Android penetration tools walkthrough series: MobSF
This article reviews the step-by-step procedures for deploying a Pentesting tool called "MobSF," which is utilized primarily on the Android OS.
MobSF is an open-source and intelligent tool that can be used to perform both static and dynamic analyses on Android and iOS platforms. It can also assist with Web API Security testing with its API Fuzzer, which can perform the following functions:

What should you learn next?
- Information Gathering;
- Analyze Security Headers;
- Identify Mobile API specific vulnerabilities such as XXE, SSRF, Path Traversal, IDOR;
- Monitor other logical issues that are related to both Session and API Rate Limiting.
The Installation procedures of MobSF are as follows:
Requirements:
- A Virtual Box
- A Linux VM // Install in Vbox
- MobSF VM ova file (for dynamic analysis) // Import in Vbox
Setting up static analyzer
Step 1: Open the Linux VM.
Step 2: Run the following command line order to install the server (this is also illustrated in the screenshot below):
git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF.git
cd Mobile-Security-Framework-MobSF

Step 3: Ensure that Python 3.6+ is installed (Link to download).
Step 4: Install the Python dependencies. These are present in the "requirements.txt" file. Execute the following command line (this is also illustrated in the screenshot below):
pip install -r requirements.txt

Step 4: To run the MobSF server, execute the following command line (this is illustrated in the screenshot below):
Python manage.py runserver

Step 5: Open a web browser, and the web interface appears at port 8000.

Setting up dynamic analyzer
Step 1: Import the Android VM- MobSF (.ova) in Vbox, as illustrated below: (NOTE: The password is 1234)

After the first step has been completed, you should get the following screenshot:

Step 2: Change the network settings as illustrated below:

Step 3: When the VM is launched, the IP set to 192.168.56.101., as seen in the screenshot below:
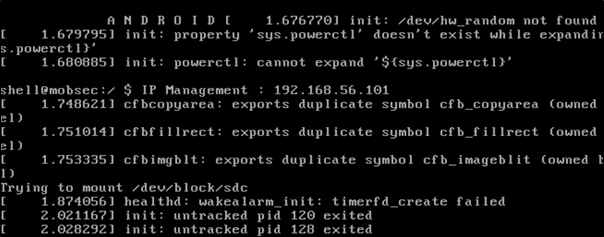
Step 4: Confirm that the IP for the VM is set to "host-only network," as seen in the screenshot below:

The IP in steps 3 and step 4 should belong to the same network. If not, follow these substeps:
- Go to the virtual box;
- Click on "File";
- Select "Preferences";
- Set the IP to be on the same network.
Step 5: To save the VM state, right click on it, and select "Open in Browser." There will be a file with a ".vbox" extension. You can open it in any text editor, and from there, record the UUID and the current snapshot ID. This is illustrated in the screenshot below:

Step 6: Go back to the Linux box and from there, go to the "MobSF/settings .py" file. You will see the dynamic analyzer settings in this file and change them to the following permutations:
- VM_IP: Change it to the one noted in step 3;
- Proxy_IP: Change it to the one noted in step 4;
- UUID: Change it to the UUID noted in step 5;
- SUUID: Change the current snapshot ID to the one noted in step 5.
This is all demonstrated in the below three screenshots:



Static analysis
Static analysis deals with analyzing the dead source code without running it. The diagram below displays the architecture of the static analyzer that is found in the "MobSF."

This specific analyzer can accept and further break down the. apk files as well as the Java source code. These could be formulated in either Eclipse or the Android studio. Once the files are uploaded, the analyzer then starts the process of examining the files and the code. All of this can be seen in the server terminal window.
The following is a demo example:
For this specific purpose, the DIVA application has been utilized, and is executed as follows:
Step 1: Run the server (refer installation) and from there, launch the web browser to upload the application. This is illustrated in the screenshot below:

Step 2: Once the analysis starts, check the terminal where the "runserver" command line was executed. This is illustrated below:

In the screenshot below, you can see the operations that are being performed on the application. If there are any errors, they can be tracked down here at this point and corrected.

The analyzer will automatically generate a report once it is done conducting the analysis. This can be seen in the screenshot below:

As can be seen, the report is divided into multiple tabs. The first one is the Information tab. It displays data such as the app icon, the app name; its size, package name, etc.
The MD5 and SHA1 are also shown. They can be useful to detect known malicious applications.
With the scan options, you can choose the following activities:
- Rescan the application;
- Start the dynamic analysis;
- Check the java code and the manifest file.
This is illustrated in the screenshot below:

The screenshot below is a sample manifest file generated by the analyzer. As can be seen, there is a lot of information that can be gathered, such as the permissions that are required.

The screenshots below display the certificate information. This is used to determine if an application has come from its original source and that the integrity of it has not changed.


The Android permissions and the results of the binary analysis are present in the manifest files, as illustrated in the screenshot below:

The API information is used for black box testing purposes on the application itself. The Java files contain the following details:
- The interprocess communications,
- SMS APIs;
- Crypto services;
- Broadcasting APIs.
These details are illustrated in the screenshot below:

This tool also performs code analysis, such as:
- How the logs are getting stored;
- The storage of any sensitive data;
- Database encryption;
- The detection of any malware.
These functionalities are illustrated in the below two screenshots:

Dynamic analysis
 Dynamic analysis is performed by executing the application in either a real device or a simulator. The collected information is then examined for:
Dynamic analysis is performed by executing the application in either a real device or a simulator. The collected information is then examined for:
- Sensitive data access
- hardcoded details
- traffic analysis
- insecure requests.
Though this requires manual intervention, it is much more efficient than intercepting the traffic at each step and performing the analysis. For demo purposes, the MobSF VM is being utilized. You also have an option to choose the VM, arm it, or read the actual device. The actual testing is done with real devices; the VM may be too slow in the application at various points in time.

The process mentioned above is illustrated in the above diagram, and is detailed as follows:
- Flash and run the APK on the device. The application will automatically start once loaded;
- Agents are invoked in to collect the information pointers;
- Share the result and the application data;
- Start the HTTP(s) proxy;
- Collect the results of the HTTP(S) traffic.
The following is a demo example:
- Select the option to start the dynamic analysis in the static analysis report. The status will then be updated, and the application will then be flashed on the Android screen.
- Once the application starts, there will be multiple options to:
These steps are illustrated in the screenshot below:

Once the application starts, it is then important to iterate through the various flows of it and try all the possible options so that the needed information can thus be collected. This is illustrated in the screenshot below:

Once this process has been completed, the report for the dynamic analysis will then be generated and displayed. It has tabs for the following:
- HTTP(s) traffic;
- Log analysis;
- API analysis;
- Application analysis.
These functionalities are illustrated in the screenshot below:

The API monitor has further subdivisions in the report for the following items:
- File operations;
- Crypto options;
- Dynamically invoked URLs, emails, process calls, etc.
These functionalities can be seen in the screenshot below:

The log files can then be viewed for further analysis. They can be used to find stored tokens, hardcoded strings, etc. This can be seen in the screenshot below:

One of the strongest advantages about MobSF is its capability to perform both static and dynamic analysis. The report can be then downloaded later to conduct further analyses.
MobSF also reduces the time that is needed to pen test an application. This is achieved by using various other tools and its capability to analyze smaller files and flows.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.







