Mobile Systems Vulnerabilities
With a significant increase in Android malware and targeted Wi-Fi attacks over the past few years, consumer and enterprise mobile devices are more prone than ever to a plethora of security threats. The ever evolving mobile threat landscape is a result of several factors such as increased speed, storage space, power and convenience of use, which has led to mobile devices being used frequently for paying bills, managing finances or shopping online. Subsequently, they are becoming easy yet valuable targets for cyber criminals.
2016 has seen a significant number of major news related to mobile security. Android OS vulnerabilities have led Google to change its approach towards security updates. We also came to know how malicious adware spies on our television habits. Not only that, there has also been an increased presence of ransomware, remote access tools (RATs) and advanced malware bringing the same threats we earlier had to deal with on our personal computers. All these threats make way into our mobile devices because of increased vulnerability and exposure to mobile applications.
Learn Vulnerability Management
What is mobile security?
Mobile security aims to protect personal and business information that is stored on, or transmitted to and from, mobile devices. It is a broad term that enfolds all aspects of security, from malware threats to mitigating risk and securing mobile data in case of unauthorized access, theft or accidental loss of a mobile device.
Why is mobile security important?
Mobile security is the key to win the war against cyber criminals. It is as important as the PIN code for your ATM card or the password of your email account. With virtual pickpocketing on the rise, computer security companies and researchers have been successfully staying ahead of cyber criminals and have devised strong standards and protection mechanisms for consumers. The same security standards devised for PCs have now been applied to mobile devices. Some protections come as built-in services with the devices themselves, such as iPhone’s default Auto Lock, whereas some protections are built into a network, such as strong encryption for data transmission. But even with all these defenses available to the user, perhaps the best and the most powerful defense is an educated user. Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against these threats.
Threats to Mobile Security
Malware spread through malicious apps continues to be the biggest threat to mobile systems. Moreover, an unencrypted Wi-Fi network is an open invitation for hackers to infiltrate into a communication channel. Phishing scams are also as popular a threat to mobile devices as they are to personal computer systems.
Let us look at some of the biggest threats to mobile systems particularly in the year 2016 and onwards.
- Mobile Web Browser Based Hacking
One of the most effective ways to hack into the entire system of a mobile device is via a mobile web browser. This is because once a hacker is able to exploit a vulnerability in the browser, they can evade system-level security measures. Webkit-based and OS level exploits affect mobile versions of Firefox, Safari, Chrome and all related iPhone and Android kernels and can allow the hacker to gain access to the system.
- Remote Device Hijacking
Mobile handsets come with preinstalled applications that are not exactly tested or authenticated for security by Google. These applications expose mobile devices to remote hijacking. Equipment manufacturers have the liberty to customize Android smartphones at will, which is why incidents related to this threat are anticipated to rise.
- Man in the Middle (MitM) Attacks
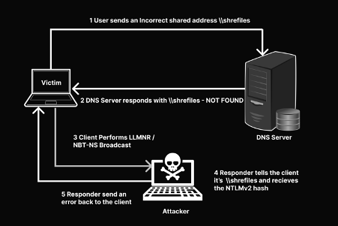
Closely related to remote device hijacking, MitM attacks intercept communication between the sender and receiver, and communicate with each on behalf of the other. The middle man acquires useful information from both parties without their knowledge. These threats usually surface during communication on unsecured Wi-Fi connections that send and receive unencrypted data across the network.
A “man” in the middle can also eavesdrop on conversations without participating himself and quietly extract sensitive data.
- Evolution of DDoS Attacks
Dedicated denial of service (DDoS) attacks in the past would cover a short time span and were easily dealt with by experienced organizations. However, the growth of mobile devices connected to the Internet has contributed to the evolution of DDoS attacks. More devices are now being hacked and used in DDoS bot attacks, thus decreasing the capability of businesses to identify and avoid denial of service attempts.
- Implications of Internet of Things (IoT)
Just as we mentioned above, the Internet of Things continues to be developed, which will allow anything and everything to connect to the Internet, thus not only bringing convenience but also exposing us to serious complications altogether. From hacking an automated car to a medical device having Internet connectivity, cybercriminals can now choose from a multitude of options for penetrating into mobile devices. Mobile applications connecting to these IoT devices via Wi-Fi or Bluetooth are vulnerable and give way to hackers to carry out device driven DDoS attacks, in combination with mobile Trojans, to gain remote access to a secure network.
Creating a Balance between Mobility and Security
From the perspective of an enterprise, it is practically impossible to effectively implement a mobile device strategy. In spite of creating a policy for using mobile devices and employee training, there would still be security loopholes resulting from human error. Moreover, employees may get disgruntled when forced not to use their mobile devices in a certain way, and many would still be careless to access corporate information outside office premises. Hence, implementing a company mobile device strategy or a BYOD policy is not much relevant.
What can be done effectively, however, is to consider mobile security as a fundamental part of your cybersecurity policy. Implement the basic security controls to filter out easy threats. Secure your wireless LAN and Ethernet networks. Implement access control by making use of a VPN and isolate data with VLANs to make data available according to roles and requirement. Use of next generation firewalls can help filter out unwanted connections and identify unusual activity across the network. Conducting regular penetration tests will ensure network security.
Now that basic controls are in place, it is necessary to invest in a vigorous Mobile Device Management solution. It can allow for the management of every single mobile device on the network. It can help authenticate a mobile device and install suitable applications. All devices connected to the network can be controlled remotely, so in case of loss or theft, they can have their network access disabled. Also, a central management system can let you detect and block unauthorized devices trying to enter a corporate network. A comprehensive MDM solution will include data loss prevention, anti-malware, encryption, packer variant protection, vulnerability shielding, web threat protection, etc.
Lastly, the most important of all is to address the threat of human element in mobile security. As already mentioned, a mobile device policy alone may not be effective, but it is integral to creating awareness and consciousness of how security is a responsibility of every member of a workforce. It is important to train and remind them with regular sessions to discourage the use of mobile devices for storing corporate information, to use strong passwords, and to connect to secured networks and access enterprise network via VPN only.
Assessing Most Common Mobile Vulnerabilities
Mobile vulnerabilities can result from poor technical controls and careless security practices of users. We look at some of the mobile vulnerabilities that are most common to all mobile devices:
- Though mobile devices come with password and PIN protection, pattern screen locks and biometric finger authentication features, seldom are these features actually enabled by users. Even if mobile consumers use PIN or password protection, they use combinations that can be easily guessed by an unauthorized user.
- When conducting online transactions, two-factor authentication is only rarely used. Studies suggest that users only use passwords rather than 2FA when conducting sensitive online transactions. Without two-factor authentication, there is an increased risk of unauthorized users gaining access to critical data and misusing mobile devices.
- A wireless transmission may not always be encrypted. As a result, an email sent via mobile device is usually unencrypted when in transit. Many corporate apps built for internal use or third party apps also send and receive unencrypted data over the network. Unencrypted data being transmitted by an application over unencrypted Wi-Fi can be intercepted easily.
- Mobile devices may also be infected with malware as a result of malware-containing apps. These apps may be disguised as a security patch, game, utility, or any other useful app.
- Many times security software does not come built-in with a mobile device and as such the device has no protection against malicious apps, viruses and spyware.
- Outdated operating systems lack security patches. It may take a considerable amount of time for updates to reach consumer mobile devices and the patching process may be complex, depending upon the vulnerability.
- Software programs on mobile devices may not be updated. Similarly, third-party apps may not always have their security patches developed.
- A mobile device may have undergone an unauthorized modification (“jailbreaking” on iPhone and “rooting” on Android). A modified device allows users to access the device’s operating system and install unauthorized applications on it. This changes the way the device works and increases its security risks.
Some useful tools for mobile device vulnerability assessment are:
- OWASP Mobile Security Project – a centralized resource that gives security teams and developers all required resources to develop and maintain secure mobile apps.
- Smartphone Pentest Framework (SPF) – an open source platform for mobile security assessment.
- zANTI by Zimperium – an app that lets security managers estimate the risk level of a network with only one button push.
Mitigating the Vulnerabilities
Completely overcoming vulnerabilities is just not possible. They can, however, be mitigated with some basic security measures.
Learn Vulnerability Management
- User authentication: Configure your devices to require PIN, password or unlock pattern to gain access.
- Antimalware Software: Antimalware software provides basic protection against viruses, malicious apps, spyware, and all other forms of malware. These programs also protect against spam.
- Installed applications verification: To ensure that installed applications have not been altered or repackaged, implement procedures to assess their digital signatures.
- Two-factor Authentication: This is necessary, especially for sensitive transactions, to provide one step higher security than conventional password-based security.
- Firewall: A firewall will intercept all incoming and outgoing traffic to check unauthorized connections across the network.
- Security Updates: Software security updates can be directly downloaded onto mobile devices.
- Remote Handling of Lost or Stolen Device: In case a mobile device is lost or stolen, the best practice is to remotely disable it to prevent the person in possession of the device from accessing any sensitive information. A locked device can be unlocked at a later time if the owner recovers the device.
- Data Encryption: Data stored on a device or a memory card must be encrypted. Some devices come with built-in encryption while others can make use of commercial encryption tools.
- Application Whitelisting: This prevents unauthorized applications from running upon request and only allows the apps on the whitelist to run and demand for resources.
- Mobile security policy: A security policy for mobile device will explain rules, objectives and basic security practices that need to be followed across the organization or as an individual. The policy must cover purpose, device security, roles and responsibilities, security assessments, etc.
- Mobile device security awareness trainings: This is perhaps one of the most important steps to mitigate mobile device vulnerabilities. If employees are not knowledgeable or do not conform to security practices, no other technical measure can succeed in mitigating vulnerabilities. Employees should be regularly trained for security policies to ensure that they configure and operate mobile devices in a secure manner.
- Risk Assessments: Risk assessments are crucial for identifying threats and vulnerabilities, recognizing potential attacks and estimating potential damages resulting from successful attacks.
To conclude, organizations are now realizing how important a matter mobile security is, and are beginning to understand that education regarding mobile security has to be ongoing, interactive and with measurable outcomes. Rather than looking for mitigation plans once things get out of control, it is always a good approach to proactively avoid and prepare for adverse circumstances. When it comes to mobile security, act right there and then. Do Not Procrastinate.