Cracking a Wi-Fi WPA2 Password, Thanks to Amazon
In a pen tester's life, sooner or later you are cracking a password. This activity depends on the type of password and available hardware.
Today I want show you a different approach to cracking a password. We will focus on how to crack a Wi-Fi WPA2 password.

FREE role-guided training plans
First of all, it's important to define this. WPA2 is the most secure protocol that currently exists, as long as it is well-configured with the latest encryption techniques. Nevertheless, I say that WPA2 is the most secure – not that it isn't hackable. Thanks to the MiTM attack, it is possible to extract an encrypted password. Did you know that?
I will show you how to redefine an attack on a Wi-Fi password and apply a new approach where resources are potentially unlimited and cost effective.
How many attacks are you familiar with to crack a WPA2 password?
The first that comes to my mind is bruteforcing. But this system wastes resources and we have to live forever to get the results. Not very effective. Let's start to verify what we need…
We need to get a wordlist. Usually in this stage, someone uses data reconnaissance from a company website or social network account and uses words commonly found to create a combination of likely words.
This approach works if you are very lucky. We don't need to be lucky; hackers make their own luck. Let's see what happens when we try to create a word list with Crunch.
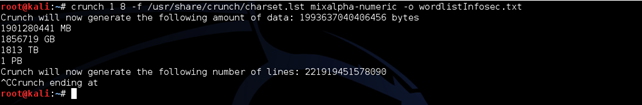
1PB! We don't have this free space on our hard disk.
Who says that we need to store the word list? We can use it in real time…
How? For example, we can use Crunch in Pyrit with pipeline.
Crunch generates all combination of 8 characters, piping the results to Pyrit that will use them to pass through the attack to a .cap file.
Again, the result of this little trick is smart, but it is not efficient. The timing is still too long, and we can't wait forever. In a real case, we might even wait some years.
Did someone think to CUDA Pyrit? Yes we can use it, but not on your client laptop or PC. If you are curious and you want try it and use it for your own Kali, follow this link: http://www.blackmoreops.com/2014/03/13/install-nvidia-driver-kernel-module-cuda-and-pyrit-kali-linux/.
CUDA is a powerful kit that boosts your Pyrit by using GPU instead of CPU.
Pyrit has an awesome feature that allows you to attack a capture usign preloaded database. It's important because it does it by millions per second and creates a table similar to a rainbow table.
In a word, it escalates; meaning we can potentially break any length WPA2 password.
Based on what we did previously, we are going to make this in 3 steps.
Creating a word list length 8 characters: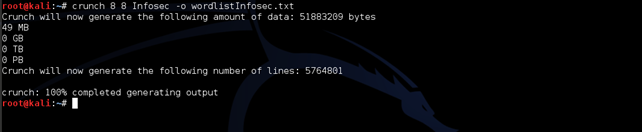
Upload the word list created to Pyrit DB and create own "rainbow table" (is not a true rainbow table): 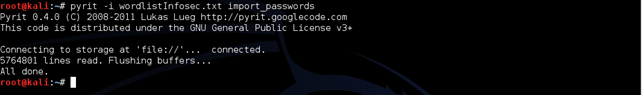
Once a password has been imported, we can run a batch command to create a DB.
Simply digit: # pyrit batch
At this time, can we start the attack to the .cap file of the password.

