Volodya/BuggiCorp Windows exploit developer: What you need to know
Check Point researchers unveiled the identity of two authors responsible for zero-day attacks on Windows using a novel technique that allows them to recognize and identify malicious developers. According to the Check Point research, “Volodya” or “BuggiCorp,” was the most active developer for Windows last year and launched more than 10 Windows Kernel Local Privilege Escalation (LPE) exploits, many of them zero-days.
By recognizing the fingerprint of specific developers, researchers were able to perform three security tasks:
- Detect the presence of attacks developed by developers in specific malware families
- Detect additional attacks developed by the same author, since they share a unique fingerprint
- Block all malware families that use an attack already studied and whose “fingerprint” has already been identified
Learn Vulnerability Management
Background
The work began after a malware incident from a specific client from the Check Point team.
Researchers said “the sample contained unusual debug strings that pointed at an attempt to exploit a vulnerability on the victim machine. Even more importantly, the sample had a leftover PDB path which proclaimed loud and clear the goal of this binary: ...\cve-2019-0859\x64\Release\CmdTest.pdb.”
No proof-of-concept or exploits were available online to take advantage of CVE-2019-0859. This was the starting point to go through this investigation as mentioned by researchers.
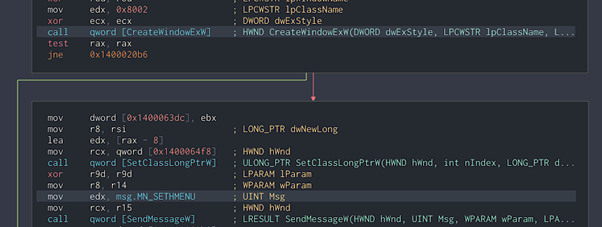
After beginning with reverse engineering, researchers found that the CVE exploited a use-after-free (UAF) vulnerability in CreateWindowEx to gain elevated privileges to the parent process.
Figure 1: A call to CreateWindowEx, as can be seen in Cutter.
From this point, a simple and straightforward methodology was developed to collect indicators from malicious code to uncover potentially bad code signatures, zero-day vulnerabilities and the authors behind the crime.
Specialized criminals create exploits that allow them to benefit, and then sell them to other cybercriminals, who build new pieces of malware with unexplored vulnerabilities that will probably bypass security detections.
A new approach to tracking malicious code
Using a new method, it was possible for Check Point researchers to unravel the work of one of the most active and prevalent malicious developers for the Windows Kernel, called “Volodya,” and also known as “BuggiCorp.”
Volodya sells unexploited code for zero-day attacks and critical vulnerabilities. Check Point researchers found that Volodya has been active since at least 2015, identifying 11 different exploit codes designed for the Windows Kernel. As a result of these codes, distinguished names are known for cybercrime, such as Dreamboat and Magniber, as well as malware families such as Turla and APT28, commonly associated with Russia.
Within this context, it’s important to notice that the exploits and malware were written by two different sets of authors. To track this, the Check Point team used the binary's properties as a unique hunting signature to find at least 11 other exploits developed by the same developer named "Volodya" (or "Volodimir").
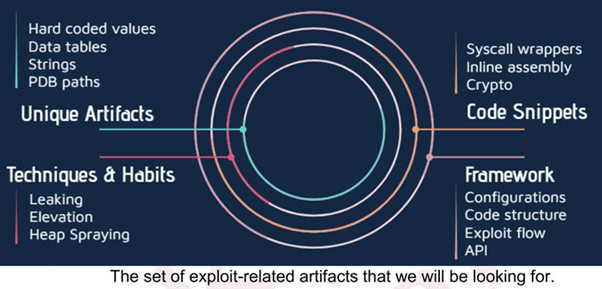
Figure 2: High-level diagram of Check Point methodology.
"Finding a vulnerability, and reliably exploiting it, will most probably be done by specific teams or individuals who specialize in a particular role. The malware developers for their part don't really care how it works behind the scenes, they just want to integrate this [exploits] module and be done with it," the researchers said.
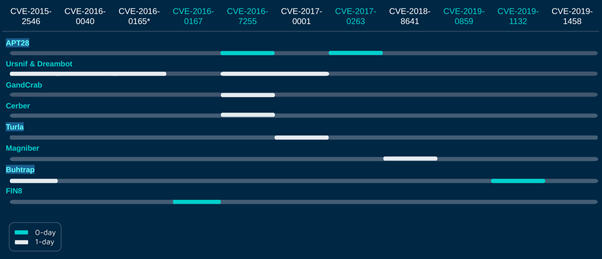
Over the years, Volodya — one of the developers — has been found to cater to an extensive clientele, including the Ursnif banking trojan, and APT groups such as Turla, APT28 and Buhtrap. The graph below from Check Point research demonstrates that scenario.
Figure 3: Volodya's customers and the CVEs that were used by them.
"The APT customers, Turla, APT28 and Buhtrap, are all commonly attributed to Russia, and it is interesting to find that even these advanced groups purchase exploits instead of developing them in-house," Check Point observed in its analysis. "This is another point which further strengthens our hypothesis that the written exploits can be treated as a separate and distinct part of the malware."
The second developer and malicious seller identified is “PlayBit,” or “luxor2008.” Check Point investigators identified five different holdings authored by PlayBit, which were later sold to prominent cybercrime groups such as REvil and Maze. Both are known to develop ransomware.
Learn Vulnerability Management
Final thoughts
We are living in an era where cyberattackers are often expanding their malicious activities in scope and magnitude. With this new approach of detecting incidents and bad code signature, it’s possible to identify crime early and track down bad actors to provide valuable insight into the black exploit market.
Finding a new vulnerability, demonstrating it, reporting it to the appropriate vendor and making sure it’s patched is a piece of art these days. But the challenge is not easy because the novel malware or CVEs are employing new TTPs. Discovering the vulnerability or the new malware is just the beginning of the challenge.
In this sense, the usage of a new methodology proposed by Check Point aims to get a better way of tracking bad signatures, similarities in source-code and potentially the identification of the authors behind the exploits.
Sources
Thread Hunting analysis, Check Point