Why information security professionals should learn about law
Information security professionals are charged with protecting information systems from human attacks, natural disasters, accidents and Murphy’s Law. These security requirements are now subject to legal requirements imposed by statute, regulation and evolving law principles. The need for security is important, but legal duties do not stop there, with additional requirements for privacy, contract, e-discovery and more.

Get your free course catalog
If you drive a car, repair cars or manage a fleet of vehicles, legal knowledge is essential and taken for granted. Wear a seatbelt, stop at red lights, ensure brakes and other systems are operable, keep registration and insurance current, don’t drive while intoxicated etc. We know what the law is, and we know its purpose.
Legal requirements exist for the information systems we protect, so we should know what they are and have intelligent discussions about these rules and how to comply with them and protect the business. These rules are newer and rapidly evolving.
The legal requirements for technology and security
Legal requirements are here for cybersecurity and privacy, and we cannot manage our technology or information systems without properly understanding them.
On the one hand, the rules are generally based on common sense and protection. On the other hand, some rules can be highly complex and cause fear, uncertainty and doubt (FUD). This FUD can cause inefficiency and sometimes even paralysis.
We can understand the legal requirements and properly apply them with proper context and understanding, improving our efficiency.
Good information security programs incorporate legal requirements
Good information security programs consider and incorporate legal requirements. An organization's internal documentation should align with the laws and regulations and their action (practice).
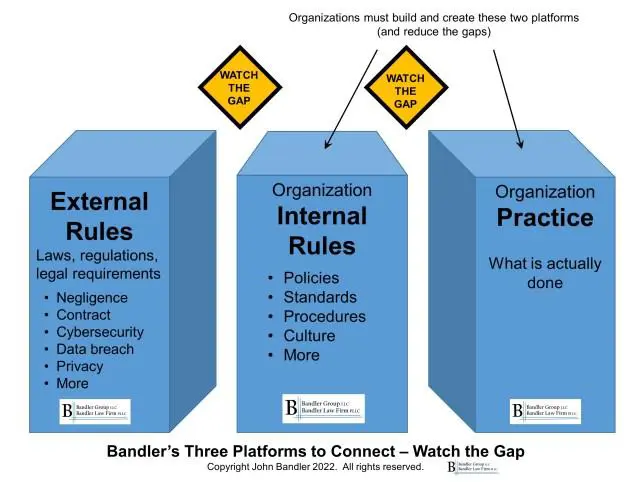
My Three Platforms to Connect is a helpful concept to help organizations visualize and implement this process.
- The first platform is external rules, including laws and regulations that we must understand and apply.
- Then we build a platform of internal rules (policies, procedures etc.).
- Finally, the third platform is what we do, our practice.
The goal is for all of those platforms to align and minimize the gaps between them. I illustrate this concept with my diagram.
Improve your knowledge of law to help you do your job better
We know that a variety of laws and regulations apply to information systems. It stands to reason we need to know what they are, comply with them, demonstrate that compliance and defend it when challenged.
If we do not know the law or what it means, we are disadvantaged. Good compliance and efficiency come from understanding both the spirit of the law and more detailed requirements.
Communicate with lawyers better
Building on the above, imagine if we do not know the law or its general principles. We would be at a disadvantage.
Many lawyers are wonderful and explain the law well, but we cannot consult them for everything. Imagine asking a lawyer about basics such as renewing your car insurance, how to comply with the speed limit or the most diligent way to avoid an accident on a slippery road. Of course, we do not do this because we understand traffic laws well enough to handle our compliance, and it is only after a serious incident that we would need to consult a lawyer.
The laws on cybersecurity, privacy, incident response and e-discovery can be complicated, but we can still understand them.
Now and then, an organization has a policy or procedure whose purpose or language is not well known, with uncertain terms that do not make apparent sense, but someone says, “It came from the lawyers,” and the discussion stops there. (On the flip side, the lawyers may be having similar conversations about something technical that they do not understand well.)
This is the point for thoughtful conversations so that the information security and legal professionals can hear each other’s concerns, justify their positions, and write in a manner that all sides can understand. To have those conversations, each side needs to know something about the other’s area of expertise. By learning more about law, you are doing just that.
A new privacy path
My new CIPP/US certification path may seem by the title to be solely focused on privacy law. But you will learn quickly that “privacy law” and “cybersecurity law” are so inextricably linked that it is often easier to think of them together as “privacy and cybersecurity law.” We also cover important and interesting topics such as e-discovery (a process in litigation where parties need to preserve and analyze data and documents that might be relevant for the lawsuit) and the general legal principles that our country was founded upon, which are even more important today.
So, why not take an online course to learn more about the CIPP/US certification, U.S. privacy law and how it relates to cybersecurity, privacy and our country.