How Do Pentesters Document and Remediate Vulnerabilities in Android?
Pentesting applications for Android requires many different levels of skills, knowledge and patience. Patience is especially important, because there are so many details that need to be documented and looked into during this process. This is especially true with regard to the documenting portion of this exercise.
We will take a brief look at the most common methods that pentesters use when trying to document and remediate vulnerabilities in Android and how these operations are generally carried out and recorded during a pentest.

FREE role-guided training plans
What Do Companies Expect to Find in Pentesting Reports on Android Vulnerabilities?
The general content of each report will vary according to the application being tested and the faults that are found. The standard format contains an introduction, which explains the overall nature of the report and what and who it is intended for. Next there should be a scope that reveals what items are to be tested and reported on in the document.
Some reports will go into some detail about the threat rating scale that is used in the report and what each different level of severity means to the reader. The threat types are normally named Low, Medium and High, or something similar.
After that comes the list of discovered vulnerabilities, all of which pertain to the main objectives in the scope of the report. Each of the items that is discovered in the Android pentest should be accompanied by a reference number, the type of vulnerability that it relates to and a severity rating.
Miscellaneous items are sometimes also noted in the report. These are issues that are not serious enough to warrant an immediate response but have the potential to become problems if not eventually remediated.
Each item that is listed as a vulnerability must have a corresponding solution attached to it so that management can steer the process of getting their development team started on the fixes required.
How Technically Complicated Should Pentesting Reports Be?
The technical level of the report should be high enough for the developers and design teams to glean useful information from it, while also containing easy-to-read sections written in non-technical, plain English.
The introduction section will be the least technical part of the report and will be a summary of what will be covered in the rest of the report. The scope will make mention of technical problems that are to be resolved and the identified vulnerabilities section will contain anything from code snippets to command output from pentesting tools. The latter segments will necessarily be very technical.
Accompanying this technical output will be a plain-English explanation that explains the ramifications of each identified vulnerability, which helps the management team assess the priorities of the remediation stage that will inevitably follow the pentest.
What Is the Purpose of a Pentesting Report?
Pentesting reports are generated so that companies that develop software applications can identify the security level of their software. This protects both the company and its customers from poorly-implemented security measures and allows for continual improvement of the application.
The feedback that a pentesting report generates can also help to inform developers how their application can be improved, as well as alerting them to new concepts in security implementations. This has the potential net benefit of upskilling your development team, making everybody a winner.
What Makes Android Pentesting Different From Other Platforms?
Android is based on Linux, which is an open-source software platform. This makes it inherently easier for developers to create applications for.
