastructure
- The number of infected hosts should not be too large, and they should constantly be updated
- The more varied the malware on the network, the better
- Pick up the pace to prevent responders or investigators from keeping up with what is going on
- Busy servers offer the perfect cover for internal hop-points
- Busy file servers may be ideal for data staging areas
- Establishing a VPN for C2 communication may facilitate bypassing some network monitoring measures
- Camouflage the source of malware transmission
When it comes to how the anti-incident response usually works, the emphasis is placed on actions taken to prevent an immediate discovery of an ongoing, and mostly continuous, cyber attack. On the other hand, due to steps taken by criminals or pen testers to damage the evidence and cause a digital investigation to die out in its infancy, anti-forensics hamper the ability of investigators (or their inability) to find enough digital evidence presentable before a court of law at a later stage. Therefore, anti-incident response activities have a sense of urgency because most of the action takes place on a live, running system in real time. Presumably, the counter-actions that incident responders are bound to take are much more time-constrained than those by investigators in a potential digital investigation later on.
On this point, Jamie Porter from Symantec wrote:
In a typical live response scenario, it is a response to an immediate and active threat. Many times the details of the threat are unknown, so the priority is identifying and quantifying the threat. Using live response memory analysis techniques, we can quickly pull a process listing showing what processes are running and begin identifying suspicious ones.
The key to using live response successfully is being very specific and focused on what to examine. When large files such as the registry or $MFT are transferred things slow down dramatically. For example, instead of pulling back the entire $MFT, focus on specific locations that malware is commonly located such as C:Users%APPDATA%roaming and instead of pulling back the complete registry start by looking at the keys commonly used for persistence such as HKLMSoftwareMicrosoftWindowsCurrentVersionRun.
Anti-Forensics
Computer forensics is a discipline whose purpose is to allow forensic experts to acquire, preserve, analyze and present digital evidence in the court of law. Anti-forensics is a notion encompassing all methods and tools which exist to delete, change or conceal digital evidence, with the ultimate goal being the manipulation, destruction or erasure of digital evidence. Marc Rogers, a professor in the Computer Technology Department at Purdue University, formulates anti-forensics as: "Attempts to negatively affect the existence, amount and/or quality of evidence from a crime scene, or make the analysis and examination of evidence difficult or impossible to conduct."
The term itself suggests that it has something to do with actions or techniques whose leitmotiv is to obstruct an eventual digital investigation and to diminish the quality and quantity of digital evidence. Typical users of anti-forensic tools and techniques are hackers, cyber terrorists, online pedophiles, counterfeiters and other cyber criminals who want to remove existing traces of nefarious computer activities which may incriminate them. Nevertheless, pen testers have recourse to the antipode of the digital forensic science as well to do what they do best – conduct a thorough test of the security capabilities of particular computer systems.
With the help of automated tools, the pen tester can mask the attack and create backdoors for further exploitation at the same time. The information security portal Security Wizardry has created a list of anti-forensic tools which can be found here.
Deleting Evidence
A common delusion among persons who count on commercial disk cleaners or privacy protection tools to delete some data they do not want others to see is the belief that these tools remove everything from the hard disc once and for all. In fact, they can clean up the following kind of information:
- Cache and history for popular Web browsers
- Chat logs produced by Skype and some other popular instant messengers
- Provide "secure delete" option to wipe files
- Clean some (but almost never all) of the following: jumplists, thumbnails, registry items, Skype chatsync, etc.
By utilizing specific forensic tools, a forensic expert can outsmart almost all clean-up programs. In reality, they can be an effective solution for casual observers, but not that effective anti-forensic measure when we take into account the amount of information that pass through, namely: thumbnails cache, Windows jumplists, browsing cache and history, chatsync, undeleted files being currently opened at the moment of deletion, deleted files with left corresponding Registry entries intact, etc.
