Password Auditing on Active Directory Databases
In this article we explore the options to acquire information from an online or offline Microsoft Active Directory database and its encryption keys. We will use this to recover the contained usernames and password hashes for password auditing or penetration testing purposes.
The database

What should you learn next?
Microsoft stores the Active Directory data in tables in a proprietary ESE database format. The database is contained in the NTDS.dit file. This file is encrypted to prevent any data extraction, so we will need to acquire the key to be able to perform the extraction of the target data. The required Password Encryption Key is stored in the NTDS.dit file, but is encrypted itself with the BOOTKEY. To obtain this BOOTKEY, we need to acquire a copy of the SYSTEM registry hive from the same Domain Controller as we acquired the NTDS.dit file.
The files
So in order to perform this attack, we need to get a copy of the NTDS.dit and a copy of the SYSTEM file. This is not too difficult in many situations. The required files can be collected from a backup tape that is stolen or that was simply found in a recycle bin (this is why media sanitization is so important). Another option is to use a preconfigured RDP client with an administrative account to access a domain controller. Sometimes administrator passwords are common knowledge within an organisation or its IT departments. Quite often they are found on sticky notes next to the console.
Once an attacker has administrator level access, many different tools can be used to extract the NTDS.DIT file and the SYSTEM hive from the domain controller. When the system can be taken offline, it's just a matter of restarting the server in Safe Mode and copying the files "c:windowsNTDSntds.dit" and "c:windowssystem32configSYSTEM" to their desired destination. In many cases however, taking a server offline could be noticed by users and it will leave a lot of audit log entries. A better option is to copy the files while the domain controller stays operational. Restoring copies of the files from a backup could be a quick solution, but this is not always an option. We might need to acquire a copy of the live database while leaving the server online. Because in this situation the files are in use, we will utilize some simple tricks.
Existing Shadow Copy Volume
This is the easiest option to copy the (almost) live files. If automatically scheduled Volume Shadow Copies are enabled on the volume that contains the required files, the tab "Previous Versions" within the volume properties will enable us to open previous versions of that volume. Once the older version is opened, the files can be found in their original locations by using Windows Explorer. Because they are not in use, we can easily copy them to where we can use them. This option will not leave a trace in the standard Windows audit logs if used correctly.
A new manual Shadow Copy Volume
Quite often automatically scheduled Volume Shadow Copies are disabled on the target volume and enabling this automated service would leave quite an Audit Trail. It could make changes to the remaining free disk space, triggering monitoring alarms, which in turn will trigger investigation. Alternatively, we can still create a new, manual Volume Shadow Copy. This will leave some traces in the Windows audit logs though, so it is still not the most stealthy option. Without going too much into detail here, tools such as the Volume Shadow Copy Management command line interface VSSOWN can provide the answer. Antivirus software might pick this .vbs script up though, revealing the attack.
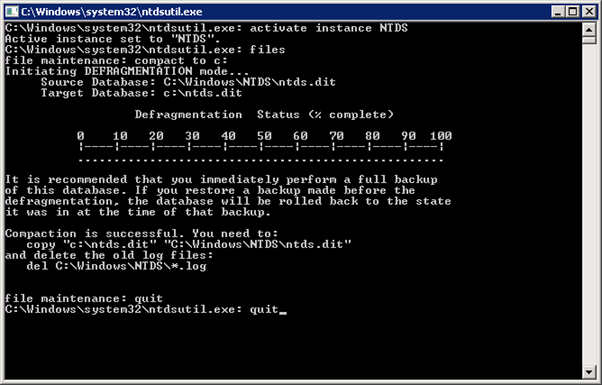
NTDSUTIL
This standard Microsoft tool allows for the creation of an offline version of NTDS.dit. The only problem here is that without the SYSTEM file, the database file will not be useful. We need to decrypt the hashes before they can be used. This means we still need to resort to the Shadow Copy methods above to obtain the SYSTEM file.
3rd Party Tools
Tools such as L0phtcrack (from $495) and Passcape Windows Password Recovery (from $345) can extract password hashes straight from a domain controller and export them to a file or start the cracking process straight away.
Another option is to use the range of PWDUMP tools. There are many versions available and most are free. Some need to be run locally and some can be used remotely.
All these third party tools have one thing in common: They need to connect to the database using an administrative account. This will usually be available when performing a password audit though.
Another issue with most of these these programs is that they can be picked up by antivirus software, resulting in alarms, log entries and automatic deletion or quarantine of the tool itself. This is hardly a stealthy option.
The relative ease of use and quick results can make it an ideal solution for password auditing though.
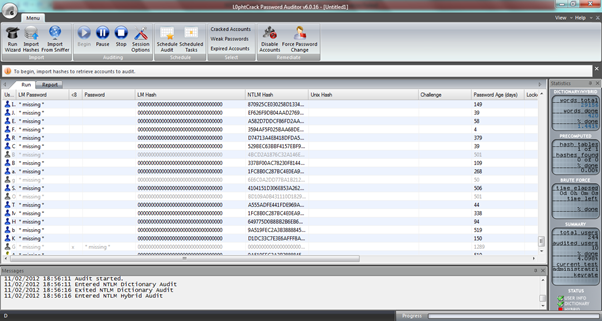
Extracting the hashes from an offline database
Without the third party tools, the hashes will need to be extracted manually. Once the required NTDS.dit and SYSTEM files are stored and ready for processing, several tools can be used to extract the hashes from the offline database.
The Quarkspwdump tool can be used from Windows to extract the hashes from the NTDS.dit file into multiple formats. One of these formats is PWDUMP, which is compatible with many hash cracking programs.
An example of a Linux tool that can be downloaded and used for free is NTDSXTRACT. It is easy to use, but the output is not in the PWDUMP format by default. This can cause problems importing the data into some cracking tools. Luckily a free Python script called NTDStoPWDUMP is available to convert the data into a more usable format.
Cracking the Hashes
The acquired hashes can be of 2 types: the older LM hash and the more recent, improved NTLM hash. This will depend on the version of Windows that is used and the security settings within the domain. A 2008 R2 domain controller will most likely only store NTLM hashes, unless the older LM hashes have been enabled on it for backwards compatibility of some older applications. An older domain controller might still have the default LM hashes stored on it.
Why is the type of hash important? The stronger the hash, the longer it will take to crack the password behind it. LM hashes uses a character set that is much smaller, is case-insensitive and breaks a password up in 7 character chunks. This means it is much quicker to crack the hash of the LM type. We should attempt to crack the LM hash first if it is available. The NTLM hash can also be cracked, but this will get infeasible if passwords are longer than 9 characters and/or contain a very large character set due to the use of symbols. Considering the purpose of a password audit is to identify only the weak passwords, this should not be a problem. The real problem will present itself when there is a need to crack a password which does not fall inside the 9 character maximum and standard a-z, A-Z and 0-9 character set limitations. Cracking an NTLM hash can then take many weeks, months or years, generating a huge power bill. The use of precalculated rainbowtables can speed up the cracking process a bit, but their size becomes enormous when the password length and size of the character set increases. Of course, it all depends on what is at stake.
Windows software (paid)
As mentioned before, there are many third party tools available that can import live data from a domain controller and start the cracking process straight away. These tools can be very expensive, but due to services such as online dictionaries and even pre-computed rainbow tables, they can save a lot of hands-on and processing time. They also include reporting functions, showing graphs of password strengths with a network. For anyone performing regular, paid password audits, owning at least one of these tools is invaluable.
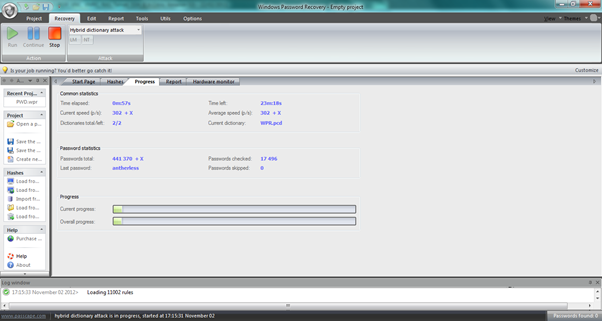
Windows software (Free)
There are also numerous free programs available for Windows users.
