3 ways to launch your security awareness program: Pros and cons of each
Starting a security awareness program can feel like climbing a mountain without proper gear. You know it's necessary, but where do you begin?
The statistics speak for themselves: according to IBM's Cost of a Data Breach Report, the average data breach cost was $4.4 million in 2025. Perhaps more telling is that 60% of breaches involve the human element, according to Verizon's Data Breach Investigations Report.
Your employees can be your most vigorous defense or a point of vulnerability. A well-designed security awareness program transforms staff from potential security risks into your first line of defense.
This guide explores three practical approaches to launching your security awareness program:
- Building a program in-house with your existing resources
- Creating a hybrid model that combines internal expertise with external tools
- Partnering with a professional security awareness training provider
Each approach has distinct advantages and challenges. By understanding the pros and cons of each method, you'll be able to choose the path that best fits your organization's needs, culture and resources.
Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization. 
1. Develop your security awareness program in-house
Building a basic security awareness program in-house is where many organizations begin their journey. This approach typically involves using existing resources to create foundational training content and can help meet basic compliance requirements when budget or resources are limited.
Key steps to implement
- Secure basic leadership approval: Get minimal buy-in from executives by explaining compliance requirements and basic risk reduction benefits.
- Conduct simple assessments: Run a brief security culture survey to find your most critical knowledge gaps.
- Create baseline training: Develop essential materials covering fundamental topics like phishing awareness, password security and data protection policies.
- Leverage free resources: Use publicly available security posters, infographics and basic awareness materials to supplement your efforts.
- Implement basic testing: Run occasional phishing simulations to gauge employee vulnerability levels.
- Track completion rates: Monitor participation to ensure compliance requirements are met.
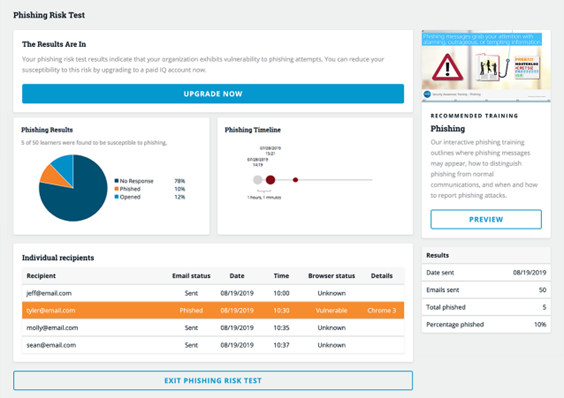
As part of your training launch, you’ll want to take advantage of freely available Phishing Risk Tests like this one from Infosec, to gauge employee vulnerability levels.
Benefits (pros)
- Might meet minimum requirements: Satisfies basic compliance needs and provides essential security information.
- Starting point: Creates a program that can evolve as your security program matures.
- Potentially low initial investment: Requires minimal budget to implement basic awareness activities.
Challenges (cons)
- Limited effectiveness: Basic programs rarely create lasting behavior change or significantly reduce human risk.
- Resource constraints: Creating content requires significant time from already-stretched security teams.
- Engagement challenges: Homegrown materials often struggle to captivate employee attention or drive meaningful participation.
- Difficult to scale: As organizations grow, maintaining even basic training becomes increasingly burdensome.
- Measurement limitations: Without specialized tools, it's difficult to assess program impact beyond completion rates.
- Rapidly outdated: Security threats evolve quickly, making manual content updates a challenge.
Real world example: Focusing on employee needs
Johnson County Government in Kansas took an employee-centered approach to its security awareness program. Donna Gomez, their Security Risk and Compliance Analyst, found success by actively seeking employee feedback on training content and format.
"Every time we do something, we ask, 'Well, what could we do? What do you want to know more about?'" says Gomez.
Johnson County broke down barriers between security staff and employees with surveys focused on employee opinions and needs. This approach helped Gomez transform her security team's reputation from "the department of no" to "the department of how can we help you."
Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
2. Use a hybrid approach: Level up your in-house training with add-on vendor solutions
As your security awareness program matures beyond basic compliance, and as you discover the unexpected costs and time of in-house training, you may look to strategically supplement your in-house efforts with specialized vendor tools and elevated content that address your most pressing needs.
Key steps to implement
- Identify your program's weaknesses: If you have a program, assess which aspects need the most improvement. Is it engaging content? Phishing simulations? Reporting capabilities? Delivery management?
- Select targeted vendor solutions: Rather than a comprehensive platform, look for specialized tools that address specific gaps:
- Professional phishing simulation tools
- High-quality training modules on complex topics
- Engagement-focused microlearning content
- Integrate selectively: Choose vendor components that complement your existing materials while providing immediate value in areas where internal development is challenging.
- Maintain your program foundation: Continue using your in-house processes for program management, while leveraging vendor content to enhance quality and engagement.
- Test and evaluate: Measure the impact of each vendor component to determine which additions deliver the best ROI for your specific needs.
Benefits (pros)
- Targeted improvement: Address specific program weaknesses without overhauling your entire approach.
- Budget flexibility: Invest in high-value components first, spreading costs over time as your program evolves.
- Quality enhancement: Access professionally developed content for complex or high-priority topics while maintaining in-house development for organization-specific materials.
- Experimentation: Test different vendor offerings before committing to a comprehensive solution.
Challenges (cons)
- Integration hurdles: Managing separate tools can create a disjointed experience without careful planning.
- Incomplete metrics: Different systems may not share data, making comprehensive reporting difficult.
- Administrative overhead: Managing multiple vendor relationships and platforms requires additional coordination.
- Inconsistent user experience: Employees may encounter varying quality and interfaces across different program elements.
- Limited scalability: As your program grows, managing multiple point solutions becomes increasingly complex.
Real-world example: Working with a vendor
Brookfield Renewable, a global renewable energy company, successfully implemented a hybrid approach to security awareness training. David Hansen, Senior Analyst for Corporate IT Security and Compliance, explains in How to build an effective security awareness program that he pairs internally developed materials with Infosec IQ's comprehensive platform.
This strategy allows Brookfield to address industry-specific challenges in the energy sector while leveraging professional content for universal security topics. Their security team develops specialized training modules for operational technology environments and critical infrastructure protection while relying on Infosec IQ for phishing simulations and foundational security awareness topics.
This balanced approach helps Brookfield maintain consistent security training across their global operations while still addressing unique regional and sector-specific requirements.
Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
3. Use a professional training provider
For organizations ready to make security awareness a strategic priority, implementing a complete security awareness platform like Infosec IQ provides an effective path to measurable security behavior change. This approach moves beyond piecemeal efforts to create an integrated program that combines professional content, automated delivery and comprehensive analytics.
Key steps to implement
- Define your security behavior goals: Identify specific behaviors you want to improve, whether it's reducing phishing susceptibility, improving password practices or enhancing data protection habits.
- Select a comprehensive platform: Look for solutions that offer:
- A complete content library covering all security topics relevant to your industry
- Automated campaign management for different roles and departments
- Advanced phishing simulations with real-time training interventions
- Detailed analytics that identify high-risk users and behaviors
- Integration capabilities with your existing systems
- Plan for a strategic rollout: Work with your vendor to create a structured implementation that builds momentum and engagement from day one.
- Customize for your environment: Tailor the platform to align with your organizational structure, security policies and industry-specific requirements.
- Establish a continuous program schedule: Move from annual "check-the-box" training to year-round microlearning that builds a security culture over time.
Benefits (pros)
- Complete solution: Access everything needed for an effective program within a single platform, from content to delivery to analytics.
- Time and resource efficiency: Automate time-consuming program management tasks, freeing your security team to focus on strategic priorities.
- Professional-quality engagement: Leverage content designed by learning experts to drive behavior change and maintain attention.
- Comprehensive reporting: Gain actionable insights into your human risk profile with easy-to-understand dashboards and detailed metrics on behaviors, knowledge gaps and improvement over time.
- Continuous improvement: Benefit from regular platform updates that incorporate the latest threats, training techniques and security best practices.
- Scalable approach: Easily expand your program as your organization grows without requiring proportional increases in security team resources
Partnering with training experts ensures engagement and promotes behavior change. View the Infosec Work Bytes: Award-Winning Engaging Cybersecurity Training Series
Challenges (cons)
- Initial investment: Professional platforms require budget allocation, though the ROI typically becomes clear within months.
- Change management: Transitioning from basic training to a comprehensive program requires effective internal communication.
- Vendor selection process: Choosing the right platform requires careful evaluation to ensure alignment with your specific needs.
Managed services: Full outsourcing
Some organizations prefer to work with a vendor to not only access a comprehensive program, but also and deliver it. If you don’t have the time or the resources to kickstart a security program, or manage it throughout the year, consider a managed services program.
For example, with the Infosec managed services program, you partner with one of our certified client success managers to build and execute your entire security awareness training program. This allows you to see results sooner, focus on your other priorities and ensure your organization is more cyber-resilient.
Real-world example: Raising the bar
Amway, an $8.8 billion direct-selling company with over 18,000 employees worldwide, partnered with Infosec IQ to transform its security awareness program. Information Security Specialist Dan Teitsma explains: "We wanted to significantly raise the bar in terms of employee security awareness and ensure all employees were doing everything in their power to help protect our company from security threats."
After implementing Infosec IQ, Amway achieved:
- 20% drop in overall phishing susceptibility
- 30% decrease in malware-infected machines
- 98% company-wide training completion rate
These results demonstrate the measurable ROI that professional security awareness training can deliver for organizations of all sizes.
Teitsma credits automation as a critical factor in their success: "We can design courses to our specifications and schedule training campaigns to run automatically — including sending learner notifications, tracking training progress and reporting important metrics to stakeholders."
Choosing the right approach for your organization
The best security awareness approach for your organization depends on your specific circumstances, resources and goals. Each approach represents a different stage in the security awareness journey:
In-house: Basic
- A starting point to meet minimum compliance requirements
- Provides essential security information with basic, limited resources
- Costs more in staff time and often has hidden expenses in design, production, maintenance and risk reduction effectiveness
Hybrid: Targeted vendor solution
- Enhances specific program elements that need improvement
- Balances budget constraints with quality improvements
- Allows experimentation before full commitment
Outsource: Stategic, comprehensive program
- Delivers measurable behavior change and risk reduction
- Automates program management to maximize efficiency
- Provides detailed analytics to demonstrate ROI
Consider the true costs and benefits
When evaluating your options, look beyond just implementation costs:
- Prevention value: The average data breach now costs $4.4 million, making even significant investments in prevention cost-effective by comparison
- Resource allocation: Does your team have the know-how, tools and time to create and deliver training in-house? Calculate the time your security team spends, or would spend, creating and managing awareness efforts that could be automated.
- Effectiveness gap: Consider the difference between "completed training" and engaging content that spurs behavior change and reduces incidents.
Focus on outcomes, not just activities
No matter which approach you choose, establish clear metrics tied to security outcomes:
- Reduction in successful phishing attacks
- Decrease in security incidents caused by human error
- Improvements in security policy compliance
- Increase in security event reporting by employees
These measurements help demonstrate program value to leadership and identify areas for continuous improvement.
See Infosec IQ in action
![]()
Start now and evolve
Some successful security awareness programs begin with basic in-house efforts and evolve toward more comprehensive solutions as their impact and importance become clear. Other organizations start by working with a vendor for their security programs.
The key is starting somewhere, measuring what’s working and what isn’t and committing to continuous improvement.
Remember that the most effective security awareness isn't a one-time training event but an ongoing process of building security behaviors and culture throughout your organization.
Ready to take your security awareness program to the next level? Explore our free security awareness resources or speak with an Infosec IQ expert to discuss which approach best fits your organization's needs.






