Noobz guide for setting up a vulnerable lab for Pentesting
Most of the people I know who are new to penetration testing want to hone and enhance their skills, but they have problems like:
- They don't have a target that is live and safe to penetrate.
- They have proposed and known targets but testing these targets is unethical and could put them in jail.
- They have questions like, "What is the best way to get a virtual machine lab up and running? What OS's should I use?"
- They haven't tried setting up vulnerable web applications like Mutillidae, DVWA (Damn Vulnerable Web Application), WebGoat, ExploitKB, etc.
- They thought that setting up a vulnerable lab is costly.
- They thought that maintaining and upgrading a hacking software lab is not that easy.
- They are afraid that they could get hacked too for setting up a vulnerable lab.
But don't worry guys! This article will guide you on how to choose a good hacking lab for penetration testing and will provide you with links of vulnerable distributions, vulnerable web applications, live and easy to customize pentesting labs, additional reading guides, and Do-It-Yourself (DIY) tutorials.

What should you learn next?
For me, the best and most practical solution to your problems if you are having a hard time getting a vulnerable lab is to choose free and open source software (I'm a FOSS advocate) and by choosing a bootable Linux distribution or a virtual image so that we can have multiple targets without paying a single penny. Also, there are bootable Linux distros or virtual images that are vulnerable by design and easy to set up. Most of these distros are Ubuntu or Debian based and with that it is easy for you to install packages if you want to customize these distros by using sudo apt-get install <package_name> command just like sudo apt-get install free-beer.
Thus, you need to download a virtualization package or software for booting up the live distro or the virtual image so that we don't need to multiple boot these operating systems and restart our PC every time we switch to a certain distribution. With virtualization we can just use one computer or a rig that is powerful (a computer that has good specs like having a 3GB RAM) for running the vulnerable virtual machines and minimize the risks of getting hacked because of added security.
Here are two common virtualization software packages that are free to download and are compatible with Windows, Linux, Mac OSX, Solaris, and FreeBSD:
1. Oracle VM Virtualbox (vbox or virtualbox)
2. VMWare Player (You need to register or create a free account with VMware before you can download this software)
After downloading the virtualization software of your choice, the next thing that you should do is download vulnerable distributions for you to hack and penetrate. Here are some of the vulnerable distributions you can try pawning:
- Metasploitable - a vulnerable VMware virtual machine based on Ubuntu that is released by the Metasploit team in order to solve your problem in learning the Metasploit framework. It focuses on network-layer vulnerabilities because it contains vulnerable services for you to penetrate.
- Hackxor - a web application hacking game built by albino. Players must locate and exploit vulnerabilities to progress through the story wherein you play as a blackhat hacker hired to track down another hacker by any means possible. It contains scripts that are vulnerable to Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Structured Query Language Injection (SQLi), Remote Command Injection (RCE), and many more. This VMware machine runs on Fedora 14.
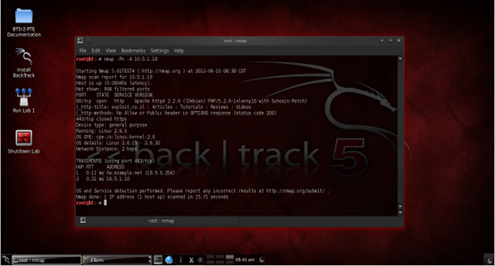
- BackTrack Linux 5r2-PenTesting Edition Lab - is a customization of BackTrack 5 r2 which has a modified version of NETinVM which has a predefined User-mode Linux (UML) based penetration testing targets. When started, this builds an entire network of machines within the VMware virtual machine. It comes with a pre-configured firewall, Exploit KB / exploit.co.il Vulnerable Web App, DMZ network with two hosts (targets), and an "internal" network with one host (target).
- Kioptrix - Kioptrix have three VMware images and challenges which require the attacker to have a root access using any technique in order to pawn the image.
- NETinVM - a Virtualbox or VMware image that runs a series of a series of User-mode Linux (UML) virtual machines which can be used for learning about systems, networks and security and is developed by Carlos Perez and David Perez.
- UltimateLAMP - a vulnerable VM image based on Ubuntu that has a LAMP server which focuses on web vulnerabilities. It runs on older and vulnerable versions of Joomla, Bugzilla, Drupal, phpMyadmin, Wordpress, Mutillidae, Moodle, and other known content management systems.
- LAMPSecurity - a series of vulnerable virtual machine images that are used for teaching and training an individual about the security configurations of a LAMP server. It is also a hacking dojo where you can play CTF's and contains pages that are vulnerable to SQL Injection and other known web vulnerabilities.
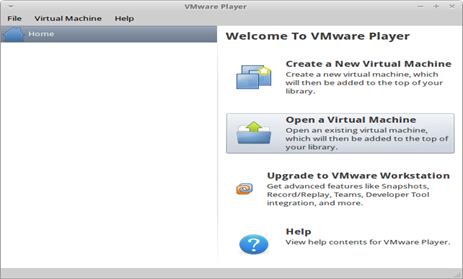
To install or run one of the vulnerable distributions in your virtualization software like VMWare, you need to create a new virtual machine (if it is a live CD) or open a virtual machine (if it is a virtual image). In this scenario, I will focus on booting up BT5 R2 Pentesting Lab Edition with my VMware player.
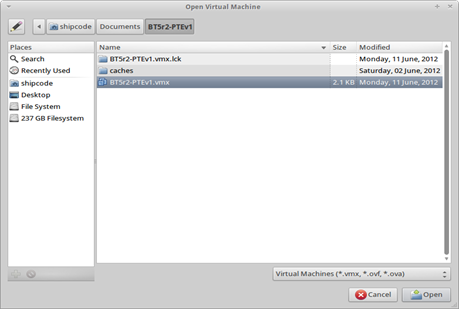
BT5 R2 Pentesting Lab Edition is a virtual image so I should choose the option "Open Virtual Image" then browse through the directories or the path where the virtual image is located and then click "Open".
The last thing you need to do is to click the option "Play Virtual Machine" and wait for the virtual machine image to boot up or start.
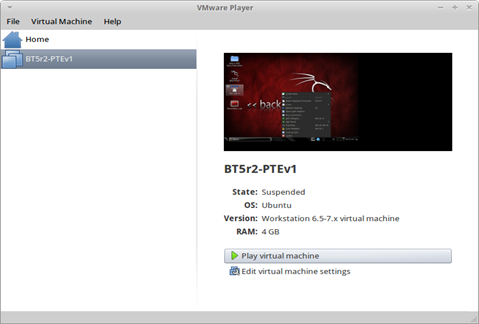

And because the virtual machine is already running, you can now start playing with it. You can refer to the official websites of the vulnerable distributions for their specific setups and cheat sheets so that you will be familiarized of the services that are running.
In order to beef up your pentesting lab, make sure you have a LAMP (Linux / Apache /MySQL, PHP / Perl / Python) server installed on your vulnerable system. Here are vulnerable web applications you can add to your system so that you have more challenges to your web application pawning experience:
- Mutillidae - a free and open source web application for website penetration testing and hacking which was developed by Adrian "Irongeek" Crenshaw and Jeremy "webpwnized" Druin. It is designed to be exploitable and vulnerable and ideal for practicing your Web Fu skills like SQL injection, cross site scripting, HTML injection, Javascript injection, clickjacking, local file inclusion, authentication bypass methods, remote code execution and many more based on OWASP (Open Web Application Security) Top 10 Web Vulnerabilties. I also wrote an article on how to setup Mutillidae its SQL Injection cheat sheet which can be found here.
- OWASP WebGoat - an OWASP project and a deliberately insecure J2EE web application designed to teach web application security lessons and concepts. What's cool about this web application is that it lets users demonstrate their understanding of a security issue by exploiting a real vulnerability in the application in each lesson. Dejan Lukan has a tutorial on how to set this up.
- OWASP Hackademic Challenges Project - is another OWASP Project that helps you test your knowledge on web application security. You can use it to attack web applications in a realistic but also controllable and safe environment.
- XSSeducation - is a set of Cross Site Scripting attack challenges for people learning about XSS or people who just want a good place to practice their already awesome skills. Various realistic challenges have been included for practice and it is still under development by AJ00200 but can already be downloaded.
- DVWA (Dam Vulnerable Web Application) - this vulnerable PHP/MySQL web application is one of the famous web applications used for testing your skills in web penetration testing and your knowledge in manual SQL Injection, XSS, Blind SQL Injection, etc. DVWA is developed by Ryan Dewhurst a.k.a ethicalhack3r and is part of RandomStorm OpenSource project. Dejan Lukan has also a tutorial on how to set this web application up.
- SQLol - is a configurable SQL injection testbed which allows you to exploit SQLI (Structured Query Language Injection) flaws, but furthermore allows a large amount of control over the manifestation of the flaw. This application was released at Austin Hackers Association meeting 0x3f by Daniel "unicornFurnace" Crowley of Trustwave Holdings, Inc. – Spider Labs.
- The BodgeIt Store - is an open source and vulnerable web application which is currently aimed at people who are new to web penetration testing. It is easy to install and requires java and a servlet engine, e.g. Tomcat. It includes vulnerabilities like Cross Site Scripting, SQL injection, Hidden (but unprotected) content, Debug Code, Cross Site Request Forgery, Insecure Object References, and Application logic vulnerabilities.
- Exploit KB / exploit.co.il Vulnerable Web App - is one of the most famous vulnerable web app designed as a learning platform to test various SQL injection Techniques and it is a functional web site with a content management system based on fckeditor. This web application is also included in the BackTrack Linux 5r2-PenTesting Edition lab.
- WackoPicko - is a vulnerable web application written by Adam Doupé. It contains known and common vulnerabilities for you to harness your web penetration skills and knowledge like XSS vulnerabilities, SQL injections, command-line injections, sessionID vulnerabilities, file inclusions, parameters manipulation, Reflected XSS Behind JavaScript, Logic Flaw, Reflected XSS Behind a Flash Form, and Weak usernames or passwords.
Conclusion
You don't need to pay a single penny in setting up a pentesting lab because there are a lot of vulnerable distros and web applications that are open source, free and easy to customize. All you need is virtualization software and virtual images in order to run a vulnerable lab. Read my additional articles below and my references for more information.
Additional reading (Articles I wrote similar to this guide):
- http://pentestlab.org/10-vulnerable-web-applications-you-can-play-with/
- http://pentestlab.org/setting-up-mutillidae-in-ubuntu-backtrack-backbox-etc-manual-sql-injection/
- http://blog.rootcon.org/2012/06/checking-out-backtrack-linux-5r2.html
- http://blog.rootcon.org/2012/05/hackxor-web-app-hacking-game.html
- http://blog.rootcon.org/2012/02/damn-vulnerable-web-app-installer-shell.html
- /vulnerable-applications/ (by Dejan Lukan)

FREE role-guided training plans







