Roadmap for performing an Active Directory assessment
Active directory (AD) networks are in almost every corporate network. These structures have three principal components: domains, trees and forests. Users and devices are part of the objects in use and part of the same AD database, which can be grouped into a single domain.
AD networks are considered insecure by default, many of them with legacy configurations, ancient systems, unconfigured and so on. As a result, there are hundreds of ways external agents can take advantage of their weaknesses. This article presents some ways security professionals can follow when performing an Active Directory assessment.
Learn Vulnerability Assessments
![]()
A look at outdated protocols
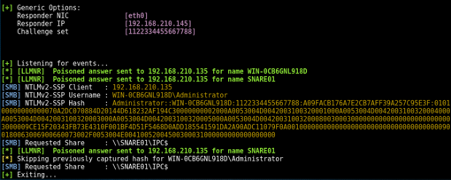
Link-local multicast name resolution (LLMNR) is a protocol under the radar when performing an AD internal assessment. This protocol traffic can be spoofed for poisoning the service and communicating with the targeted controlled system by re-using the authentication requests in relay attacks or cracking the NTLMv2 hash in use.
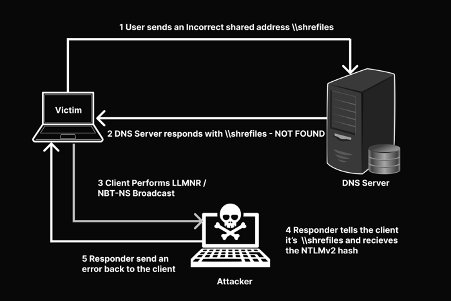
As observed, when a non-existent file share is requested to the DNS server, it responds with the NOT FOUND status to the request. Next, a broadcast solicitation is sent to the local network segment, and anyone can reply to the client with an OK status. The NTLMv2 authentication is received, and it can be relayed to target machines or collect the hash and crack it offline.
On the other hand, LDAP signing, a feature from the simple authentication and security layer (SASL) of the lightweight directory access protocol (LDAP), should also be used to protect the network against man-in-the-middle (MitM) attacks.
Microsoft recommends LDAP signing requirements to protect active directory domain controllers from an elevation of privilege vulnerability (ADV190023).
Learn Vulnerability Assessments
![]()
SMB mining
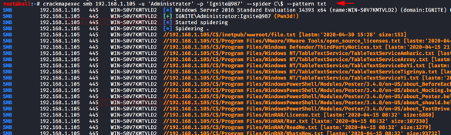
After obtaining a relay to a bunch of machines on the domain using the previously described LLMRN protocol, inspecting SMB shares is possible. If the relay authentication is not a local admin on the target, readable and writable shares can be used to find sensitive files or implant payloads. If the relayed authentication has local admin rights, a lot of attacks can be executed, including dumping the hashes, running mimikatz, or using the machine as a jumping machine to execute further tests and bypass security restrictions.
Abusing of popular vulnerabilities
Another way to exploit domain controllers while running an internal pentest is to take advantage of known exploits and verify if patches have been applied correctly.
Petitpotam CVE-2021-36942
Petitpotam abuses Microsoft’s Encrypting File System Remote Protocol (MS-EFSRPC) to coerce a host into authenticating to another over LSARPC on TCP port 445. NTLM hash is received on the target machine, and it can be used for performing relay attacks, downgrading to NTLMv1, and cracking it in minutes.
As mentioned in Microsoft’s ADV210003 advisory, users are potentially vulnerable if the AD using Active Directory Certificate Services (AD CS) with any of the following services:
-
Certificate Authority Web Enrollment
-
Certificate Enrollment Web Service
More details on Petitpotam are here.
Certipy/CVE-2022–26923
CVE-2022–26923 is a dangerous attack vector that allows getting domain admin privileges directly. The active directory does not have certificate services enabled by default, but if enabled, vulnerable certificate templates can expose the security of the entire domain.
Additional details about this CVE can be found here.
Password spraying
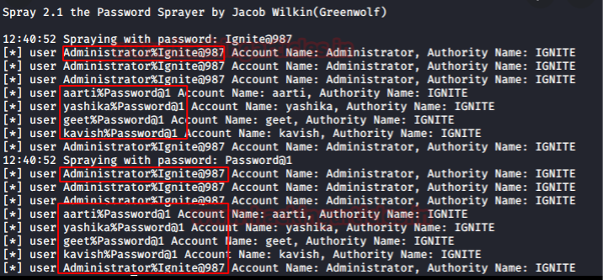
Password spraying is a kind of attack used to discover usernames and their credentials in an active directory network. With a weak password policy (length 7) and without a block threshold, running a popular list of passwords can retrieve some valid accounts.
Learn Vulnerability Assessments
![]()
Take care of your garden
Maintaining a secure network is an arduous and complex task due to the constant day-to-day changes. Within this field, active monitoring plays a key role. Not only rules at the network level and based on EventIDs, but also at the user account level, an attack vector generally used by cyber threats in remote threats, e.g., VPN access.
Thus, monitoring users on the domain and keeping an eye on some characteristics can reduce the risk of potential attacks, namely:
-
Ensure the minimum number of users with passwords never expire active
-
Service accounts should be complex and have passwords > 25 characters (these accounts are often exposed to Kerberosroast and pre_authenticated attacks)
-
Ensure that there are no admin and user accounts that have been inactive for too long (e.g., > 6 months)
And last but not least, the user-password authentication method is insecure by default. The usage of additional layers of security, such as MFA, plays a key role in preventing unauthorized access to stolen or leaked accounts.





