Gaining Shell Access via UART Interface Part 3
This is the 3rd post in IoT-Hacking-Shell-via-UART series. I hope you have gone through the first two parts. If not, please go through them.
In this part, I will explain how I was able to gain shell access on a smart camera via UART interface.

FREE role-guided training plans
About the Device – I already had a camera with me. So, I decided to check the same for gaining shell via UART. The typical smart camera looks like the one shown below

On opening the camera, there were many components present on the board.
Some of the components found along with the pictures are shown below. These components may not be relevant to us, but it will give a small idea of various components which are present on a board.
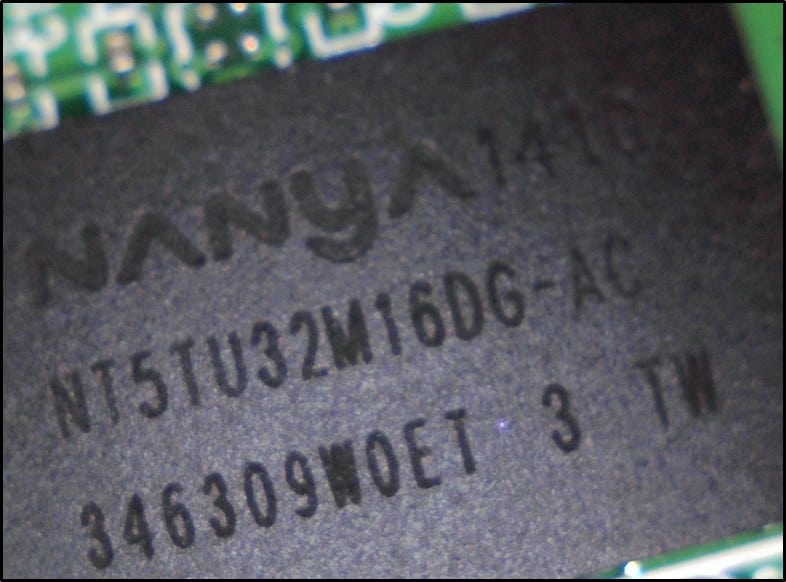
- NanyaNT5TU32M16DG-AC – 512 Mb DDR2 SDRAM
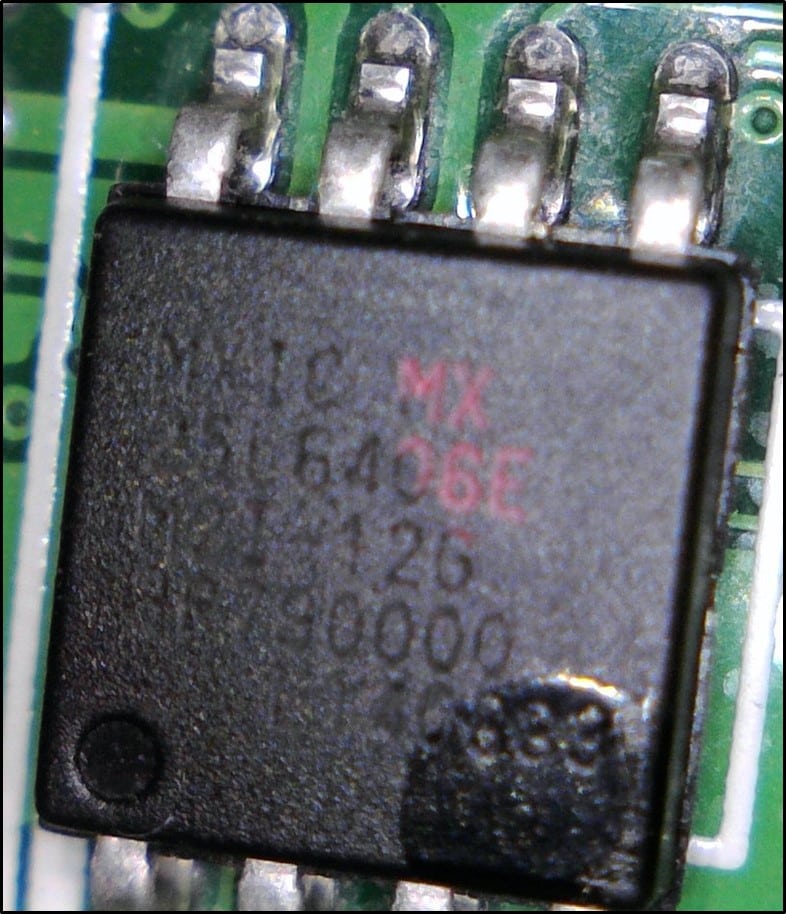
- CMOS SERIAL FLASH
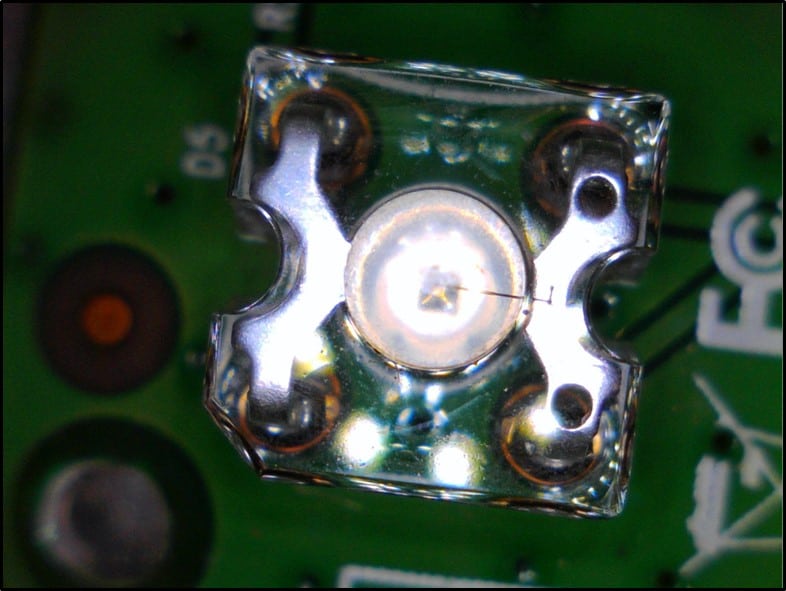
- IR LED
- LS 3N SS14 - Schottky Rectifier

- RTL 8188ER - SINGLE-CHIP IEEE 802_11bgn 1T1R WLAN

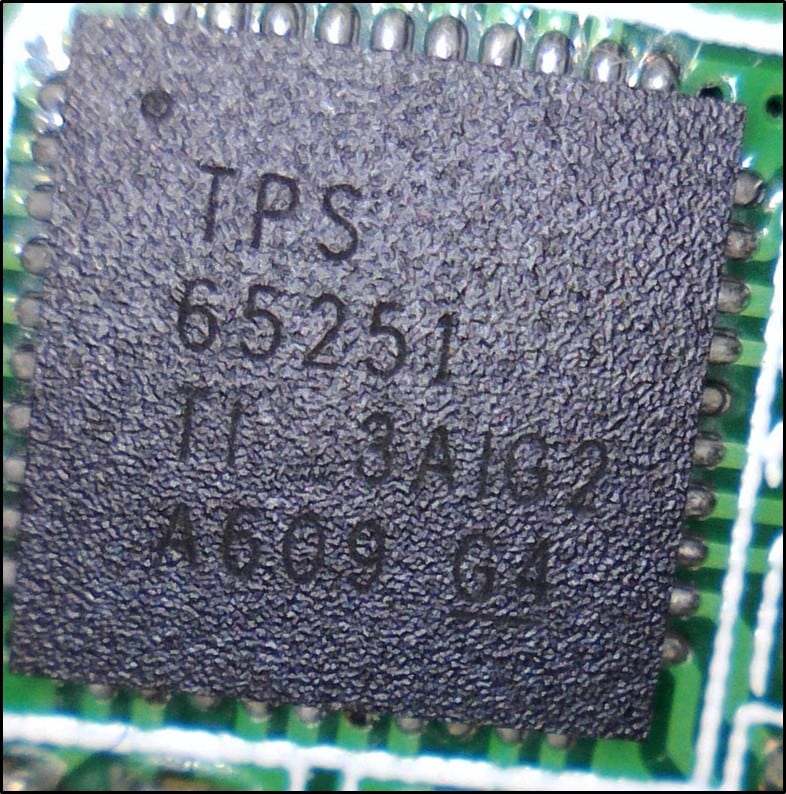
- TPS65251 - 4V to 18V Input High-Current Synchronous Step_Down Three Buck Switcher with Integrated FET
Above mentioned components were identified. The best way to learn about these components is to google search the letters or numbers printed on them simply. This will describe a component and what it does.
Gaining a shell via UART – Now the task is to gain a shell via UART.
The procedure for gaining the shell is as below -
On opening the camera, I found a UART interface present on it along with the components mentioned above.
Using a multimeter, I identified all the 4 pins –Vcc, Rx, Tx, and Gnd. Once they were identified using USB-TTL and appropriate wires, I connected the camera to my laptop as shown below –

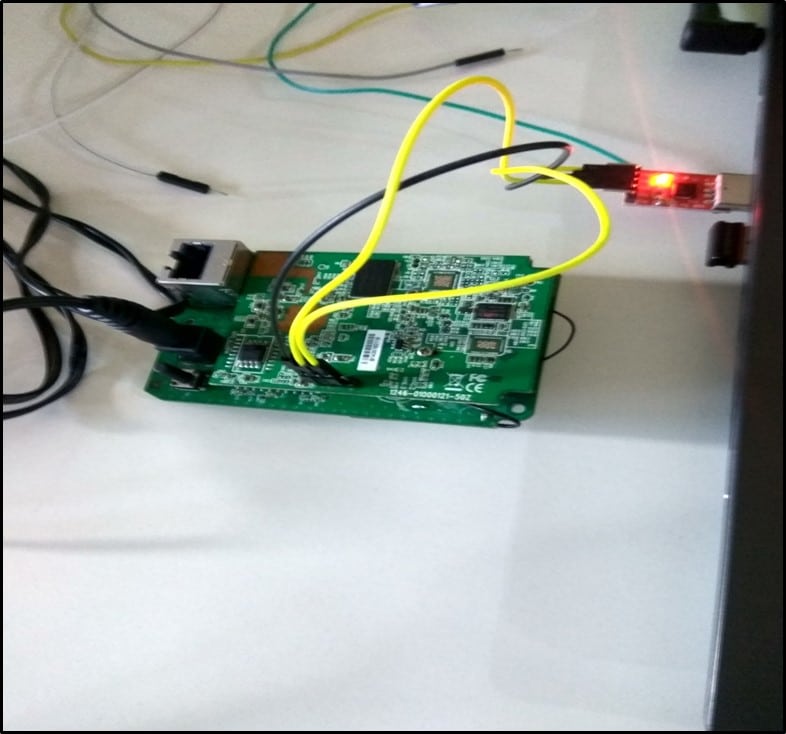
Connection Description –
- GND of the camera was connected to GND of USB-TTL.
- Rx of the camera was connected to Tx of USB-TTL.
- Tx of the camera was connected to Rx of USB-TTL.
I must identify the USB device name. By running the following command – ls /dev/tty* the device was identified as ttyUSB0 by the laptop.
Once the device was identified, I ran baud rate.py script for identifying the baud rate. The screenshot of which is shown below -
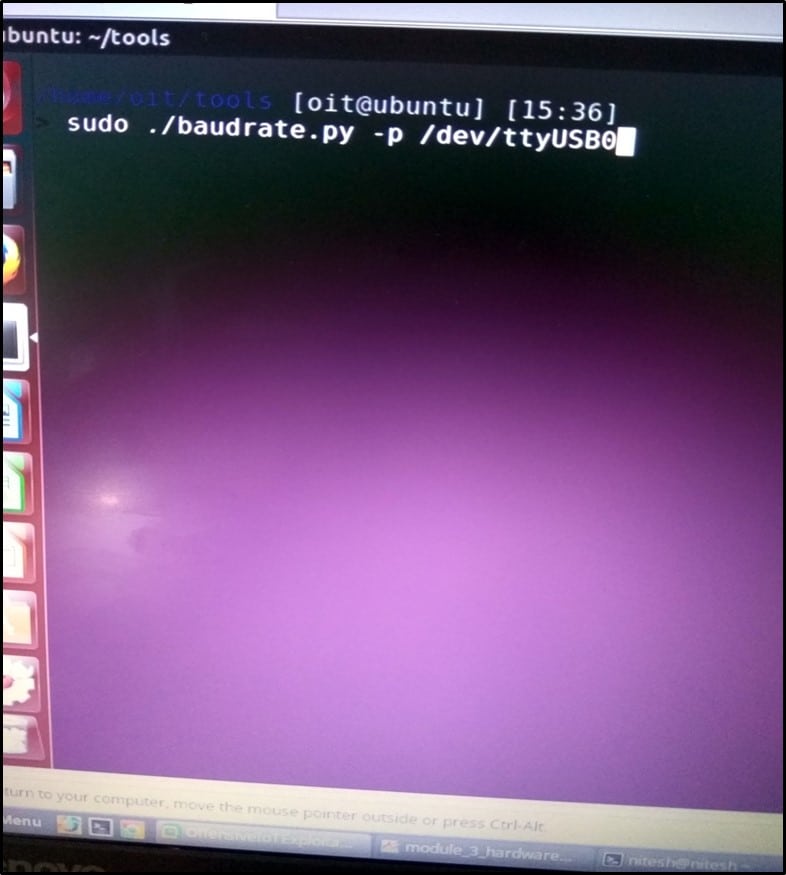
The baud rate was identified as 38400 as shown below –
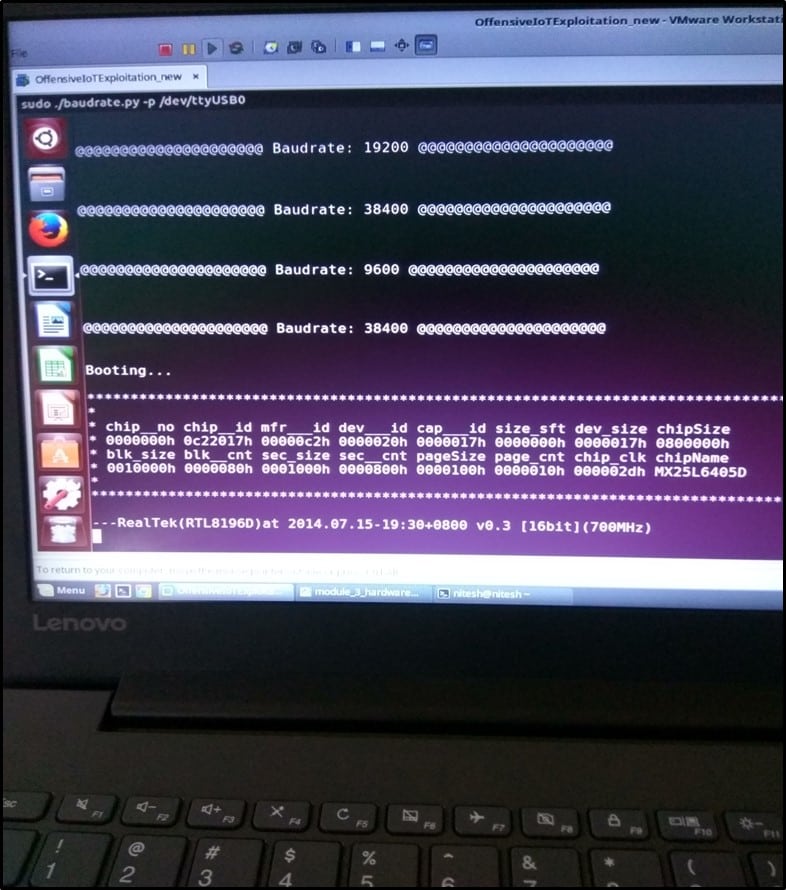
After the baud rate was identified, it's time to run the camera and monitor all the communication which happens when the device boots up.
