SIM card forensics: An introduction

The SIM (subscriber identity module) is a fundamental component of cellular phones. It also known as an integrated circuit card (ICC), which is a microcontroller-based access module. It is a physical entity and can be either a subscriber identity module (SIM) or a universal integrated circuit card (UICC).
A SIM can be removed from a cellular handset and inserted into another; it allows users to port identity, personal information, and service between devices. All cell phones are expected to incorporate some type of identity module eventually, in part because of this useful property. Basically, the ICC deployed for 2G networks was called a SIM and the UICC smart card running the universal subscriber identity module(USIM) application. The UICC card accepts only 3G universal mobile telecommunications service (UMTS) commands. USIMs are enhanced versions of present-day SIMs, containing backward-compatible information. A USIM has a unique feature in that it allows one phone to have multiple numbers. If the SIM and USIM application are running on the same UICC, then they cannot be working simultaneously.
The first SIM card was about the size of a credit card. As technology developed, the cell phone began to shrank in size and so did the SIM card. The mini-SIM card, which is about one-third the size of a credit card. But today we are using smartphones that use micro-SIM, which is smaller than mini-SIM. These SIM cards vary in size but all have the functionality for both the identification and authentication of the subscriber's phone to its network and all contain storage for phone numbers, SMS, and other information, and allow for the creation of applications on the card itself.

SIM structure and file systems
A SIM card contains a processor and operating system with between 16 and 256 KB of persistent, electronically erasable, programmable read-only memory (EEPROM). It also contains RAM (random access memory) and ROM (read-only memory). RAM controls the program execution flow and the ROM controls the operating system work flow, user authentication, data encryption algorithm, and other applications. The hierarchically organized file system of a SIM resides in persistent memory and stores data as names and phone number entries, text messages, and network service settings. Depending on the phone used, some information on the SIM may coexist in the memory of the phone. Alternatively, information may reside entirely in the memory of the phone instead of available memory on the SIM.
The hierarchical file system resides in EEPROM. The file system consists of three types of files: master file(MF), dedicated files, and elementary files. The master file is the root of the file system. Dedicated files are the subordinate directories of master files. Elementary files contain various types of data, structured as either a sequence of data bytes, a sequence of fixed-size records, or a fixed set of fixed-size records used cyclically.
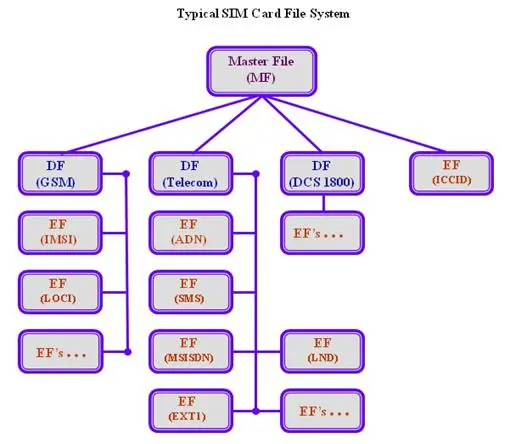
As can be seen in the above figure, dedicated files are subordinate directories under the MF, their contents and functions being defined by the GSM11.11 standards. Three are usually present: DF (DCS1800), DF (GSM), and DF (Telecom). Also present under the MF are EFs (ICCID). Subordinate to each of the DFs are supporting EFs, which contain the actual data. The EFs under DF (DCS1800) and DF (GSM) contain network-related information and the EFs under DF (Telecom) contain the service-related information.
All the files have headers, but only EFs contain data. The first byte of every header identifies the file type and the header contains the information related to the structure of the files. The body of an EF contains information related to the application. Files can be either administrative- or application-specific and access to stored data is controlled by the operating system.
Security in SIM
SIM cards have built-in security features. The three file types, MF, DF, and EF, contain the security attributes. These security features filter every execution and allow only those with proper authorization to access the requested functionality. There are different level of access conditions in DF and EF files. They are:
- Always—This condition allows to access files without any restrictions.
- Card holder verification 1 (CHV1)—This condition allows access to files after successful verification of the user's PIN or if PIN verification is disabled.
- Card holder verification 2 (CHV2)—This condition allows access to files after successful verification of the user's PIN2 or if the PIN2 verification is disabled.
- Administrative (ADM)—The card issuer who provides SIM to the subscriber can access only after prescribed requirements for administrative access are fulfilled.
- Never (NEV)—Access of the file over the SIM/ME interface is forbidden.
The SIM operating system controls access to an element of the file system based on its access condition and the type of action being attempted. The operating system allows only limited number of attempts, usually three, to enter the correct CHV before further attempts are blocked. For unblocking, it requires a PUK code, called the PIN unblocking key, which resets the CHV and attempt counter. If the subscriber is known, then the unblock CHV1/CHV2 can be easily provided by the service provider.
Sensitive data in SIM

The SIM card contains sensitive information about the subscriber. Data such as contact lists and messages can be stored in SIM. SIM cards themselves contain a repository of data and information, some of which is listed below:
These data have forensics value and can be scattered from EF files. Now we will discuss some of these data.
A. Service related information
1. ICCID: The integrated circuit card identification is a unique numeric identifier for the SIM that can be up to 20 digits long. It consists of an industry identifier prefix (89 for telecommunications), followed by a country code, an issuer identifier number, and an individual account identification number.
Twenty-digit ICCIDs have an additional "checksum" digit. One example of the interpretation of a hypothetical nineteen digit ICCID (89 310 410 10 654378930 1) is shown below.
- Issuer identification number (IIN) is variable in length up to a maximum of seven digits:
- The first two digits are fixed and make up the Industry Identifier. "89" refers to the telecommunications industry.
- The next two or three digits refer to the mobile country code (MCC) as defined by ITU-T recommendation E.164. "310" refers to the United States.
- The next one to four digits refer to the mobile network code (MNC). This is a fixed number for a country or world zone. "410" refers to the operator, AT&T Mobility.
- The next two digits, "10," pertain to the home location register.
- Individual account information is variable in length: The next nine digits, "654378930," represent the individual account identification number. Every number under one IIN has the same number of digits.
- Check digit—the last digit, "1," is computed from the other 18 digits using the Luhn algorithm.
2.IMSI: The international mobile subscriber identity
is a unique 15-digit number provided to the subscriber. It has a similar structure to ICCID and consists of the MCC, MNC, and MSIN. An example of interpreting a hypothetical 15-digit IMSI (302 720 123456789) is shown below:
- MCC—The first three digits identify the country. "302" refers to Canada.
- MNC—The next two (European Standard) or three digits (North American Standard) identify the operator. "720" refers to Rogers Communications.
- MSIN—The next nine digits, "123456789," identify the mobile unit within a carrier's GSM network
3.MSISDN—The Mobile Station International Subscriber Directory Number is intended to convey the telephone number assigned to the subscriber for receiving calls on the phone. An example of the MSISDN format is shown below:
- CC can be up to 3 digits.
- NDC usually 2 or 3 digits.
- SN can be up to a maximum 10 digits.
B. Phonebook and call information
1. Abbreviated dialing numbers (ADN)—Any number and name dialed by the subscriber is saved by the ADN EF. The type of number and numbering plan identification is also maintained under this. This function works on the subscriber's commonly dialed numbers. The ADN cannot be changed by the service provider and they can be attributed to the user of the phone. Most SIMs provide 100 slots for ADN entries.
2. Fixed dialing numbers (FDN)—The FDN EF works similar to the ADN because it involves contact numbers and names. With this function, The user doesn't have to dial numbers; by pressing any number pad of the phone, he can access to the contact number.
3. Last number dialed (LND)—The LND EF contains the number most recently dialed by the subscriber . The number and name associated with that number is stored in this entry. Depending upon the phone, it is also conceivable that the information may be stored in the handset and not on the SIM. Any numbers that may be present can provide valuable information to an investigator.
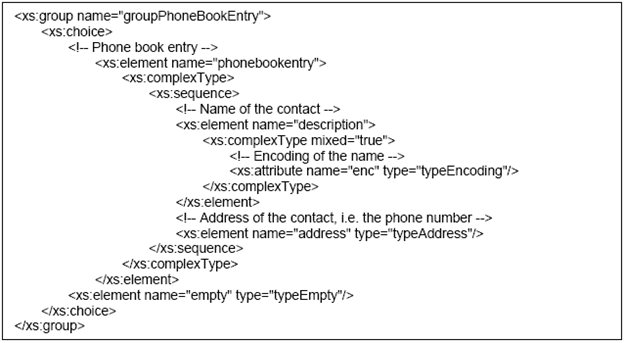
XML Phonebook Entry
C. Messaging information
Messaging is a communication medium by which text is entered on one cell phone and delivered via the mobile phone network. The short message service contains texts and associated parameters for the message. SMS entries contain other information besides the text itself, such as the time an incoming message was sent, as recorded by the mobile phone network, the sender's phone number, the SMS center address, and the status of the entry. An SMS is limited to either 160 characters (Latin alphabet) or 70 characters (for other alphabets). Longer messages are broken down by the sending phone and reassembled by the receiving phone.
Tools for SIM forensics
To perform forensic investigation on a SIM card ,it has to be removed from the cell phone and connect to a SIM card reader. The original data of SIM card is preserved by the elimination of write requests to the SIM during its analysis. Then we calculate the HASH value of the data; hashing is used for checking the integrity of the data, that is, whether it has changed or not. There are lots of forensic tools are available but all tools are not able to extract data from every type of cell phone and SIM card. Now we will discuss about some famous tools:
Encase Smartphone Examiner: This tool is specifically designed for gathering data from smartphones and tablets such as iPhone, iPad, etc. It can capture evidence from devices that use the Apple iOS, HP Palm OS, Windows Mobile OS, Google Android OS, or RIM Blackberry OS. It can acquire data from Blackberry and iTunes backup files as well as a multitude of SD cards. The evidence can be seamlessly integrated into EnCase Forensic.
MOBILedit! Forensic: This tool can analyze phones via Bluetooth, IrDA, or cable connection; it analyzes SIMs through SIM readers and can read deleted messages from the SIM card.

pySIM: A SIM card management tool capable of creating, editing, deleting, and performing backup and restore operations on the SIM phonebook and SMS records.
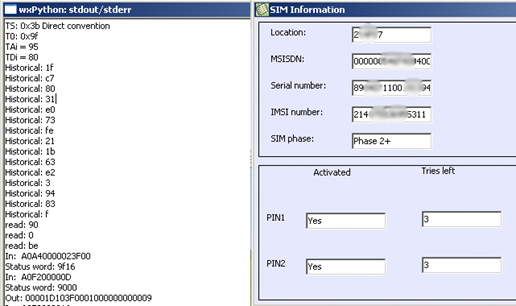
AccessData Mobile Phone Examiner (MPE) Plus: This tool supports for than 7000 phones including iOS , Android , Blackberry, Windows Mobile, and Chinese devices and can be purchased as hardware with a SIM card reader and data cables. File systems are immediately viewable and can be parsed in MPE+ to locate lock code, EXIF, and any data contained in the mobile phone's file system.
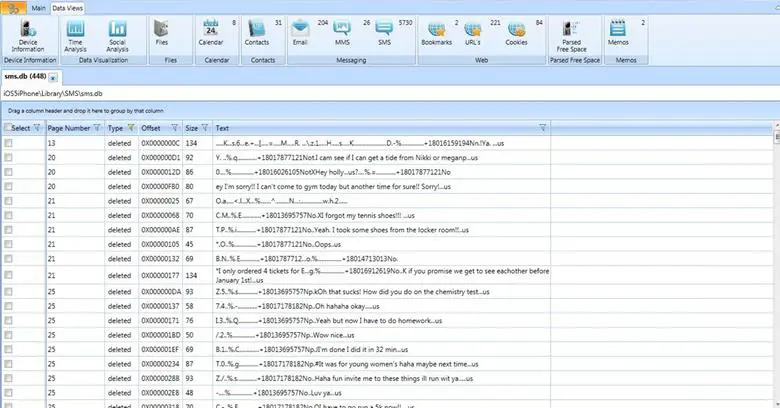
SIMpull: SIMpull is a powerful tool, a SIM card acquisition application that allows you to acquire the entire contents of a SIM card. This capability includes the retrieval of deleted SMS messages, a feature not available on many other commercial SIM card acquisition programs. SIMpull first determines if the card is either a GSM SIM or 3G USIM, then performs a logical acquisition of all files defined in either ETSI TS 151.011 (GSM) or ETSI TS 131.102 (USIM) standards.
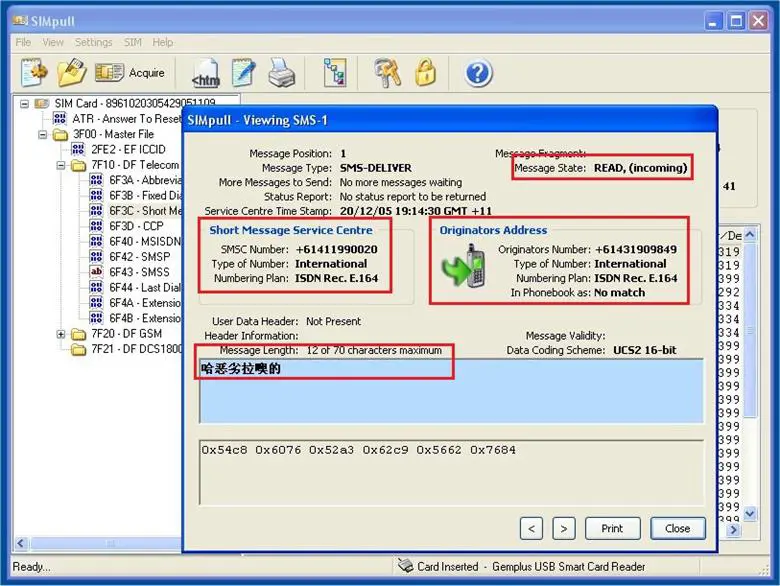
As can be seen in above figure, by using the SIMpull application we can see the information of SMS such as a SMS text and its length, the SMS sender's number information, service center information, etc.