The time of execution required is the same as before with the pipe approach. We don't have the scalability to execute it in a right manner. It's necessary to use something more powerful, but buying a new graphics card is not a right solution.
Amazon will help us….
AMAZON LINUX AMI
Amazon provides other kinds of web services, including AMI. The Amazon Linux AMI is a supported and maintained Linux image provided by Amazon Web Services for use on Amazon Elastic Compute Cloud (Amazon EC2). It provides a stable, secure, and high performance execution environment for the NVIDIA GRID GPU Driver AMI, which allows application developers to run NVIDIA GeForce-optimized games and applications from the cloud on Amazon EC2.
Amazon Web Services provides ongoing security and maintenance updates to all instances running Amazon Linux AMIs. But I don't want to get lost in explanation about Amazon AMI. You can find more information here: http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/AMIs.html.
AMI gives us a possibility to escalate to the power level that we need. It uses the GPU graphics card instead of CPU, increasing computational calculation.
When you buy the first AMI, it's empty, without the tools that we require. To do a good job, we'll require Python, CUDA Pyrit and Crunch.
In this case, we pay Amazon for the hours that we use, we can't lose time! So first, before we buy AMI services, we need to prepare a ready package with own tools inside.
If we start a benchmark test on Linux AMI we can see soon the difference. Now we have what we want!
Now we can still hack into, potentially, any WPA2 passphrase length. Yes, potentially… we are still at too much time to crack with only one AMI, we need many AMI machines to connect all together and create a distributed service. If we use more AMI servers, we have the maximum escalation possible.
We don't need too much power for now. I want explain how to crack a password with minimum effort possible.
If you look at online documentation, all theories say to use Crunch to create a huge word list and Pyrit for distributing loads to other AMIs. But there's a little trick for this.
Step one
Prepare your right tools for the job. We don't create a production machine but only a template for saving time and performing multi-creations.
Step two
Create a small portion of the word list. This is the main part of the trick ;-) . We don't know the maximum value of our word list, so we can ask it to Pyrit. If we input a huge value, it will return a maximum value accepted, and this is our number!
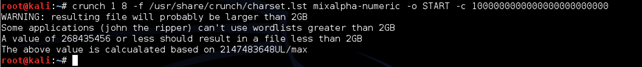
Pyrit tells us that it's too huge a value, and returns the correct parameter as 268435456.
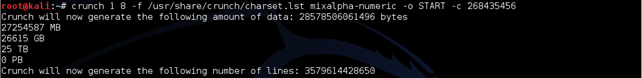
Now we need to put our attention on the size of file created and stop it before we run out of space. To amplify it, start a new VM and continue where we left off.
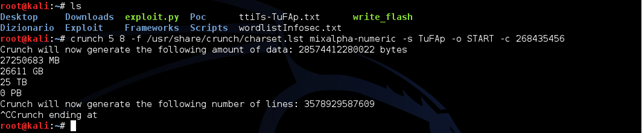
We see the new file called yyyyy-bbbbb.txt. We'll need to start from there, check the number of characters, in this case 5, and restart Crunch with the new command.
Step three
Upload all the files to the Pyrit database with the same command used before. You could generate the word file offline and afterward upload it on VM. This way you won't take up space with useless files. You will upload to one VM and pass it to Pyrit and do manual distribution to other VMs.
Step four
Save the VM as a template. This step could you save time the next time. Go to your EC2 management console, choose the instance (all the instances pre-loaded with the word list), give it a name and choose "create image".
Step five
Launch all the instances, insert the ESSID in Pyrit, and run the batch.
Conclusion
All the steps might take some time. VM creation, word creation, and uploading to Pyrit database are done just one time. The challenge here was to see how to improve the strategy to crack a Wi-Fi password.
The new clouds and processing power will give us the possibility to perform an attack faster than before and get the best results. Amazon is only a third party actor, and maybe some contract policy now could deny the scope of this paper.
Amazon is an excellent company, and I want to underline that this guide is not for bad things, but a demonstration on how the new technology could be used to perform an attack.
I want say thanks to Bruno Rodrigues, the author of this hack.
Resources
http://uk.reuters.com/article/2011/01/07/us-amazon-hacking-idUKTRE70641M20110107
http://www.zdnet.com/article/researcher-uses-aws-cloud-to-crack-wi-fi-passwords/
http://www.infosecisland.com/blogview/11018-Cracking-WPA-Protected-WiFi-in-Six-Minutes.html

FREE role-guided training plans
https://kakkulearning.wordpress.com/2014/05/25/using-amazon-ami-cracking-wpa2-wifi-hack/







