A Beginner’s Guide to Setting Up an SNMP Pentest Lab Using Vyos and Pfsense
SNMP often provides a great deal of information during the information gathering phase of a penetration test. It is often seen that SNMP protocol is commonly misconfigured, thus causing information leakage. Though it is an old protocol, this article aims to show how readers can set up their own lab to understand various SNMP misconfigurations. We will also see how to assess the security of these misconfigured hosts from pentester's viewpoint in a later article.
What is SNMP?
SNMP stands for Simple Network Management Protocol that is used for exchanging management information between network devices. SNMP allows an administrator to gather information about the host on which SNMP is running. It is also possible to modify this information.

What should you learn next?
Managed devices such as routers, hubs, switches, servers, desktop computers are usually configured with SNMP protocol. An SNMP configured device often includes an Agent, which does functions such as collecting information about the environment which can be later used by other utilities.
MIB and OID
MIB stands for Management Information Base. An MIB is a collection of Information for managing network element.
The MIBs comprise of managed objects identified by something known as Object Identifier (OID). OID consists of a series of numbers or strings separated by dots.
Specific information from the device can be queried using these OIDs. The OID can be globally the same for multiple devices. It is also possible that a vendor can customize it, as they like.
For example, a quick Google search for "SNMP OID for sysName" shows the following result from Cisco.
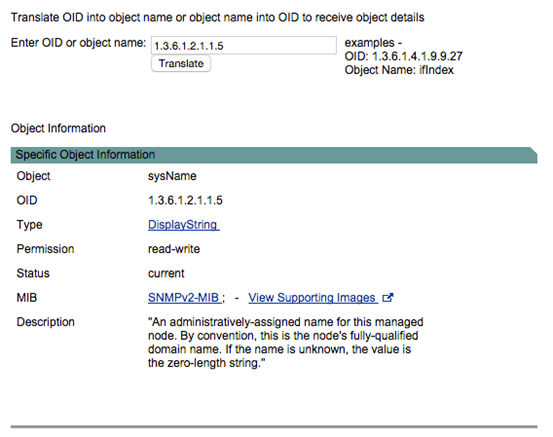
In a later article, we will see how we can use the above OID to query sysName from VyOS and pfSense.
When we query for an object, the return value of each identifier could be different depending on what we are querying. e.g. Text, Number, Counter, etc.
Lab setup
Most of the time we see these SNMP misconfigurations on routers. For the same reason, this article focuses on setting up a lab using a routing device.
The following lab is set up using Virtualbox. We will use two different scenarios as described below. We will use both VyOS and pfSense to provide more options to the readers. Kali Linux is the attacking machine in both the cases.
Scenario 1:
We will configure VyOS as one of our target devices with SNMP misconfigurations. We will configure VyOS with "public" as its community string with "rw" authorization.
Scenario 2:
We will configure pfSense as our target device with SNMP misconfigurations. We will configure pfSense with "public" as its community string with "ro" authorization.
Configuring VyOS
Note: Earlier, VyOS was earlier known as Vyatta. Vyatta Inc. acquired by Brocade in 2012 and the names have been changed with certain changes. A fork of Vyatta called VyOS has been made available for the open source community.
VyOS can be downloaded from the following link
http://vyos.net/wiki/Main_Page
Create a new VM with VyOS ISO image in your Virtual box.
Once it boots, it will ask for the credentials.
The default username and password to login is "vyos" and "vyos"
We are ready to configure VyOS and let's begin with configuring the interfaces.
Type the following command to check the details about the current interfaces.
show interfaces
It shows the following output.

