CGEIT Domain 4: Risk Optimization
Introduction
Risk optimization falls under the fourth domain of the ISACA’s Certified in the Governance of Enterprise IT (CGEIT) exam and constitutes 24% of the overall objectives of the exam. This domain ensures that the framework for IT risk management is in place to identify, evaluate, monitor, mitigate, and communicate IT-related business risk. In addition, risk optimization ensures that the IT risk management framework is in alignment with an enterprise risk management (ERM) framework. The following sections elaborate the essential concepts that candidates must understand to take the CGEIT exam and expect an elite score.
What Topics Are Covered in This Domain?
This domain covers seven task statements and 14 knowledge statements. A thorough understanding of each topic is indispensable for CGEIT candidates. Below are detailed descriptions of these concepts:

Get certified with an Exam Pass Guarantee
Looking to get certified? Many of our boot camps are backed by an Exam Pass Guarantee, ensuring you leave with the certification you want.
Task Statements:
- Ensure that comprehensive IT risk management processes are established to identify, analyze, mitigate, manage, monitor, and communicate IT risk.
- Ensure that legal and regulatory compliance requirements are addressed through IT risk management.
- Ensure that IT risk management is aligned with the enterprise risk management (ERM) framework.
- Ensure that there is appropriate senior level management sponsorship for IT risk management.
- Ensure that IT risk management policies, procedures, and standards are developed and communicated.
- Ensure the identification of key risk indicators (KRIs).
- Ensure timely reporting and proper escalation of risk events and responses to appropriate levels of management.
Knowledge Statements:
- Knowledge of the application of risk management at the strategic, portfolio, program, project and operations levels.
- Knowledge of risk management frameworks and standards (for example, RISK IT, the Committee of Sponsoring Organizations of the Treadway Commission Enterprise Risk Management—Integrated Framework (2004) [COSO ERM], International Organization for Standardization (ISO) 31000).
- Knowledge of the relationship of the risk management approach to legal and regulatory compliance.
- Knowledge of methods to align IT and enterprise risk management (ERM).
- Knowledge of the relationship of the risk management approach to business resiliency (for example, business continuity planning [BCP] and disaster recovery planning [DRP]).
- Knowledge of risk, threats, vulnerabilities, and opportunities inherent in the use of IT.
- Knowledge of types of business risk, exposures, and threats (for example, external environment, internal fraud, information security) that can be addressed using IT resources.
- Knowledge of risk appetite and risk tolerance.
- Knowledge of quantitative and qualitative risk assessment methods.
- Knowledge of risk mitigation strategies related to IT in the enterprise.
- Knowledge of methods for monitoring effectiveness of mitigation strategies and/or controls.
- Knowledge of stakeholder analysis and communication techniques.
- Knowledge of methods to establish key risk indicators (KRIs).
- Knowledge of methods to manage and report the status of identified risk.
What Do I Need to Know About Risk Optimization?
Risk is a future-uncertain event that may impact the enterprise’s objectives. It is generally measured in terms of impact and likelihood. IT-related business risk consists of IT-related incidents such as cyber-attacks, compliance issues, and natural disasters that could potentially impact the business.
Risk optimization is the assurance that an enterprise’s IT-related risks do not exceed risk tolerance and risk appetite, the potential impact of IT risks to business value is identified, and the possibility for noncompliance is minimized.
According to ISO 31000, “Risk appetite is the type and amount of risk that an enterprise is prepared to pursue, take, or retain in order to meet its strategic objectives.” The enterprises link the risk appetite to their business decisions and collect appropriate metrics to implement and enforce it. Risk tolerance is, per the ISO Guide 73:2009 Risk Management definition, “an organization or stakeholder’s readiness to bear the risk in the wake of risk treatment to accomplish its objectives.”
A risk appetite statement is also vital because it delineates the levels of risk that management considers acceptable. Risk tolerance is narrower and sets the acceptable level of variation around the objectives.
Application of Risk Management: Risk management is the cornerstone of IT governance. It ensures that IT failures do not jeopardize the strategic objectives of the enterprise. Besides, business risk is affected by a business environment that involves management culture or style, risk appetite, and industry factors such as reputation, competition, and national and international regulations. Furthermore, the business environment can also affect IT risks. Therefore, the business community must take IT risks into consideration. The National Institute of Standards and Technology (NIST), in its Risk Management Guide, declares that the fundamental goal of an enterprise risk management process should be to protect the business and its capability to accomplish its mission, rather than just protecting its IT assets.
