All about carding (for noobs only) [updated 2021]
Disclaimer
The Article writer's intent is to spread awareness about the carding. The writer is not responsible if any damage occurs. This is for educational purpose only.
Hello Guys, if you were a victim of carding fraud or really want to understand what is Carding and how it should be done then here I prepared the document which will clear the basic understanding.
Points I cover:
- What is carding?
- What are the factors relates to carding?
- How it's done, I mean process?
- Precautionary measures Carder should take

Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization.
Overview
Nowadays, if we see the credit card fraud trend, it is being increased day by day and new techniques being discovered to hack the credit card info and use it for malicious purpose.
As everything goes cashless, the use of a credit card will be necessary for everyone. This is reason people should be aware of how carding fraud is done and learn how to become not to become a victim.
There are so many ways to get the credit card details available on the internet through Darknet sites as well as on TOR sites (Data Leak .etc.).
My aim is to spread security awareness about carding, what is it, how the carder does it, etc.
I have referred many articles, sites and basic documentation which I feel will be useful to share it with you. I want the normal user to be aware of carding methods so they can be alert to it.
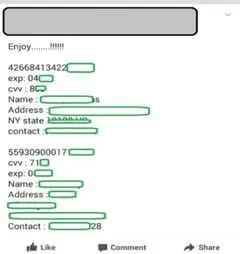
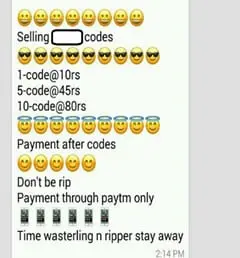
As we can see on social media sites and groups, most of the carders provide the offers which are collected from Online Sites and groups for your reference:
Be aware that you should never contact a ripper. A Ripper is a fraud who takes the money and never deliver the product.
Offer on Facebook group
Offer on WhatsApp group

Let's start with the basics.
1. Introduction to carding and key points
There are multiple definitions available per different views.
Carding itself is defined as the illegal use of the card (Credit/Debit) by unauthorized people (carder) to buy a product. For educational purposes, I will now show how a carder is able to go about their illicit activities. Remember - carding is highly illegal, and should not be attempted under any circumstances.

1.1 Key points in carding method
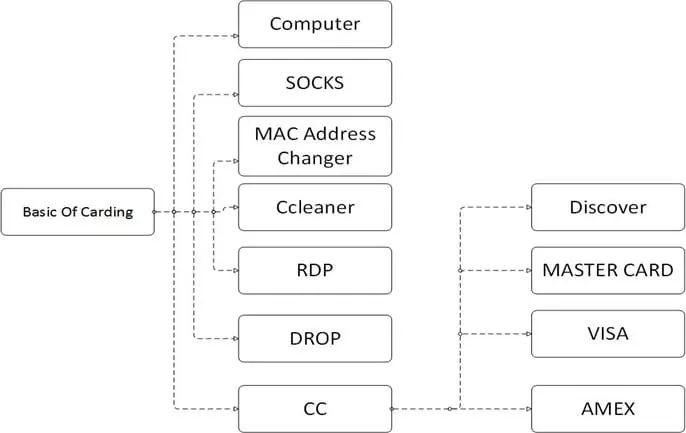
2. Let us understand each point one by one
2.1 Computer (PC)
For doing carding always use a computer. I know some methods using a mobile device, but it is less secure and involves more risk.
2.2 SOCKS
SOCKS stands for SOCKet Secure. It is internet protocol which allows client and server traffic pass through a proxy server, so real IP is getting hidden and proxy IP get reflected.
This is useful while carding because carder wants to use the credit card holder's location while doing it.
Users can buy SOCKS.
2.3 Mac Address Changer
MAC stands for Media Access Control. It is the unique address of every Network Interface Card (NIC).
A MAC address changer allows you to change the MAC address of NIC instantly. It is required to be anonymous and safe J
2.4 CCleaner
It is very useful tool help in cleaning your browsing history, cookies, temp files, etc.
Many people ignore this part and get caught, so be careful and don't forget to use it J
2.5 RDP (Remote Desktop Protocol)
RDP allows one computer to connect to another computer within the network. It is protocol developed by Microsoft.
Basically, carders use it to connect to computers of the geolocation of the person whose credit card carder want to use. It is used for safety and stay anon. Here carders use others PC for doing carding instead of their own.