Google created Android and it was initially used as a smartphone operating system, but Android was quickly adopted by many device creators and not just smart phone manufacturers. The OS continues to grow in popularity; today, Android now runs on a whole slew of different devices, from smart watches to TVs and gaming consoles.
Because of this openness, Android is easier for attackers to target, which makes the likelihood of vulnerabilities affecting the security of the OS that much higher. Android comes with options that allow for the installation of unsigned installation packages by default. These are disabled but can easily be activated without any special applications or tools. This makes the probability of harmful software being installed on an Android device much higher than that of iOS.
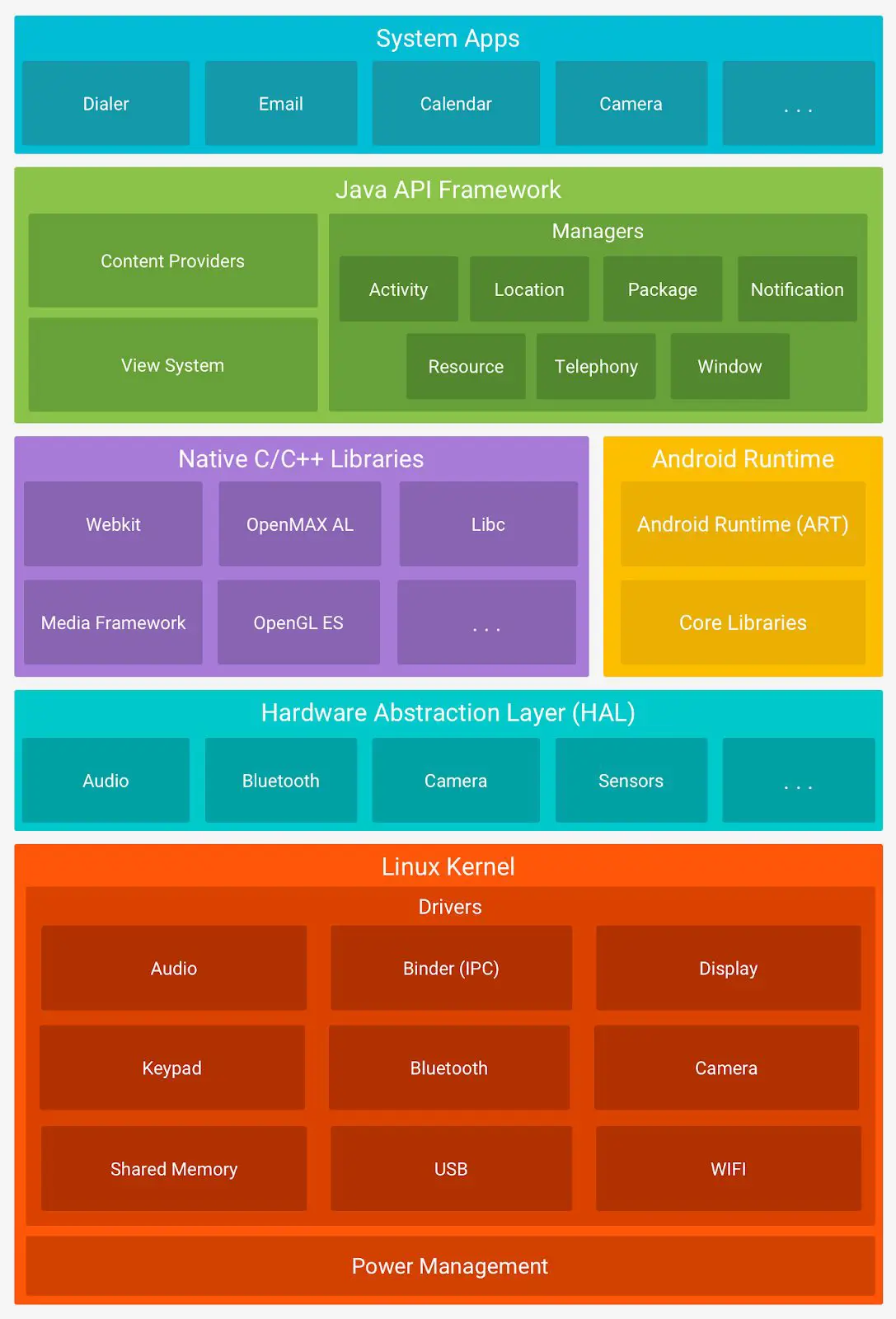
The software stack can be seen below.
What Tools Are Useful for Fixing Security Problems in Android, and How Are They Used?
Android has a massive variety of hacking utilities and pentesting apps that will assist with the testing and attacking of an Android device or application. We will look at some of the most popular ones and give a brief overview of what they can do and when they are likely to be used during the course of a pentest.
AndroRAT
Perhaps the most well-known tool in our list, Android Remote Administrator Tools is a very useful app that gives testers access to the information that they need when compiling a report and running through the objectives of their pentest. The app is server- and client-based and can be used over Wi-Fi and the Internet to connect the server and client devices to one another. Everything from call history to messages and system logs are accessible from within this app, and using it often reveals just how vulnerable a device is, giving pentesters valuable information about the state of security on a specific device.
Hackode
Hackode is a suite of commonly-used Android tools and can be used to initiate pentests directly from the device itself. SQL injection, Google hacks, DNS tools and a multitude of different exploits make this a Swiss Army Knife of an application.
zANTI
Yet another suite of handy hacking tools, zANTI brings a lot of network-based attacking tools to the table and is another good selection that can make pentesting much easier from a single device. It is able to provide pentesters with NMAP, port discovery, packet-sniffing and more.
cSploit
Another advanced toolkit for Android pentesting, cSploit is able to perform network scans and identify vulnerable targets on the network. It can also help pentesters establish if the target Android devices on their network are vulnerable to some of the common exploits that cSploit is able to launch.
Conclusion
Not all documentation for Android-specific pentests will be identical. The basic structure of a pentest report will have multiple headers that come as a result of testing separate components within the Android OS or an application that needs to be certified as being safe. This is done by collecting as much information as is possible during the testing phase and then compiling all of this data into a preliminary report. This report is then reviewed, double-checked and then edited into its final form, where it will be presented to the customer and expanded upon in a series of meetings.
Once the report has been issued, the customer will then take some time to remediate all of the highlighted issues and then request a follow-up consultation to ensure that all of the identified risks have been secured. This process will continue until all issues are resolved and the application is deployed to the intended target audience.
Sources
Android Platform Overview, GitHub
Cost effective assessment of the infrastructure security posture, IEEE Xplore

What should you learn next?
Security, Android Central