Blackbox Assessments with Introspy
This article explains how to start performing black box assessments on Android applications using Introspy. Introspy is one of the important tools in an Android pentester's arsenal.
As per their official Github page, we can use the "Blackbox tool to help understand what an Android application is doing at runtime and assist in the identification of potential security issues".

FREE role-guided training plans
The following figure gives a quick overview of how Introspy for Android works.
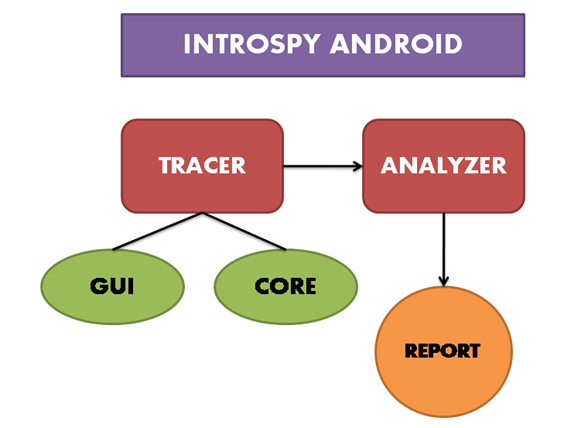
Introspy consists of two different modules:
-
Tracer:
GUI Interface
GUI Interace is used to configure hooks. We can select the target application(s) and the tests we want to perform and other options using this GUI Interface.
Cydia Substrate Extension(core):
This is the heart of the tool and can be used to hook into the application and analyse it at runtime to identify vulnerabilities. -
Analyser:
Analyser can be used to analyze the database generated by Tracer and to get well formatted reports.
Now, let's see how we can use Introspy to do blackbox assessments on Android apps.
Getting ready with setup:
-
Download Introspy Tracer
Introspy Tracer can be downloaded from the following link. - Download Introspy Analyzer
Analyzer can be downloaded from the following link.
https://github.com/iSECPartners/Introspy-Analyzer -
Before proceeding, we need to install Cydia Substrate for Android. We can directly download it from Android app store and install it as shown in the screenshot below.

- Now, install "Introspy-Android Config.apk" and "Introspy-Android Core.apk" which we have downloaded in step 1.
Commands to install using adb:
adb install Introspy-Android Config.apk
adb install Introspy-Android Core.apk
Now, we should have all the things set in our device and you should see the following icons on your device.

Now, let's begin performing hooking and analyzing the target application.
-
Launch "Introspy Config" and choose the target application to be analyzed. In my case, I am using an application which uses shared preferences to store and retrieve data.
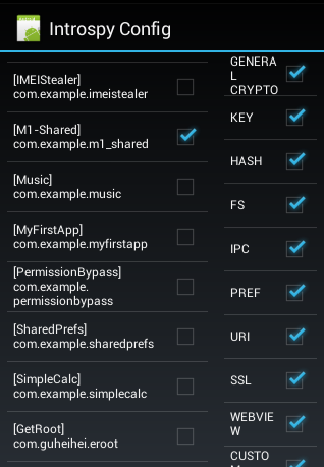
As we can see in the figure above, the name of the application is M1-Shared and package name is "com.example.m1_shared".
The following screenshot shows the file system before hooking into the app. This is needed to understand what happens after hooking into the app.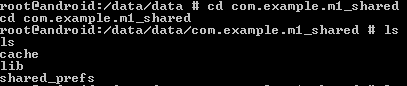
-
After selecting the target application, it is ready to get analyzed. We need to browse it as much as possible to cover the entire functionality of the app.
-
Once we are done browsing the app, the database with the analysis results must be ready in the same directory of the application package. So, let's navigate to the app package, and see if there are any changes.
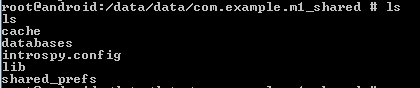
As we can see, a new folder with the name "databases" has been created. We should see a file called "introspy.db" inside this folder.
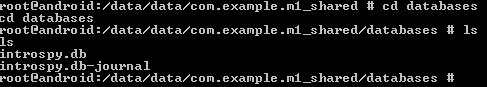
-
We need to pull "introspy.db" file onto our system in order to analyze it. I am copying it onto my device's SDCARD and copying the file onto my system from there as shown below.

-
Now, we can analyze the database using "introspy-analyzer" which we have downloaded earlier. Navigate to "Introspy-analzer-master" folder and run "introspy.py" file with "–h" switch to see the options available.
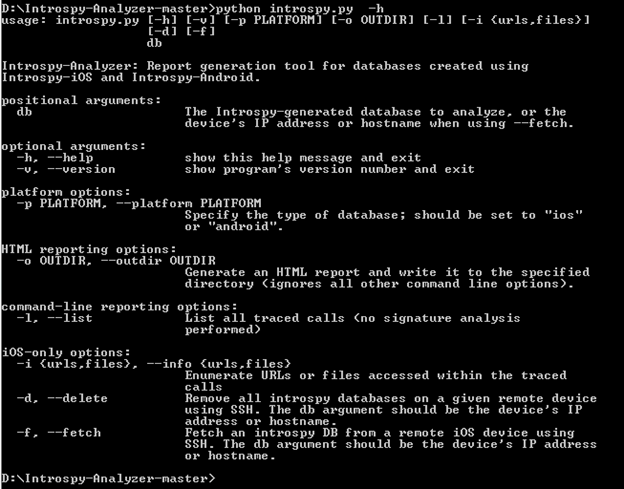
-
Now, place the "introspy.db" file we pulled from the device in the current folder where "introspy.py" is located and run the following command to generate an HTML report.
python introspy.py –p [platform] –o [output folder name] databasename.db
-p is to specify the platform. "android" in our case.
-o is the output folder name in which the report is going to be saved.

-
The above step should create a new folder named "outputreport" with the HTML report placed inside it as shown below.
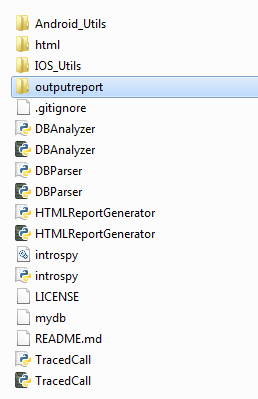
-
Navigate to the "outputreport" folder and open up the "report.html" file with your favorite browser to see the well formatted report of the analysis performed. This is shown in the figure below.
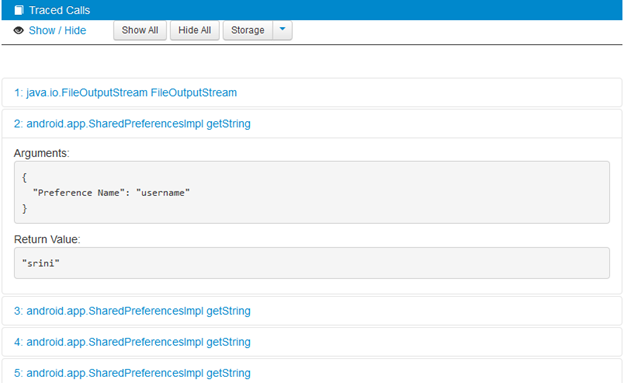
As we can see in the above figure, it has traced the shared preferences calls and reported them as issues. Now it's our job to check things like how the data is being stored in the XML file, whether the data is really sensitive or not, etc.
- We can also check out the analyzed report using command line as shown below.Command:
python intropsy.py –p [platform] –l databasename.db
-p is to specify the platform being used. "android" in our case.
-l is to list all the traced calls.
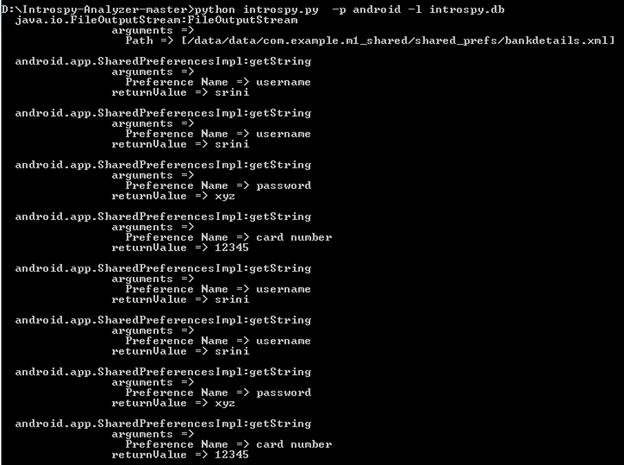
As we can see in the above figure, a detailed report has been generated right on the command line.
Conclusion

What should you learn next?
In this article we have seen how we can perform black box assessments on Android applications using Introspy. This article has given a glimpse of how one can set up to begin assessments with Introspy as well as a demo with a sample application. Introspy is a more powerful tool than what we have seen in the demo. You can go ahead and try analyzing various apps to see the power of Introspy.