2.6 DROP
DROP is an address which the carder uses for the shipping address in the carding process.
Let me explain in details with an example:
If I am carding with US credit card, then I use USA address as shipping address then my order will be shipped successfully, and I will be safe. If you have relatives/friends, then no problem, otherwise use sites who provide drop services only we have to pay extra for shipping it.
2.7 Credit card
This part is very much important so read it carefully. Any credit card it is in the following format:
| credit card Number |Exp Date| CVV2 code | Name on the Card | Address | City | State | Country | Zip code | Phone # (sometimes not included depending on where you get your credit card from)|
e.g.: (randomly taken number/details)
| 4305873969346315 | 05 | 2018 | 591 | UNITED STATES | John Mechanic | 201
Stone Wayne Lane | Easternton | MA | 01949 |
Types of credit card
Every Credit card company starts their credit card number with a unique number to identify individually like shown below
American Express (AMEX Card) – 3
Visa Card - 4
Master Card - 5
Discover (Disco) – 6
Company wise credit card details
Visa
- Classic: The Card is used worldwide in any locations designated by Visa, including ATMs, real and virtual Stores, and shops offering goods and services by mail and telephone.
- Gold – This card has a higher limit capacity. Most used card and adopted worldwide.
- Platinum – Card is having limits over $10,000.
- Signature – No preset spending limit – great bin to get
- Infinite – Most prestigious card with having virtually no limit. There is less in circulation so be alert when buying these. Use only with reputable sellers!
- Business – it can be used for small to medium sized businesses, usually has a limit.
- Corporate – it can be used with medium to large size businesses, having more limit than a Business card.
- Black – It has limited membership. It has no limit only having $500 annual fee, high-end card.
MasterCard
- Standard – it is same as classic visa card.
- Gold – it is same as visa gold card.
- Platinum – it is same as visa platinum card
- World – it has a very high limit.
- World Elite – it is virtually no limit, high-end card.
Amex Card
- Gold – it usually has around a 10k limit.
- Platinum- is usually has a higher limit (around 35k).
- Centurion – it has a High limit (75k+). It is also known as the black card, note: do not confuse with visa black card.
Phishing simulations & training
Questionnaire
Now we can start with some of the questionnaire and basic concepts before starting practical process of Carding.
Q1. What is BIN?
It is known as Bank Identification Number (BIN). It is a 6-digit number e.g.: 431408.

Some of the reference sites that give BIN info which I also refer could be found in the sources section of the article.
Simply go to the site (www.bins.pro)àenter BIN number and click on find to get the details. Now the question is how to know the balance of CC. is it possible? and answer is Yes, I will let you know step by step using normal as well as Skype method J
Q2. What is the meaning of VBV, NON VBV and MSC?
VBV (Verified by Visa) – Extra level protection is added by Visa to protect the Card from fraud.
Like DOB, password, Social Security Number and Mother's name, etc. also sending OTP (one-time password) as extra security level to card owner mobile number to validate the transaction.
NON VBV (Verified by Visa) –Handy to use. No need extra information as specified in VBV card while doing the transaction.
Note it down (IMP)- Carders mainly buy and use NON VBV cards for carding.
MSC (MasterCard Secure Code) – security level same as VBV card.
Q3. What is AVS?
It stands for Address Verification System
It is the system which is used to identify the credit card holder original address with billing address provided by the user while shopping or online transaction.
The system is used to identify the online fraud over the internet.
Q4. How to check credit card is live or dead?
There are many sites available on the internet to verify credit card is live or dead, but they charge for it approx. $0.001 (price may vary). Also, 80% websites kill the credit card so never use it.
There are tools also available on the internet to check the credit card status, but most of them are a backdoor or Trojan so prefer not to use it.
As such there is no easy method to check it. Carder uses own ways to find it out. One of the ways is...
Most carder go to Porn sites, buy a membership and confirm the credit card is live and proceed with carding.
Q5. How to check the credit card is live or dead? (Skype Method)
(Note: method is posted on March 16)
Login into Skype account and call on Magic number +18005xx5633 (masked). You will connect to voice mail (lady's voice). Start by entering the credit card number, and voice mail lady will stop automatically.
After that enter Expiry date of a card like 01 16 (mm: yy format).
If your credit card is live then voice mail lady will speak like "Thank you for calling, we really appreciate your business, since u are a 1st-time caller we would like to connect you .. blah blah" then just hang the call.
