Introduction to the paros proxy lightweight web application tool
The Paros Proxy Lightweight Web Application tool is one of the most popular penetration testing tools for web applications. Web app developers and security experts use it to test their web applications for security vulnerabilities. Paros is built on Java, meaning it can run on multiple operating systems.
In this article, we shall take a look at this tool and discuss the different features it provides.

FREE role-guided training plans
Paros overview
Paros runs as a GUI JAVA application and supports spidering, HTTP message editing, proxy-chaining, and intelligent scanning for SQL and XSS vulnerabilities. However, it has not been updated since August 14, 2013 and, as a result, may be prone to many false positives or may even miss some vulnerabilities.
Paros can be downloaded from the project download link on SourceForge, found here. It can also be found within the Kali Linux Penetration Testing Linux distribution. Due to its nearly ancient code, the project has been forked into a more updated tool, the OWASP Zed Attack Proxy (ZAP), which is maintained by the OWASP community. For an introduction to the OWASP ZAP tool, kindly visit this article [link-article-to-OWASP-ZAP].
Launching Paros Proxy Lightweight
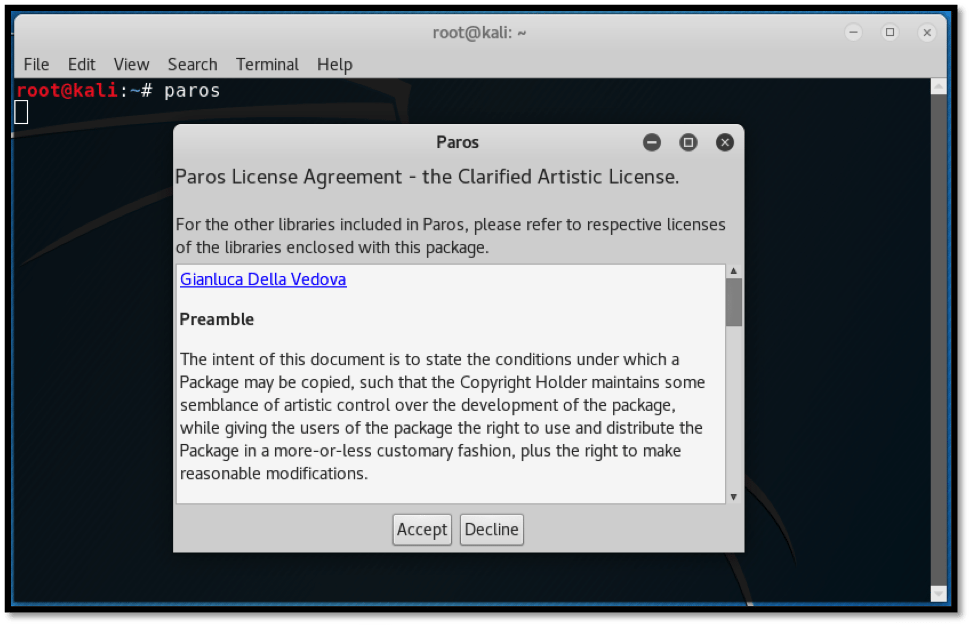
Kali Linux ships by default with Paros since the Kali Rolling Edition. Launching the tool is as simple as typing “paros” on the terminal. This is shown below:
The license agreement that appears outlines the developer’s guidelines. For us to proceed, we need to accept the terms.
Paros Proxy Lightweight GUI
Paros is the brainchild of the GUI that inspired its successor, OWASP ZAP. It (Paros) defaults to a window divided into three sections; the top section, which is divided into left and right sections, and the lower section.
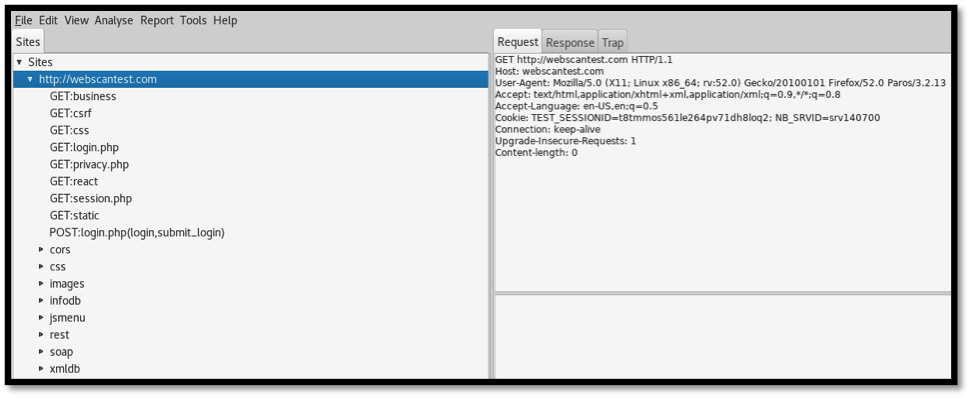
Left Section: This section displays the website being tested and the discovered files and folders. This helps the pentester to create a virtual map of the target website.
Right Section: This section displays the requests and responses to each request made to the target website. Requests can be trapped, modified and re-sent, thus allowing various tests to be initiated within the website parameters.
Bottom Section: This section displays the responses from the crawling and scans performed on the target website. This section contains the history, spider, alerts and output tabs that display information depending on the activity being executed against the target website.
Attacking vulnerable web applications with Paros
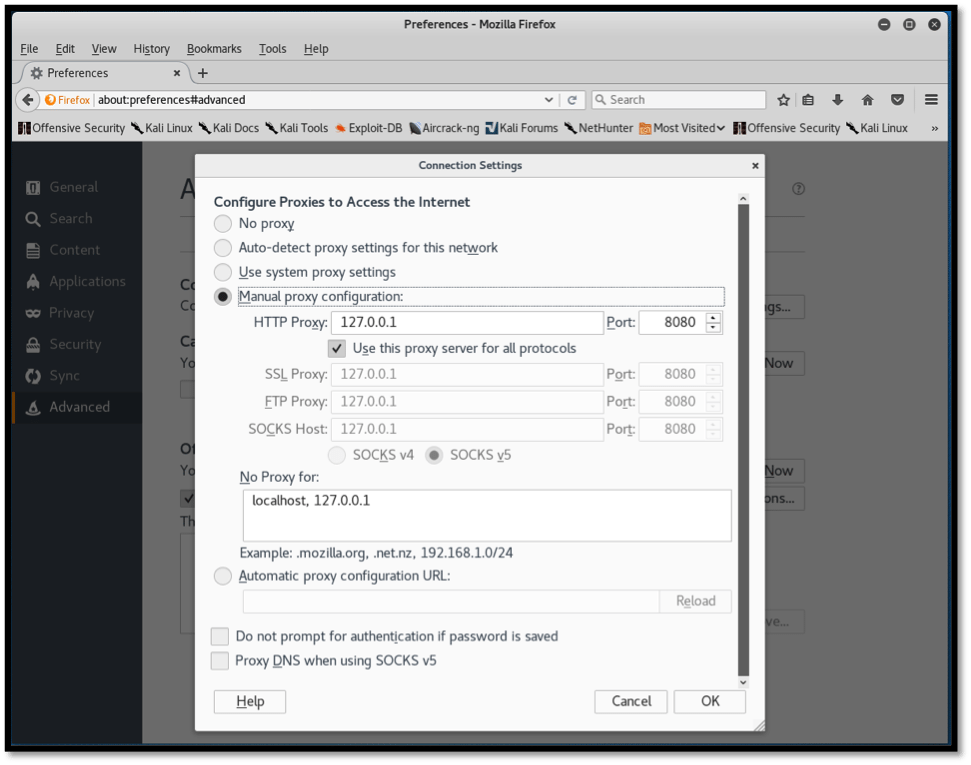
Before we can attack a web application, it is important to set a proxy in order to allow Paros to intercept traffic between our browser and target website. We do this by launching our browser on Kali Linux. In this case, we are using “Firefox ESR” on Kali Rolling. From the three lines on the top right-hand section of the browser, we select “preferences,” then “Advanced.” Finally, under the “Network” tab we click on “Settings” and configure our proxy settings as shown in the screenshot below:
Paros intercepts traffic by listening on localhost (127.0.0.1) and on port 8080. We apply these settings for HTTP, SSL, FTP, and Socks v5.
Paros is now ready to intercept our traffic. We will be using the vulnerable website http://webscantest.com, which is intentionally left vulnerable for testing web application vulnerabilities.
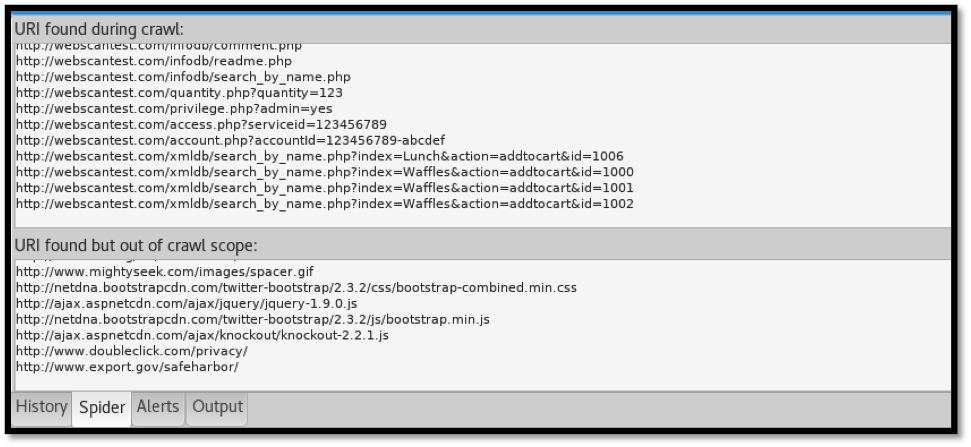
To identify files and folders on the target website, we select “Scan” from the menu bar. The spidering process begins and identifies URLs that are within scope, differentiating them from those out of scope. This can be seen below:
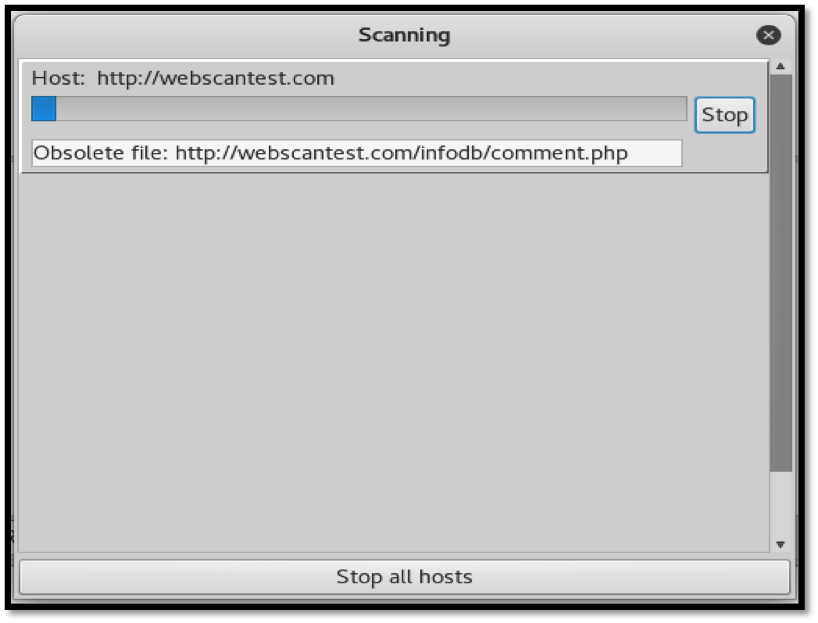
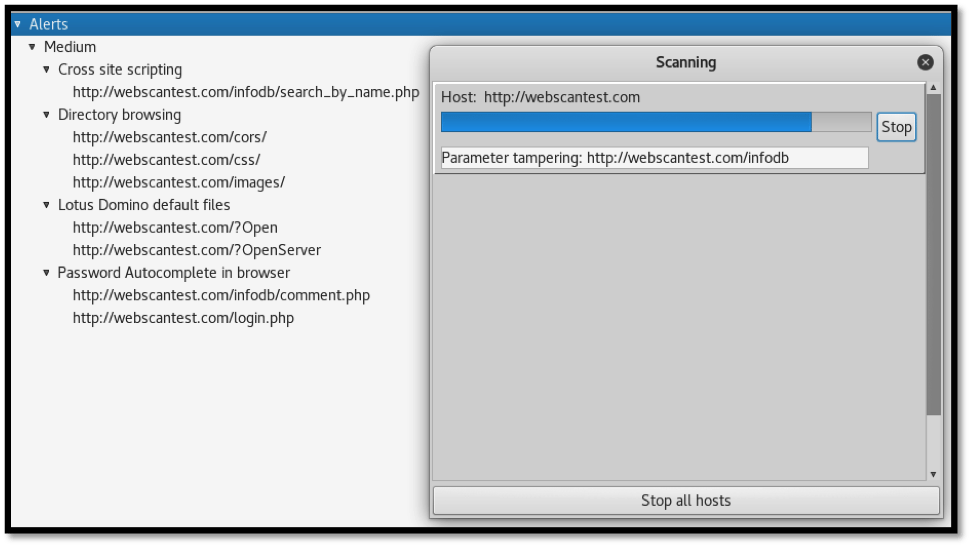
Once the spidering process is complete, we can begin the scan. Paros then attempts to discover vulnerabilities throughout the website.
As the scan runs, the two top sections display discovered information. The left-hand side section shows the discovered folders and the files they contain. After the files are selected on the left, the right section shows the corresponding request and responses that were made while obtaining the files. This can be seen below:
These requests and responses can be effectively modified to achieve a desired result.
The “Alerts” section at the bottom of the Paros window displays discovered vulnerabilities. The build-up of alerts proceeds until the scan is completed.
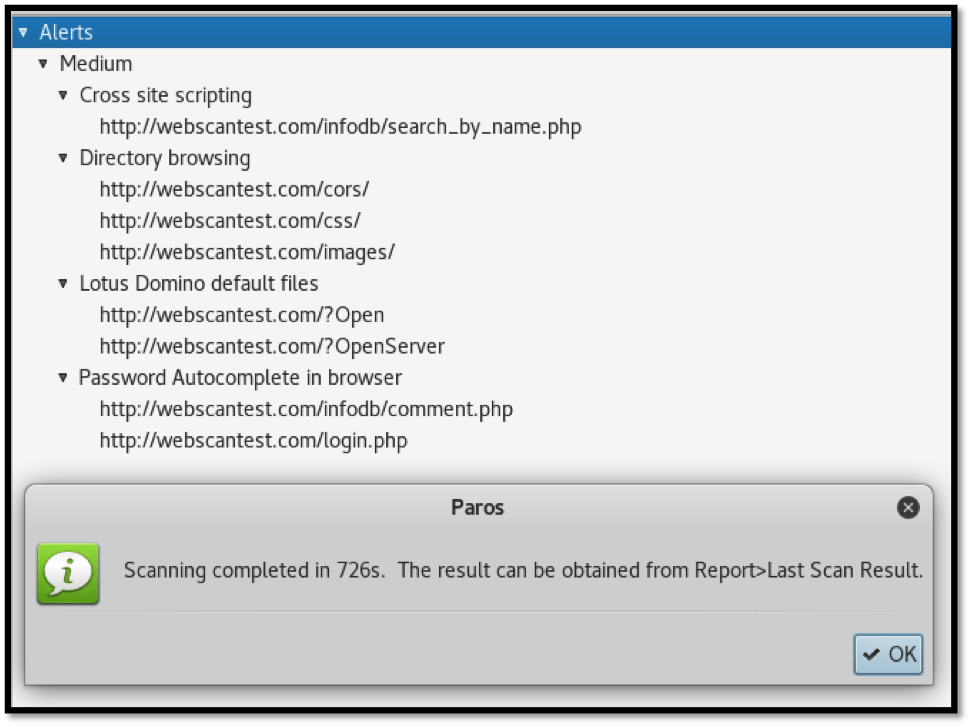
As can be seen below, Paros identified four issues ranked at “medium” severity. Let us take a look at the identified vulnerabilities as per the screenshot below:
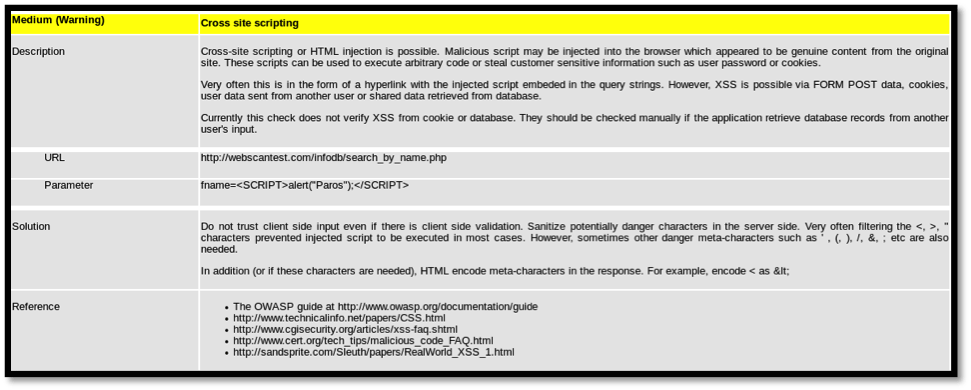
Cross-Site Scripting
Cross-site scripting (XSS) is a vulnerability that abuses JavaScript. XSS allows attackers to inject malicious JavaScript into affected websites that redirect legitimate website visitors to malicious sites. These malicious sites may contain downloadable malware that can be used in further attacks. XSS can also allow attackers to alter the way a website loads on client browsers, allowing, to a certain extent, fake fields to be included that can be used in obtaining credentials from the login page.
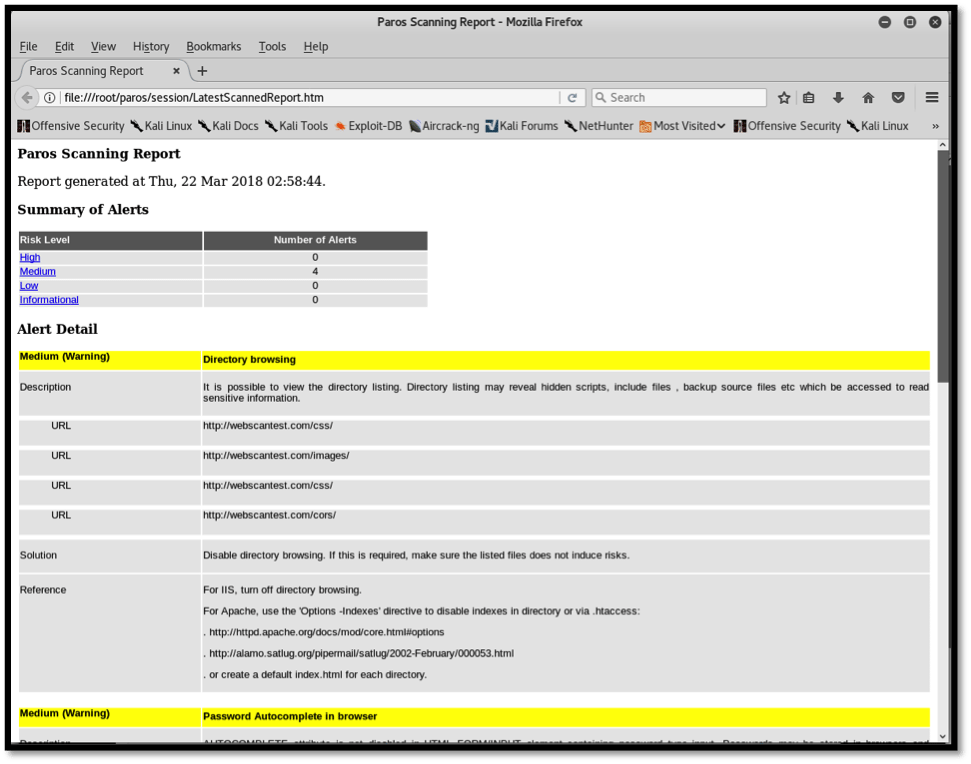
Directory browsing
Directory browsing allows anyone on the Internet to view the files resident on the back end of the affected website due to inappropriate permissions. Files such as source code can be accessed and, in some cases, downloaded. In cases where database or system connection files are accessed, credentials may be obtained that may allow unauthorized individuals to gain access into databases or, if credentials are reused, then even allow unauthorized SSH logins.
Lotus Domino default files
Default installation files may disclose sensitive information while the pages that include them are visited. Such files may display software and hardware versions used, which may aid attackers in planning attacks against the web server.
Password autocomplete
When websites allow credentials to be remembered on login pages, it allows attackers to obtain them using specially crafted tools.
Scan results report
Once the scan is complete, the results are automatically saved as an HTML file within the Kali Linux system. As we can see below, the scan duration was 726 seconds. Paros instructs us to visit “Report,” then “Last Scan Result” on the menu bar.
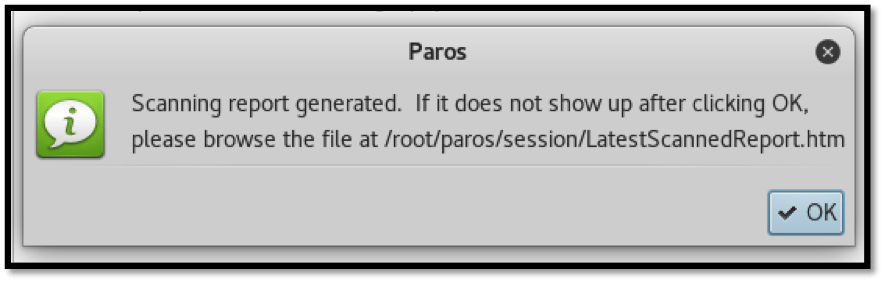
Paros also tells us where to manually locate the saved report HTML file. In this case it is located under the directory:
/root/paros/session/LatestScannedReport.htm
We open the file with our browser and we can view the results in detail. Paros categorizes the identified issues according to risk rating. Our last scan session resulted in four medium risk issues as can be seen in the screenshot below:
Paros also provides a brief description of the identified vulnerability, the affected URLs, files, a solution for remediation as well as references in case further study on the issue is needed.
For some vulnerabilities, Paros shares the affected URL and payload used during parameter injection. This can be seen in the screenshot above, obtained from an XSS identification.
Conclusion
Paros Proxy Lightweight Web Application testing tool is a light and less demanding tool that allows testing of web applications on systems with low resources, as opposed to more demanding tools such as the OWASP ZAP and Burpsuite. Even though Paros is not regularly maintained, it can be resorted to in situations where other proxy tools are unavailable.

FREE role-guided training plans