Pictures of interest, for instance, can be recovered because, even if the original image has been deleted, a smaller version of this picture should still exist in Windows Thumbnails. And even if the thumbnail has been removed, forensic examiners could attempt to restore it via file carving. Windows Vista, Windows 7, 8, 8.1 and Windows 10 usually keep their thumbnails stored in one location (i.e., %userprofile%AppDataLocalMicrosoftWindowsExplorer). Alternatively, there are automated tools designed to perform that task.
Jumplists (another good example of a way to beat some cases of deleting) provide information about applications, documents, pictures and various other kinds of files with which the user has interacted. They are generated even for files accessed from external devices and remain intact, irrespective of whether the original file is deleted or the external device is removed. Jumplists contain the name, computer name, MAC address, path to the file being accessed, application utilized to open the file, and access date and time, therefore they can be an excellent proof of access. From a technical point of view, jumplists are small files in plain text format stored in %APPDATA%MicrosoftWindowsRecentAutomaticDestinations.
Manually wiping Skype history will also not erase the internal data kept in the "chatsync" folder whose content may reveal fragments of user conversations.
Despite the imperfectness of the "Delete" method. A well-done erase will irreversibly dispose of evidence, leaving investigators empty-handed. Nevertheless, not so proficient users are prone to make mistakes, which may cost them a lot in cases of unsuccessful attempts to delete the data on the hard disk.
Unless we discuss SSD drives (which are programmed to destroy data automatically), hard drives and storage media are susceptible to almost fully recovery via data carving. All in all, this method is very popular but not so effective. According to a 2015 article "Countering Anti-Forensic Efforts - Part 2" by Oleg Afonin, Danil Nikolaev and Yuri Gubanov, a typical wipe tool merely "overwrite[s] the content of a file (or the entire disk volume) with one or more passes of random data. This is enough to permanently overwrite information stored on magnetic hard drives and, to a large extent, on USB flash drives. However, some users will set unnecessarily large number of wipe cycles, overwriting the data several times. Needless to say, this is a much slower wipe that may give law enforcement a chance to stop the process mid-way."
Moving, Hiding, Altering or Renaming Files
Although it may seem naive, some wrongdoers use these techniques in the hope of evading justice. In this case, 'covering tracks' can take the form of moving given files (for instance, those that contain conversation histories), changing extensions or renaming.
It is an arduous task to retrieve and rearrange the hidden data. Some programs can split files into small partitions and conceal each partition at the end of other files. With the help of the right programs, a pen tester can take advantage of an unused file space dubbed slack space, thereby hiding important information in plain sight.
Similarly, a pen tester can hide one file inside another (more or less like steganography) – a method which copes well with executable files, in particular. In this regard, J. Strickland mentioned in his article "How Computer Forensics Works": "Programs called packers can insert executable files into other kinds of files, while tools called binders can bind multiple executable files together."
Timestamping: More often than not, the people involved in a cyber investigation do not have the time to examine one by one all the files residing in a computer system. One approach which allows them to prioritize their search of information potentially relevant to the investigation is to arrange this information in chronological order so that they can focus on the important pieces of data occurred around the moment of the cybercrime (if it is known). Criminals, however, try to tackle this approach by modifying the metadata about any files they want. In most cases, they change the date on which each file was created, last accessed, or last modified. This effective anti-forensic technique is named time stopping, and tools to detect its creations do exist.
Among the anti-forensic inventory, there are tools that can alter the information in file headers. Once the transformation is completed, the computer will think it is a different type of file (for example, to rename an mp3 file so that it will appear as a .gif one).
Despite that investigators often rely on their skills and flair to locate renamed or moved files, there are information forensic methods which automatically analyze hard drives for suspicious discrepancies, such as data carving. Data carving (a.k.a. file carving) is a technique that conducts a very precise sequential scan of media for different sets of artifacts. What makes this method so effective is its ability to read low-level data directly from the media instead of relying entirely on the way the file names and locations appear on the file system. For example, a ZIP archive will be identified as such based on the actual data stream that possesses information inherent to ZIP archives, not based on the name of the file.
Last but not least, encryption can be great security-wise, but it can be a real nightmare as far as digital forensics is concerned. A powerful algorithm can render the data unreadable, hence useless to investigators.