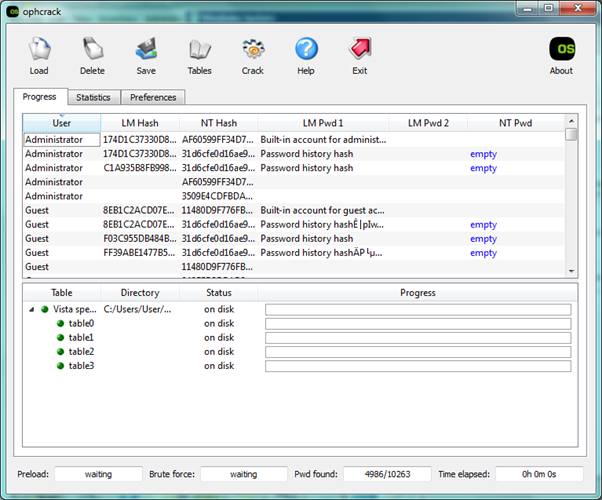
Ophcrack is an example of a program designed for rainbowtable usage, although the larger rainbowtables will need to be purchased. It will come with a basic, free rainbowtable for a quick bruteforce attack.
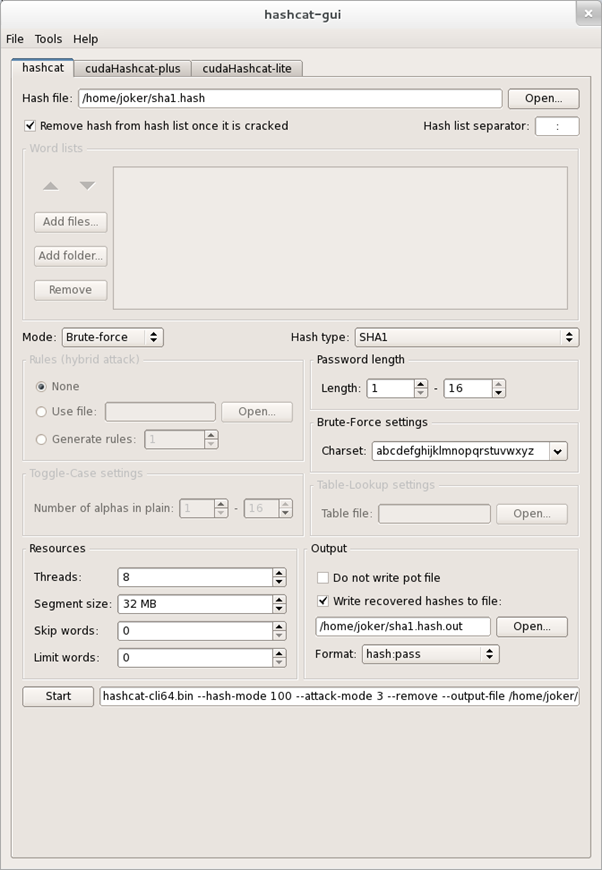
Oclhashcat-plus
is a free tool that utilizes the GPU for brute force attacks. The GPU is much more efficient than a CPU for bruteforce attacks due to its floating point calculation capacity. This will drastically reduce password cracking times, but requires a powerful video adapter. The program can import PWDUMP formatted files and a GUI is available for Windows users.
Linux software (Free)
Oclhashcat is preinstalled within Backtrack 5, but can be downloaded for other Linux versions as well. Just like for the Windows version, a GUI is available for download.
Don't get carried away
Finally, I would like to pay attention to the legality of password cracking. It is quite obvious that cracking a password to gain unauthorised access to information is illegal in most jurisdictions. What is a little less obvious however, is the legal base of performing a password audit for a client or employer. This depends very much on the applicable jurisdictions of where for instance the user is based, where the head office is based, or where the data is stored.
In some countries actual passwords cannot be viewed by auditors and management due to the classification as private data. An employee's Windows password could for instance also be used for a private Facebook page. In that situation, a simple notification stating the fact that a password has for example less than 6 characters or that it only has a character set of a-z, will need to be used. Another option would be to blank out any identifiable user imformation that is related to the passwords. This does not have to be an issue, because the remaining data could be all the information that is required for an audit report. Data can be gathered for instance for a report which could justify a password policy that is to be implemented. A simple percentage of unsafe passwords can be enough.
It will be very important to do some research beforehand into the rules and regulations in place in all applicable jurisdictions. Something to always keep in mind is to obtain a written authorisation contract from the highest level of management, asking for the work to be performed and stating details such as the scope of the work and the timeframe within which the audit will need to be completed. This might be your get-out-of-jail-free card when a dispute arises and the client claims never to have authorised the audit. This would make the performed work a criminal offence, creating a lot of trouble for the auditor.
Testing on your own data is completely free of course, so don't hesitate to start cracking.

FREE role-guided training plans