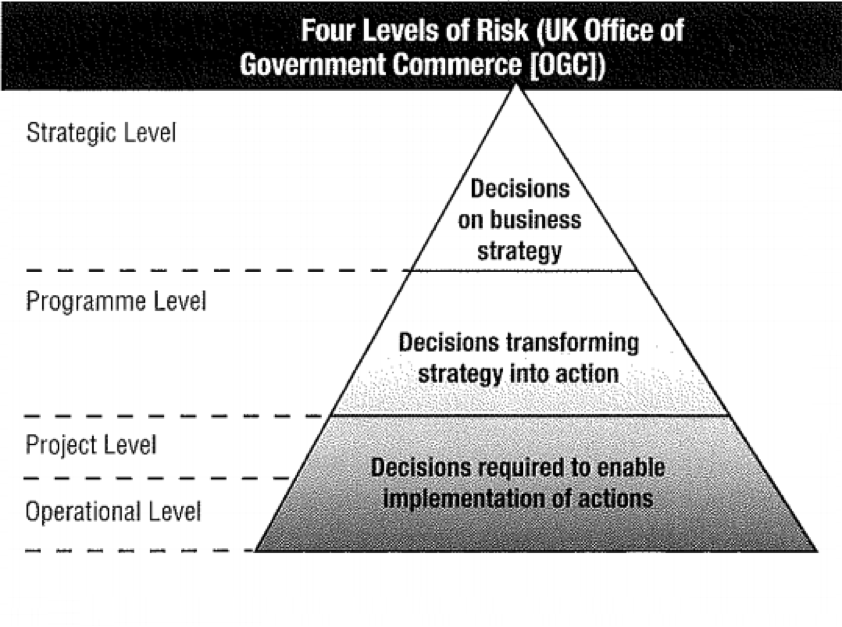
The UK Office of Government Commerce (OGC) defines four levels of risks that help businesses to consider IT risks. These four levels are strategic, program, project, and operational. Their brief description and pyramid visualization are given below.
- Strategic: Risk to IT accomplishing its objectives (e.g., financial, commercial, cultural, environmental, and so forth).
- Program: Risk involving acquisition or procurement, business continuity, security, organizational, and funding.
- Project: Project risks can be about people, cost, technical aspect, resources, schedule, security, and quality.
- Operational: Operational risks include all project risks plus some other risks, including infrastructure failures, business continuity, and customer relations.
 Source: ISACA, IT Governance Domain Practices, and Competencies: Information Risks (www.isaca.org)
Source: ISACA, IT Governance Domain Practices, and Competencies: Information Risks (www.isaca.org)
Risk Management Frameworks and Standards: Several risk management frameworks and standards are available, including Risk IT, COSO ERM, and ISO 3100. These frameworks and standards provide guidance for the application of risk management. For example, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) developed a framework for evaluating and improving an organization’s enterprise risk management (ERM). COSO ERM framework provides guidance on how to align risk appetite, enhance risk response, reduce operational surprises, identify and manage cross-enterprise risks, seize opportunities, and improve deployment of capital.Source: ISACA, IT Governance Domain Practices, and Competencies: Information Risks (www.isaca.org).
Types of Business Risks, Exposures, and Threats: The ERM model should address the enterprise objectives with the control objectives for risk in the underlying categories of business.
- Planning: High-level planning, budgeting, and resources allocation.
- Compliance Risk: Complying with the statutory requirements of all the jurisdictions within which the enterprise does business.
- Financial Reporting Risk: Presentation of financial results.
- Operational Risk: Involvement with day-to-day activities.
To run a business according to plan, enterprises must implement the internal controls that ensure that management reporting and financial statements provide an accurate view of operations and that all activities meet compliance requirements. One of the best internal controls that prevent frauds and mitigate risks is the so-called segregation of duties. Segregation of duties control is used to distribute specific tasks to specific individuals or groups. To detect segregation of duties violations, the enterprises use some automated tools that often contain three elements, access controls, locked-down operating and decision support, and risk analytics and reporting.
Quantitative and Qualitative Risk Assessment Methods: These methods are used to analyze threats and their related IT risks. The quantitative risk assessment method assigns numeric values to the loss of assets, but it cannot assign asset value for a potential monetary loss. On the other hand, the qualitative risk assessment method assigns intangible and subjective values to the loss of the asset.
Risk Mitigation Strategies: In the wake of risk assessment techniques, the risk management security folks implement several solutions, including risk avoidance, acceptance, transference, deterrence, and mitigation. Various other risk mitigation strategies include change management, incident management, performing routine audits, user rights and permission reviews, enforcing technology controls, and enforcing policies and procedures to prevent data theft and loss.
Where Should I Focus My Time Studying in This Domain?
Though taking any exam is stressful, candidates can make it easier by improving the way they study. Whether the student is a morning person or a night-owl, he/she should have a proper schedule for studying each day, rather than thriving on last-minute cramming, which is never the best way to approach an exam, CGEIT or otherwise.
Studying for the CGEIT domain Risk Optimization efficiently and effectively will keep the candidates from feeling unprepared and set them on the path to success. Doing so requires the candidates to review the CGEIT syllabus for this domain, pay attention in the class, prepare good notes, and make studying part of one’s daily habits.
More importantly, the candidates should pay heed to the CGEIT-approved material which is available at the ISACA Official Bookstore. Candidates should also refer to this “CGEIT Resources” article to get the best preparation material for the CGEIT exam.
InfoSec CGEIT Boot Camp—Your First Bet
InfoSec Institute's CGEIT Boot Camp Training is specifically designed to prepare students for ISACA's certification on IT governance principles and practices. You can enroll this course to acquire a professional CGEIT certification.
InfoSec has been one of the most awarded (42 industry awards) and trusted information security training vendors for the past 17 years.

Get certified with our Exam Pass Guarantee
Many of our boot camps come with an Exam Pass Guarantee: if you fail on your first attempt, we'll invite you to re-sit the course for free and cover the cost of your second exam.
InfoSec also offers thousands of articles on a variety of security topics.