Log Tampering
In Windows-based computer systems, all of the log files are stored in the event viewer, easily findable via the "Search" bar. In almost all Linux and UNIX operating systems the log files are located in the /var/log directory, and in MAC operating systems one should open the Finder, click "Go to Folder" in the Go menu, and type in /Library/Logs and press Enter to activate the Log File Management which will display all log files.
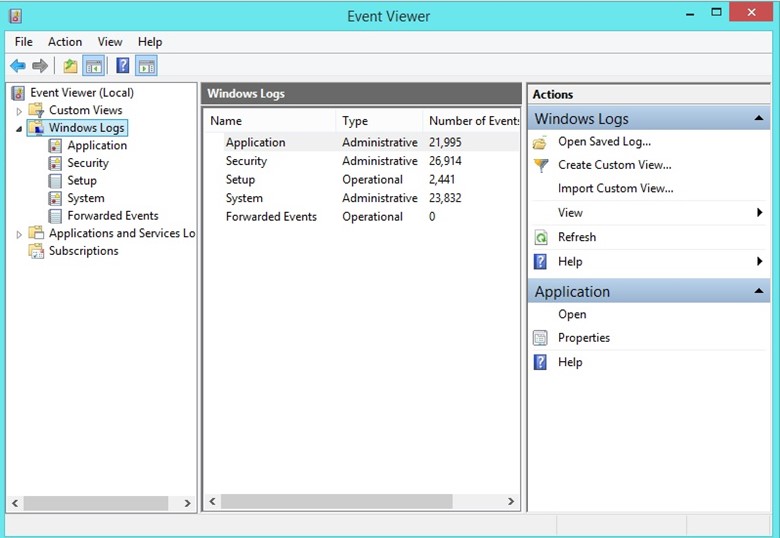
If administrators want to check for malicious activities within the system for which they are responsible, they simply examine the log files. There are two kinds of log files: system generated and application generated.
When it comes to log manipulation, the attacker usually has two options. The first option is to delete the log, and the second one is to alter its content. Deletion of log files and replacement of system binaries with Trojan malware ensures that the security staff employed by the targeted company will not detect evidence of the cyber intrusion.
The first choice – to delete the log files – is not always the ultimate solution to undetectability, since the removal of such information might create a gap between logs files and raise suspicion. One look at the processes and log files would be enough for a system administrator at the target's premises to establish the existence of any malicious activities. So, chances are the system administrator may notice when a log file is deleted. Log files are used to detect malicious activities, but that is only one of their purposes; they serve as a warning system on the actual state and health of the system, and any irregularities with their availability or attributes may draw unwanted attention. Presumably, it will be prudent on the part of the attacker if he decides to wait for a time when the probability of system administrators to check the log data is minimal, for instance, during nighttime or weekends.
N.B.
To tamper with log files information, a pen tester must have root privileges. Once privileges are being elevated, a pen tester can manipulate log data related to his activities within the log file itself. So, an examination performed by a system administrator will not reveal anything out of ordinary.
As a defensive tactic against log files tampering, system administrators sometimes configure their system to transfer all logs from the system to a remote server specifically dedicated to log data retention. In such a case, the pen tester would have no other option but to cease the transfer process or attempt to compromise the log server.
Conclusion
Being stealthy is a great precondition for success. For that reason, avoiding detection until the penetration test is over is sometimes not enough (i.e., the anti-response part). Sometimes it is very important that the cyber attack as a fact will continue to remain unknown to the victim after its end, regardless whether we talk about a pen test or an actual cybercrime. And if you happen to set off the radar detection, anti-forensics should come to the rescue.
Some people undeservingly tend to underestimate the significance of "Covering Tracks" phase. Perhaps they think that their job is done when the objective of the mission is completed (e.g., to obtain a bundle of valuable documents). However, if you want to get the knack of penetrating sophisticated systems, it is imperative to learn how to do so in as low-profile manner as possible. And that is exactly where "Covering Tracks" phase comes into play. It is simply a fail-safe mechanism for pen testers and hackers which would keep them out of trouble, both immediate and such that might occur during an investigation.
