Email Security Awareness: How To Get Quick Results
Phishing and Spear phishing attacks on the rise
Phishing and spear phishing attacks are the most effective attack vectors. Despite the high level of awareness of the cyber threats, bad actors still consider email their privileged attack vector.
According to the security experts at Trend Micro firm, spear phishing is the attack method used in some 91 percent of cyber attacks,
The report titled the "Global Phishing Survey 2h3014" published by the Anti-Phishing Working Group (APWG) highlighted that in the second half of 2014, the domain names used for phishing broke a record. At least 123,972 unique attacks were observed all over the world, reaching the amazing figure of 95,321 unique domain names.
This data demonstrates intense activity related the phishing practices. In the majority of attack scenarios, they rely on malicious email that appears to come from a legitimate entity, which requests an action from the victims. Phishing messages usually include malicious links to websites controlled by bad actors, while others include a malicious attachment that once opened starts the infection process on the targeted system.
Differently from a common phishing attack, in the spear phishing attack scenario bad actors target a subset of people, usually the employees of an organization, members of an association or visitors of a particular website. The purpose of the attack is to collect personal information and other sensitive data that would be used later in further attacks against the victims.
Recent hacking campaigns carried out by several APT groups relied on malicious emails sent to the victims encouraging them to open Word or PDF documents that were specifically crafted to exploit vulnerabilities in the web browser to compromise the host. The analysis of the data related to the cyber attacks that occurred in the last five years demonstrates that email is the privileged threat vector for an attacker to compromise enterprises and organizations of any size.
The "Operation Aurora" attack (2010), the Target breach (2013), the most recent Sony Entertainment hack (2014), and the cyber attacks operated by Operation Carbanak and the Syrian Electronic Army are just a few examples of offensives that relied on spear phishing emails as an infection method.
In every case, the attacks started with malicious email not properly managed by the internal staff.
Every attack relying malicious email tries to exploit the weakest link of a security chain, the humans. It is clear that it is important to spread basic knowledge of email security in order to reduce drastically the success rate of the attacks.
Why criminals are interested my email account?
What is the commercial value of a hacked email account?
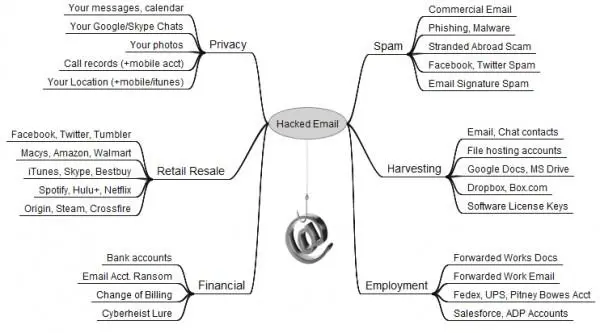
A couple of years ago, the popular investigator Brian Krebs published an interesting post to explain the commercial value of a hacked email account. The article provided useful information on the business model behind the theft of these precious commodities.
Email accounts are the containers where crooks can access an infinite amount of information, including passwords, documents, credit card data, utility bills and much more. A fraudster taking over a victim's account could discover his network of contacts, examine his habits, find information about his expenses (e.g. Travel, books, etc.), and then use the hacked email account to gain the access to the accounts of other web services (i.e. Facebook, eBay, PayPal, other email accounts).
The post published by Brian Krebs highlighted the importance of email security. An email account is an essential component of our digital identity and must be properly protected.
By accessing an email account, cyber-criminals steal data to resell on the underground market. It is quite easy to find many offers for hacked email accounts on the principal black markets. There are forums specializing in the sale of email accounts by industry. This is the right place for attackers that want to target individuals in a specific sector.
Figure 1 - Brian Krebs - Hacked Email accounts
Criminals could be interested in hacking email accounts for various reasons. Hackers could access them to spy on directly-connected accounts, or to use them to run phishing campaigns. In some cases the crooks could try to monetize the hacked account directly. As explained by Krebs, an individual could receive a message from a his contact, the hacked email account, that asking him to wire money somewhere claiming the owner of the account was without funds in some other part of the globe.
Email accounts could also be used to obtain access to cloud file-storage services linked to the email. Web storage, such as Dropbox and Google Drive are a privileged target for cyber-criminals.
