Top 11 security awareness posters with messages that STICK [updated 2025]
The importance of security awareness in modern business practice can’t be overstated. Simply put, Security Awareness (SA) needs to be a priority in every security plan. Each employee is a front-line defender against incoming threats. That’s why so much money is put into security awareness training campaigns for employees.
Unfortunately, it only takes one employee’s split-second decision to roll out the welcome mat for hackers and scammers. While security awareness training should always be the center of your security strategy, these cybersecurity posters can provide that crucial memory jog, a flash of recognition at a moment of uncertainty that could mean the difference between breached and secure.
Here is a deep dive into 11 of the very best security awareness posters for employees to provide optimal strategies for every situation.
Phishing simulations & training
![]()
Location and Security tips: Home, but not alone

Since 2020, working remotely or work-from-home has gone from an option for the few to one that’s becoming the default for many. But just because you’re outside the physical office doesn’t mean you aren’t in hackers’ sights!
Treat your remote workspace like it’s a virtual bank vault — use strong passwords for your Wi-Fi and router and always work through a VPN to keep unwanted intruders out. And if you share devices with other family members, make sure to secure all tablets and mobile devices against accidental security missteps!
To create a 12-month security awareness and anti-phishing plan that will keep employees engaged all year long, download our Need to Know program plan.
Don't let Data Vampires drain your network — use VPN at all open Wi-Fi spots

One of Infosec’s best-loved learning tools for security awareness is the live-action teaching series, “Work Bytes.” In it, a host of colorful employees from fantastical backgrounds (A fairy princess, a zombie, a vampire, a pirate and more) make common security errors and learn from them with the help of their security team. Here, Volkov Volkovovich (Work Bytes’ head of Sales) wants you to learn from his mistakes: using public Wi-Fi without a VPN just SUCKS. Choose your networks carefully and use a VPN to protect your data’s jugular.
You can also download a full set of Work Bytes posters for your office, breakroom, or work-from-coffin environment! And if you want to learn more about what can happen when a hacker chooses to attack via an insecure public Wi-Fi, check out Keatron Evans’ presentation, How to Perform a Man-In-The-Middle Attack.
Cyber Hygiene 101: Be mindful of scam emails; be vigilant against Phishing

Your old cubemate never learned: microwaving fish in the breakroom creates a smell that lingered for days. And falling for Phishing scams will leave a stink on your company that can last years — or worse!
Scam emails can look like unusual requests from colleagues or supervisors, special offers selected “just for you,” or even fake warnings saying that you’ve already been hacked! Remember: go slow, report suspicious messages to your I.T. department, and always, ALWAYS speak to the person making the request personally to make sure this is really something they want. You’ll often find that the coupon for a year of free steaks conceals a nasty Phish(ing attack) instead.
For a full cookbook of tasty cybersecurity posters, training modules, infographics and screensavers, download our Recipe for Cybersecurity kit.
Bad things come in small packages — don't trust delivery failure notifications

“It's not my birthday,” you think, wondering who sent you a package that’s waiting for you to pick it up from the UP$ Sh1ping Netw0rk.
Wait, is that even the name of a shipping service??
Many people are fooled by fake shipping notifications that are sent via email or even texts on their phone (called SMS Phishing, or SMishing). A friendly reminder: if you don’t remember ordering something, it’s likely a scam email. Watch for obvious spelling errors in the notifications or overly long and complicated URLs, and DO NOT CLICK THEM. Avoid using the URL in the message altogether; instead, go directly to the shipping company’s website (like usps.com, ups.com or fedex.com) to check your packages' status.
And don’t forget to mark that email or text as spam, junk, and/or phishing so it can be reported!
Download our Hacked for the Holidays toolkit. It contains tools, training modules, quizzes, and more posters aimed at raising awareness of holiday scams.
Spearphishers are the worst kind of bottom-feeders — don't give them your bait!
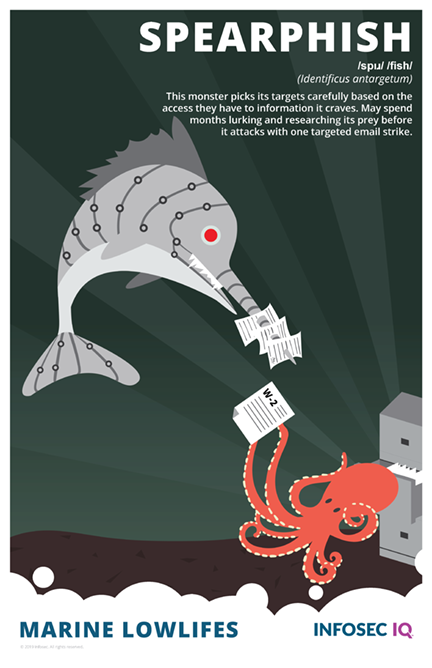
Spear phishing is a variant of phishing. Spear phishing means that an attacker is able to target individuals by gathering useful data about their target that may speed the processing of cracking a password or answering personal security questions.
Fortunately, spear phishers will starve if you don’t give them any more of your information. Avoid the urge to publicly post personal information (birthdays, phone numbers) or take social media “games” that ask you to reveal your childhood street address, your mother’s maiden name or the first car you ever drove — this information can be plugged into banks of stolen passwords until a match is made! And regularly check haveibeenpwned.com to see if any of your passwords have been found in lists of stolen passwords. If so, change those immediately!
Our Marine Lowlifes poster series offers species identification for a whole ecosystem of cybercriminal bottom-feeders.
Ransomware: The Most Dangerous Game

If you receive a notification that an ecommerce site you use has had a data breach, it’s easy enough to change your password and move on with your day. But one mistake that’s not so easy to clean up is a Ransomware attack. Using phishing techniques like those we described above, hackers can inject programs into your system that will lock all your files and render them unusable until you pay a sky-high “ransom fee” for their release.
Ransomware has bankrupted individuals and companies alike, and it’s not a game you should ever want to play. Fortunately, good cyber-hygiene is one of the best defenses against Ransomware!
Our Outsmart Them All toolkit is free to download and contains everything you need to teach your employees to outsmart every phishing email in their inbox.
See Infosec IQ in action
![]()
Security Posture training: make your passwords longer and more complex

Ed from Accounting, who is part of our great big Work Bytes family, wants you to use your brains, and not just because he’s a zombie who thinks brains are tasty! When creating passwords, the longer and more complex you can make them, the better. Never use parts of your name, easily identifiable information like birthdates, names of family members or pets, hobbies, or references that hackers could guess. (You would be amazed at the software that hackers have at their disposal to crack weak passwords!)
Create passwords that consist of whole phrases, substitute numbers, mid-word capitals and symbols for letters (i.e. “$yMb0L$ 4 l3tT3rZ”), or best of all, use a password manager to generate long, randomized passwords that are nearly impossible to guess.
And make sure your password manager’s password is equipped with two-factor and has its own strong password!
Psst! Ed from Accounting wants you to download the free Password Security Toolkit!
Be a Data Defender with Two-Factor authentication
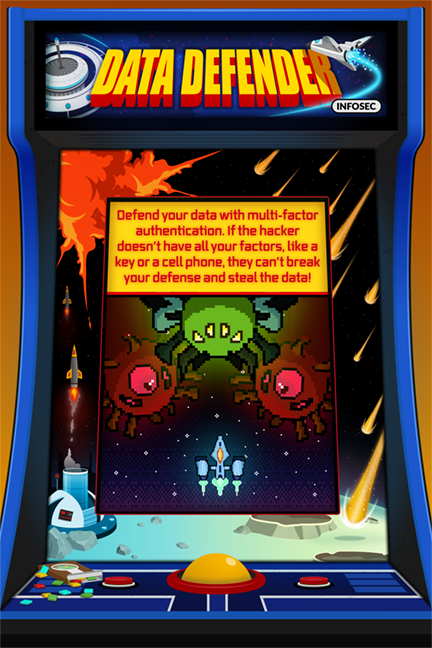
Even the most complex passwords can be lost, stolen, unintentionally revealed or guessed given enough time and ingenuity. But what if you held something that hackers cannot access? Two-Factor authentication uses traits unique to you — something you own, like a mobile device; something you know, like personalized security questions or random numbers emailed to your personal account; or something you are, like your unique facial characteristics or fingerprint.
Enabling two-factor authentication means an extra step for you during login, but for many would-be attackers, it’s a perimeter wall that even their greatest weapons can’t break through!
For the old-school gamers amongst you, our free Level Up Toolkit contains beautiful cybersecurity awareness posters inspired by classic video games. Check it out!
Insecure mobile devices: the second-greatest heartbreak ever

Your phone, tablet or other mobile device can be a source of both good news and bad news: “We’re offering you a raise!”, or “I think we should break up.” But one big way mobile devices can bear bad news is when they get compromised by hackers.
One of the best defenses against mobile device hacking is turning on auto-updates for your phone’s operating system and all apps. This ensures they’re updating as quickly as possible. You’ve got enough heartaches in your life without adding a preventable mobile takeover to the mix!
Our free Secure Your Screen security toolkit contains movie-themed posters, presentations, and assessments to make sure your staff is ready for their silver screen debut!
Properly dispose of data when you’ve finished with it

A common phrase at the dawn of the ecommerce era suggested that “data is the new oil,” meaning that customer info is the most valuable commodity in the tech economy. But as we’ve seen time and time again, data isn’t just the new oil, it’s also the new plutonium. Unless it is safely, properly and thoroughly disposed of, data lasts forever and can be stolen, corrupted and used to take advantage of millions of people, including your customers — millions of people who trusted your company to keep their data safe! (Search the term “reputational damage” to see what non-monetary losses your company can incur from a data breach.)
As this poster notes, just because a storage drive is broken doesn’t mean a hacker can’t pull data from it. Make sure that all data is properly disposed of at the end of its lifecycle.
If you don’t know how, ask your I.T. department!
Be ready for Data Privacy Week — and every other week! — with our Data Privacy Toolkit aimed at securing sensitive data.
The Golden Rule of Security Awareness: Go Slow

As our final poster demonstrates, most of the mistakes made during security compromises can be avoided by adhering to one universal rule: when dealing with incoming messages of any kind, especially unusual ones, go slowly and carefully. Hackers rely on impulsive decisions made in a moment of confusion or fear. “An abundance of caution” is never a bad idea.
Our Road to Security Campaign Kit includes everything you need to prepare employees for any pothole and sharp turns along the way, so they are ready to detect, report and outmaneuver security threats.
See Infosec IQ in action
![]()
Security Awareness is a full-time job
And now, you have 11 more tools to help design an effective cybersecurity awareness campaign! From phishing to cell phone scams to home network security, the future can look safer when you help your staff read and apply these cybersecurity core concepts to their work and home networks and make them a daily part of their cyber-secure workday.
We’ve provided numerous resources, toolkits and guides in the links above. In addition, the following webinar will help you create a Security Awareness program, while many other tips and strategies can be found at Infosec’s Security Awareness resources page, which contains still more ebooks, posters and guides.