Other articles on Penetration Testing:
Penetration Testing: Maintaining Access
https://resources.infosecinstitute.com/penetration-testing-maintaining-access/
Penetration Testing: Intelligence Gathering
https://resources.infosecinstitute.com/information-gathering/
Ethical Hacking vs. Penetration Testing
https://resources.infosecinstitute.com/ethical-hacking-vs-penetration-testing/
Reference List
Afonin, O., Nikolaev, D. & Gubanov, Y. (2015). Countering Anti-Forensic Efforts - Part 1. Available at http://www.forensicmag.com/article/2015/09/countering-anti-forensic-efforts-part-1 (31/07/2016)
Afonin, O., Nikolaev, D. & Gubanov, Y. (2015). Countering Anti-Forensic Efforts - Part 2. Available at http://www.forensicmag.com/article/2015/09/countering-anti-forensic-efforts-part-2 (31/07/2016)
Berghel, H. (2007). Hiding Data, Forensics and Anti-Forensics. Available at http://www.berghel.net/col-edit/digital_village/apr-07/dv_4-07.php (31/07/2016)
Booth, N. (2015). Rise of anti-forensics techniques requires response from digital investigators. Available at http://www.computerweekly.com/microscope/opinion/Rise-of-anti-forensics-techniques-requires-response-from-digital-investigators (31/07/2016)
Carvey, H. (2013). HowTo: Determine/Detect the use of Anti-Forensics Techniques. Available at https://windowsir.blogspot.bg/2013/07/howto-determinedetect-use-of-anti.html (31/07/2016)
Clarke, S. (2014). Identifying Anti-forensics: Timestomping. Available at https://www.nuix.com/2014/11/19/identifying-anti-forensics-timestomping (31/07/2016)
De Lucia, E. (2013). Anti-Forensics – Part 1. Available at https://resources.infosecinstitute.com/anti-forensics-part-1/ (31/07/2016)
IP Copper. Network Forensics & Antiforensics. Available at http://www.ipcopper.com/forensics_and_antiforensics.htm (31/07/2016)
hackingloops.com. How to remove traces : Hacker's Guide for Anti-Forensics. Available at https://www.hackingloops.com/how-to-remove-traces-make-your-computer-untraceable/ (31/07/2016)
Harbour, N. (2012). Anti-Incident Response. Available at https://digital-forensics.sans.org/summit-archives/2012/anti-incident-response.pdf (31/07/2016)
Holmes, K. (2016). Understanding the Impact of Anti-Forensics Techniques. Available at http://www.ftitechnology.com/resources/blog/understanding-impact-anti-forensics-techniques (31/07/2016)
Kishore, A. (2016). Delete or Clear Jump List Recent Items in Windows 7, 8 & 10. Available at http://www.online-tech-tips.com/computer-tips/clear-recent-items-windows-jumplists/ (31/07/2016)
Olzak. T. (2008). The five phases of a successful network penetration. Available at http://www.techrepublic.com/blog/it-security/the-five-phases-of-a-successful-network-penetration/ (31/07/2016)
Pajek, P. and Pimenidis, E. (2009). Computer Anti-forensics Methods and Their Impact on Computer Forensic Investigation. Available at https://core.ac.uk/download/files/96/10809913.pdf (31/07/2016)
Porter, J. (2014). Live Response vs. Traditional Forensics. Available at http://www.symantec.com/connect/blogs/live-response-vs-traditional-forensics-0 (31/07/2016)
Saliba, J. (2016). Anti-forensics: Finding the Hidden Evidence. Available at http://htciaconference.org/sessions/anti-forensics-finding-hidden-evidence/ (31/07/2016)
Strickland, J. How Computer Forensics Works. Available at http://computer.howstuffworks.com/computer-forensic3.htm (31/07/2016)

FREE role-guided training plans
In the diagram are used the following images:







