Enumeration of Heaps, Environment Variables
Continuing with the series, in this article, we will learn about enumeration of important structures like heaps, environment variables, DLLs pointed by main PEB. Just to recap in the previous two articles, we have looked at the way of finding the processes within memory and then enumerated structures like Page Tables, VADs, and PEB.
Dynamic Link Library (DLL)
DLL's are used to be shared among processes for code reusability. These get linked to process via dynamic linking, as dependencies of other DLLs and even via injection. Since DLLs lives under a process, they got full access to process memory space. A recap from the previous article on the 3 doubly linked lists that constitute of DLLs in memory.

What should you learn next?
Below is a structure _PEB_LDR_DATA which shows 3 doubly linked lists
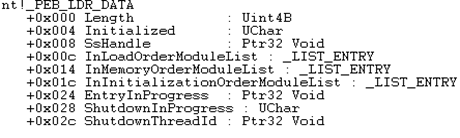
- InLoadOrderModuleList: Member of _PEB_LDR_DATA .This will organize executables/DLLs in the order in which they are loaded into a process. Process executable is always the first in the list.
- InMemoryOrderModuleList: Member of _PEB_LDR_DATA .This will organize executables/DLLs in the order in which they are loaded into memory.
- InIntializationOrderModuleList: Member of _PEB_LDR_DATA .Organized order in which DLLmain function is executed.
To list DLLs in memory, following Volatility plugins can be used
- dlllist: Dlllist plugin can be used to find DLLs loaded for a process of interest. Below is an example of DLL in action
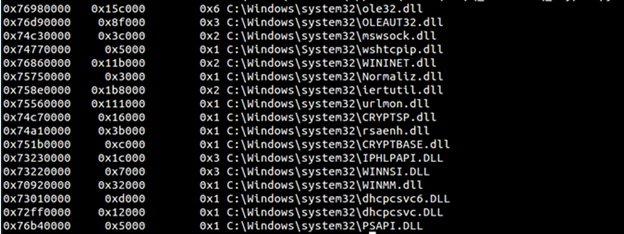
This plugin works after we got a process of interest from pslist plugin. To this plugin, the important parameter is to provide the process id gathered from pslist output and above you can see what all DLLs are loaded by this process. This plugin gives a really good indication of what this process is designed to do. For example in above urlmon and CRYPTSP tells us specifics about this process.
- ldrmodules: This is a very useful plugin to find out the hidden DLLs. Like explained earlier DLL can be easily hidden from the LinkedLists by changing the Flink and Blink pointers. Ldrmodules can list the DLL status in all 3 lists stated above in 'True' or 'False' column. Below is an example of ldrmodules in action
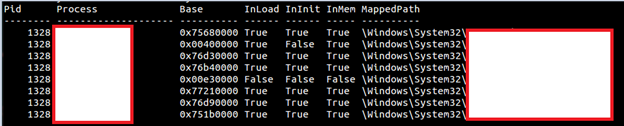
As you can see from above we get an idea that what all process can be traced in those 3 linked lists (described above). For example, it would be good to look at 2nd process I listing since it is missing in InInit List but present in both others. Also always keep in mind the false positives for these linked list order that we discussed in Part 2. Also, we can use Volatility plugin named malfind to look at the unmapped executables and those contain PAGE_EXECUTE_READWRITE permission and look out for code in the memory. Below is an example of malfind in action
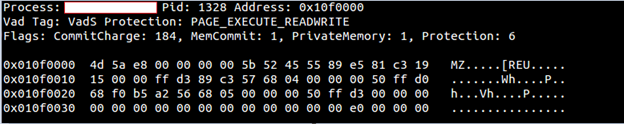
Remember the Protection Flag covered in part 2 of this series and the Vad Tag. What does this tell you about this output? Also, notice that there is an 'MZ' header which denotes that it is executable code in that region of memory.
- dlldump: So you find the dll that looks of particular interest to you. How would you see what's inside the dll? One way is to dump the dll and then investigate it with other tools. Dlldump does the same job for you. However, there are chances when you are not able to dump DLLs because base have been swapped out, and you will get error similar to below:
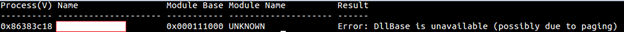
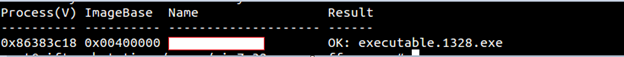
- procdump: Used to dump a process executable of particular interest. It can be done either with supplying –-pid or with _EPROCESS offset. As you might have guessed and with what we discussed in the previous article, you can find dump hidden processes this way.
Environment Variables
Environment variables are very critical for a process, and if they get manipulated, it is mayhem. For example, you have some docx file that is known a type and Explorer knows which application should open the file. IF PATHEXT variable gets manipulated to open docs with a certain executable, then potentially a malicious one will run. Also, some important points between parent and child process like child inherit PEB from its parent needs to be remembered.
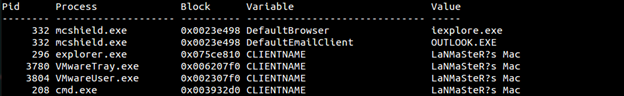
With volatility, we can look at the environment variables loaded for an image. Below is an example of plugin envars in action.To suppress all the noise (known variables) use the --silent option. Below is an example of listing the environment variables with the –silent option
Heaps
Analyzing heap contents of a process sometimes gives greater insights and volatility gives a plugin for the same. If you recall from the previous article we have used vaddump to dump the vadtree. If we have found a process of particular interest and are interested in analyzing the heaps of the process we can use Volatility heaps plugin with the process id and find out some important parameters in the output.

FREE role-guided training plans
Conclusion
So in these 3 article series, we have seen _EPROCESS structure, PEB, Linked Lists; how to parse these structures using Volatility plugins, etc.