According to the principal security firms, the most valuable commodities traded in the principal black markets are:
- Annual accounting balances and financial reports;
- Project plans and strategies of the company for several years;
- Intellectual property and innovations used for successful business;
- Customers databases and partners' contacts (CRM);
- Employee databases (Intranet systems);
- Credentials to corporate e-mails and personal e-mails of employees;
- Internal network infrastructure and its specifics.
Hacked email account could be used to gather access to payment systems such as PayPal, on daily basis cyber-criminals get access to tens of thousands of accounting credentials across multiple online payment processing services commercializing them in the underground.
Email Security Tips
Below is a list of useful suggestions that will allow you to secure your email account and your sensitive data if you do not have an email security awareness program:
Pay attention to the alleged phishing emails
Phishing emails are usually not solicited, and request sensitive information from the victims. Be wary when you receive messages asking for your personal information, or when the emails inform you that the service provider (i.e. Your Bank, Facebook, Twitter, eBay, etc.) is experiencing trouble with your account and request your credentials to solve the situation. In many cases, the malicious emails reproduce the layout of legitimate websites and include links to phishing pages crafted to request user data.
Never click links embedded in the Emails
In the majority of cases, when emails contains link you should not click on. It is a good practice to click on the link only when you're are expecting a particular email that is sent by trusted sources or by a service you trust.
Never click on link and images contained in unsolicited emails that offer a particular service or product for sale. If the email pretends to be from your bank, do not use the link it contains. Instead, always visit the website manually and do not copy and paste the link in your browser.
Do not open attachments in unsolicited email
Malicious attachments are the most common vector for infections, do not open files attached to emails sent by unknown people. Never open attachments in unsolicited email. Do not trust the file extension. Filenames can be spoofed and JPEG images could be EXEs in disguise and hide a loader for malicious payloads.
Avoiding the use of a unique email account to manage several web services.
In the majority of cases, Internet users used to have a unique email account which servedv as a recipient of messages from several different platforms and services. The same account is often used for work, to receive messages from social media, to receive newsletters, and many other uses.
Concentrating all of our activities into a single email account is a common error, in case of breach our entire digital identity would be compromised.
Having separate email accounts will improve the security of our digital existence in a significant way, in case of hack just a portion of our messages would be compromised. It could be useful to have a work account, a personal account for private messages, an account for recreational activities such as social networks and ecommerce websites, and a throwaway account for potential spam links.
Never share the same password over multiple email services
Avoid using a unique password for each email account we have. Using a single password for all the email accounts is a common mistake. If an attacker hack into a user personal email account it is able to access all the other accounts belonging to the victim that share the same password. Unfortunately, this simple practice is still neglected by the majority of the internet users.
Always scan for malware
Every time you receive suspect emails, even from trusted sources, run a malware and virus scanner. The attackers can compromise email account of your business partner of your girlfriend and then spread malware to the entire list of contacts.
Avoid Public Wi-Fi
Another good suggestion to secure email is avoid checking email when you are on public Internet. Hackers can sniff your password, your sensitive data or run Man-In-The-Middle attacks in order to hack in your email account.
Adopt a defense-in-depth approach
Cyber threats to email services have different forms for this reason it is not possible to adopt a unique approach, instead it is important to implement a defense-in-depth model that involves different technologies, including:
- Antivirus and anti-malware
- Content filtering
- Anti-spam
Use two-factor authentication
The two-factor authentication mechanisms could drastically improve security of email accounts. The authentication requires the knowledge of the password with the possession of a second factor of authentication, like a smart card or a mobile device used to generate a one-time-password code or to involve in a challenge-response process.
Enabling the two-factor authentication, even if the password is hacked, your account will be protected by the second factor of authentication.
Encrypt your email
Another important suggestion to follow to protect the emails from prying eyes is to encrypt them. Encryption could be used to protect private emails, making them impossible to decipher, this means that even if the account is compromised, the contents of the message will be not accessible. The only way to access the mail is to have the encryption key. Most encryption uses the Advanced Encryption Standard (AES), which provides key lengths of 128, 192 and 256 bits.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
References
http://securityaffairs.co/wordpress/37468/cyber-crime/global-phishing-survey-2h3014.html
http://securityaffairs.co/wordpress/36922/cyber-crime/study-phishing-emails-response.html
http://securityaffairs.co/wordpress/36922/cyber-crime/study-phishing-emails-response.html
http://www.makeuseof.com/tag/7-important-email-security-tips-you-should-know-about/