As we can see, currently we don't have any IP addresses configured at eth0 interface.
To start configuring anything in VyOS, we need to type the command "configure". Then configure what you need. Finally, enter "commit" to save the changes and exit by typing the command "exit".
The following figure shows how to setup an IP address manually on the interface eth0. You can hit tab button to get help from VyOS.
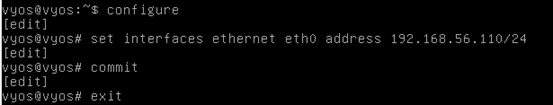
As we can see in the above figure, we have assigned the IP address 192.168.56.110 to eth0 interface. We will use this interface to interact with Kali box.
We can cross check the configured interfaces using "show interfaces" command.
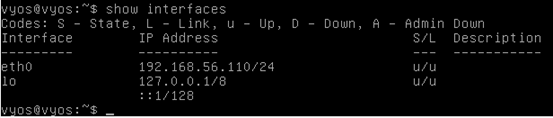
Let's check the connection from kali Linux by pinging this IP.
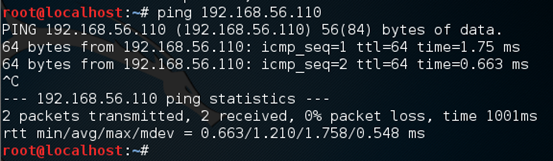
"Mis"configuring the SNMP Service
Before we configure SNMP let's check if any services are already running on this box.
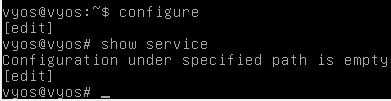
As we can see, there are no services configured currently.
Now, let's see how to configure SNMP service for our lab. As mentioned earlier, to configure anything in VyOS, we need to begin with "configure" command.
We can get help from VyOS by hitting the tab button as shown below.
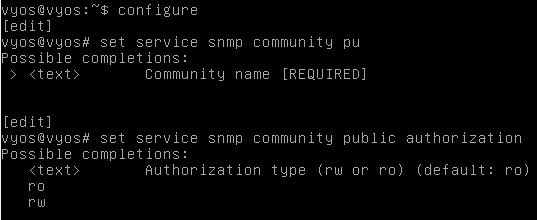
To configure SNMP, you can directly type the following command as shown in the figure below.
set service snmp community public authorization rw
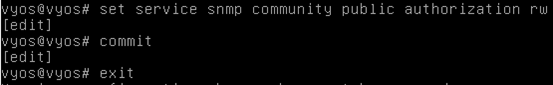
We are basically setting up the SNMP service using "public" as it's community string and "rw" as it's authorization.
SNMP Community String is like a password. Querying information via SNMP requests is possible if we know the community string being used by your target. "public" is the default community string that is often used by most of the vendors.
In the above figure, we have configured it with "rw" authorization. This means, anyone with the community string "public" can read the configuration details. Writing is also possible. This is really worrisome if you find it in production systems exposed to other hosts over the network.
Let's cross check to see if the changes have been reflected. We can check it by typing the following command.
show service
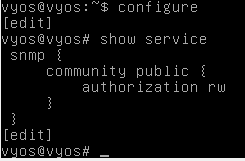
Everything is set. Now, let's do a quick nmap scan from Kali box to see if SNMP service has been started.
SNMP service by default runs on UDP port 161. So, we need to run nmap with UDP scan option as shown in the command below.
nmap 192.168.56.110 –Pn –sU –p 161
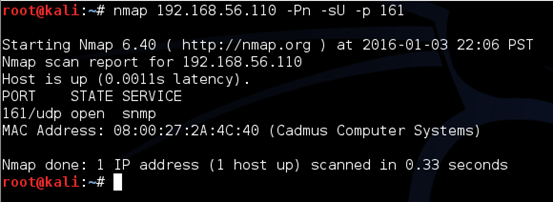
As we can see in the above figure, port 161 is open on VyOS box.
Configuring pfSense
I have previously covered how to set up a virtual pen testing lab using pfSense. You can read it here. The article covers how you can install and setup network interfaces in order to be able to communicate with Kali Linux using the same settings shown in the beginning of this article. This article shows how to configure SNMP in pfSense.
Below are the interfaces configured in my case.
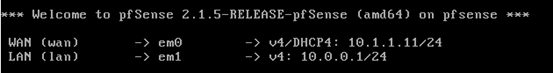
WAN interface is connected to Bridged Adapter and LAN interface is connected to Internal Adapter.
Login to the pfSense Webconfigurator from Kali Linux by typing 10.0.0.1 in the browser and navigate to "Services" – "SNMP".
You should see the following screen showing SNMP is not running.

Let's configure SNMP as shown below.
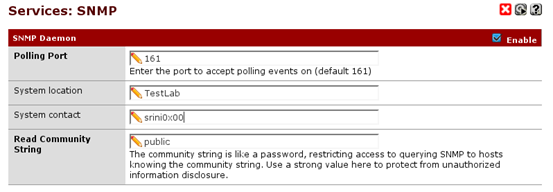
Once you finish the above configuration, scroll down until you see the following dropdown menu.
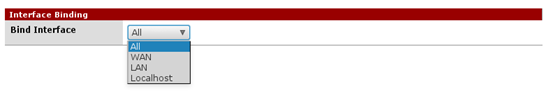
As we can see in the above figure, we can choose the interface, which we can use to request SNMP data. Since Choose "All" so that it is accessible over all the interfaces. This is another misconfiguration for the obvious reasons.
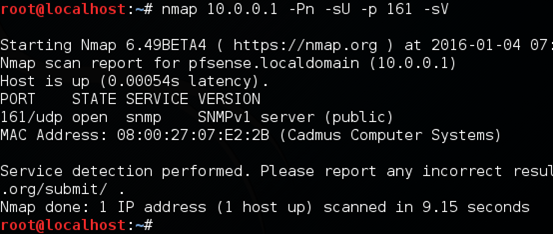
Once you are done with setting up the above-mentioned options, you can save the configuration. The SNMP service screen should now look as shown below.

nmap 10.0.0.1 –Pn –sU –p 161 -sV

What should you learn next?
We are ready with the setup. You can now fire up your Kali Linux and practice SNMP attacks on both the boxes using various tools available in Kali. We will see some of the common SNMP attacks in the next article.