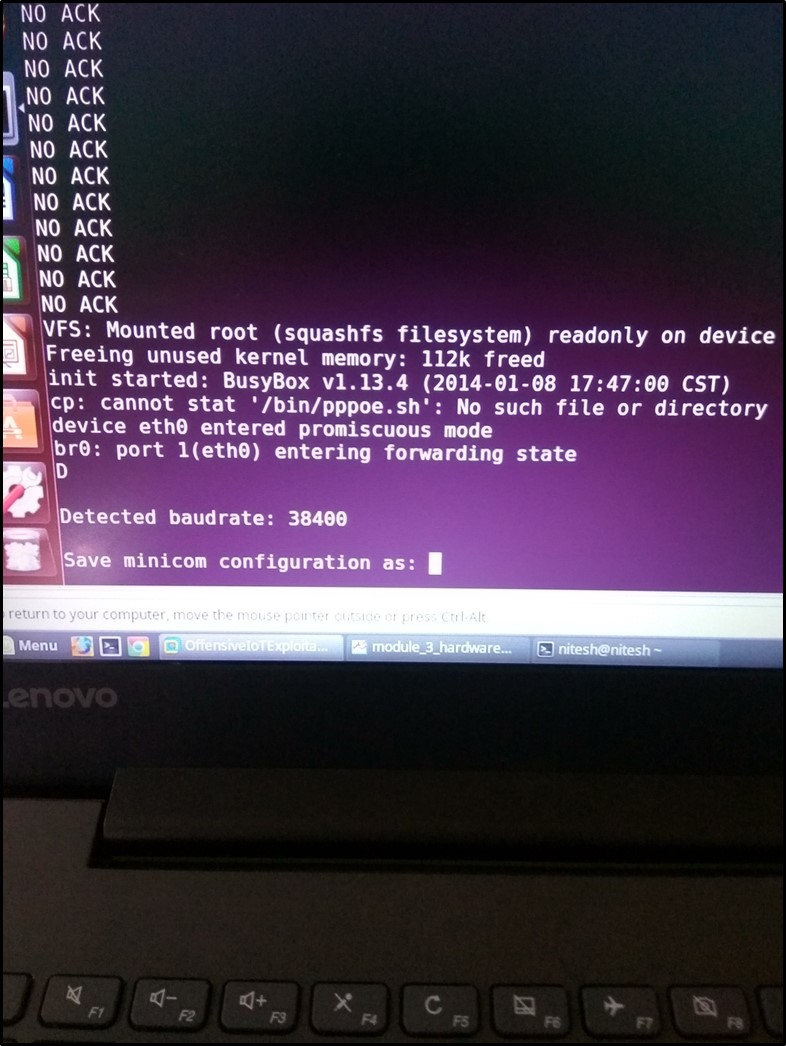
I turned on the camera using the above connection and ran minicom on my laptop. I gave 38400 as baud rate value to minicom. Once everything was set, I started the camera, and everything was being read in plain text. It shows our baud rate value is correct.
I booted the device 2-3 times but did not get any shell via UART. Tried pressing other keys like shift, Ctrl but all went in vain. After pressing "enter key" continuously while the device was booting up, finally, I got a shell on the camera as shown below –
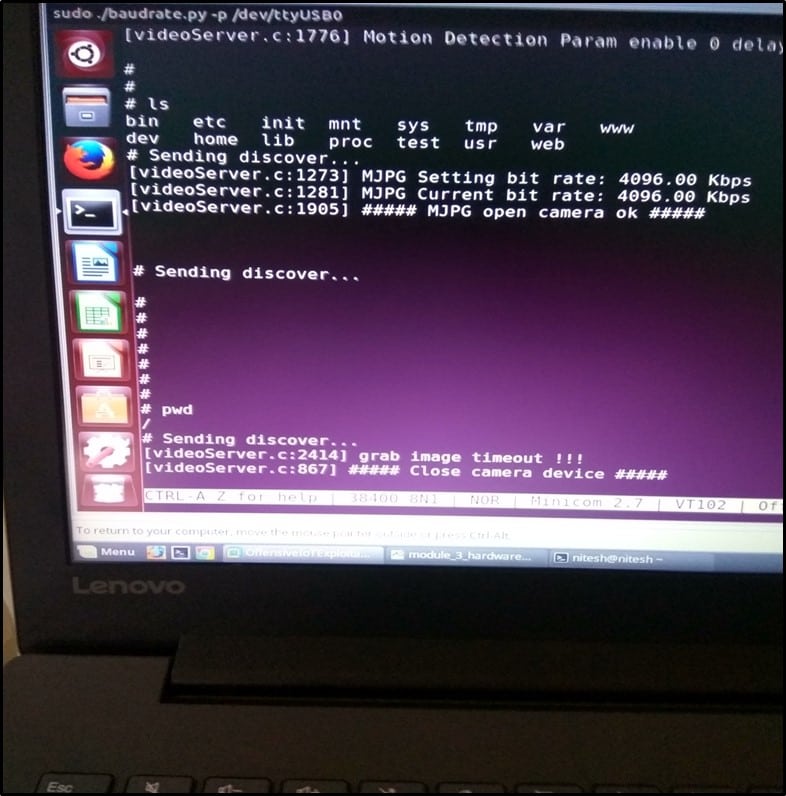
Once we have the shell access of the camera, we can run any command and skim through all the files present on the file system of the camera.

What should you learn next?
This is how can obtain shell access on camera via UART