But if the credit card is used and voice mail lady speak like "Ohh I'm sorry please re-enter your credit card number now" then the card is dead. You can repeat the same process as many time you want.
Note: You need a good internet connection for Skype calls.
Q6. What is Bill=ship/Bill=CC/Ship=your Address?
Kindly pay attention here as it is also the main portion in carding process. Any mistake will cancel the order and id get blocked.
BILL=SHIP (Billing address: Shipping address)
Take a scenario of normal online shopping scenario, when you are doing carding you will use billing address and shipping address are same. Means in both u will use your address. No need to use credit card address.
Bill=Shipping address, Ship=your address
When you are doing carding, you will use credit card holder address as your billing address, and shipping address will be your address. Most sites use this method.
Now we have cleared basic concepts and starting with the actual process of Carding
Setup SOCKS proxy in Firefox:
Follow the steps à open Firefox à go to options àadvanced options à network à
A pop-up will come. It will show options
No proxy 2. Auto Detect 3. Use system proxy 4. Manual proxy configuration
Select manual proxy configuration. Enter socks host: <<proxy ip>> and port: <<proxy port>> e.g.: 141.141.141.141: 8080. Press ok and restart Firefox. Now you are connected to secure Socks5 J
Note: when you buy a socks always match with credit card holder address. If credit card holder is from California, USA then try to get SOCKS5 at least matching state, country J
Guys now time to start the Carding process. Kindly follow the steps:
- Create the email id matching with credit card holder name. If his name is John Cena (the random name was taken), then email id should be johncena92@gmail.com or near about.
- Now Run RDP and connect to the credit card holder location system to proceed. If you didn't have RDP, then follow following steps.
- Open MAC changer and change the address randomly.
- Run CCleaner and clean all the unwanted data (cookies/history/temp data etc.).
- Setup SOCKS5 proxy in Firefox. <<Already explained>>.
- Be sure to use SOCK5 is matching to the location of credit card holder and be aware not to use blacklisted IP. Check with www.check2ip.com
- Open the site for shopping. I want to recommend a website shop from your country because you don`t need to wait a lot for your package.
- Register with credit card holder information (John Cena), name, country, city, address, and email.
- Shop and choose your item and add to cart. Precaution: Select item not more than $500 at first step.
- In shipping address add your address or drop address where the product is going to deliver.
- Then go to the payment page and choose payment method like a credit card.
- Enter all details of credit card manually because most of site having copy paste detector script.
- Finally, in billing address add credit card owner address info and then proceed with the payment process.
- If everything all right then the order will get successfully placed.
- Once the order arrives at the shipping address, receive it from delivery boy.
- (Few carder arrange fake id if delivery boy ask for proof).
Carding method using mobile:
Extra pro carder uses mobile for doing carding. If you followed steps carefully, you would also do that.
Basic requirement:
- Require rooted Android mobile.
- Install few application require for carding (proxy apps, CCleaner, IMEI changer, Photo and Android ID changer).
- You can use any VPN for carding I recommend HMA or Zen mate.
- You can use SOCKS5 proxy with proxy droid apps.
- Also, proceed with IMEI and Android ID changer and do it.
- Now connect with proxy droid with SOCKS5 proxy and connect it.
- Now follow all the steps explained above J
See Infosec IQ in action
Sources:
- CC from shop
- SOCKS
- CCleaner software
- MAC address changer
- SOCKS checker
- www.bins.pro
- www.binlists.com
- www.exactbins.com
Acronyms
- BIN: Bank Identification Number
- CC: Credit Card
- CCN: Credit Card Number
- CVV/CVV2: Credit Verification Value (Card Security Code)
- SSN: Social Security Number
- MMN: Mother Maiden Name
- DOB: Date Of Birth
- COB: Change of Billing
- VBV: Verified by Visa
- MCSC: MasterCard Secure Code
- POS: Point of Sale
- VPN: Virtual Private Network
- BTC: Bitcoin
Personal Advice
- Normal users: Keep your credit card safe hands. Keep changing the credit card PIN on a monthly basis. Do not make the online transaction from unknown system/mobile.
- Who want to learn carding - I observed many of the newcomers try to be smart and got ripped multiple times. Don't do it, it's finally your loss.
- Carding is Illegal activity. Do not do it. If get caught, then, you will be in trouble.
- Be safe and have fun J
Interested in reading more? Check out these articles:







