Protocol analysis using Wireshark
Protocol analysis is examination of one or more fields within a protocol’s data structure during a network investigation. Understanding the bits and pieces of a network protocol can greatly help during an investigation.
This article discusses analyzing some high-level network protocols that are commonly used by applications. We will specifically use Wireshark to do protocol analysis in this article. Wireshark has the ability to decode the stream of bits flowing across a network and show us those bits in the structured format of the protocol.
Learn Network Forensics
What is a network protocol
As protocol is a set of standards and rules that has to be followed in order to accomplish a certain task, in the same way network protocol is a set of standards and rules that defines how a network communication should be done.
The standards that are used for the internet are called requests for comment (RFC). RFCs are numbered from 1 onwards, and there are more than 4,500 RFCs today. Many of them have become out of date, so only a handful of the first thousand RFCs are still used today.
The OSI model
The International Standardization Office (ISO) has standardized a system of network protocols called ISO OSI.
- Physical layer
- Data link layer
- Network layer
- Transport layer
- Sessions layer
- Presentation layer
- Application layer
The OSI model breaks the various aspects of a computer network into seven distinct layers, each depending on one another. The following section briefly discusses each layer in the OSI model.
Physical layer
The physical layer is responsible for activating the physical circuit between the data terminal equipment and data circuit-terminating equipment, communicating through it and then deactivating it. To put it differently, the physical layer describes the electric or optical signals used for communicating between two computers.
Physical circuits are created on the physical layer.
Data link layer
The data link layer is responsible for the node-to-node delivery of the message. The main function of this layer is to make sure data transfer is error-free from one node to another, over the physical layer. When a packet arrives in a network, it is the responsibility of the data link layer to transmit it to the host using its MAC address.
The data link layer is divided into two sub layers:
- Logical link control (LLC)
- Media access control (MAC)
Network layer
The network layer ensures the data transfer between two hosts located in different networks. The basic unit of transfer is a datagram that is wrapped (encapsulated) in a frame. The datagram is also composed of a header and data field.
Transport layer
The transport layer provides services to the application layer and takes services from the network layer.
The data in the transport layer is referred to as segments. It is responsible for the end-to-end delivery of the complete message. The transport layer also provides the acknowledgement of the successful data transmission and re-transmits the data if an error is found.
Session layer
The session layer is responsible for the establishment of connection, maintenance of sessions and authentication. It also helps ensure security.
Presentation layer
Presentation layer is also called the translation layer. The data from the application layer is extracted here and manipulated as per the required format to transmit over the network.
Application layer
The application layer defines the format in which the data should be received from or handed over to the applications. For example, the OSI virtual terminal protocol describes how data should be formatted as well as the dialogue used between the two ends of the connection.
Learn Network Forensics
Common protocols in Wireshark
Let's go through some examples and see how these layers look in the real world. As mentioned earlier, we are going to use Wireshark to see what these packets look like.
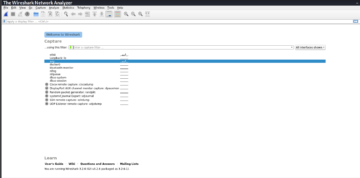
Open Wireshark on the analysis laptop/Virtual Machine(Kali Linux Virtual Machine in this case). To listen on every available interface, select any as shown in the figure below.
Once Wireshark is launched, we should see a lot of packets being captured since we chose all interfaces. Enter http as the filter which will tell Wireshark to only show http packets, although it will still capture the other protocol packets.
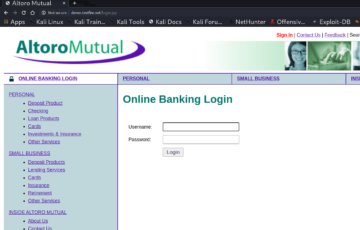
Visit demo.testfire.net/login.jsp, which is a demo website that uses http instead of https, so we will be able to capture the clear text credentials if we login using the login page.
Enter some random credentials into the login form and click the login button.
Now switch back to the Wireshark window and you will see that it's now populated with some http packets. It should be noted that, currently Wireshark shows only http packets as we have applied the http filter earlier.
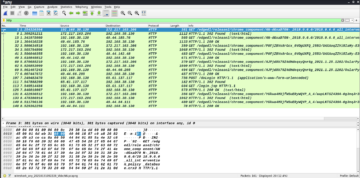
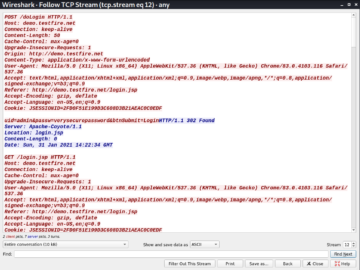
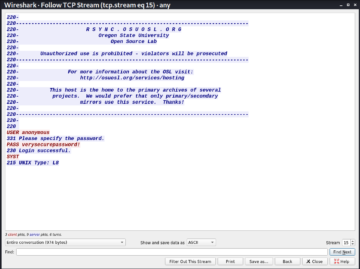
Let us look for the packets with POST method as POST is a method commonly used for login. Following is a good candidate to check if any credentials are being sent over the network.
Right click on this packet and navigate to follow | TCP Stream. You will be able to see the full http data, which also contains the clear text credentials. This looks as follows.
Data sent using any protocol without encryption can be captured and analyzed the same way to obtain some interesting details. Depending on the protocol being used, the data may be located in a different format. Let us see another example with file transfer protocol.
Once again launch Wireshark and listen on all interfaces and apply the filter as ftp this time as shown below.
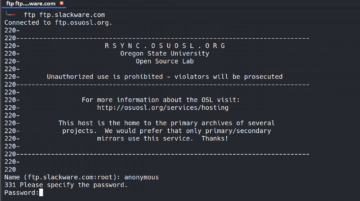
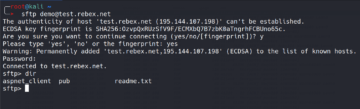
To be able to capture some FTP traffic using Wireshark, open your terminal and connect to the ftp.slackware.com as shown below.
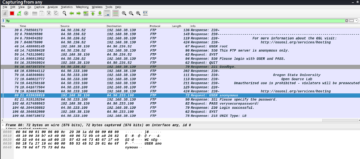
Specify the user: anonymous and any password of your choice and then hit enter and go back to the Wireshark window. The captured FTP traffic should look as follows.
As we can observe in the preceding picture, Wireshark has captured a lot of FTP traffic. Now, let’s analyze the packet we are interested in. This the request packet which contains the username we had specified, right click on that packet and navigate to follow | TCP Stream to get the full details of it.
As we can see, we have captured and obtained FTP credentials using Wireshark.
When traffic contains clear text protocols such as http and FTP, analysis is easier as the data we are looking for is typically available in clear text as we have seen in our examples. When traffic contains encrypted communications, traffic analysis becomes much harder.
The following example shows some encrypted traffic being captured using Wireshark. For the demo purposes, we’ll see how the sftp connection looks, which uses ssh protocol for handling the secure connection. We will be using a free public sftp server test.rebex.net. The credentials for it are demo:password. Before logging in, open Wireshark and listen on all interfaces and then open a new terminal and connect to the sftp server.
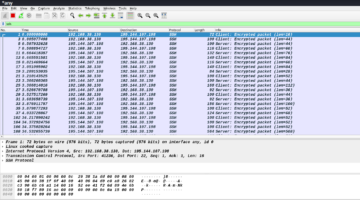
Switch back to the Wireshark window and observe the traffic being generated. As we can see in the following figure, we have a lot of ssh traffic going on.
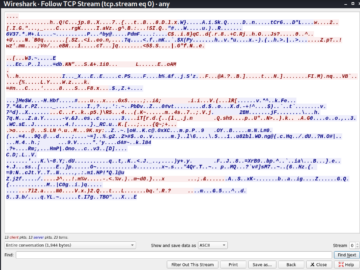
If we try to select any packet and navigate to follow | TCP stream as usual, we’ll notice that we are not able to read the clear text traffic since it’s encrypted. This looks as follows.
The preceding figure shows the tcp stream of an SSH packet and it appears as gibberish the traffic is encrypted.
Learn Network Forensics
Conclusion
During network forensic investigations, we often come across various protocols being used by malicious actors. For instance, a malicious actor may choose to use HTTP(S) or DNS for data exfiltration, and it is worth understanding how these protocols may look like when analyzed using a tool like Wireshark.
This will give some insights into what attacker controlled domain the compromised machine is communicating with and what kind of data is being exfiltrated if the traffic is being sent in clear text. However, the use of clear text traffic is highly unlikely in modern-day attacks. In such cases, we may have to rely on techniques like reverse engineering if the attack happened through a malicious binary.
Sources
Network Forensics, Ric Messier
Internet Forensics: Using Digital Evidence to Solve Computer Crime, Robert Jones
Network Forensics: Tracking Hackers through Cyberspace, Sherri Davidoff